[网络/Linux]网络嗅探工具——nmap
1 nmap 简介
Nmap 即 Network Mapper,最早是Linux下的网络扫描和嗅探工具包。
nmap是网络扫描和主机检测的工具,用nmap进行信息收集和检测漏洞,功能有:
- 检测存活主机
- 检测主机开放端口(端口发现或枚举)
- 检测端口对应的软件和版本
- 检测操作系统类型、版本,硬件地址和软件版本
- 检测脆弱性的漏洞
2 安装使用
2-1 安装
安装方式1: yum
(CentOS下)
yum install nmap -y
安装方式2: rpm
- step1 下载、上传rpm安装包
nmap安装包下载 - nmap.org
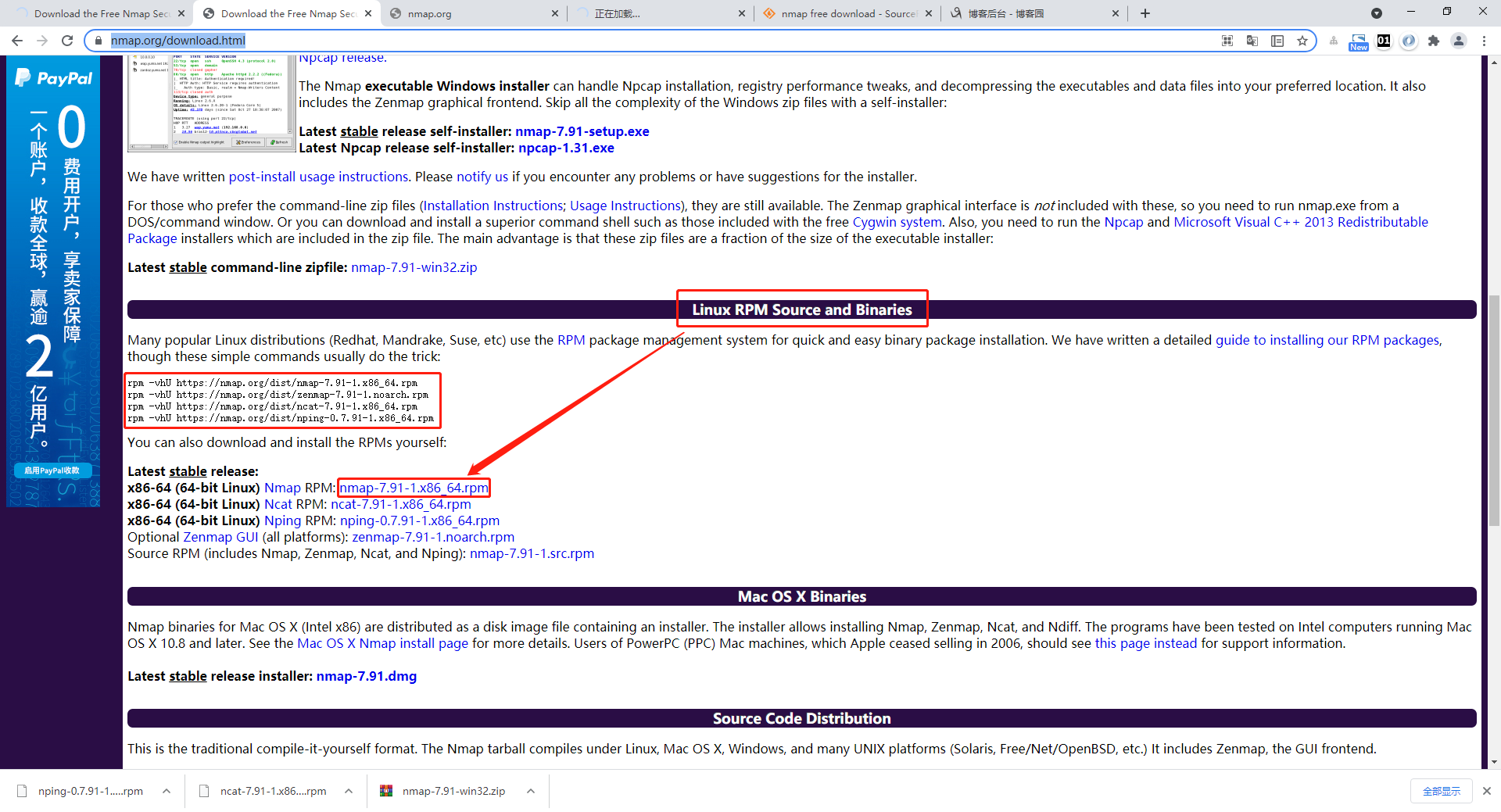
