【VMware vSAN】vSAN Data Protection Part 4:脚本部署。
之前“vSAN Data Protection Part 1:安装部署。”这篇文章介绍了如何通过手动导入 OVA 模板并部署 VMware Snapshot Service Appliance 设备,还补充了安装过程中对于配置应该注意的一些事项。其实,我们也可以通过脚本自动化部署这一过程,这里使用了 VMware 工程师 William Lam 的 PowerCLI 脚本文件 deploy_vsan_data_protection_ova.ps1 ,下面是脚本的全部内容。
# vSAN DP OVA Path
$vsanDPOVA = "/Volumes/software/VMware OVA/snapservice_appliance-8.0.3.0-24057802_OVF10.ova"
# Deployment Configuration
$vsanDPVMName = "snap.primp-industries.local"
$vsanDPCluster = "Supermicro-Cluster"
$vsanDPDatastore = "sm-vsanDatastore"
$vsanDPVMNetwork = "Management"
# OVF Property Values
$vsanDPRootPassword = "VMware1!VMware1!"
$vsanDPHostname = "snap.primp-industries.local"
$vsanDPIPAddress = "192.168.30.96"
$vsanDPPrefix = "24"
$vsanDPGateway = "192.168.30.1"
$vsanDPDNS = "192.168.30.2"
$vsanDPDNSDomain = "primp-industries.local"
$vsanDPDNSSearch = "primp-industries.local"
$vsanDPvCenterServer = "vcsa.primp-industries.local"
$vsanDPvCenterServerUsername = "administrator@vsphere.local"
$vsanDPvCenterServerPassword = "VMware1!"
$vsanDPvCenterServerSSODomain = "vsphere.local"
#### DO NOT EDIT BEYOND HERE
# https://gist.github.com/jstangroome/5945820
Function Get-VCCertificate {
[CmdletBinding()]
param (
[Parameter(Mandatory=$true)]
[string]
$ComputerName,
[int]
$Port = 443
)
$Certificate = $null
$TcpClient = New-Object -TypeName System.Net.Sockets.TcpClient
try {
$TcpClient.Connect($ComputerName, $Port)
$TcpStream = $TcpClient.GetStream()
$Callback = { param($sender, $cert, $chain, $errors) return $true }
$SslStream = New-Object -TypeName System.Net.Security.SslStream -ArgumentList @($TcpStream, $true, $Callback)
try {
$SslStream.AuthenticateAsClient('')
$Certificate = $SslStream.RemoteCertificate
} finally {
$SslStream.Dispose()
}
} finally {
$TcpClient.Dispose()
}
if ($Certificate) {
if ($Certificate -isnot [System.Security.Cryptography.X509Certificates.X509Certificate2]) {
$Certificate = New-Object -TypeName System.Security.Cryptography.X509Certificates.X509Certificate2 -ArgumentList $Certificate
}
return $Certificate
}
}
# Get vCenter Server TLS Certificate
$cert = Get-VCCertificate -ComputerName $vsanDPvCenterServer
$vccert = "-----BEGIN CERTIFICATE-----" + $([System.Convert]::ToBase64String($cert.GetRawCertData()))+ "-----END CERTIFICATE-----"
$ovfconfig = Get-OvfConfiguration $vsanDPOVA
$ovfconfig.Common.vami.hostname.Value = $vsanDPHostname
$ovfconfig.Common.varoot_password.Value = $vsanDPRootPassword
$ovfconfig.NetworkMapping.Network_1.Value = $vsanDPVMNetwork
$ovfconfig.vami.VMware_SnapshotService_Appliance.addrfamily.Value = "ipv4"
$ovfconfig.vami.VMware_SnapshotService_Appliance.ip0.Value = $vsanDPIPAddress
$ovfconfig.vami.VMware_SnapshotService_Appliance.prefix0.Value = $vsanDPPrefix
$ovfconfig.vami.VMware_SnapshotService_Appliance.gateway.Value = $vsanDPGateway
$ovfconfig.vami.VMware_SnapshotService_Appliance.dns.Value = $vsanDPDNS
$ovfconfig.vami.VMware_SnapshotService_Appliance.domain.Value = $vsanDPDNSDomain
$ovfconfig.vami.VMware_SnapshotService_Appliance.searchpath.Value = $vsanDPDNSSearch
$ovfconfig.vcenter.VMware_SnapshotService_Appliance.hostname.Value = $vsanDPvCenterServer
$ovfconfig.vcenter.VMware_SnapshotService_Appliance.vcusername.Value = $vsanDPvCenterServerUsername
$ovfconfig.vcenter.VMware_SnapshotService_Appliance.vcuserpassword.Value = $vsanDPvCenterServerPassword
$ovfconfig.vcenter.VMware_SnapshotService_Appliance.vcdomain.Value = $vsanDPvCenterServerSSODomain
$ovfconfig.vcenter.VMware_SnapshotService_Appliance.vccert.Value = $vccert
$VMHost = Get-Cluster $vsanDPCluster| Get-VMHost | Select -first 1
Write-Host -ForegroundColor Green "Deploying vSAN Data Protection VM ..."
