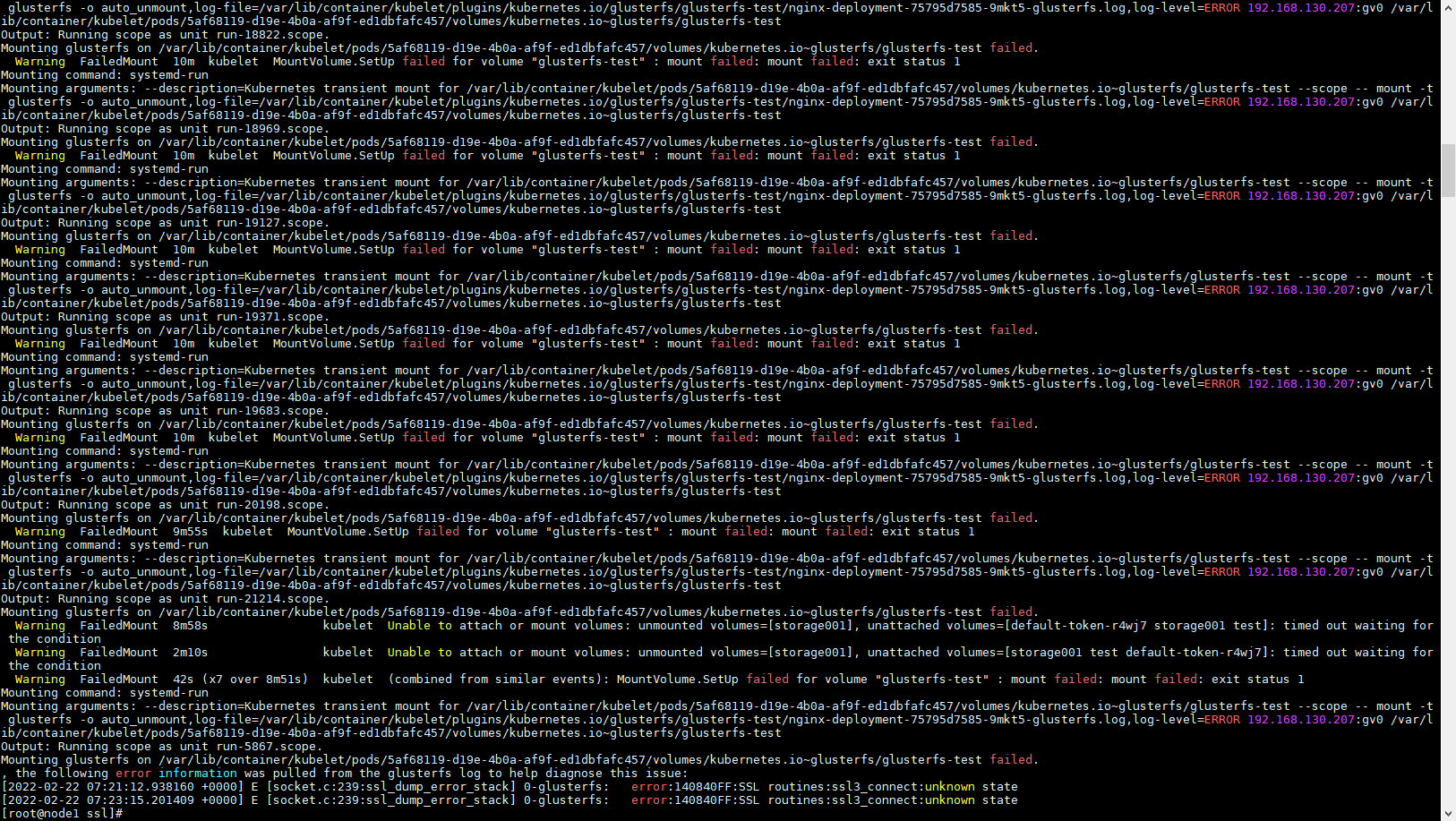
glusterfs集群启用ssl加密
原文:https://www.onitroad.com/jc/linux/how-to-enable-tlsssl-encryption-with-glusterfs-storage-cluster-on-linux.html
需求:
实现通过加密手段实现K8S利用glusterfs做为后端存储。
1.文件准备
需要在每个节点创建以下文件以进行TLS/SSL加密:
/etc/ssl/glusterfs.pemSSL证书。该文件"必须在每个节点上创建",并且"不得与群集中的任何其他节点或任何其他服务器共享"。/etc/ssl/glusterfs.keySSL私钥。该文件"必须在每个节点上创建",并且"不得与群集中的任何其他节点或任何其他服务器共享"。/etc/ssl/glusterfs.ca所有节点证书的串联。该文件"不是唯一的",并且在所有服务器节点和客户端上必须"相同"。/var/lib/glusterd/secure-access在每个节点的管理路径上启用TLS加密。需要使用touch命令在每个节点上创建此文件
2.配置
以下信息都需要在/etc/hosts中添加解析,此处不再列举
| K8S节点 | glusterfs节点 |
| master | gl1 |
| node1 | gl2 |
| node2 | gl3 |
3.实现glusterfs加密验证
#以下操作在所有节点操作 #生成私钥 cd /etc/ssl openssl genrsa -out glusterfs.key 2048 #输出示例 Generating RSA private key, 2048 bit long modulus ....................................+++ ............................+++ e is 65537 (0x10001) #生成自签证书
#不同节点替换主机名 openssl req -new -x509 -key glusterfs.key -subj "/CN=master" -out glusterfs.pem
#在gl1上操作
mkdir /tmp/ca
cd /tmp/ca
#拷贝所有节点到.pem文件到本地
scp root@master:/etc/ssl/glusterfs.pem master.pem
scp root@node1:/etc/ssl/glusterfs.pem node1.pem
scp root@node2:/etc/ssl/glusterfs.pem node2.pem
scp root@gl2:/etc/ssl/glusterfs.pem gl2.pem
scp root@gl3:/etc/ssl/glusterfs.pem gl3.pem
##给所glusterfs集群使用的证书
cat /etc/ssl/glusterfs.pem master.pem node1.pem node2.pem gl2.pem gl3.pem > glusterfs.ca