上传路径: /opt/nmap/nmap-7.91-1.x86_64.rpm
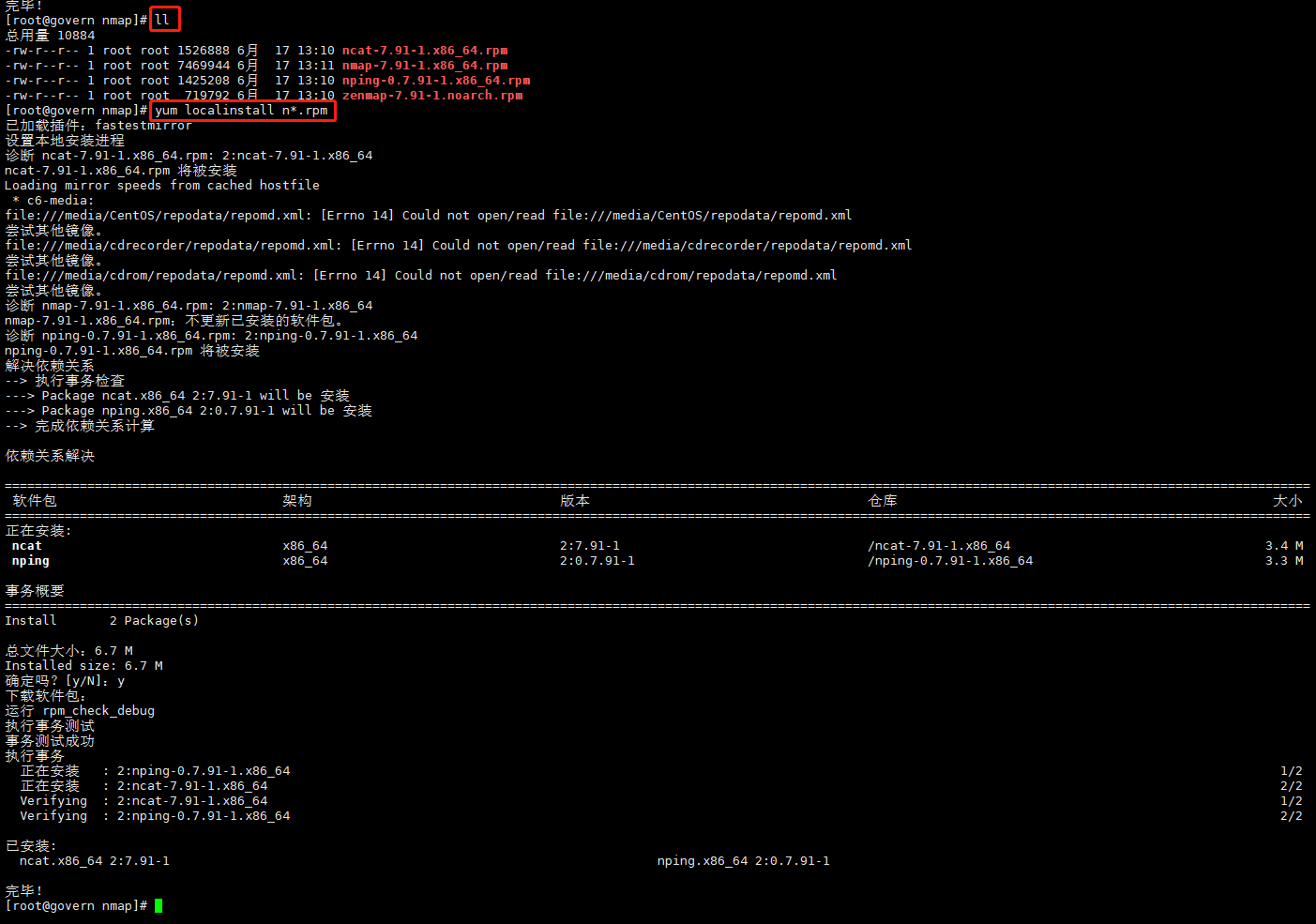
- step2 安装
cd /opt/namp/
yum localinstall *.rpm
或者 rpm -Uvh *.rpm
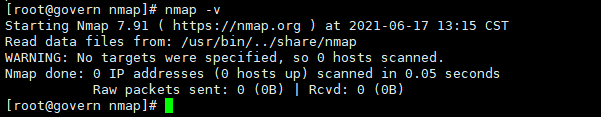
2-2 基本使用
# nmap localhost #查看主机当前开放的端口
Starting Nmap 6.40 ( http://nmap.org ) at 2020-10-23 07:11 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0000060s latency).
