[Terraform] 04 - VPC + EC2 + EBS + RDS
子网内挂载EC2
在第一个子网的地方,创建一个ec2。
resource "aws_instance" "example" { ami = var.AMIS[var.AWS_REGION] instance_type = "t2.micro" # the VPC subnet 确定了"子网" subnet_id = aws_subnet.main-public-1.id # the security group vpc_security_group_ids = [aws_security_group.allow-ssh.id] # 因为是group,所以这里是列表 --> [安全组] # the public SSH key key_name = aws_key_pair.mykeypair.key_name # 在 key.tf中做了定义 --> [SSH Key 配置] }
-
-
安全组
-
instance 绑定上 vpc,以及进一步引用 vpc security 的 设置。
egress,表示流量的出口,这里基本没做限制。
ingress,表示流量的进入。
resource "aws_security_group" "allow-ssh" { vpc_id = aws_vpc.main.id name = "allow-ssh" description = "security group that allows ssh and all egress traffic" egress { from_port = 0 to_port = 0 protocol = "-1" # 对协议不作限制 cidr_blocks = ["0.0.0.0/0"] } ingress { from_port = 22 to_port = 22 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] } tags = { Name = "allow-ssh" } }
-
-
SSH Key 配置
-
resource "aws_key_pair" "mykeypair" { key_name = "mykeypair" public_key = file(var.PATH_TO_PUBLIC_KEY) }
EBS (Elastic Block Store)
以下内容追加在 instance.tf 之后。
resource "aws_ebs_volume" "ebs-volume-1" { availability_zone = "eu-west-1a" size = 20 type = "gp2" tags = { Name = "extra volume data" } }
将 instance 和 ebs volume 关联起来。
resource "aws_volume_attachment" "ebs-volume-1-attachment" { device_name = "/dev/xvdh" volume_id = aws_ebs_volume.ebs-volume-1.id instance_id = aws_instance.example.id }
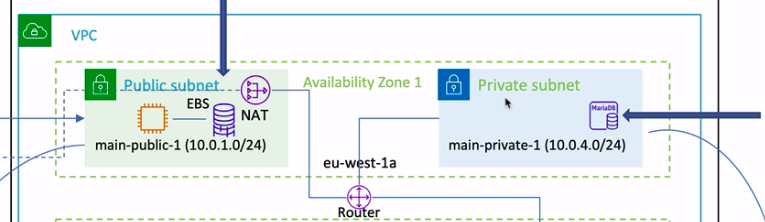
RDS (relational database service)
一、在private subnet中
几种支持的关系数据库选项。

二、rds.tf配置
这里指定了两个private subnet,一个作为“主”,一个作为“从”。
resource "aws_db_subnet_group" "mariadb-subnet" { name = "mariadb-subnet" description = "RDS subnet group" subnet_ids = [aws_subnet.main-private-1.id, aws_subnet.main-private-2.id] }
先定义一个参数组。之后被db的实例所引用。
resource "aws_db_parameter_group" "mariadb-parameters" { name = "mariadb-parameters" family = "mariadb10.1" description = "MariaDB parameter group" parameter { name = "max_allowed_packet" value = "16777216" } }
#------------------------------------------------------------------------------------------ resource "aws_db_instance" "mariadb" { allocated_storage = 100 # 100 GB of storage, gives us more IOPS than a lower number engine = "mariadb" engine_version = "10.1.14" instance_class = "db.t2.small" # use micro if you want to use the free tier identifier = "mariadb" name = "mariadb" username = "root" # username password = var.RDS_PASSWORD # password db_subnet_group_name = aws_db_subnet_group.mariadb-subnet.name parameter_group_name = aws_db_parameter_group.mariadb-parameters.name multi_az = "false" # set to true to have high availability: 2 instances synchronized with each other vpc_security_group_ids = [aws_security_group.allow-mariadb.id] storage_type = "gp2" backup_retention_period = 30 # how long you’re going to keep your backups availability_zone = aws_subnet.main-private-1.availability_zone # prefered AZ skip_final_snapshot = true # skip final snapshot when doing terraform destroy tags = { Name = "mariadb-instance" } }
三、数据库的安全组
除了之前的ssh外,这里又定义了一个 security group for Mariadb数据库。
resource "aws_security_group" "allow-mariadb" { vpc_id = aws_vpc.main.id name = "allow-mariadb" description = "allow-mariadb" ingress { from_port = 3306 to_port = 3306 protocol = "tcp" security_groups = [aws_security_group.allow-ssh.id] # allowing access from our example instance } egress { from_port = 0 to_port = 0 protocol = "-1" cidr_blocks = ["0.0.0.0/0"] self = true } tags = { Name = "allow-mariadb" } }
四、配置结果
11_demo-10_RDS$ terraform apply var.RDS_PASSWORD Enter a value: Unsw2016 aws_ebs_volume.ebs-volume-1: Refreshing state... [id=vol-04ba19620775cf54c] aws_key_pair.mykeypair: Refreshing state... [id=mykeypair] aws_vpc.main: Refreshing state... [id=vpc-00181c505aeaaa8c1] aws_eip.nat: Refreshing state... [id=eipalloc-0dbeb7811d022a409] aws_db_parameter_group.mariadb-parameters: Refreshing state... [id=mariadb-parameters] aws_internet_gateway.main-gw: Refreshing state... [id=igw-0362e58939a7ccab7] aws_subnet.main-public-2: Refreshing state... [id=subnet-0730da3ee6e61349d] aws_subnet.main-public-1: Refreshing state... [id=subnet-0cb36da594c323b9a] aws_subnet.main-private-1: Refreshing state... [id=subnet-088af118755ae9b05] aws_subnet.main-private-2: Refreshing state... [id=subnet-010692fdaf141007f] aws_security_group.allow-ssh: Refreshing state... [id=sg-0323d44f797f7b145] aws_route_table.main-public: Refreshing state... [id=rtb-0d5629c8b9198885c] aws_nat_gateway.nat-gw: Refreshing state... [id=nat-07779d2a71a19f851] aws_db_subnet_group.mariadb-subnet: Refreshing state... [id=mariadb-subnet] aws_security_group.allow-mariadb: Refreshing state... [id=sg-06843b421cdcdbda1] aws_instance.example: Refreshing state... [id=i-01cc3d7bc9e8dc7ad] aws_route_table.main-private: Refreshing state... [id=rtb-02a0baec7ae5659f8] aws_route_table_association.main-public-1-a: Refreshing state... [id=rtbassoc-05af461979ccfe27e] aws_route_table_association.main-public-2-a: Refreshing state... [id=rtbassoc-0e4305bfe44edc8ec] aws_db_instance.mariadb: Refreshing state... [id=mariadb] aws_route_table_association.main-private-1-a: Refreshing state... [id=rtbassoc-04bd9f69502d7a5a1] aws_route_table_association.main-private-2-a: Refreshing state... [id=rtbassoc-0d4ee222399d1c023] aws_volume_attachment.ebs-volume-1-attachment: Refreshing state... [id=vai-2970736263] Apply complete! Resources: 0 added, 0 changed, 0 destroyed. Outputs: instance = 3.231.167.87 rds = mariadb.cqbzk599flky.us-east-1.rds.amazonaws.com:3306
先登录实例,再其上登录mysql。
引申思考:Lambda --> MariaDB时,Lambda和MariaDB是同一个子网么?
End.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号