Hackthebox 第0关(Meow)解题过程详解
写在前面,虽然第0关(Meow)很简单,但是对于从来没接触过此类题目的同学可能一开始有些发蒙,因此这里将详细的相关解题步骤都贴出来以供参考。
建议选择使用Kali Linux作为渗透测试平台,在Hackthebox网站(https://hackthebox.com/)注册账号以后,按照下述的步骤进行解题:
第一步:在Kali Linux安装openvpn,比较简单:
# apt install openvpn
第二步:在Hackthebox网站上开始第0关解题,按照步骤,首先进行连接,在连接之前需要下载VPN配置文件,如下图所示:
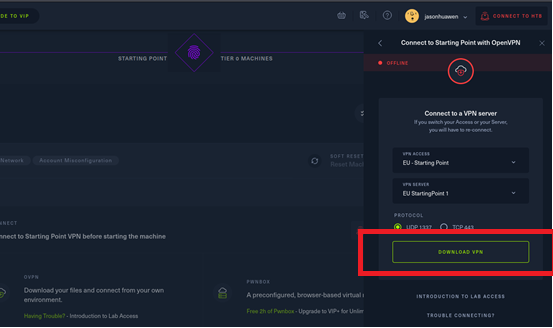
下载VPN配置文件后,可将该配置文件移到root目录
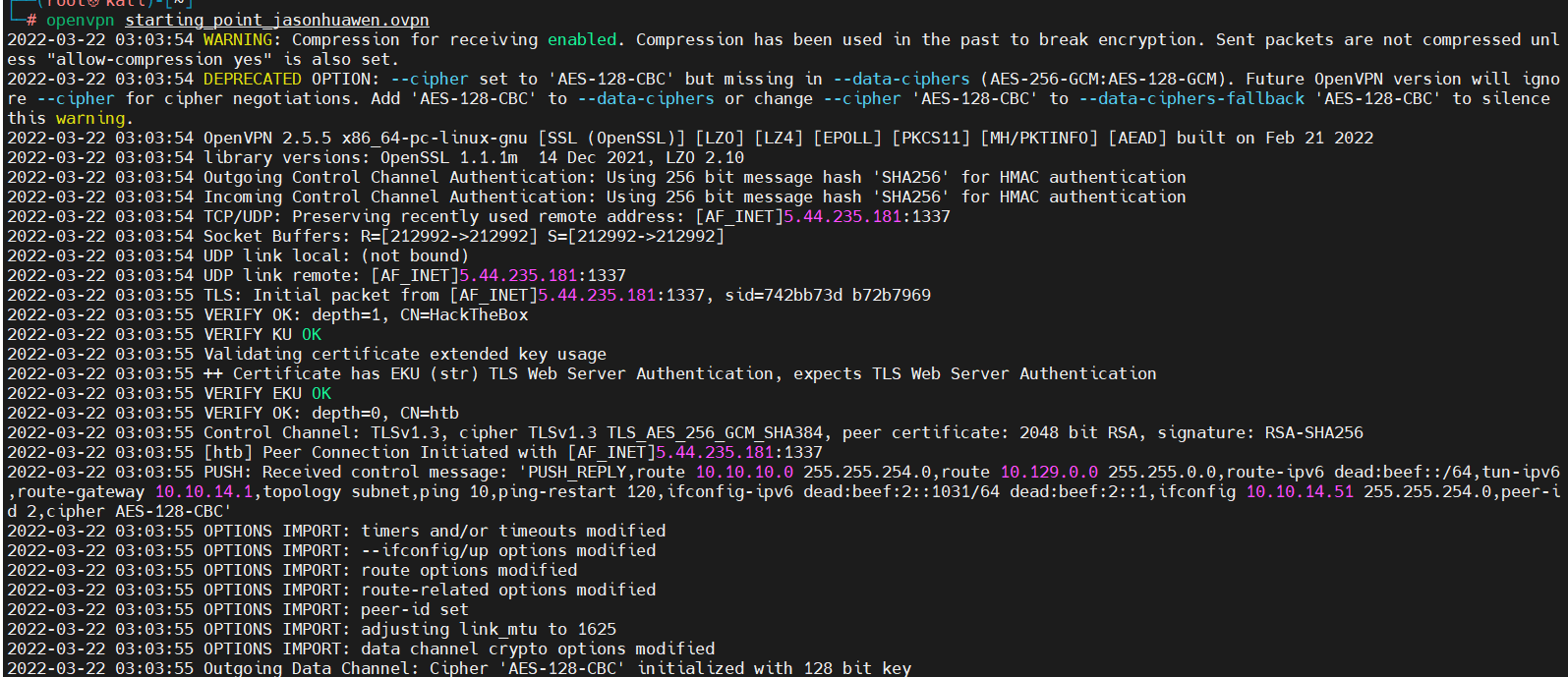
第三步:利用openvpn以及所下载的VPN配置文件进行连接,如果没有报错即表明连接成功:
#openvpn staring_point_jasonhuawen.ovpn
(配置文件名称会根据每个人账号不同而不同)
连接成功以后,在Hackthebox网站上即显示已连接,并且给出目标的IP地址(绿色字体部分),用户可重启或者重置该目标机器。
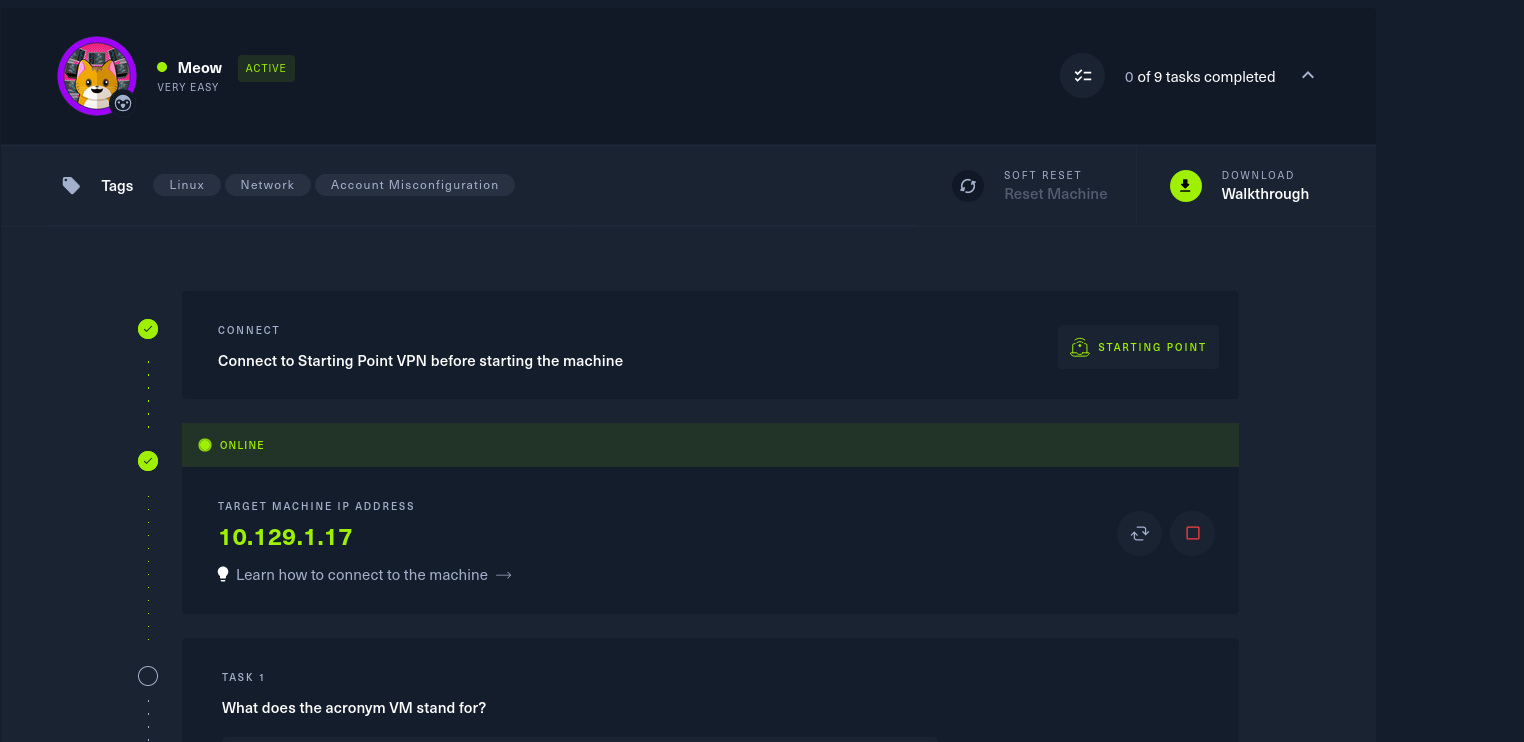
第四步:由于不清楚目标运行什么服务,因此用nmap进行扫描,根据扫描结果可以得知,该目标仅运行telnet服务(这点很重要).