Other addresses for localhost (not scanned): 127.0.0.1
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
3306/tcp open mysql
Nmap done: 1 IP address (1 host up) scanned in 1.57 seconds
[root@centos7 ~]# nmap -O localhost
Starting Nmap 6.40 ( http://nmap.org ) at 2020-10-23 07:18 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0000050s latency).
Other addresses for localhost (not scanned): 127.0.0.1
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
3306/tcp open mysql
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.7 - 3.9
Network Distance: 0 hops
OS detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3.92 seconds
nmap -p 1024-65535 localhost #查看主机端口(1024-65535)中开放的端口
nmap -PS 192.168.21.163 #探测目标主机开放的端口
nmap -PS22,80,3306 192.168.21.163 #探测所列出的目标主机端口
nmap -O 192.168.21.163 #探测目标主机操作系统类型
nmap -A 192.168.21.163 #探测目标主机操作系统类型
nmap --help #更多nmap参数请查询帮助信息
2-3 常见使用
case0 扫描主机端口并跟踪路由
nmap --traceroute 8.8.7.5

case1 扫描(单台)主机当前开放的端口 : nmap host
# nmap localhost #查看(单台)主机当前开放的端口
Starting Nmap 6.40 ( http://nmap.org ) at 2020-10-23 07:11 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0000060s latency).
Other addresses for localhost (not scanned): 127.0.0.1
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
3306/tcp open mysql
Nmap done: 1 IP address (1 host up) scanned in 1.57 seconds
case2 扫描多台[整个IP段(子网)]主机当前开放的端口 : nmap host/网段掩码位数 | nmap 192.168.1.*
[通过子网掩码位,分网段扫描]
# nmap 108.61.87.202/24
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-04 09:37 ?D1ú±ê×?ê±??
Warning: 108.61.87.27 giving up on port because retransmission cap hit (10).
Stats: 0:32:27 elapsed; 10 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 99.65% done; ETC: 10:10 (0:00:07 remaining)
Stats: 0:32:29 elapsed; 10 hosts completed (64 up), 64 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 99.65% done; ETC: 10:10 (0:00:07 remaining)
Stats: 0:32:29 elapsed; 10 hosts completed (64 up), 64 undergoing SYN Stealth Scan
[* 本网络范围内所有主机]
可以用*通配符代表范围内的所有主机
[root@vultr ~]# nmap 108.61.87.*
Starting Nmap 5.51 ( http://nmap.org ) at 2018-07-04 15:01 CST
sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 108.61.87.62, 16) => Operation not permitted
Offending packet: TCP 108.61.87.202:35647 > 108.61.87.62:1503 S ttl=57 id=46459 iplen=44 seq=3156521255 win=2048 <mss 1460>
sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 108.61.87.34, 16) => Operation not permitted
Offending packet: TCP 108.61.87.202:35647 > 108.61.87.34:34571 S ttl=45 id=57342 iplen=44 seq=3156521255 win=2048 <mss 1460>
sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 108.61.87.39, 16) => Operation not permitted
[指定具体的多台主机]
nmap 192.168.1.1 192.168.5.6 //加空格分隔,写第二个ipAddress
# nmap 108.61.87.202 108.61.87.1
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-04 09:39 ?D1ú±ê×?ê±??
