Hackthebox Fawn解题过程详解
目标靶机:Fawn
题目难度:very easy
依然使用Kali Linux作为Pentest的操作系统,在Kali Linux首先通过openvpn以及此前下载的VPN配置文件建立VPN连接:
# openvpn starting_point_XXXXX.ovpn
然后回到Hackthebox网站,并启动Fawn目标机,Hackthebox网站会显示其目标地址,如下图绿色字体部分所示:
接下来需要回答一些基础题目:(答案可见图片里)
Task 1: What does the 3-letter acronym FTP stand for?
答案: File Transfer Protocol
Task 2: What communication model does FTP use, architecturally speaking?
答案:Client-Server model
Task 3: What is the name of one popular GUI FTP program?
答案:FileZilla
Task 4: Which port is the FTP service active on usually?
答案:21 TCP
Task 5: What acronym is used for the secure version of FTP?
答案:SFTP
Task 6: What is the command we can use to test our connection to the target?
答案: ping
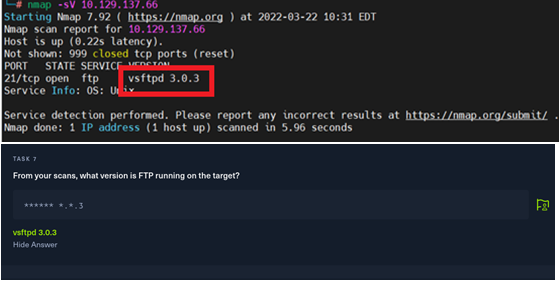
Task 7: From your scans, what version is FTP running on the target?
思路:此题nmap神器了: :
#nmap -sV 10.129.137.66
答案:vsftpd 3.0.3
Task 8: From your scans, what OS type is running on the target?
答案:UNIX
最后一道题,需要拿flag,这里我走了一些弯路,虽然从上面的nmap扫描可以得到vsftpd的版本3.0.3,但是似乎对应这个版本的漏洞不多,只有一个拒绝服务的漏洞。
事实上用加强的nmap去扫描会有另外的惊喜
# nmap -A 10.129.137.66 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-30 08:08 EDT Nmap scan report for 10.129.98.73 Host is up (0.18s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 | ftp-syst: | STAT: | FTP server status: | Connected to ::ffff:10.10.14.115 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | At session startup, client count was 4 | vsFTPd 3.0.3 - secure, fast, stable |_End of status | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_-rw-r--r-- 1 0 0 32 Jun 04 2021 flag.txt No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.92%E=4%D=3/30%OT=21%CT=1%CU=39197%PV=Y%DS=2%DC=T%G=Y%TM=6244486 OS:F%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)SEQ OS:(SP=108%GCD=1%ISR=10C%TI=Z%CI=Z%TS=A)OPS(O1=M505ST11NW7%O2=M505ST11NW7%O OS:3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11NW7%O6=M505ST11)WIN(W1=FE88%W2= OS:FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M505NNSN OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Network Distance: 2 hops Service Info: OS: Unix
从这个扫描结果可以看出,这个ftp服务器配置有问题,允许匿名访问,接下就简单了 ftp登录到该服务器,flag就在登录所在的目录中。
#ftp 10.129.98.73 Connected to 10.129.98.73. 220 (vsFTPd 3.0.3) Name (10.129.98.73:root): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 0 0 32 Jun 04 2021 flag.txt 226 Directory send OK.






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· 【自荐】一款简洁、开源的在线白板工具 Drawnix