Docker 镜像仓库
安装 Docker、Docker-Compose:https://www.cnblogs.com/jhxxb/p/11410816.html
Harbor
一、下载安装 Harbor
下载 Harbor(harbor-offline-installer):https://github.com/goharbor/harbor/releases
# 解压 sudo tar -zxf harbor-offline-installer-v2.0.2.tgz # 进入解压的目录,修改配置 sudo cp harbor.yml.tmpl harbor.yml sudo vim harbor.yml
修改配置(测试使用,不配置证书)
# 修改地址 hostname: 192.168.8.138 # http related config http: # port for http, default is 80. If https enabled, this port will redirect to https port port: 80 # 注释掉 https 访问 # https related config #https: # https port for harbor, default is 443 #port: 443 # The path of cert and key files for nginx #certificate: /your/certificate/path #private_key: /your/private/key/path # The default data volume data_volume: /data
安装启动
sudo ./install.sh
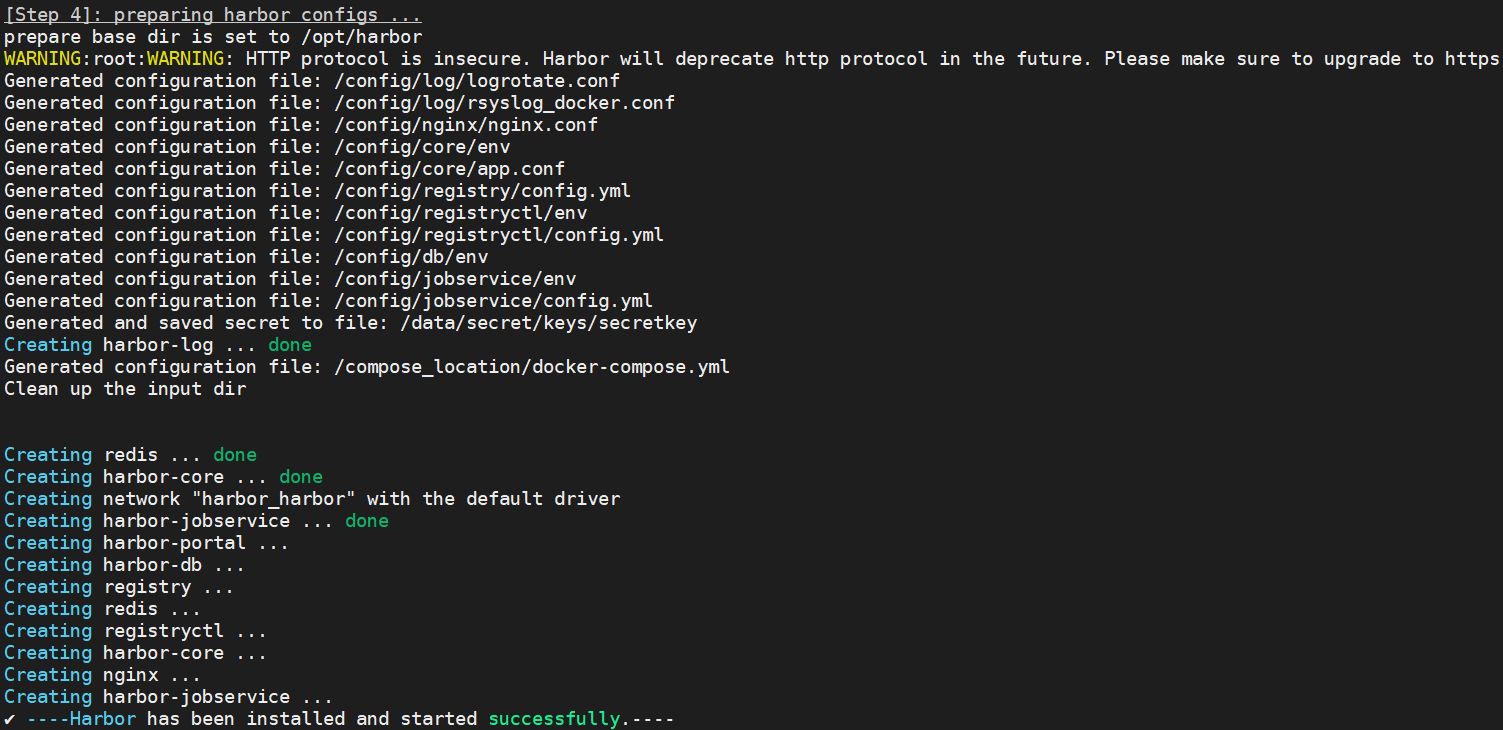
默认为 80 端口,用户名:admin,密码:Harbor12345

停止、重启 Harbor(需要在安装目录下运行)
# Stop Harbor. sudo docker-compose down -v # Restart Harbor sudo docker-compose up -d
开机自启
sudo vim /lib/systemd/system/harbor.service [Unit] Description=Harbor After=docker.service systemd-networkd.service systemd-resolved.service Requires=docker.service Documentation=http://github.com/goharbor/harbor [Service] Type=simple Restart=on-failure RestartSec=5 ExecStart=/usr/bin/docker-compose -f /opt/harbor/docker-compose.yml up ExecStop=/usr/bin/docker-compose -f /opt/harbor/docker-compose.yml down [Install] WantedBy=multi-user.target sudo systemctl enable harbor sudo systemctl start harbor
上传镜像
修改 docker push 配置,跳过 https 验证
# 需要配置 insecure-registries sudo vim /etc/docker/daemon.json { "registry-mirrors": ["https://ke9h1pt4.mirror.aliyuncs.com"], "insecure-registries": ["http://xxx.xxx.xxx.xxx", "http://myregistrydomain.com:5000", "0.0.0.0"] } # 重启服务 sudo systemctl restart docker
上传
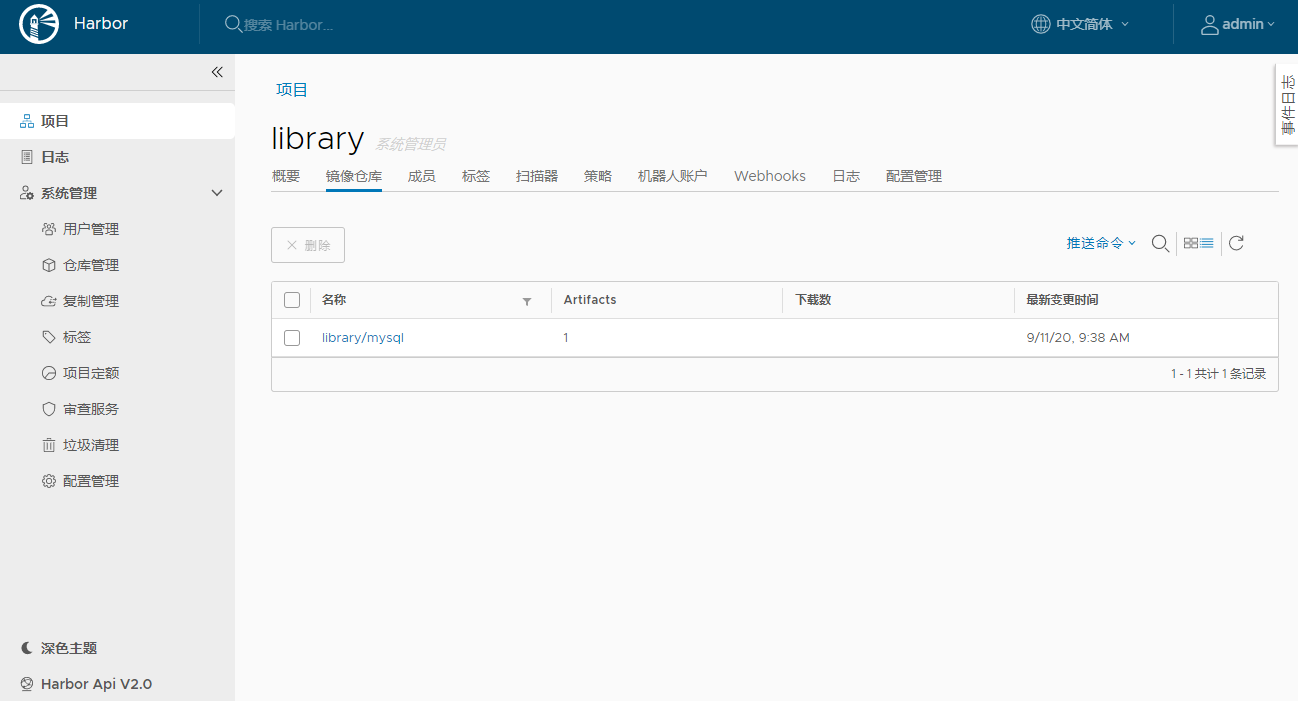
docker tag cd645f5a4769 192.168.8.138/library/mysql:latest # admin Harbor12345 docker login 192.168.8.138 # 上传 docker push 192.168.8.138/library/mysql:latest
批量执行