$vm = Import-VApp -Source $vsanDPOVA -OvfConfiguration $ovfconfig -Name $vsanDPVMName -Location $vsanDPCluster -VMHost $VMHost -Datastore $vsanDPDatastore -DiskStorageFormat thin -Force
Write-Host -ForegroundColor Green "Powering on vSAN Data Protection $vsanDPVMName ..."
$vm | Start-VM -Confirm:$false | Out-Null脚本中以下内容需要修改为自己当前环境中的实际信息,与手动部署 OVA 模板时相关配置的一样,需要提前在脚本里预定义这些信息。
- 配置虚拟机部署的 OVA 模板文件所在的位置。
# vSAN DP OVA Path
$vsanDPOVA = "D:\System\VMware\VMware vSAN\snapservice_appliance-8.0.3.0-24057802_OVF10.ova"- 配置虚拟机名称、所部署的集群、所使用的存储和网络。
# Deployment Configuration
$vsanDPVMName = "snap.mulab.local"
$vsanDPCluster = "vsan8-hci-esa"
$vsanDPDatastore = "vsanDatastore"
$vsanDPVMNetwork = "VM Network"- 配置虚拟机 Root 密码、主机名以及网络相关信息,连接 vCenter Server 的地址、用户名和密码等。注意,无需配置证书信息。
# OVF Property Values
$vsanDPRootPassword = "vSphere8@password"
$vsanDPHostname = "snap.mulab.local"
$vsanDPIPAddress = "192.168.32.13"
$vsanDPPrefix = "24"
$vsanDPGateway = "192.168.32.254"
$vsanDPDNS = "192.168.32.3"
$vsanDPDNSDomain = "mulab.local"
$vsanDPDNSSearch = "mulab.local"
$vsanDPvCenterServer = "vcsa8-01.mulab.local"
$vsanDPvCenterServerUsername = "administrator@vsphere.local"
$vsanDPvCenterServerPassword = "vSphere8@password"
$vsanDPvCenterServerSSODomain = "vsphere.local"准备好自动化部署脚本以后,现在您可以在你的环境中运行它。注意,请确保你已经安装了 PowerCLI 环境,这是运行脚本的前提条件。
1.打开 PowerShell 并进入脚本所在文件夹。
cd "C:\Users\JUNIOR_MU\Desktop\snap"