Nmap scan report for 108.61.87.202.vultr.com (108.61.87.202)
Host is up (0.32s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
22/tcp open ssh
Nmap scan report for 108.61.87.1.vultr.com (108.61.87.1)
Host is up (0.32s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
593/tcp filtered http-rpc-epmap
4444/tcp filtered krb524
Nmap done: 2 IP addresses (2 hosts up) scanned in 77.69 seconds
case3 综合扫描: nmap -A host
-A: Enable OS detection, version detection, script scanning, and traceroute
-A: 综合扫描,包括系统探测,版本探测,脚本扫描,路由跟踪
[root@centos7-202010061038 ~]# nmap -A www.baidu.com
Starting Nmap 6.40 ( http://nmap.org ) at 2020-10-23 07:34 UTC
Nmap scan report for www.baidu.com (119.63.197.139)
Host is up (0.11s latency).
Other addresses for www.baidu.com (not scanned): 119.63.197.151
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http-proxy sslstrip
|_http-methods: No Allow or Public header in OPTIONS response (status code 302)
| http-robots.txt: 10 disallowed entries
| /baidu /s? /ulink? /link? /home/news/data/ /bh /shifen/
|_/homepage/ /cpro /
|_http-title: \xE7\x99\xBE\xE5\xBA\xA6\xE4\xB8\x80\xE4\xB8\x8B\xEF\xBC\x8C\xE4\xBD\xA0\xE5\xB0\xB1\xE7\x9F\xA5\xE9\x81\x93
443/tcp open ssl/http-proxy sslstrip
|_http-methods: No Allow or Public header in OPTIONS response (status code 302)
| http-robots.txt: 10 disallowed entries
| /baidu /s? /ulink? /link? /home/news/data/ /bh /shifen/
|_/homepage/ /cpro /
|_http-title: \xE7\x99\xBE\xE5\xBA\xA6\xE4\xB8\x80\xE4\xB8\x8B\xEF\xBC\x8C\xE4\xBD\xA0\xE5\xB0\xB1\xE7\x9F\xA5\xE9\x81\x93
| ssl-cert: Subject: commonName=baidu.com/organizationName=Beijing Baidu Netcom Science Technology Co., Ltd/stateOrProvinceName=beijing/countryName=CN
| Not valid before: 2020-04-02T07:04:58+00:00
|_Not valid after: 2021-07-26T05:31:02+00:00
|_ssl-date: 2020-10-23T07:35:14+00:00; 0s from local time.
| tls-nextprotoneg:
|_ http/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|switch
Running (JUST GUESSING): AVtech embedded (88%), HP embedded (86%)
OS CPE: cpe:/h:hp:procurve_switch_4000m
Aggressive OS guesses: AVtech Room Alert 26W environmental monitor (88%), HP 4000M ProCurve switch (J4121A) (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 13 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 ...
2 0.35 ms 149.28.184.193
3 ... 4
5 0.36 ms xe-1-1-10.r20.sydnau02.au.bb.gin.ntt.net (202.68.65.5)
6 18.78 ms ae-1.r21.sydnau03.au.bb.gin.ntt.net (129.250.5.44)
7 112.96 ms ae-11.r31.tokyjp05.jp.bb.gin.ntt.net (129.250.5.34)
8 113.45 ms ae-3.r03.tokyjp05.jp.bb.gin.ntt.net (129.250.3.56)
9 113.11 ms ae-0.ocn.tokyjp05.jp.bb.gin.ntt.net (120.88.53.18)
10 114.63 ms 118.23.168.138
11 ... 12
13 114.72 ms 119.63.197.139
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.62 seconds
case4 软件版本检测: nmap -sV host
扫描目标主机的端口上运行的软件版本。
它不是用于扫描目标主机开放的端口,但需要从开放的端口获取信息来判断软件的版本。
所以,需要先进行端口扫描。
[root@centos7 ~]# nmap -sV xx.kk.yy.zz
Starting Nmap 6.40 ( http://nmap.org ) at 2020-10-23 07:56 UTC
Nmap scan report for xx.kk.yy.zz.vultr.com (xx.kk.yy.zz)
Host is up (0.0000040s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
3306/tcp open mysql MySQL 5.7.31-34
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.89 seconds
openssl version / ssh -V
case5 列出 指定服务器 开放的所有SSL加密套件: nmap --script ssl-enum-ciphers -p 443 baidu.com
更多类似用法[验证xxxx套件],可参见:
使用nmap 验证多种漏洞 - CSDN
[验证弱加密SSL套件]
[root@centos7 ~]# nmap --script ssl-enum-ciphers -p 443 baidu.com
Starting Nmap 6.40 ( http://nmap.org ) at 2020-10-23 08:05 UTC
Nmap scan report for baidu.com (220.181.38.148)
Host is up (0.34s latency).