# 批量 tag for i in $(docker images | grep ^pig | awk 'BEGIN{OFS=":"}{print $1,$2}'); do docker tag $i xxx.xxx.xxx.xxx/xx-name/$i; done # 批量 push for i in $(docker images | grep xx-name | awk 'BEGIN{OFS=":"}{print $1,$2}'); do docker push $i; done
二、Helm 安装 Harbor
安装 helm
# 版本对应关系:https://helm.sh/zh/docs/topics/version_skew # 下载解压安装,https://helm.sh/zh/docs/intro/install/#用二进制版本安装 wget https://mirrors.huaweicloud.com/helm/v3.11.1/helm-v3.11.1-linux-amd64.tar.gz tar -zxf helm-v3.11.1-linux-amd64.tar.gz sudo mv linux-amd64/helm /usr/local/bin/helm # 查看安装结果 helm version # 配置命令提示补全,https://helm.sh/zh/docs/helm/helm_completion_bash helm completion bash > /etc/bash_completion.d/helm # https://helm.sh/zh/docs/intro/using_helm/#helm-repo使用仓库 # 添加 chart 仓库,https://artifacthub.io/packages/search helm repo add bitnami https://charts.bitnami.com/bitnami # 同步信息 helm repo update # 可以被安装的 charts 列表 helm search repo bitnami # 安装,一个 chart 在同一个集群里面可以被安装多次,每一个都可以被独立的管理和升级 #helm install mysql bitnami/mysql --create-namespace -n mysql helm install bitnami/mysql --create-namespace -g -n mysql # 查看创建的所有资源 kubectl get all -l app.kubernetes.io/instance=mysql-1678262196 -A -o wide # 了解到这个 chart 的基本信息 helm show chart bitnami/mysql # 获取关于该 chart 的所有信息 helm show all bitnami/mysql # 看哪些 chart 被发布了 helm ls -aA # 卸载,--keep-history 会保存版本历史 helm uninstall mysql-1678262196 -n mysql # 查看版本的信息 helm status mysql-1678262196 # 升级 helm upgrade mysql-1678262196 bitnami/mysql --force # 查看历史版本 helm history mysql-1678262196 # 如果是 uninstalled 状态,可以对它进行回滚版本 helm rollback mysql-1678262196 1 # https://helm.sh/zh/docs/intro/using_helm/#安装前自定义-chart # 查看 chart 中的可配置选项 helm show values bitnami/mysql # 可以使用 YAML 格式的文件覆盖上述任意配置项,并在安装过程中使用该文件 echo '{mariadb.auth.database: user0db, mariadb.auth.username: user0}' > values.yaml helm install -f values.yaml bitnami/mysql --generate-name
安装 Harbor