2.使用 PowerCLI 命令连接到 vCenter Server。
Connect-VIServer vcsa8-02.mulab.local -user administrator@vsphere.local -password vSphere8@password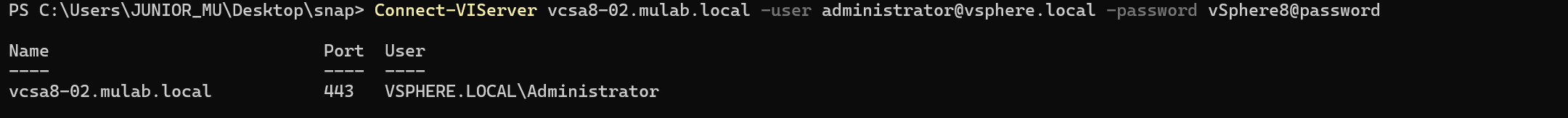
3.运行自动化部署脚本。
.\deploy_vsan_data_protection_ova.ps1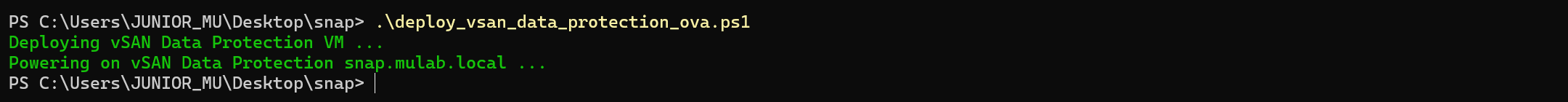
脚本运行后,如果一切顺利,登录 vSphere Client 可以看到已部署完成的虚拟机。
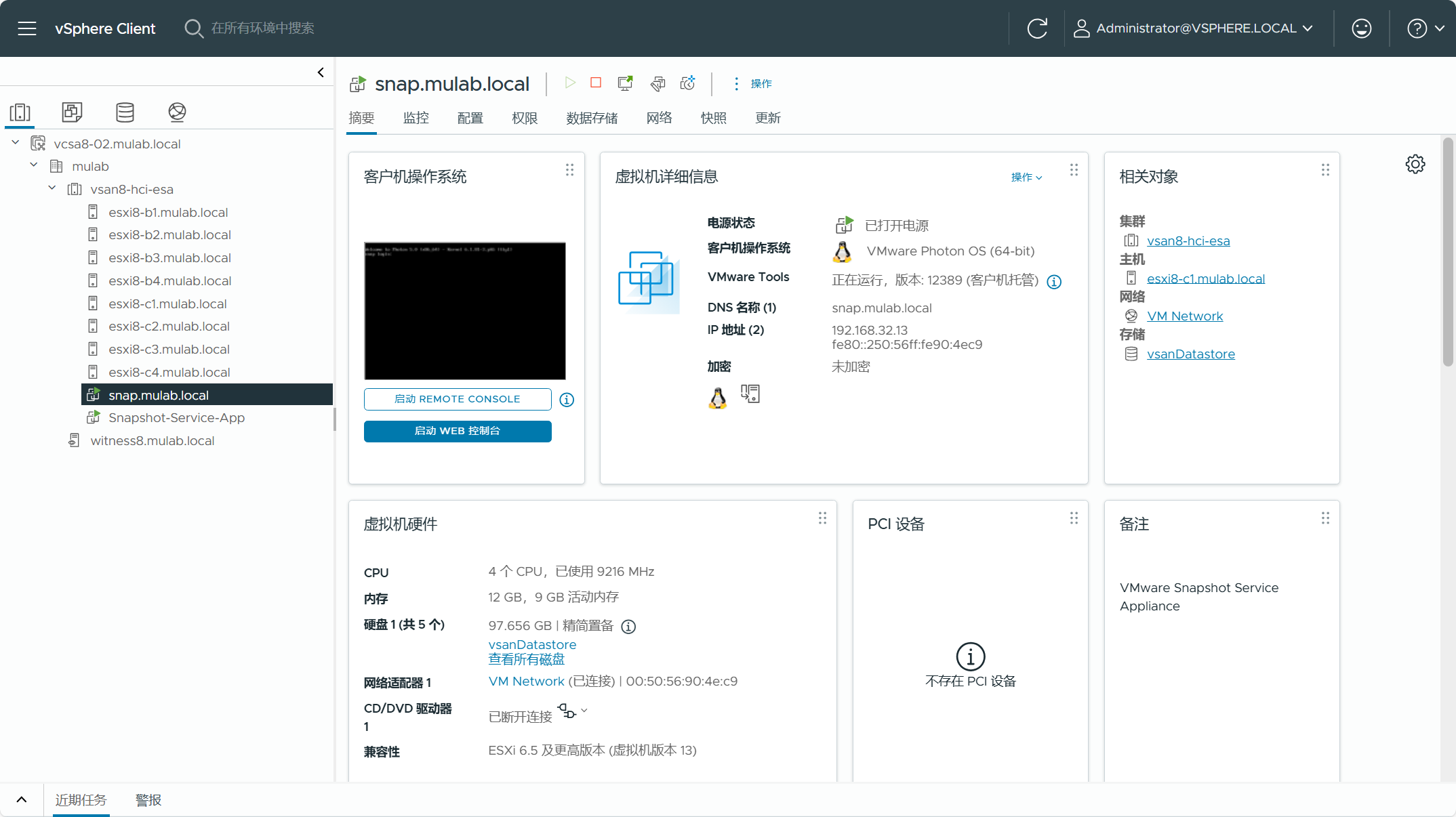
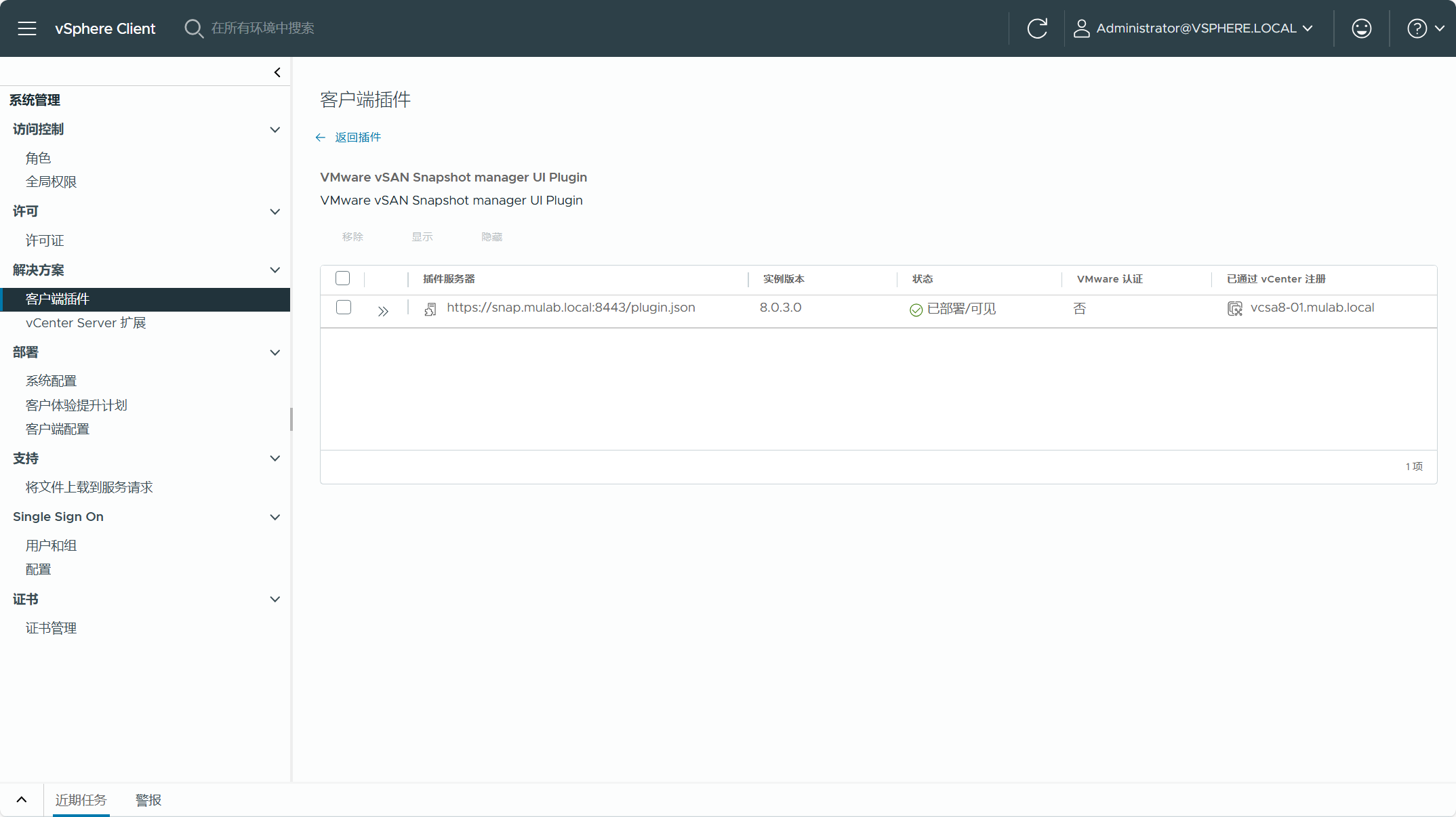
等待片刻后,登录到 vcsa8-01.mulab.local,如果所有配置都正确,您应该会在 vSphere Client 中看到一个通知横幅并显示“已成功部署插件......”。只需通过刷新浏览器即可访问新的 vSAN Data Protection 视图,请导航到已启用 vSAN ESA 的集群->配置->vSAN->数据保护。可以导航到vSphere Client->系统管理->解决方案->客户端插件,点击“VMware vSAN Snapshot manager UI Plugin”查看已注册的插件。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号