Other addresses for baidu.com (not scanned): 39.156.69.79
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| SSLv3:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_RC4_128_SHA - strong
| compressors:
| NULL
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_RC4_128_SHA - strong
| compressors:
| NULL
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| compressors:
| NULL
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 - strong
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_ECDHE_RSA_WITH_RC4_128_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_256_GCM_SHA384 - strong
| compressors:
| NULL
|_ least strength: strong
[更多demo]
nmap -p 80 --script http-iis-short-name-brute +ip(192.168.1.1)[验证iis短文件名泄露]
nmap -sV -p 11211 -script memcached-info +ip[验证Memcached未授权访问漏洞]
nmap -sV -(-)script http-vuln-cve2015-1635 +ip[验证http.sys远程代码执行漏洞]
nmap -sV --script=ssl-heartbleed +ip[验证心脏出血漏洞]
nmap -p 27017 --script mongodb-info +ip[验证Mongodb未授权访问漏洞]
nmap -p 6379 --script redis-info +ip[验证Redis未授权访问漏洞]
nmap --script=http-vuln-cve2015-1427 --script-args command=‘ls’ +ip[验证Elasticsearch未授权访问漏洞]
nmap -p 873 --script rsync-brute --script-args ‘rsync-brute.module=www’ [验证Rsync未授权访问漏洞]
case6 扫描指定端口是否开放
默认扫描端口,1-10000的端口,大于10000的端口无法扫描出来
nmap -p 0-20000 8.8.7.55
# 探测服务器的0-20000端口范围,则能把大于10000的端口扫描出来了

nmap -p 10086,16638 8.8.7.55
# 使用-p参数探测10086、16388端口(指定查一个或者多个端口的状态)

case7 openssl 测试:指定服务器 是否支持 TLS 某版本的协议
关于 OpenSSH 与 OpenSSL可见:
[网络/SSH]OpenSSH: sshd / sftp-server / ssh-agent | ssh / scp / sftp | OpenSSL - 博客园/千千寰宇
# openssl s_client -connect www.baidu.com:443 -cipher RC4-SHA
# openssl s_client -connect www.baidu.com:443 -cipher DES-CBC3-SHA
# openssl s_client -connect 192.168.163.131:8443 -tls1_1
# openssl s_client -connect baidu.com:443 -tls1
# openssl s_client -connect baidu.com:443 -tls1_1
# openssl s_client -connect baidu.com:443 -tls1_2
[支持 TLS1.2协议的验证结果]
# openssl s_client -connect www.baidu.com:443 -cipher RC4-SHA
# openssl s_client -connect www.baidu.com:443 -cipher DES-CBC3-SHA
(输出内容与下面类似)
# openssl s_client -connect baidu.com:443 -tls1_2
CONNECTED(00000003)
depth=2 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA
verify return:1
depth=1 C = US, O = DigiCert Inc, CN = DigiCert SHA2 Secure Server CA
verify return:1
depth=0 C = CN, ST = Beijing, O = "BeiJing Baidu Netcom Science Technology Co., Ltd", OU = service operation department, CN = www.baidu.cn
verify return:1
---
Certificate chain
0 s:/C=CN/ST=Beijing/O=BeiJing Baidu Netcom Science Technology Co., Ltd/OU=service operation department/CN=www.baidu.cn
i:/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA
1 s:/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA
i:/C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIHJjCCBg6gAwIBAgIQAQV1J9uhA/WtTyocZe9DYTANBgkqhkiG9w0BAQsFADBN
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMScwJQYDVQQDEx5E
aWdpQ2VydCBTSEEyIFNlY3VyZSBTZXJ2ZXIgQ0EwHhcNMjAwMjI3MDAwMDAwWhcN
MjEwMjI2MTIwMDAwWjCBmDELMAkGA1UEBhMCQ04xEDAOBgNVBAgTB0JlaWppbmcx
OTA3BgNVBAoTMEJlaUppbmcgQmFpZHUgTmV0Y29tIFNjaWVuY2UgVGVjaG5vbG9n