##注意两个文件名一致不要重复了
#把对应的证书拷贝到对应的节点上
#glusterfs
cp glusterfs.ca /etc/ssl/
scp glusterfs.ca root@gl2:/etc/ssl/
scp glusterfs.ca root@gl3:/etc/ssl/
##给K8S节点使用的证书
cat /etc/ssl/glusterfs.pem gl2.pem gl3.pem > glusterfs.ca
#K8S
scp glusterfs.ca root@master:/etc/ssl/
scp glusterfs.ca root@node1:/etc/ssl/
scp glusterfs.ca root@node2:/etc/ssl/
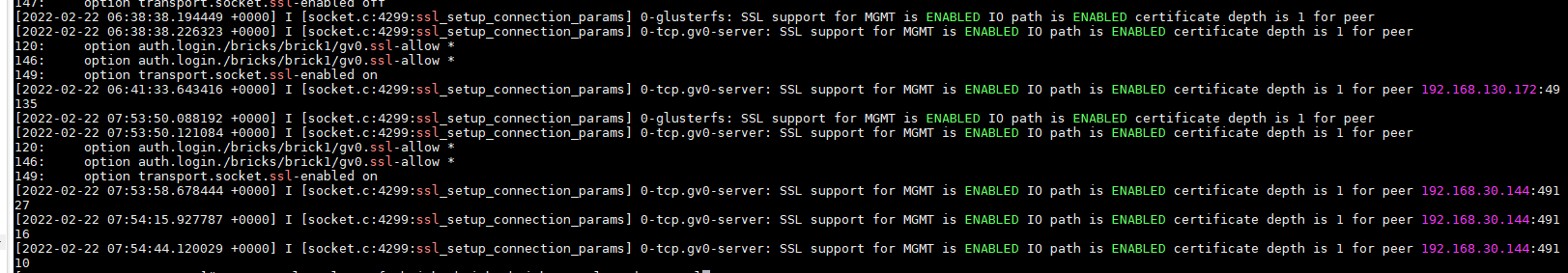
在glusterfs端实现SSL加密
#在所有glusterfs节点执行 touch /var/lib/glusterd/secure-access systemctl restart glusterfs-server.service #在K8S节点上挂载
###注意只要创建了该空文件,glusterfs客户端挂载时就默认使用加密验证,此时连接未加密的节点会报错删除即可 touch /var/lib/glusterd/secure-access #需要重新挂载 umount /var/www mount -t glusterfs gfs01:/gv0/mnt/www/
glusterfs虚拟机gv0启用TLS/SSL I/O加密
#首先停止集群中的gv0卷 gluster volume stop gv0 #卸载所有挂载点(如果有),并重启glusterfs节点的服务 umount /var/www systemctl restart glusterd #指定可以访问卷的节点 gluster volume set gv0 auth.ssl-allow 'master,node1,node2,gl1,gl2,gl3' ##也可以指定所有通过TLS验证的节点访问 gluster volume set gv0 auth.ssl-allow '*' #设置客户端访问卷用SSL gluster volume set gv0 client.ssl on #设置服务的访问卷用SSL gluster volume set gv0 server.ssl on #重启卷服务 gluster volume start gv0 #查看卷信息 gluster volume status gv0
##所有图片地址和上文不符不用纠结, 原环境用完已经删除
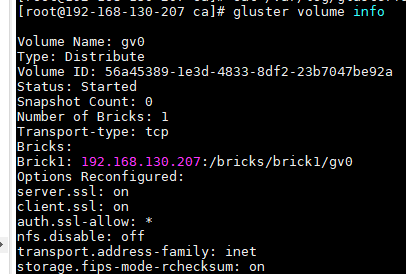
##客户端挂载验证 mount -t glusterfs gl1:/gv0 /mnt/www/ #glusterfs查看卷gv0的I/O路径上是否启用了SSL cat /var/log/glusterfs/bricks/bricks-brick1-gv0.log |grep ssl
5.创建PV验证
#创建endpoint
