Hackthebox 靶机Appointment攻略
今天继续闯关,依然用Kali Linux作为渗透测试平台,利用OpenVPN以及此前所下载的配置文件建立与Hackthebox的VPN连接,并得到Appointment实例的IP地址。
# openvpn starting_point_jasonhuawen.ovpn
Task 1: What does the acronym SQL stand for?
答案: Structured Query Language
Task 2: What is one of the most common type of SQL vulnerabilities?
答案: SQL injection
Task 3: What does PII stand for?
思路: Google一下,还是比较有名的数据保护条例
答案:Personally Identifiable Information
Task 4: What does the OWASP Top 10 list name the classification for this vulnerability?
思路: 整的SQL注入漏洞类别名称”与上面那道题一样只能Google了。
答案: A03:2021-Injection
Task 5: What service and version are running on port 80 of the target?
思路: 用扫描神器nmap
# nmap -sV 10.129.2.114 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-01 00:45 EDT Nmap scan report for 10.129.2.114 Host is up (0.19s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.38 ((Debian)) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 15.67 seconds
答案: Apache httpd 2.4.38 ((Debian))
Task 6: What is the standard port used for the HTTPS protocol?
答案: 443
Task 7: What is one luck-based method of exploiting login pages?
答案: brute-forcing
Task 8: What is a folder called in web-application terminology?
答案: directory
Task 9: What response code is given for "Not Found" errors?
答案: 404
Task 10: What switch do we use with Gobuster to specify we're looking to discover directories, and not subdomains?
思路:看题目就知道是问Gobuster工具哪个选项是用于发现目录而不是子域名,那简单gobuster -h看一下帮助即可,不过竟然我手上的kali Linux版本没有默认安装,不过安全很简单,只需要:
#apt install gobuster
# gobuster -h Usage: gobuster [command] Available Commands: dir Uses directory/file enumeration mode dns Uses DNS subdomain enumeration mode fuzz Uses fuzzing mode help Help about any command s3 Uses aws bucket enumeration mode version shows the current version vhost Uses VHOST enumeration mode Flags: --delay duration Time each thread waits between requests (e.g. 1500ms) -h, --help help for gobuster --no-error Don't display errors -z, --no-progress Don't display progress -o, --output string Output file to write results to (defaults to stdout) -p, --pattern string File containing replacement patterns -q, --quiet Don't print the banner and other noise -t, --threads int Number of concurrent threads (default 10) -v, --verbose Verbose output (errors) -w, --wordlist string Path to the wordlist
答案: dir