eSBDby4sIEx0ZDElMCMGA1UECxMcc2VydmljZSBvcGVyYXRpb24gZGVwYXJ0bWVu
dDEVMBMGA1UEAxMMd3d3LmJhaWR1LmNuMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
MIIBCgKCAQEArYQtyRkFnRTFFIMCr2kfMPZLlCCMUOOCTeLj7VBk5gG4OjQa+Mns
DVOqQgpy58hejCKUgaAl4Jm73RQFeIC/2BDi8yRoRBhL9YrVoQMF7/5/8RI/94Lv
pEsf8hREYtP3uxleeh6ZwJceHzg3mLNuzWbjDg4EOemRE38OHdVeURBif0jG20zm
9Q8yQWT2MKp4oP2CeQv6NdL5lGWfSLq58D6GoWWoszMoP1HPfVv1pw4ywApjc5ls
gBaXquMOTy+AGpX1RmXGDTgK5yeRWAngeIA7szABJfnIndynnW1rTaBGr184sOfq
L7KscKIxErbR6vZD71iGrciHfIG3hP0exwIDAQABo4IDtDCCA7AwHwYDVR0jBBgw
FoAUD4BhHIIxYdUvKOeNRji0LOHG2eIwHQYDVR0OBBYEFNWOkWTVS4/rqlwmRPa/
AjIO41XEMIH0BgNVHREEgewwgemCCGJhaWR1LmNuggliYWlkdS5jb22CDGJhaWR1
LmNvbS5jboILdy5iYWlkdS5jb22CDHd3LmJhaWR1LmNvbYIQd3d3LmJhaWR1LmNv
bS5jboIQd3d3LmJhaWR1LmNvbS5oa4IMd3d3LmJhaWR1LmhrghB3d3cuYmFpZHUu
bmV0LmF1ghB3d3cuYmFpZHUubmV0LnBoghB3d3cuYmFpZHUubmV0LnR3ghB3d3cu
YmFpZHUubmV0LnZugg53d3d3LmJhaWR1LmNvbYIRd3d3dy5iYWlkdS5jb20uY26C
DHd3dy5iYWlkdS5jbjAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUH
AwEGCCsGAQUFBwMCMGsGA1UdHwRkMGIwL6AtoCuGKWh0dHA6Ly9jcmwzLmRpZ2lj
ZXJ0LmNvbS9zc2NhLXNoYTItZzYuY3JsMC+gLaArhilodHRwOi8vY3JsNC5kaWdp
Y2VydC5jb20vc3NjYS1zaGEyLWc2LmNybDBMBgNVHSAERTBDMDcGCWCGSAGG/WwB
ATAqMCgGCCsGAQUFBwIBFhxodHRwczovL3d3dy5kaWdpY2VydC5jb20vQ1BTMAgG
BmeBDAECAjB8BggrBgEFBQcBAQRwMG4wJAYIKwYBBQUHMAGGGGh0dHA6Ly9vY3Nw
LmRpZ2ljZXJ0LmNvbTBGBggrBgEFBQcwAoY6aHR0cDovL2NhY2VydHMuZGlnaWNl
cnQuY29tL0RpZ2lDZXJ0U0hBMlNlY3VyZVNlcnZlckNBLmNydDAJBgNVHRMEAjAA
MIIBAgYKKwYBBAHWeQIEAgSB8wSB8ADuAHUA7ku9t3XOYLrhQmkfq+GeZqMPfl+w
ctiDAMR7iXqo/csAAAFwhphdtAAABAMARjBEAiAk6qFarGxA9EQYUwRLa/5c+O32
PoWoiT8UHx2AnlvhpQIgWqfccctYWuyldVrEefwz7oeKmYj4DFZwA2cYqECVfokA
dQBc3EOS/uarRUSxXprUVuYQN/vV+kfcoXOUsl7m9scOygAAAXCGmF2pAAAEAwBG
MEQCIHbw6/3W4PwZoqwPGwqAnu78DBlbzlg84ngsaZ5O0Ab1AiAFae+lqnF9irvh
x9JyWUoedSqno53X+DqRp4vvD+uTDzANBgkqhkiG9w0BAQsFAAOCAQEAfHiQU/1K
AjZzbD5Eoy/gN5Gkbhtowztis1TZBlxkHsrqAxGXT47ZuHqo5JuSm/LePzKyuJXl
/E4H8kCk7a7tt2NWHFPIahU1svot1pAK9zyQItsJFqnwgQUBPwPGulgP7s/CquK2
U9KCTWHDMiT30lG5ydEKXUq520yn6Ew4V4fzFdINiO78VJzYb1og7Eb1m1wNwEWm
GrMRBOlVdoPKDLluyowGzIbwAADp/GSl5kGgNo7R4fDOT8Umv58p8qYKxu5bto++
G0h8rqce1b2jsRjBd1NaXG0azwAMncK615vGMdgrH/SAXLKewPErz5kWohIdVWzz
wKIvDsysKW1iSg==
-----END CERTIFICATE-----
subject=/C=CN/ST=Beijing/O=BeiJing Baidu Netcom Science Technology Co., Ltd/OU=service operation department/CN=www.baidu.cn
issuer=/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 3672 bytes and written 415 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES128-GCM-SHA256
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-GCM-SHA256
Session-ID: 405CBA3129490307D7A3845E07B3717B61295B5C6468D2C8A66A34E1E45DDF4B
Session-ID-ctx:
Master-Key: 2277DC7723C031C06B2DBBBB4E919D580B179BB81C00AF2E7D026A22221794554C1F560DC03311BCB70BC786F42B5A55
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 72000 (seconds)
TLS session ticket:
0000 - 1e 9c 4e 9f 18 19 4b f9-dd ff 98 d8 98 cb ee 0d ..N...K.........
0010 - 7b f5 83 7d 0f a3 31 d2-22 18 d0 db e3 c8 2a 52 {..}..1.".....*R
