华为AirEngine 5760-22W Web示例(V200R021C00SPC200版本):NAT网关模式(DHCP方式入网)【胖AP+上层网络】和NAT网关模式(静态IP方式入网)【胖AP+上层网络】配置方法
说明:此版本存在一些默认的WLAN无线业务配置,AP上电启动后,默认创建名称为“HUAWEI-XXXX”的SSID,其中XXXX是AP MAC地址的后四位。默认无线业务覆盖使用无认证方式,用户搜索到该SSID之后,无需输入密码就可以成功关联该无线网络。本示例是在其默认配置的基础上提供一些常见配置的修改操作步骤。
业务需求
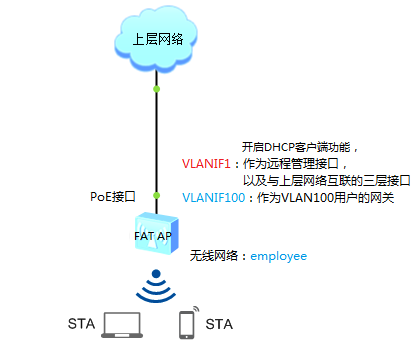
企业已经部署了有线上网方式的网络,现需要将FAT AP以DHCP方式接入网络,并做为STA的网关,为员工提供无线上网服务。
拓扑简图
操作步骤
一、登录到FAT AP的Web界面
使用网线通过浏览器登录胖AP的Web网管
https://forum.huawei.com/enterprise/zh/thread-637631.html
二、进入配置页面
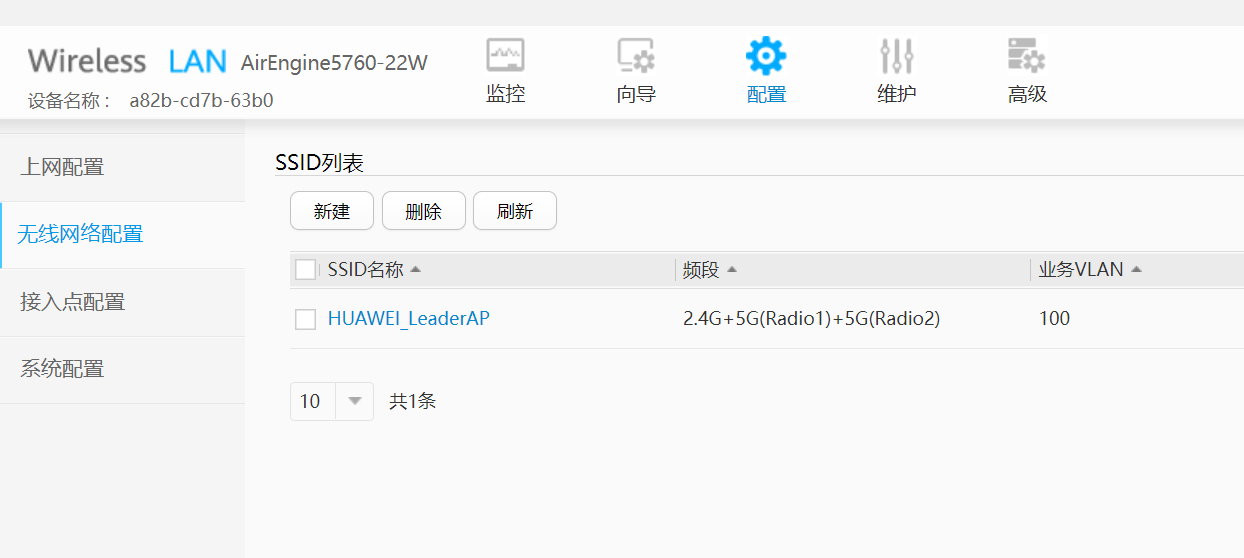
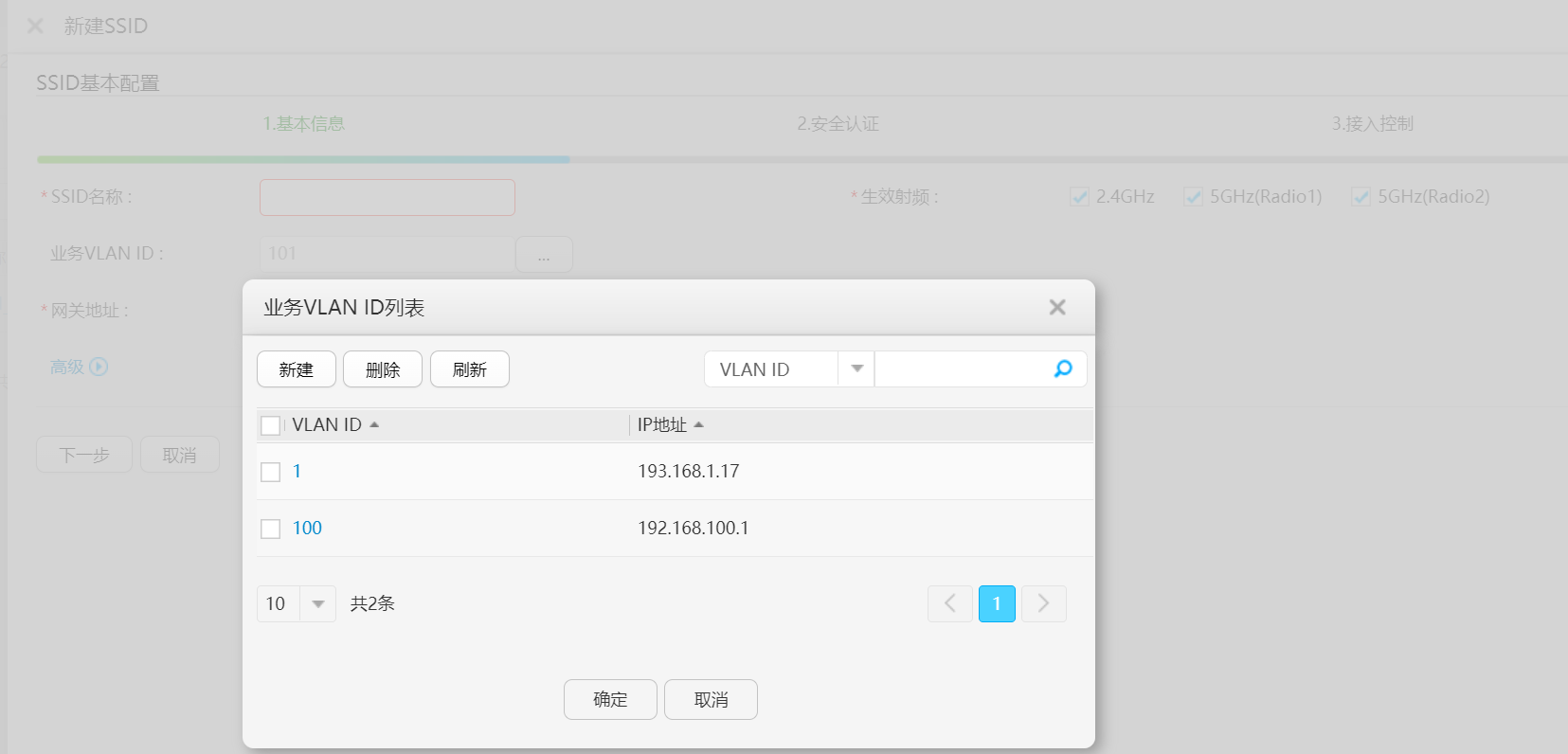
登录WEB网管进入“配置”页面,可以参照下面的步骤进入配置页面中的“无线网络配置”页面。在SSID列表里新建SSID名称,业务VLAN ID :新建AP用户要使用的VLANID并创建VLANIF接口IP即可,然后下一步,进行安全认证和接入控制设置完成即可。
(1)参照下图根据实际情况配置基本信息,单击“应用”。
三、进入维护页面
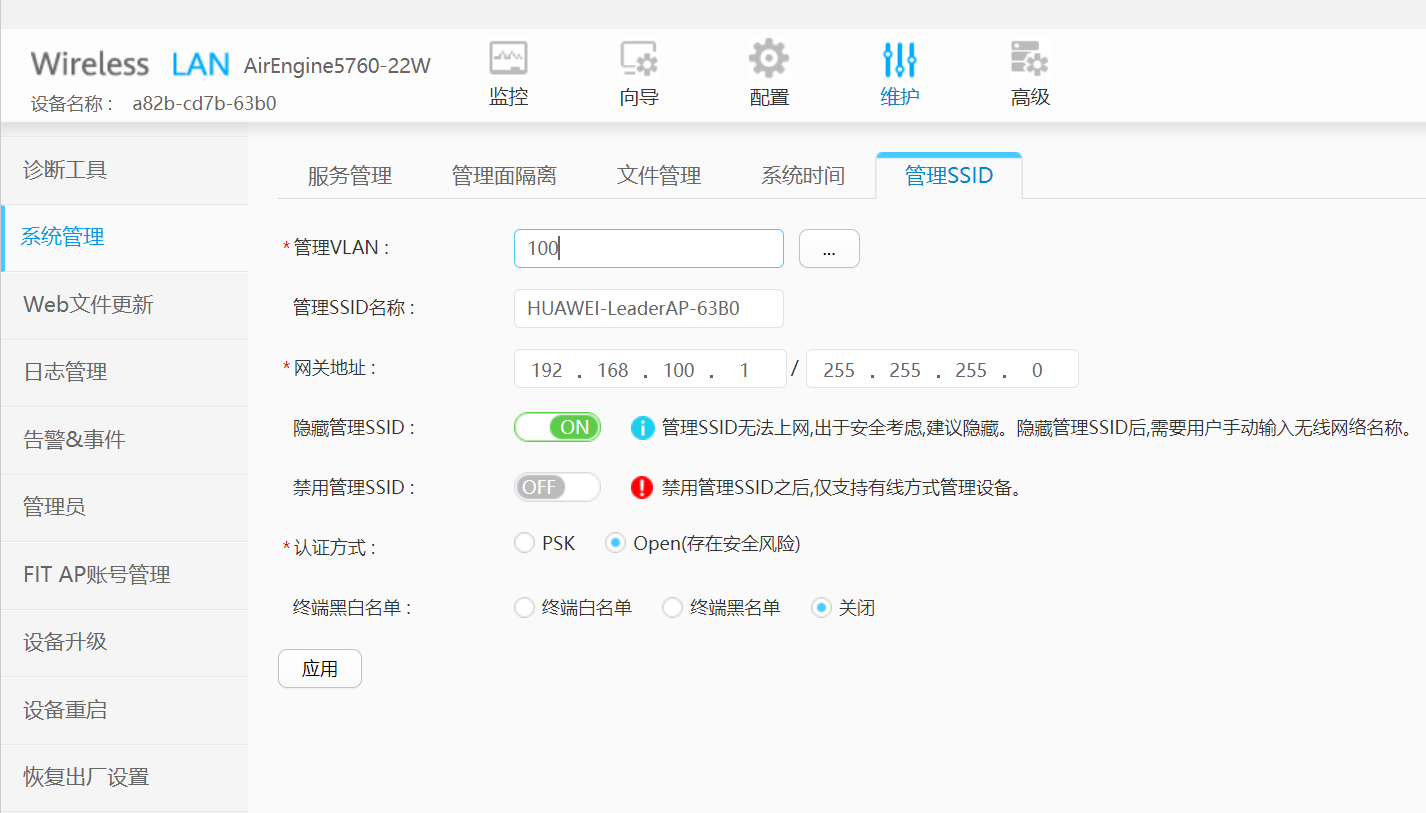
进入维护页面的系统管理,将管理SSID隐藏或者删除。
四、最后保存配置
NAT网关模式(静态IP方式入网)【胖AP+上层网络】
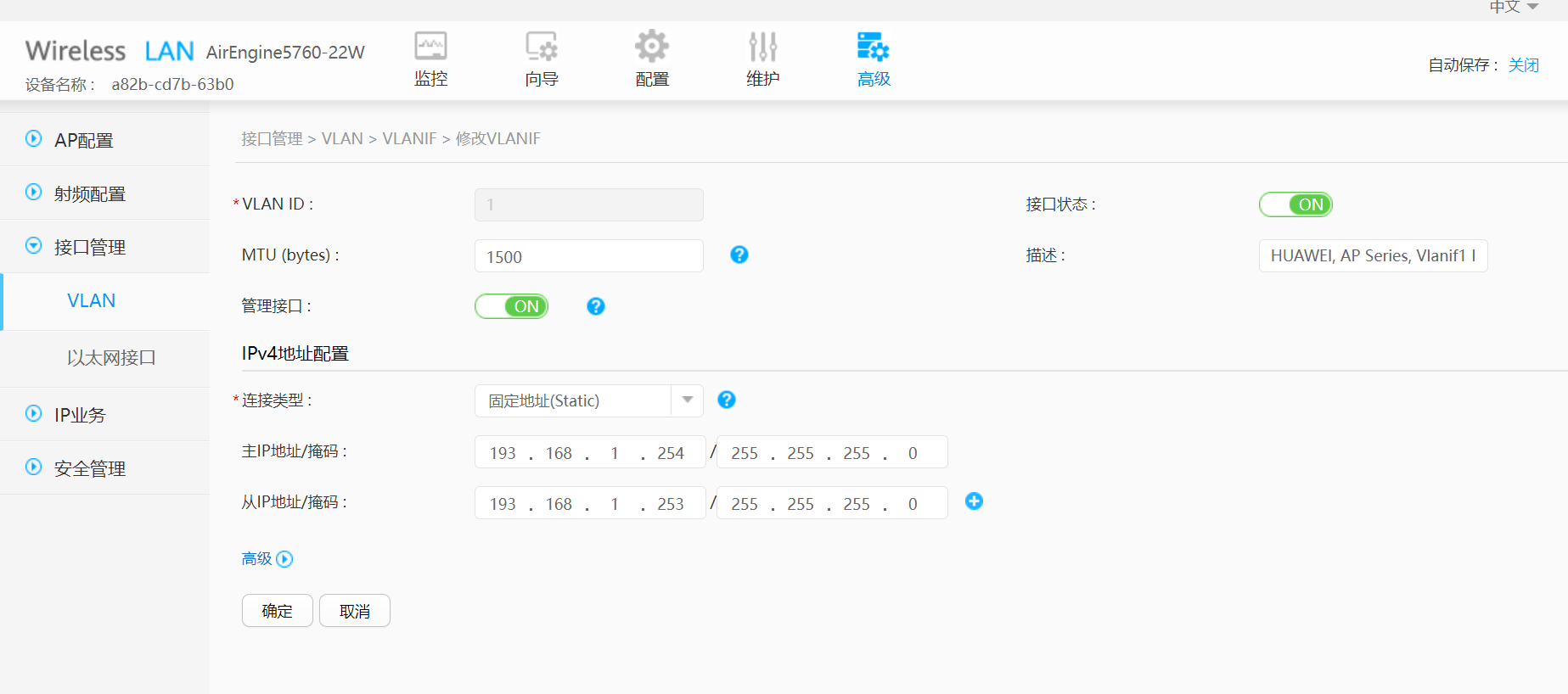
1、修改静态IP方式入网的关键是修改VLAN1的接口地址
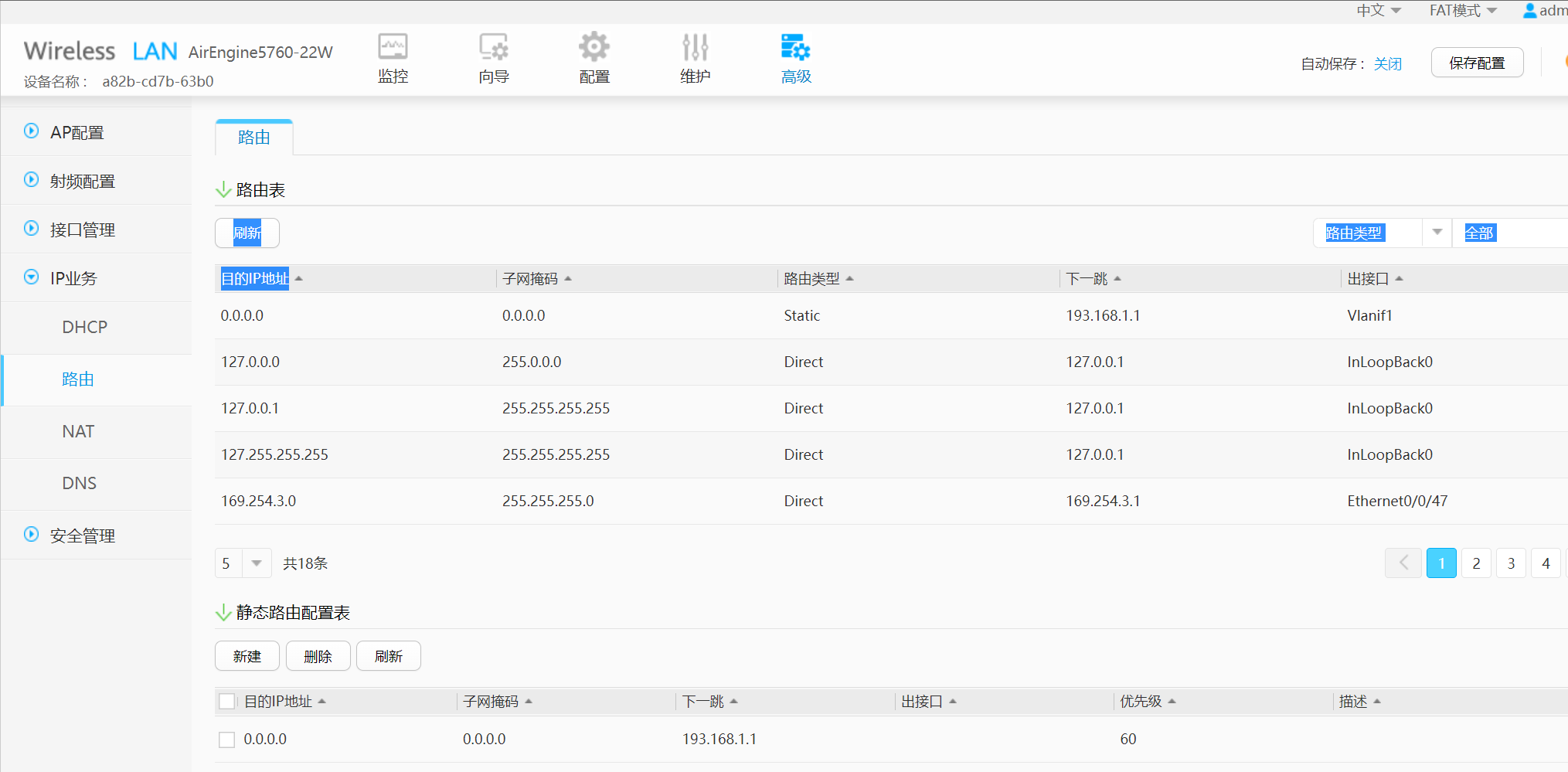
2、新建静态路由
0.0.0.0 0.0.0.0 193.168.1.1
