zabbix3.4 low level discovery功能
zabbix3.4 low level discovery功能
业务需求:由于公司业务比较多,需要监控java项目进程,故使用了ZABBIX LLD 功能
1.在zabbix客户端上面添加相应获取进程以及项目名称的脚本
[root@UX206-CSP1 script]# cat /usr/local/script/zabbix_lld.sh
#!/bin/bash
#user: pb
#low-level discovery
java()
{
port=(`sudo ss -anlp | awk -F"[ :]+" '/java/ {print $5}'`)
max_port=$[${#port[@]}-1]
#echo $max_port
printf '{\n'
printf '\t"data":['
for key in ${!port[@]}
do
java_pid=`sudo ss -anlp | grep ${port[$key]} | awk -F"[ :]+" '/java/ {print $9}' | awk -F "[(\",]+" '{print $3}'`
JAVA_NAME=`sudo ps -ef | grep $java_pid | grep -v grep | awk -F "/usr/local/" '{print $3}' | cut -d '/' -f1`
printf '\n\t\t{\n'
#printf "\"{$JAVA_NAME}\":\"${port[$key]}\"}"
printf "\t\t\t\"{#JAVANAME}\":\"${JAVA_NAME}\","
printf '\n'
printf "\t\t\t\"{#JAVAPORT}\":${port[$key]}"
printf '\n\t\t}'
if [ $key -ne $max_port ]
then
printf ","
fi
done
printf '\n\t]'
printf '\n}'
}
case "$1" in
discovery)
java;;
esac
由于脚本中用到了 ss -anlp命令,获取结果时,是用zabbix用户在获取,故需要给zabbix相应的权限
[root@UX206-CSP1 script]# grep "zabbix" /etc/sudoers #User_Alias ZABBIX=zabbix zabbix ALL=(root) NOPASSWD:/bin/,/usr/bin/,/usr/sbin/
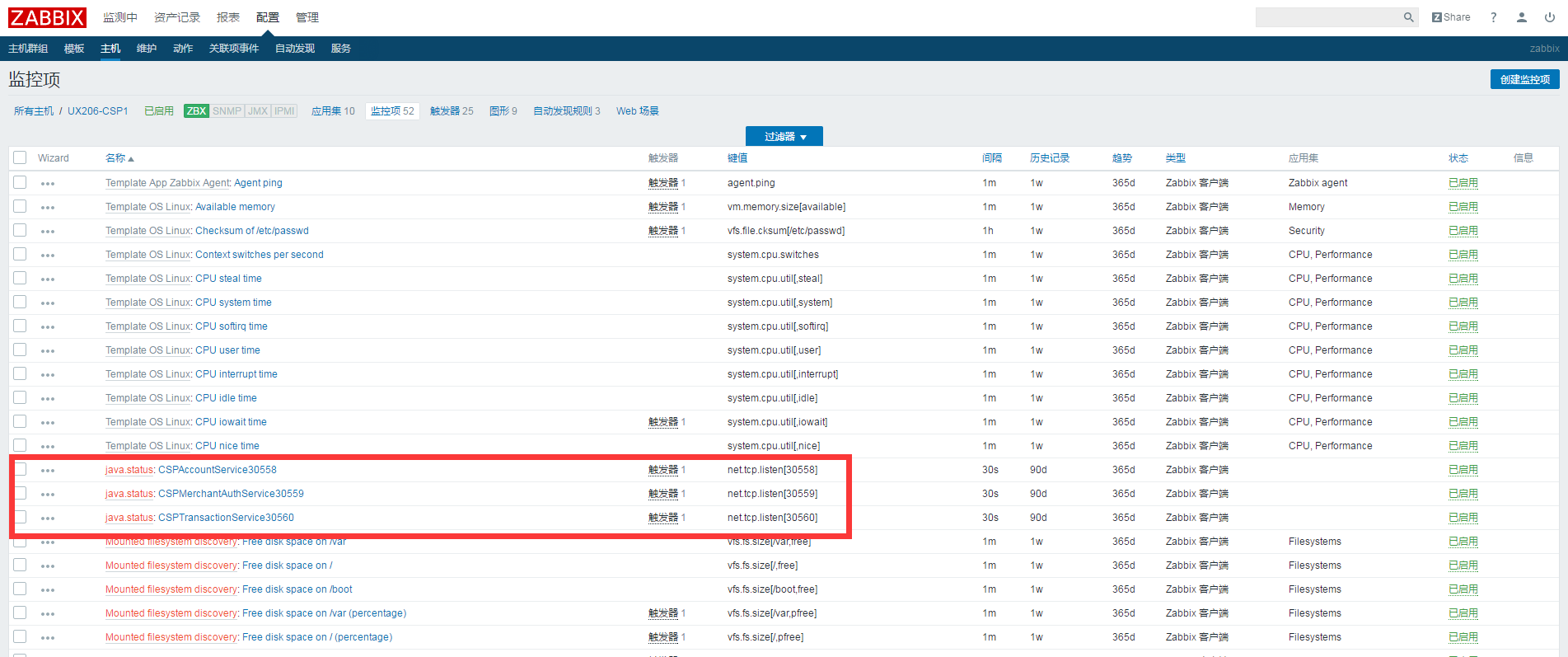
执行脚本得到的结果为
[root@UX206-CSP1 script]# sudo -u zabbix ./zabbix_lld.sh discovery
{
"data":[
{
"{#JAVANAME}":"CSPAccountService",
"{#JAVAPORT}":30558
},
{
"{#JAVANAME}":"CSPMerchantAuthService",
"{#JAVAPORT}":30559
},
{
"{#JAVANAME}":"CSPTransactionService",
"{#JAVAPORT}":30560
}
]
}
就是以一个json格式打印的结果