# 安装 helm repo add harbor https://helm.goharbor.io helm fetch harbor/harbor --untar --create-namespace -g -n harbor # 获取密钥 kubectl get secrets -n harbor harbor-1678332370-ingress -o jsonpath="{.data.ca\.crt}" | base64 --decode # docker 登录 sudo mkdir -p /etc/docker/certs.d/core.harbor.domain sudo tee /etc/docker/certs.d/core.harbor.domain/ca.crt > /dev/null <<EOF -----BEGIN CERTIFICATE----- MIIDFDCCAfygAwIBAgIRAOqvNfRxVeQkV8atPIXd0tkwDQYJKoZIhvcNAQELBQAw FDESMBAGA1UEAxMJaGFyYm9yLWNhMB4XDTIzMDMwOTAzMjYxM1oXDTI0MDMwODAz MjYxM1owFDESMBAGA1UEAxMJaGFyYm9yLWNhMIIBIjANBgkqhkiG9w0BAQEFAAOC AQ8AMIIBCgKCAQEApobDj5JkyED0LW+2C2in+AAtfmbOFLkKhZBvA13qtbMInHZf Te6onGkyLvYgZxh26qUhg5mjimWYJGEWCdfEe5G3SlQPXG17at/glZGqoRPmUrwu VCKOX72dnMu34gs/Qck2m7K7qxZnQvBA2pqnnulry+mauMv4PuMnLOfrwjGL2Jbi HugM4DW0xFjFfVHKZoQGcaXRl0QCzMq7L7uXJun+lPvKzb62MDozqOf5fz+q4QJJ JRzcsxER+ty93IIYFnv0lluykMet+UgErX/wgco0oyV/EnkFf1rWnVfK0+8YYuA6 d0qViuROVben9nvp6Ihoaysk1pSuThDo3watEwIDAQABo2EwXzAOBgNVHQ8BAf8E BAMCAqQwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMA8GA1UdEwEB/wQF MAMBAf8wHQYDVR0OBBYEFC2gNOghiSAB1HlZSGJr/cXvZSI6MA0GCSqGSIb3DQEB CwUAA4IBAQAU7XecSLaBmTy1uv9gkE9A/AzRXDkkdk5YyBh8BRjAeqWxERaJT9ic 5JRlRqLxjNjRrs7GSSCF9xJKMXGGrT4dAHkJdc208376mnUyye73zrQ8vLaPlOgK RMCCffyJvej+8JrF0e7wk0ef0eVcLBNhePGXrOVMYsyPTIIR1aggYo3U6wMucZhg g+4ofg63ISA7NFmzkiSORDU04+FnmXZQ2ULgkJnBzLFlfqL/7lB34MW9DOfiPfhR xJW7D3EFwJO23qnRR96RqPNSEW9dZjGFugIVQMMTxlT3KghBl1j5fvo56Mdk+QyD eyb+8bGY4F77tLYBVK8B6gd5qLWxolar -----END CERTIFICATE----- EOF echo '10.74.1.170 core.harbor.domain' | sudo tee -a /etc/hosts docker login core.harbor.domain -u admin Harbor12345 # k8s 拉取私有镜像需要账号密码 kubectl create secret docker-registry regsecret --namespace=streampark --docker-server=core.harbor.domain --docker-username=admin --docker-password=Harbor12345
distribution
一、安装仓库服务
创建 SSL 证书
https://docs.docker.com/engine/security/protect-access
https://docs.docker.com/registry/#use-self-signed-certificates
一般情况下,证书只支持域名访问,要使其支持 IP 地址访问,需要修改配置文件 openssl.cnf
