ida flare_emu模拟执行批量解密字符串(Orchard_Botnet)
🙃前言
在恶意软件对抗中,经常遇到字符串自解密函数,并且大部分使用的频率还不低。如果算法是基本的f(a) = b模式的话,可能首先想到的是动态调试拿解密后字符串,但是这样效率很低。🌚
或者使用ida pyhton来本地写出解密方案,再通过一层层寻找解密相关的传参指令找到需要的input。这种方法比较通用,但是找参数的话可能会遇到字符串传参形式多变的情况。
比如开发者使用堆栈字符串传参,在另一个地方使用动态生成。谁也不想对抗脚本里面全是if else try等...
在早些时候📣曾在kx上发过类似的解密案例。
本次使用的样本是👉360NetLab中的僵尸网络 Orchard 。
md5: cb442cbff066dfef2e3ff0c56610148f。你可以在公众号内回复cb442cbff066获取样本,但是毕竟是恶意样本,请在隔离环境分析运行🤐。
🙏简单分析
我们不去关注样本的其他行为,这不是帖子的主要目的,主要是针对其解密函数位置,把堆中的字符串存放到栈中,然后创建解密对象,传递给解密函数
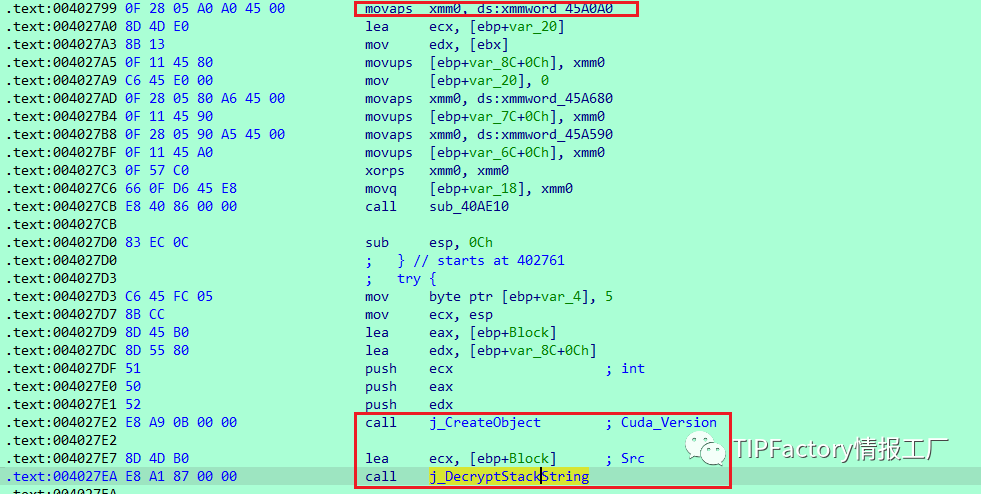
解密函数经过分析复原如下:
def decrypt(data):
alphabet = "!\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyzw"
decrypted = ""
for b in data:
if (b != 0):
decrypted += alphabet[b - 1]
return decrypted
print(decrypt([0x4b,0x45,0x52,0x4e,0x45,0x4c,0x13,0x12,0x0e,0x44,0x4c,0x4c,0x0d]))
结果kernel32.dll。
其中,经过调用分析发现:
EDX指向偏移的首地址
EAX中保存的值减去首地址,除以4就是字符串长度
ECX this 指针
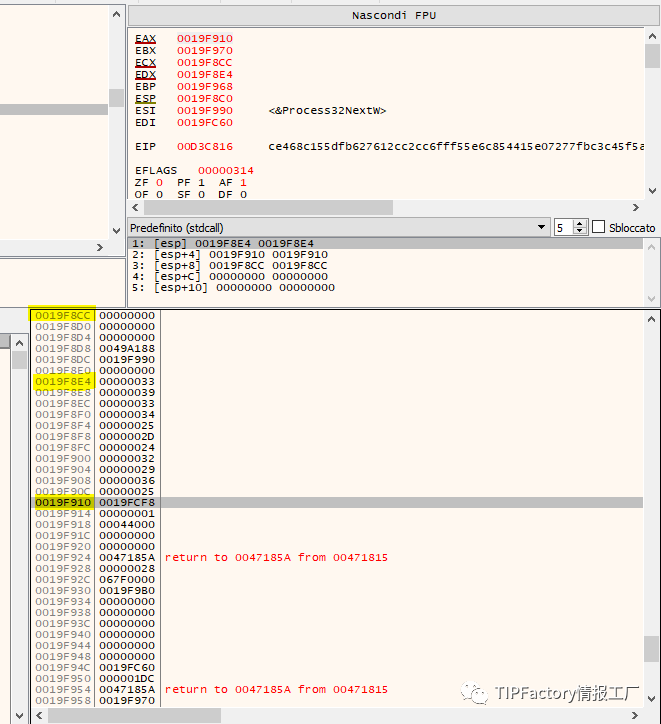
例如,如图所示,EDX指向0x19F8E4,即指向33、39、33、34、25、2D、24、32、29、36、25,这等同于SYSTEMDRIVE字符串。在EAX中,我们有0x19F910,因此(0x19F920–0x19F8E4)/4=11。
代码模拟
我们将使用flare-emu🚩进行代码模拟。安装可以参考官网,很简单。首先要明确我们的需求,解密函数的方法已知了,重要的是搞定参数,脚本如下:
import flare_emu
import binascii
import struct
def iterateCallback(eh, address, argv, userData):
encryptWords = eh.getEmuBytes(argv[0], eh.getRegVal( "eax" ) - eh.getRegVal( "edx" ))
encryptList = [encryptWords[x] for x in range(0, len(encryptWords), 4)]
alphabet = "!\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyzw"
decrypted = ""
for b in encryptList:
if (b != 0):
decrypted += alphabet[b - 1]
eh.analysisHelper.setComment(address,decrypted,False) # 添加注释
# argv[0]:待解密字符串 ,长度如下
# (eh.getRegVal( "eax" ) - eh.getRegVal( "edx" )/4 字符串长度
if __name__ == '__main__':
eh = flare_emu.EmuHelper()
eh.iterate(eh.analysisHelper.getNameAddr("j_CreateObject"), iterateCallback)
🔨 注意使用创建对象的函数模拟,来获取参数j_CreateObject,因为解密函数本体的参数是一个结构体。
运行效果:
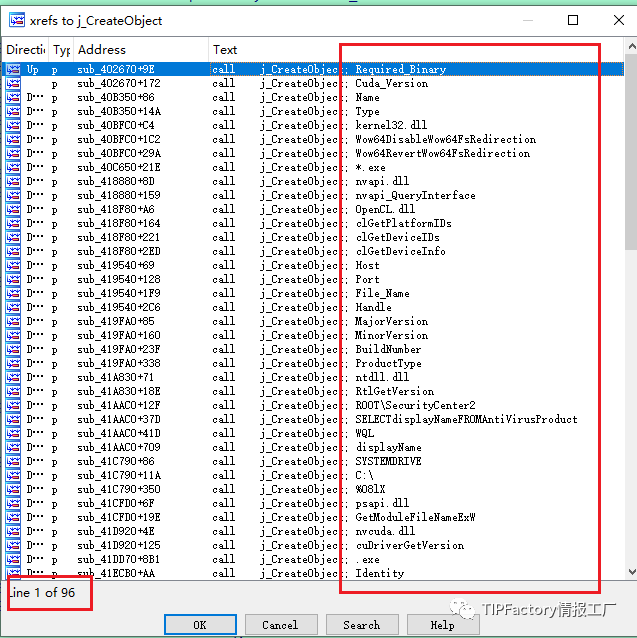
全部字符串:
Direction Type Address Text
Down p sub_421690+78 call j_CreateObject; %04d-%02d-%02d
Down p sub_41C790+350 call j_CreateObject; %08lX
Down p sub_40C650+21E call j_CreateObject; *.exe
Down p sub_421690+F1 call j_CreateObject; .com
Down p sub_421690+C7 call j_CreateObject; .duckdns.org
Down p sub_41DD70+8B1 call j_CreateObject; .exe
Down p sub_421690+11B call j_CreateObject; .net
Down p sub_421690+145 call j_CreateObject; .org
Down p sub_41ECB0+A77 call j_CreateObject; Active_Window