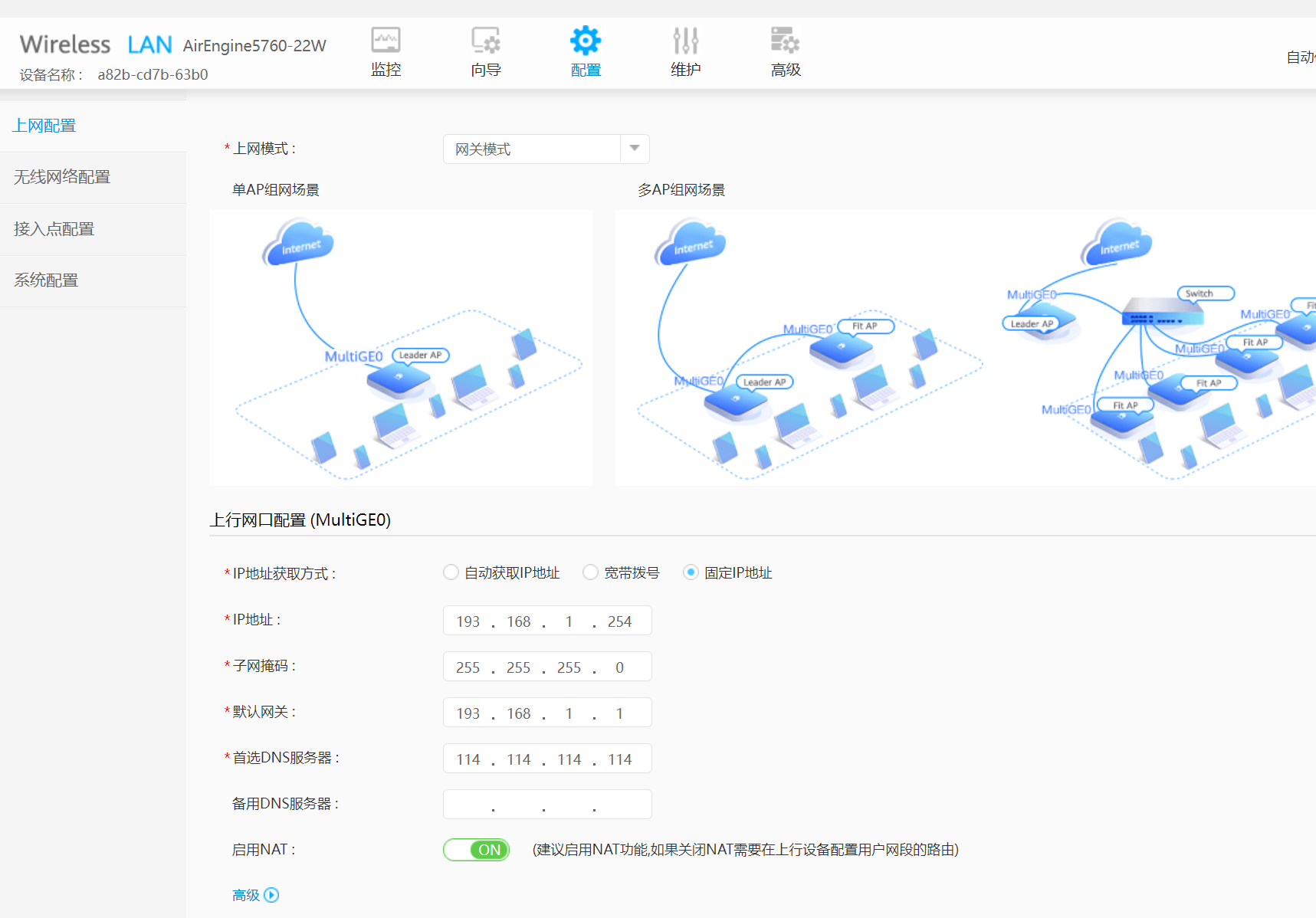
3、在配置页面的上网配置页面 启用NET 开启
1 <a82b>dis current- 2 Software Version V200R021C00SPC200 3 # 4 http secure-server ssl-policy default_policy 5 http server enable 6 # 7 clock timezone Beijing add 08:00:00 8 # 9 vlan batch 100 200 10 # 11 authentication-profile name default_authen_profile 12 authentication-profile name dot1x_authen_profile 13 authentication-profile name mac_authen_profile 14 authentication-profile name macportal_authen_profile 15 authentication-profile name portal_authen_profile 16 # 17 dns resolve 18 dns server 114.114.114.114 19 dns proxy enable 20 # 21 dhcp enable 22 # 23 radius-server template default 24 # 25 pki realm defaultPki_houp 26 certificate-check none 27 pki realm default 28 certificate-check none 29 # 30 ssl policy default_policy type server 31 pki-realm default 32 version tls1.2 33 ciphersuite ecdhe_rsa_aes128_gcm_sha256 ecdhe_rsa_aes256_gcm_sha384 34 ssl policy https type client 35 pki-realm default 36 version tls1.2 37 server-verify enable 38 