# 在其中的 [ v3_ca ] 部分,添加 subjectAltName 选项 sudo mkdir -p /etc/pki/tls sudo vim /etc/pki/tls/openssl.cnf [ v3_ca ] subjectAltName = IP:10.74.2.71 # 生成证书,Common Name 写 registry 域名 mkdir -p certs openssl req \ -newkey rsa:4096 -nodes -sha256 -keyout certs/domain.key \ -x509 -days 365 -out certs/domain.crt Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BJ Locality Name (eg, city) [Default City]:BJ Organization Name (eg, company) [Default Company Ltd]: Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []:myregistry.domain.com Email Address []: # 修改权限,安装证书文件到 docker 客户端 sudo chcon -Rt svirt_sandbox_file_t ./certs sudo mkdir -p /etc/docker/certs.d/10.74.2.71:5000/ sudo cp ./certs/domain.crt /etc/docker/certs.d/10.74.2.71:5000/ca.crt
创建账号
https://docs.docker.com/registry/#authentication
Linux 中, > 表示覆盖原文件内容,>> 表示追加内容,下面两个镜像命令都可以生成用户名密码
sudo mkdir -p /opt/registry/auth docker run --rm --entrypoint htpasswd registry:2.6.2 -Bbn user pass >> /opt/registry/auth/htpasswd docker run --rm --entrypoint htpasswd httpd:2 -Bbn user pass >> /opt/registry/auth/htpasswd
创建镜像仓库
docker run -d --name registry \ --restart=always --privileged=true \ -v /opt/registry/data:/var/lib/registry \ -e REGISTRY_STORAGE_DELETE_ENABLED=true \ -v /opt/registry/auth:/auth \ -e REGISTRY_AUTH=htpasswd \ -e REGISTRY_AUTH_HTPASSWD_REALM=basic-realm \ -e REGISTRY_AUTH_HTPASSWD_PATH=/auth/htpasswd \ -v /opt/registry/certs:/certs \ -e REGISTRY_HTTP_TLS_CERTIFICATE=/certs/domain.crt \ -e REGISTRY_HTTP_TLS_KEY=/certs/domain.key \ -p 5000:5000 \ registry
-v /opt/registry/data:/var/lib/registry:自定义镜像存放路径
-e REGISTRY_STORAGE_DELETE_ENABLED=true:开启删除镜像的功能
-v /opt/registry/auth:/auth:认证文件路径,用于 docker login 时的用户名密码验证
-v /opt/registry/certs:/certs:SSL 证书文件路径,用于 docker login 时的 https 验证
编辑配置
https://github.com/Joxit/docker-registry-ui#using-cors
https://distribution.github.io/distribution/about/configuration
docker exec -it registry vi etc/docker/registry/config.yml version: 0.1 log: fields: service: registry storage: delete: enabled: true cache: blobdescriptor: inmemory filesystem: rootdirectory: /var/lib/registry http: addr: :5000 headers: X-Content-Type-Options: [nosniff] Access-Control-Allow-Origin: ['*'] Access-Control-Allow-Methods: ['HEAD', 'GET', 'OPTIONS', 'DELETE'] Access-Control-Expose-Headers: ['Docker-Content-Digest'] health: storagedriver: enabled: true interval: 10s threshold: 3 docker restart registry