Down p sub_41ECB0+7E3 call j_CreateObject; Antivirus
Down p sub_41ECB0+ED6 call j_CreateObject; Authenticate_Type
Down p sub_4238B0+1AA call j_CreateObject; Binary_Source
Down p sub_4238B0+86 call j_CreateObject; Buffer
Down p sub_424490+A1 call j_CreateObject; Buffer
Down p sub_419FA0+23F call j_CreateObject; BuildNumber
Down p sub_41C790+11A call j_CreateObject; C:\
Down p sub_4223B0+253 call j_CreateObject; CPU_Hashrate
Down p sub_41ECB0+BA9 call j_CreateObject; CPU_Model
Down p sub_4223B0+9A call j_CreateObject; CPU_Status
Down p sub_41ECB0+6F6 call j_CreateObject; Camera
Down p sub_402670+172 call j_CreateObject; Cuda_Version
Down p sub_422C60+7D call j_CreateObject; Domain
Down p sub_41ECB0+4E0 call j_CreateObject; Elevated
Down p sub_4238B0+115 call j_CreateObject; Execute_Name
Down p sub_423C40+8E call j_CreateObject; Execute_Name
Down p sub_423C40+177 call j_CreateObject; Execute_Result
Down p sub_423C40+278 call j_CreateObject; Execute_Result_Type
Down p sub_4238B0+23E call j_CreateObject; Execute_Type
Down p sub_419540+1F9 call j_CreateObject; File_Name
Down p sub_4223B0+4F4 call j_CreateObject; GPU_Algorithm
Down p sub_4223B0+330 call j_CreateObject; GPU_Hashrate
Down p sub_41ECB0+CE6 call j_CreateObject; GPU_Models
Down p sub_4223B0+180 call j_CreateObject; GPU_Status
Down p sub_4223B0+3FA call j_CreateObject; GPU_Type
Down p sub_41CFD0+19E call j_CreateObject; GetModuleFileNameExW
Down p sub_419540+2C6 call j_CreateObject; Handle
Down p sub_424490+128 call j_CreateObject; Handle
Down p sub_419540+69 call j_CreateObject; Host
Down p sub_41ECB0+AA call j_CreateObject; Identity
Down p sub_422C60+58B call j_CreateObject; In_Memory
Down p sub_422C60+747 call j_CreateObject; Install_Path
Down p sub_422C60+4B4 call j_CreateObject; Is_Patched
Down p sub_419FA0+85 call j_CreateObject; MajorVersion
Down p sub_4207F0+84 call j_CreateObject; Message
Down p sub_4240D0+110 call j_CreateObject; Message_Option
Down p sub_424490+1C5 call j_CreateObject; Message_Option
Down p sub_4204B0+168 call j_CreateObject; Message_Type
Down p sub_4207F0+23C call j_CreateObject; Message_Type
Down p sub_4223B0+5C7 call j_CreateObject; Message_Type
Down p sub_422C60+AE6 call j_CreateObject; Message_Type
Down p sub_423C40+355 call j_CreateObject; Message_Type
Down p sub_424270+189 call j_CreateObject; Message_Type
Down p sub_419FA0+160 call j_CreateObject; MinorVersion
Down p sub_40B350+86 call j_CreateObject; Name
