hadoop安全报警
【漏洞名词】
Hadoop 未授权访问【原理扫描】
【漏洞说明】
Hadoop是一个由Apache基金会所开发的分布式系统基础架构。
用户可以在不了解分布式底层细节的情况下,开发分布式程序。充分利用集群的威力进行高速运算和存储。
在默认情况下,Hadoop允许任意用户访问管理接口。
【加固建议】
1. 配置Service Level Authorization
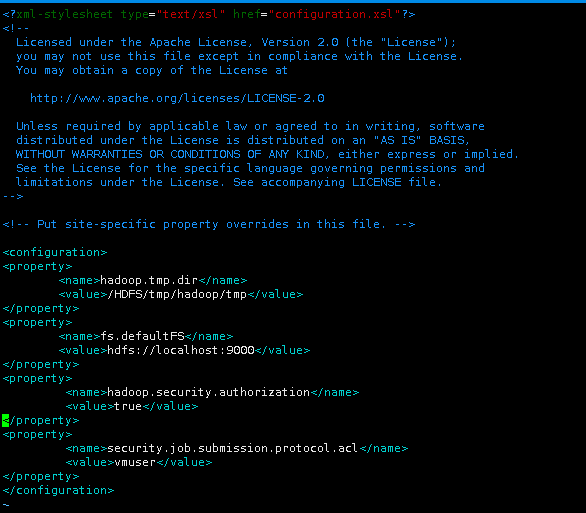
修改coresite.xml
<property>
<name>hadoop.security.authorization</name>
<value>true</value>
</property>
hadoop.security.authorization=true则开启ServiceLevel Authorization,若为false则不经过任何验证,所有用户拥有全部权限。(修改此配置需要重启hadoop)
每个可配置多个用户,用户之间用“,”分割;可配置多个用户组,分组之间用“,”分割,用户和分组之间用空格分割,如果只有分组,前面保留一个空格,如:
<property>
<name>security.job.submission.protocol.acl</name>
<value>alice,bobgroup1,group2</value>
</property>
默认情况下,属性不对任何用户和分组开放。
该配置文件可使用以下命令动态加载:
(1) 更新namenode相关属性:bin/hadoop dfsadmin –refreshServiceAcl
(2) 更新jobtracker相关属性:bin/hadoopmradmin –refreshServiceAcl
【利用证明】
攻击Payload:
GET /ws/v1/cluster/info HTTP/1.1
Host: 192.168.10.52:8088
Content-Type: application/json
目标响应结果:
HTTP/1.1 200 OK
Transfer-Encoding: chunked
Cache-Control: no-cache
Content-Type: application/json;charset=utf-8
Date: Fri, 15 Mar 2024 16:55:03 GMT
Date: Fri, 15 Mar 2024 16:55:03 GMT
Expires: Fri, 15 Mar 2024 16:55:03 GMT
Pragma: no-cache
Vary: Accept-Encoding
X-Frame-Options: SAMEORIGIN
2da
{"clusterInfo":{"id":1709705359653,"startedOn":1709705359653,"state":"STARTED","haState":"ACTIVE","rmStateStoreName":"org.apache.hadoop.yarn.server.resourcemanager.recovery.NullRMStateStore","resourceManagerVersion":"3.0.0","resourceManagerBuildVersion":"3.0.0 from c25427ceca461ee979d30edd7a4b0f50718e6533 by andrew source checksum 8b512a64c38be0e0ef28f66e742db5","resourceManagerVersionBuiltOn":"2017-12-08T19:22Z","hadoopVersion":"3.0.0","hadoopBuildVersion":"3.0.0 from c25427ceca461ee979d30edd7a4b0f50718e6533 by andrew source checksum 397832cb5529187dc8cd74ad54ff22","hadoopVersionBuiltOn":"2017-12-08T19:16Z","haZooKeeperConnectionState":"Could not find leader elector. Verify both HA and automatic failover are enabled."}}
0
【修复过程】
vim core-site.xml
启动hadoop