二、基本使用
取消 docker login 时的 https 验证(若仓库没有配置 SSL):修改 docker 配置文件:/etc/docker/daemon.json,增加内容 "insecure-registries": ["10.74.2.71:5000"]
{
"registry-mirrors": ["https://82m9ar63.mirror.aliyuncs.com", "https://hub-mirror.c.163.com"],
"insecure-registries": ["10.74.2.71:5000"]
}
重启服务
systemctl daemon-reload && systemctl restart docker
命令
# 登录登出 docker login 10.74.2.71:5000 -u user -p pass docker logout 10.74.2.71:5000 # 拷贝一个镜像,并重命名(用于测试下一步的上传) docker tag 28dzdaf856cb 11.71.91.51:5000/openjdk:alpine # 推送镜像到本地镜像仓库 docker push 11.71.91.51:5000/openjdk:alpine # 拉取本地仓库中的镜像 docker pull 11.71.91.51:5000/openjdk:alpine
删除,不会实际删除镜像文件,需要手动清理:https://distribution.github.io/distribution/about/garbage-collection
docker exec -it registry sh registry garbage-collect /etc/docker/registry/config.yml du -sch /var/lib/registry
API
https://distribution.github.io/distribution/spec/api
# 查看本地镜像仓库的镜像 curl http://11.71.91.51:5000/v2/_catalog # 查看本地镜像仓库镜像的 tag curl http://11.71.91.51:5000/v2/openjdk/tags/list
三、第三方 UI 界面
https://hub.docker.com/r/joxit/docker-registry-ui
参数说明:https://github.com/Joxit/docker-registry-ui#available-options
若 UI 也想用 HTTPS 访问:https://github.com/Joxit/docker-registry-ui/tree/main/examples/issue-20
不要使用 127.0.0.1,会指向容器本机,非宿主机。把 REGISTRY_URL 换成 NGINX_PROXY_PASS_URL 就会使用 Nginx 代理访问仓库(不会出现跨域问题)
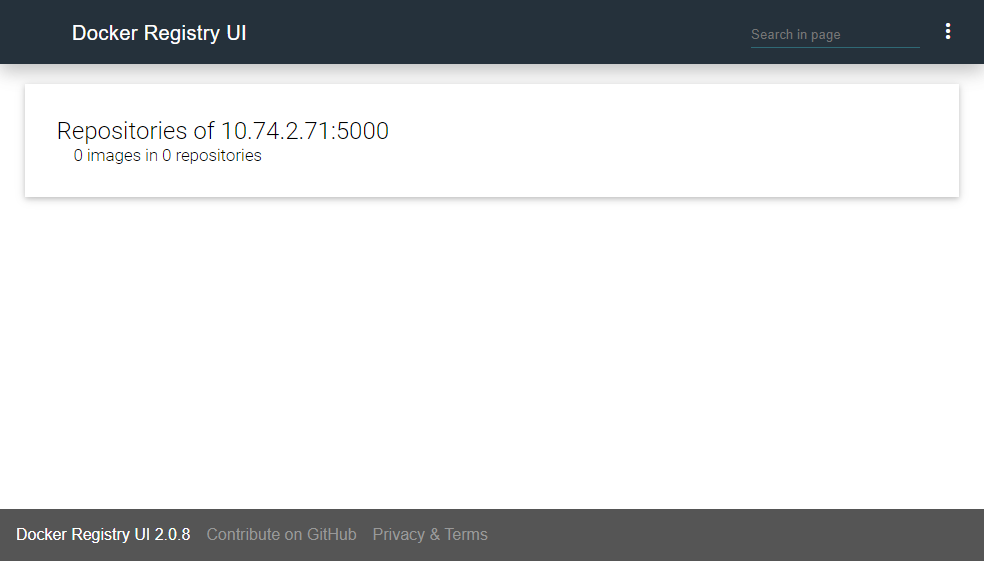
docker run -d --name registry-ui \ --restart=always \ -e DELETE_IMAGES=true \ -e SINGLE_REGISTRY=true \ -e PULL_URL=10.74.2.71:5000 \ -e REGISTRY_URL=https://10.74.2.71:5000 \ -p 5001:80 \ joxit/docker-registry-ui
当 SINGLE_REGISTRY 设置为 false 时(默认 false),界面上会出现一个菜单,允许动态更改 docker registry URL
访问服务器 5001 端口
https://docs.docker.com/registry/configuration
https://goharbor.io/docs/latest/install-config
https://hub.docker.com/_/registry