prefer-ciphersuite ecdhe_rsa_aes128_gcm_sha256 ecdhe_rsa_aes256_gcm_sha384 39 ssl policy defaultPolicy_houp type client 40 pki-realm defaultPki_houp 41 version tls1.2 42 server-verify enable 43 prefer-ciphersuite ecdhe_rsa_aes128_gcm_sha256 ecdhe_rsa_aes256_gcm_sha384 44 # 45 acl name nat 2000 46 rule 1 permit 47 acl number 2001 48 rule 5 permit 49 # 50 free-rule-template name default_free_rule 51 # 52 portal-access-profile name portal_access_profile 53 # 54 aaa 55 authentication-scheme default 56 authentication-mode local 57 authentication-scheme radius 58 authentication-mode radius 59 authorization-scheme default 60 authorization-mode local 61 accounting-scheme default 62 accounting-mode none 63 local-aaa-user password policy administrator 64 password expire 0 65 domain default 66 authentication-scheme default 67 accounting-scheme default 68 radius-server default 69 domain default_admin 70 authentication-scheme default 71 accounting-scheme default 72 local-user admin password irreversible-cipher $1a$pQM(22l>8G$cV9+{9C,7/:$ 73 local-user admin privilege level 15 74 local-user admin service-type ssh http 75 # 76 interface Vlanif1 77 ip address 193.168.1.254 255.255.255.0 78 ip address 193.168.1.253 255.255.255.0 sub 79 nat outbound 2001 80 management-interface 81 # 82 interface Vlanif100 83 ip address 192.168.100.1 255.255.255.0 84 management-interface 85 # 86 interface Vlanif200 87 ip address 172.10.1.1 255.255.255.0 88 dhcp select interface 89 dhcp server dns-list 172.10.1.1 90 management-interface 91 # 92 interface Ethernet0/0/47 93 ip address 169.254.3.1 255.255.255.0 94 # 95 interface GigabitEthernet0/0/0 96 # 97 interface GigabitEthernet0/0/1 98 # 99 interface GigabitEthernet0/0/2 100 # 101 interface GigabitEthernet0/0/3 102 # 103 interface XGigabitEthernet0/0/0 104 port hybrid tagged vlan 2 to 4094 105 dhcp snooping trusted 106 # 107 interface MultiGE0/0/0 108 port hybrid tagged vlan 2 to 4094 109 dhcp snooping trusted 110 # 111 interface NULL0 112 # 113 info-center timestamp log date