Task 11: What symbol do we use to comment out parts of the code?
答案: #
接下来又是一些基础知识相关的题目。
这个题目需要用到gobuster工具,不过竟然我手上的kali Linux版本没有默认安装,不过安全很简单,只需要:
#apt install gobuster
然后根据题目的要求,用-h选项,找到问题的答案:
最后一道题需要拿到flag,不过从前面的扫描可以知道,只有一个80端口是开放的,因此通过浏览器访问该网站:
因为题目中提到了gobuster工具,所以自然而言就想到用gobuster去扫描一下有没有敏感目录或者文件
# gobuster dir -u http://10.129.13.28 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
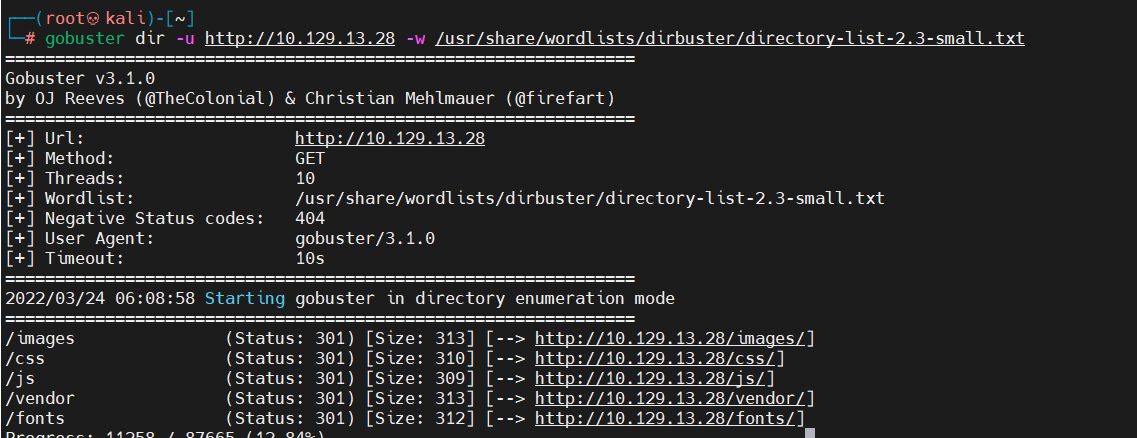
在检查了网络目录后,我们没有发现任何有用的信息。输出中显示的结果代表大多数网站的默认目录,并且大多数情况下,它们不包含可能以任何方式被攻击者利用或有用的文件。
由于 Gobuster 没有发现任何有用的东西,我们需要检查常见的用户名密码看能否成功登录例如:
admin:admin
guest:guest
user:user
root:root
administrator:password
在尝试了所有这些组合之后,我们仍然无法登录。假设我们可以使用工具来尝试暴力破解登录页面。 但是,这将花费很多时间,并且可能会触发安全措施。
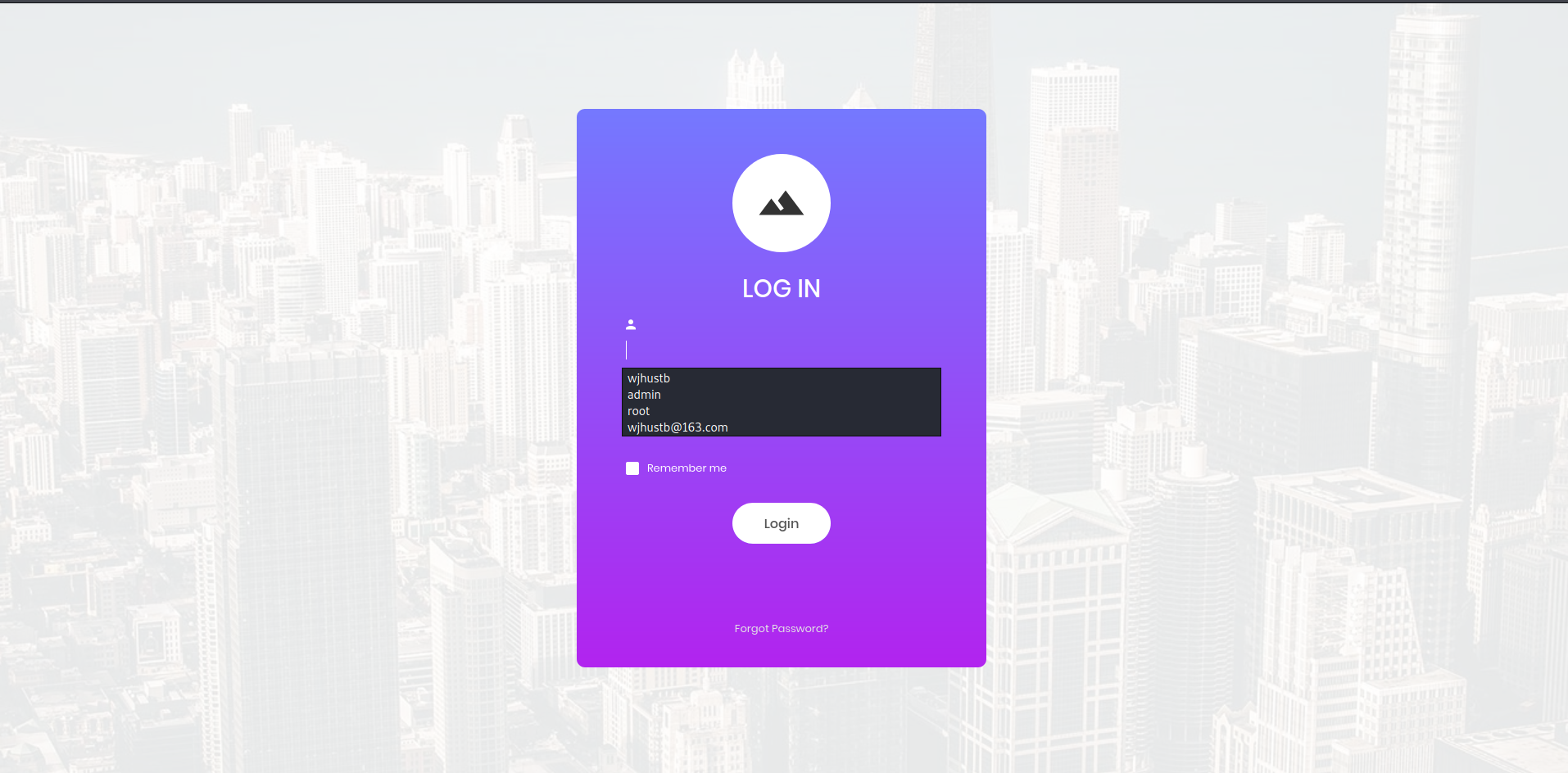
同时由于前面的题目中也提到了注入漏洞,因此下一个明智的策略是测试登录表单是否存在可能的 SQL 注入漏洞。
Username: admin'#
password:
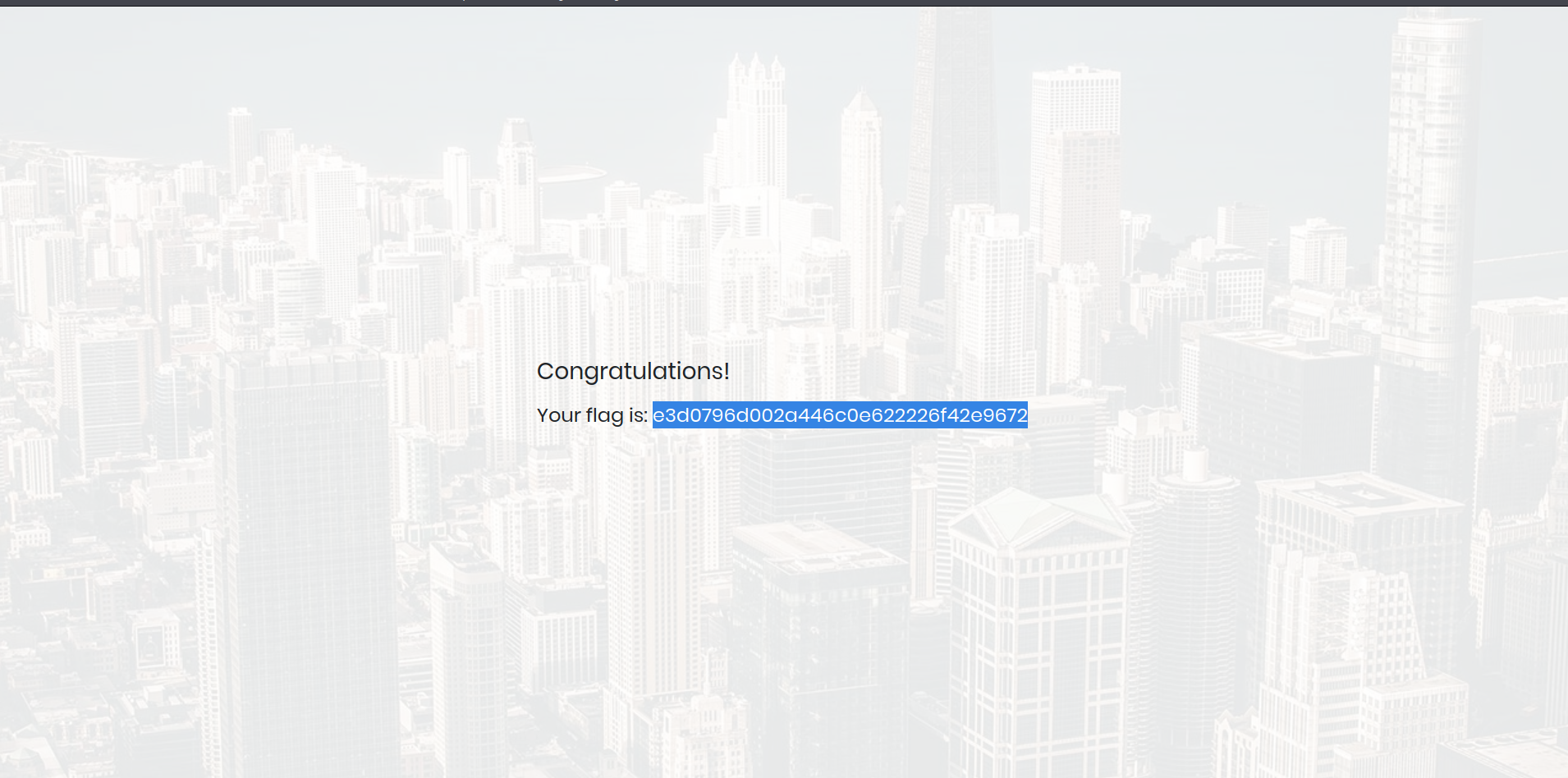
结果发现可以成功登陆并拿到flag.






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了