Down p sub_418F80+A6 call j_CreateObject; OpenCL.dll
Down p sub_41ECB0+1FD call j_CreateObject; Operating_System
Down p sub_4240D0+6E call j_CreateObject; Option
Down p sub_422C60+669 call j_CreateObject; Patch_Name
Down p sub_419540+128 call j_CreateObject; Port
Down p sub_422C60+142 call j_CreateObject; Port
Down p sub_422C60+A09 call j_CreateObject; Power_SaverMode
Down p sub_4207F0+15F call j_CreateObject; Problem_Type
Down p sub_422C60+220 call j_CreateObject; Process_ID
Down p sub_422C60+2FB call j_CreateObject; Process_Name
Down p sub_422C60+3D6 call j_CreateObject; Process_Path
Down p sub_419FA0+338 call j_CreateObject; ProductType
Down p sub_41AAC0+12F call j_CreateObject; ROOT\SecurityCenter2
Down p sub_41ECB0+DCF call j_CreateObject; Ram_Size
p sub_402670+9E call j_CreateObject; Required_Binary
Down p sub_41A830+18E call j_CreateObject; RtlGetVersion
Down p sub_41AAC0+37D call j_CreateObject; SELECTdisplayNameFROMAntiVirusProduct
Down p sub_41C790+86 call j_CreateObject; SYSTEMDRIVE
Down p sub_4204B0+8E call j_CreateObject; Serial_Number
Down p sub_41ECB0+38B call j_CreateObject; System_Architecture
Down p sub_422C60+82F call j_CreateObject; System_Idle
Down p sub_422C60+916 call j_CreateObject; System_Uptime
Down p sub_41ECB0+5D7 call j_CreateObject; Threads
Down p sub_424270+FB call j_CreateObject; Transfer_Port
Down p sub_40B350+14A call j_CreateObject; Type
Down p sub_424270+60 call j_CreateObject; Type
Down p sub_41ECB0+8FA call j_CreateObject; Version
Down p sub_41AAC0+41D call j_CreateObject; WQL
Down p sub_40BFC0+1C2 call j_CreateObject; Wow64DisableWow64FsRedirection
Down p sub_40BFC0+29A call j_CreateObject; Wow64RevertWow64FsRedirection
Down p sub_418F80+221 call j_CreateObject; clGetDeviceIDs
Down p sub_418F80+2ED call j_CreateObject; clGetDeviceInfo
Down p sub_418F80+164 call j_CreateObject; clGetPlatformIDs
Down p sub_41D920+125 call j_CreateObject; cuDriverGetVersion
Down p sub_41AAC0+709 call j_CreateObject; displayName
Down p sub_421690+2A5 call j_CreateObject; https://blockchain.info/balance?active=1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa
Down p sub_40BFC0+C4 call j_CreateObject; kernel32.dll
Down p sub_41A830+71 call j_CreateObject; ntdll.dll
Down p sub_418880+8D call j_CreateObject; nvapi.dll
Down p sub_418880+159 call j_CreateObject; nvapi_QueryInterface
Down p sub_41D920+4E call j_CreateObject; nvcuda.dll
Down p sub_41CFD0+6F call j_CreateObject; psapi.dll