0020 - f3 c7 06 5d e1 8c 75 c0-58 60 90 b7 af bd 4a 62 ...]..u.X`....Jb
0030 - 3a b8 3c 17 81 32 b5 60-2f 45 16 fe 68 a6 2c c8 :.<..2.`/E..h.,.
0040 - bd 79 6f 57 fb 2d bb f0-a8 38 f1 01 67 3b 6c 8e .yoW.-...8..g;l.
0050 - 0c 8b 73 04 de 0c 02 df-8f 4b dc 3d 31 1f 79 01 ..s......K.=1.y.
0060 - b7 43 86 a2 cc 29 e0 77-0f 0c 56 f7 01 a4 81 ed .C...).w..V.....
0070 - ec a5 74 46 be cd 94 cd-eb af 8e 6d 46 fb b9 62 ..tF.......mF..b
0080 - dc 0d 88 63 1b 6f 60 8c-a2 21 47 72 64 ff 5e 43 ...c.o`..!Grd.^C
0090 - 35 3b 2b 41 19 5b f6 fa-4e 5d 9a de cf 40 de 66 5;+A.[..N]...@.f
Start Time: 1603446407
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---
closed
Cipher说明:
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-GCM-SHA256
- TLS协议: 支持TLS1.2版本
- 密钥交换算法: ECDHE-RSA (Elliptic Curve Diffie-Hellman Ephemeral, 椭圆曲线Diffie-Hellman临时-RSA密钥交换算法)
- 加密算法: AES128-GCM
GCM:Galois计数器模式(Galois/Counter Mode)。
消息认证码(MAC,Message Authentication Code)用于保障消息的完整性,防止各种伪造。
AES-CMAC 使用分组密码,取代 HMAC 的加密散列函数。
Galois 消息认证码(GMAC)则采用了 AES 算法的一种特殊模式。
- 报文认证信息码(MAC)算法: SHA256
[不支持 TLS1协议的验证结果]
# openssl s_client -connect xxxx.com:443 -tls1
CONNECTED(000000D8)
5424:error:1408F10B:SSL routines:SSL3_GET_RECORD:wrong version number:.\ssl\s3_pkt.c:362:
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 5 bytes and written 0 bytes
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1
Cipher : 0000
Session-ID:
Session-ID-ctx:
Master-Key:
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1565314976
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---
3 namp命令
[root@centos7 ~]# nmap --help
Nmap 6.40 ( http://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
--dns-servers <serv1[,serv2],...>: Specify custom DNS servers
--system-dns: Use OS's DNS resolver
--traceroute: Trace hop path to each host
SCAN TECHNIQUES:
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags <flags>: Customize TCP scan flags
-sI <zombie host[:probeport]>: Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b <FTP relay host>: FTP bounce scan
PORT SPECIFICATION AND SCAN ORDER:
-p <port ranges>: Only scan specified ports
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
-F: Fast mode - Scan fewer ports than the default scan
-r: Scan ports consecutively - don't randomize
--top-ports <number>: Scan <number> most common ports
--port-ratio <ratio>: Scan ports more common than <ratio>
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
--version-intensity <level>: Set from 0 (light) to 9 (try all probes)
--version-light: Limit to most likely probes (intensity 2)
--version-all: Try every single probe (intensity 9)
--version-trace: Show detailed version scan activity (for debugging)
SCRIPT SCAN:
-sC: equivalent to --script=default
--script=<Lua scripts>: <Lua scripts> is a comma separated list of
directories, script-files or script-categories
--script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts
--script-args-file=filename: provide NSE script args in a file
--script-trace: Show all data sent and received
--script-updatedb: Update the script database.