[root@k8s-1 glusterfs]# cat endpoints-test.yaml
apiVersion: v1
kind: Endpoints
metadata:
name: glusterfs-test
subsets:
- addresses:
- ip: 192.168.130.207
ports:
- port: 49159
protocol: TCP
#创建PV
[root@k8s-1 glusterfs]# cat glusterfs-test.yaml
apiVersion: v1
kind: PersistentVolume
metadata:
name: glusterfs-test
labels:
app: glusterfs-test
spec:
storageClassName: glusterfs
capacity:
storage: 10Gi
accessModes:
- ReadWriteMany
glusterfs:
endpoints: glusterfs-test
path: gv0
readOnly: false
创建PVC
[root@k8s-1 glusterfs]# cat glusterfs-pvc-test.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: gluster-test
spec:
storageClassName: glusterfs
accessModes:
- ReadWriteMany
resources:
requests:
storage: 2Gi
selector:
matchLabels:
app: glusterfs-test
#创建测试pod
[root@k8s-1 glusterfs]# cat nginx-test.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
spec:
selector:
matchLabels:
name: nginx
template:
metadata:
labels:
name: nginx
spec:
nodeSelector:
kubernetes.io/hostname: 192.168.30.144
containers:
- name: nginx
image: nginx
ports:
- containerPort: 80
volumeMounts:
- name: storage001
mountPath: "/usr/share/nginx/html"
- name: test
mountPath: /var/hyperledger/orderer/genesis.block
volumes:
- name: storage001
persistentVolumeClaim:
claimName: gluster-test
- name: test
hostPath:
path: /root/Agilement-zkjc/system-genesis-block/genesis.block
#type: File
##如果K8S节点验证失败会报错