2.zabbix客户端配置文件
UnsafeUserParameters=1 UserParameter=java.status,/usr/local/script/zabbix_lld.sh discovery
配置自定义的key为java.status,重启zabbix客户端
3.从zabbix server端来取对应的值是否正常
[root@hk-vsan1-zabbix ~]# /usr/local/zabbix/bin/zabbix_get -s 10.20.209.11 -p 10050 -k "java.status"
{
"data":[
{
"{#JAVANAME}":"CSPAccountService",
"{#JAVAPORT}":30558
},
{
"{#JAVANAME}":"CSPMerchantAuthService",
"{#JAVAPORT}":30559
},
{
"{#JAVANAME}":"CSPTransactionService",
"{#JAVAPORT}":30560
}
]
}
4.配置zabbix server
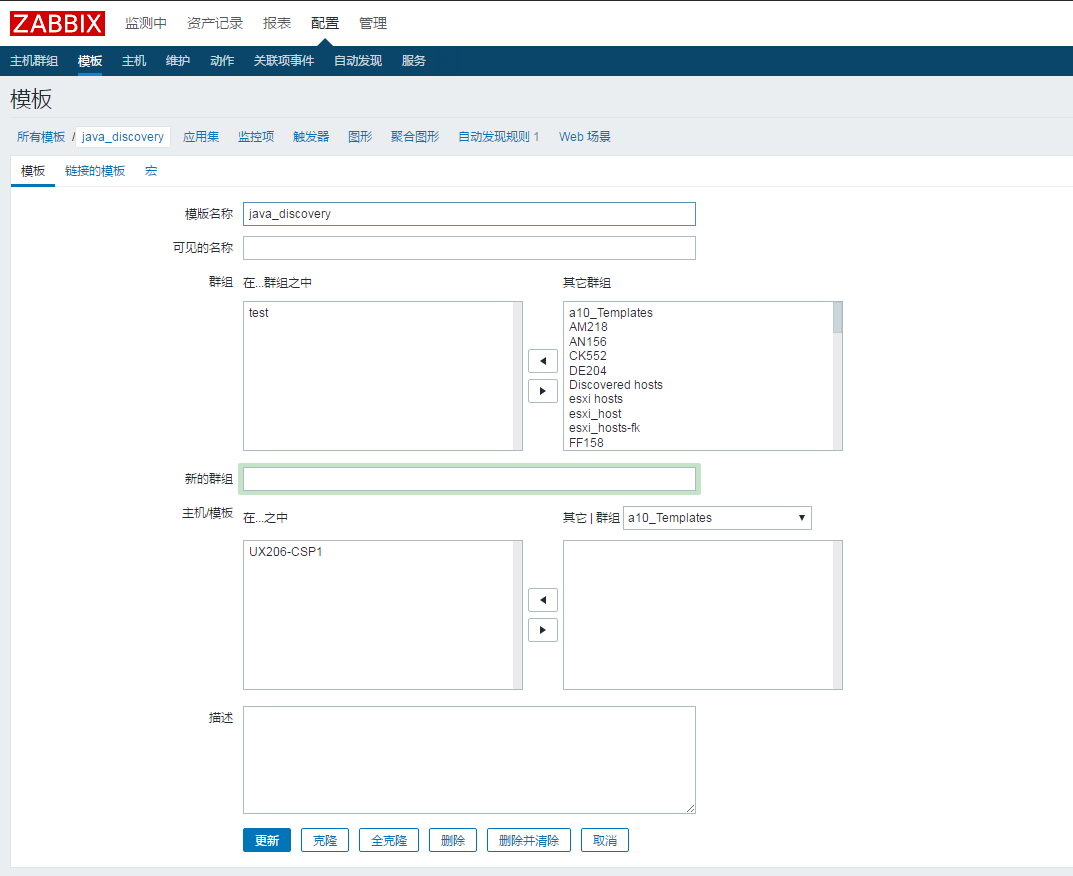
新建模板

添加组以及哪些主机在这个模板下面
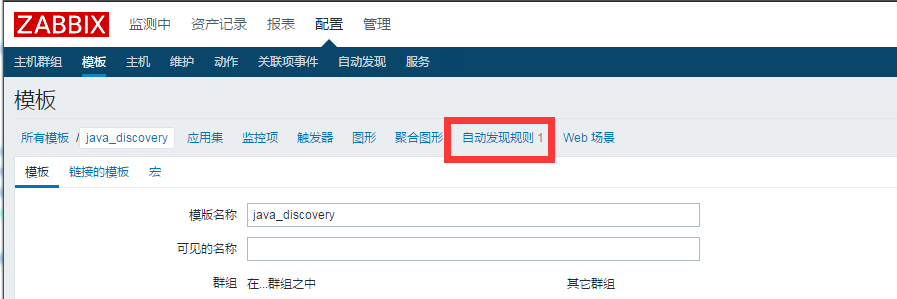
添加自动发现规则
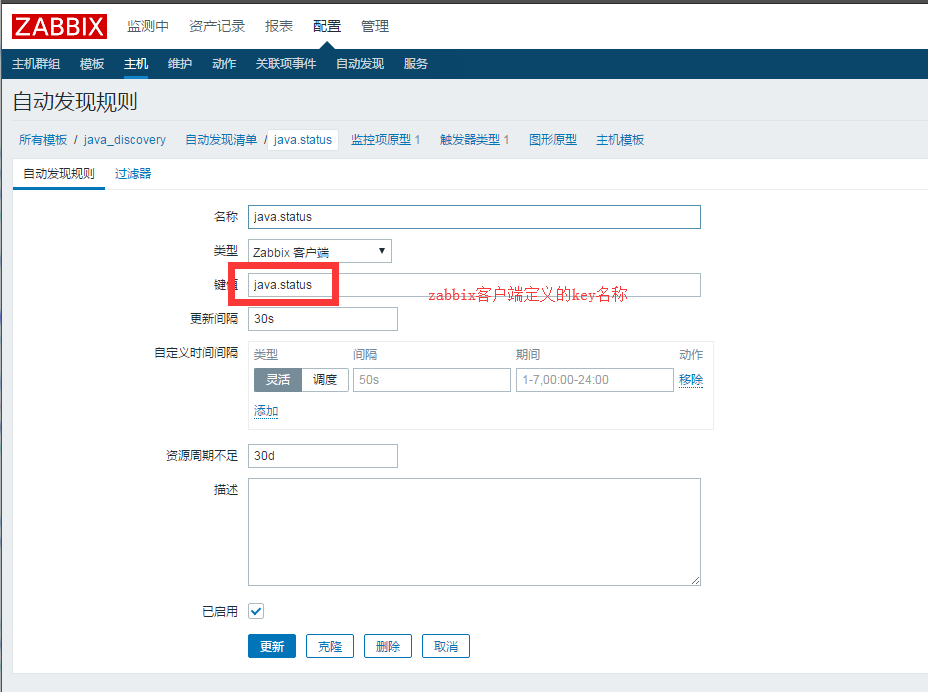
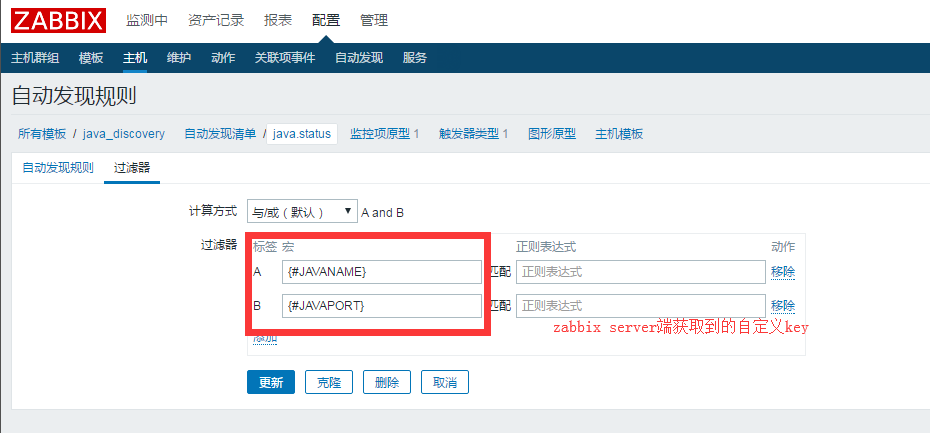
添加监控项原型

添加触发器原型

到此,zabbix server端已经添加完成,查看监控的客户端机器