--script-help=<Lua scripts>: Show help about scripts.
<Lua scripts> is a comma separted list of script-files or
script-categories.
OS DETECTION:
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
TIMING AND PERFORMANCE:
Options which take <time> are in seconds, or append 'ms' (milliseconds),
's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m).
-T<0-5>: Set timing template (higher is faster)
--min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes
--min-parallelism/max-parallelism <numprobes>: Probe parallelization
--min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies
probe round trip time.
--max-retries <tries>: Caps number of port scan probe retransmissions.
--host-timeout <time>: Give up on target after this long
--scan-delay/--max-scan-delay <time>: Adjust delay between probes
--min-rate <number>: Send packets no slower than <number> per second
--max-rate <number>: Send packets no faster than <number> per second
FIREWALL/IDS EVASION AND SPOOFING:
-f; --mtu <val>: fragment packets (optionally w/given MTU)
-D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys
-S <IP_Address>: Spoof source address
-e <iface>: Use specified interface
-g/--source-port <portnum>: Use given port number
--data-length <num>: Append random data to sent packets
--ip-options <options>: Send packets with specified ip options
--ttl <val>: Set IP time-to-live field
--spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address
--badsum: Send packets with a bogus TCP/UDP/SCTP checksum
OUTPUT:
-oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3,
and Grepable format, respectively, to the given filename.
-oA <basename>: Output in the three major formats at once
-v: Increase verbosity level (use -vv or more for greater effect)
-d: Increase debugging level (use -dd or more for greater effect)
--reason: Display the reason a port is in a particular state
--open: Only show open (or possibly open) ports
--packet-trace: Show all packets sent and received
--iflist: Print host interfaces and routes (for debugging)
--log-errors: Log errors/warnings to the normal-format output file
--append-output: Append to rather than clobber specified output files
--resume <filename>: Resume an aborted scan
--stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML
--webxml: Reference stylesheet from Nmap.Org for more portable XML
--no-stylesheet: Prevent associating of XSL stylesheet w/XML output
MISC:
-6: Enable IPv6 scanning
-A: Enable OS detection, version detection, script scanning, and traceroute
--datadir <dirname>: Specify custom Nmap data file location
--send-eth/--send-ip: Send using raw ethernet frames or IP packets
--privileged: Assume that the user is fully privileged
--unprivileged: Assume the user lacks raw socket privileges
-V: Print version number
-h: Print this help summary page.
EXAMPLES:
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
SEE THE MAN PAGE (http://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
4 补充: ntsysv
ntsysv # 打开系统服务器管理器(需先安装yum install ntsysv),选择要关闭或者打开的服务
X 参考/推荐资料

本文作者:
千千寰宇
本文链接: https://www.cnblogs.com/johnnyzen
关于博文:评论和私信会在第一时间回复,或直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
日常交流:大数据与软件开发-QQ交流群: 774386015 【入群二维码】参见左下角。您的支持、鼓励是博主技术写作的重要动力!
本文链接: https://www.cnblogs.com/johnnyzen
关于博文:评论和私信会在第一时间回复,或直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
日常交流:大数据与软件开发-QQ交流群: 774386015 【入群二维码】参见左下角。您的支持、鼓励是博主技术写作的重要动力!