precision-time millisecond 114 info-center timestamp trap date precision-time millisecond 115 # 116 undo icmp name timestamp-request receive 117 # 118 undo snmp-agent 119 # 120 ssh server-source -i all 121 stelnet server enable 122 ssh server secure-algorithms cipher aes256_ctr aes128_ctr 123 ssh server secure-algorithms hmac sha2_256 124 ssh server key-exchange dh_group16_sha512 dh_group15_sha512 dh_group_exchange_sha256 dh_group14_sha1 125 ssh client secure-algorithms cipher aes256_ctr aes128_ctr 126 ssh client secure-algorithms hmac sha2_256 127 ssh client key-exchange dh_group16_sha512 dh_group15_sha512 dh_group_exchange_sha256 dh_group14_sha1 128 # 129 ip route-static 0.0.0.0 0.0.0.0 193.168.1.1 130 # 131 capwap dtls control-link encrypt off 132 # 133 user-interface con 0 134 authentication-mode password 135 set authentication password irreversible-cipher $1b$UG1.#.$O+=$_=+CvZ@@<1^Nsi\[.)<F1=$ 136 user-interface vty 0 4 137 authentication-mode aaa 138 protocol inbound ssh 139 user-interface vty 16 20 140 protocol inbound ssh 141 # 142 wmi-server 143 # 144 wmi-server2 145 # 146 wlan 147 temporary-management psk %^%#I_I41>B*W.HP5~4QLV}CDERM,WQ%^%# 148 ap username admin password cipher %^%#FT6]AIxok6XZNm$bF|8C%^%# 149 traffic-profile name default 150 traffic-profile name huawei-leaderap 151 traffic-profile name webZlcCswCifXMF 152 security-profile name default 153 security-profile name huawei-leaderap 154 security open 155 security-profile name webZlcCswCifXMF 156 security open 157 ssid-profile name default 158 ssid-profile name huawei-leaderap 159 ssid HUAWEI-LeaderAP-63B0 160 ssid-hide enable 161 ssid-profile name webZlcCswCifXMF 162 ssid HUAWEI_LeaderAP 163 vap-profile name huawei-leaderap 164 service-vlan vlan-id 100 165 ssid-profile huawei-leaderap 166 security-profile huawei-leaderap 167 traffic-profile huawei-leaderap 168 type leaderap-management 169 radio 0 1 2 170 vap-profile name webZlcCswCifXMF 171 service-vlan vlan-id 200 172 ssid-profile webZlcCswCifXMF 173 security-profile webZlcCswCifXMF 174 traffic-profile webZlcCswCifXMF 175 ap-zone default 176 radio 0 1 2 177 regulatory-domain-profile name default 178 air-scan-profile name default 179 rrm-profile name default 180 radio-2g-profile name default 181 radio-5g-profile name default 182 wids-spoof-profile name default 183 wids-whitelist-profile name default 184 wids-profile name default 185 ap-system-profile name default 186 port-link-profile name default 187 wired-port-profile name default 188 ap-group name default 189 ap-id 0 type-id 133 ap-mac 0000-0000-0000 ap-sn 000000000000000000 190 ap-name a82b-cd7b-63b0 191 provision-ap 192 # 193 interface Wlan-Radio0/0/0 194 # 195 interface Wlan-Radio0/0/1 196 # 197 dot1x-access-profile name dot1x_access_profile 198 # 199 mac-access-profile name mac_access_profile 200 # 201 undo ntp-service enable 202 ntp-service server server-source -i all 203 # 204 return






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· Manus爆火,是硬核还是营销?
· 一文读懂知识蒸馏
· 终于写完轮子一部分:tcp代理 了,记录一下