第五步:回到Hackthebox网站继续答题,相对来说都是比较简单的题目:
Task 1:What does the acronym VM stand for?
答案:virtual machine (提交答案,如果错误,会有提示)
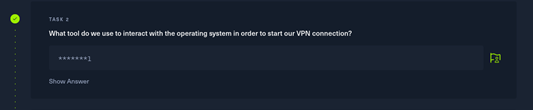
Task 2: What tool do we use to interact with the operating system in order to start our VPN connection?
答案:Terminal
Task 3: What service do we use to form our VPN connection?
答案:Openvpn
Task 4: What is the abreviated name for a tunnel interface in the output of your VPN boot-up sequence output?
答案:tun (从ifconfig 或者openvpn建立连接时的输出也可以得到答案)
Task 5: What tool do we use to test our connection to the target?
答案:Ping
Task 6: What is the name of the tool we use to scan the target's ports?
答案:nmap (扫描神器)
Task 7: What service do we identify on port 23/tcp during our scans?
思路:用namp扫描一下目标即可知道开放的端口以及相应的服务。
#nmap -sS 10.129.1.17 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-29 23:44 EDT Nmap scan report for 10.129.1.17 Host is up (0.19s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 23/tcp open telnet
答案:Telnet
Task 8: What username ultimately works with the remote management login prompt for the target?
思路:由于目标只运行一种服务:telnet,那就试试咯,结果发现root竟然没让输入密码即可登陆了:
└─# telnet 10.129.1.17 Trying 10.129.1.17... Connected to 10.129.1.17. Escape character is '^]'. ls^M █ █ ▐▌ ▄█▄ █ ▄▄▄▄ █▄▄█ ▀▀█ █▀▀ ▐▌▄▀ █ █▀█ █▀█ █▌▄█ ▄▀▀▄ ▀▄▀ █ █ █▄█ █▄▄ ▐█▀▄ █ █ █ █▄▄ █▌▄█ ▀▄▄▀ █▀█ Meow login: root Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Wed 30 Mar 2022 03:58:49 AM UTC System load: 0.0 Usage of /: 41.7% of 7.75GB Memory usage: 4% Swap usage: 0% Processes: 136 Users logged in: 0 IPv4 address for eth0: 10.129.1.17 IPv6 address for eth0: dead:beef::250:56ff:feb9:4ed * Super-optimized for small spaces - read how we shrank the memory footprint of MicroK8s to make it the smallest full K8s around. https://ubuntu.com/blog/microk8s-memory-optimisation 75 updates can be applied immediately. 31 of these updates are standard security updates. To see these additional updates run: apt list --upgradable The list of available updates is more than a week old. To check for new updates run: sudo apt update Last login: Mon Sep 6 15:15:23 UTC 2021 from 10.10.14.18 on pts/0
Submit root flag
因为毕竟是第0关,所以比较简单,用telnet登陆以后,ls列出目录文件,结果发现flag.txt就在那里,都不用麻烦的搜索。
root@Meow:~# ls flag.txt snap root@Meow:~# cat flag.txt b40abdfe23665f766f9c61ecba8a4c19






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· 【自荐】一款简洁、开源的在线白板工具 Drawnix