What is dwwin.exe?
The genuine dwwin.exe file is a software component of Dr Watson Application Program Debugger by Microsoft Corporation.
The name "dwwin.exe" has been used for years by Microsoft in application program error reporting and handling software. Their approach has changed repeatedly and "dwwin.exe" may refer to different code. It was called "Watson Client" in the "Dr. Watson" debugger, still found in "C:\Windows\System32" as "drwtsn32.exe" in XP systems or as "drwatson.exe" in Win7. For a limited time there was Microsoft Error Reporting (MER), whose main executable was "dw20.exe", had no "dwwin.exe", and resided in "C:\Program Files\Common Files\Microsoft Shared\DW". MER only worked for Win2000 SP3, WinXP, or Windows Server 2003. Vista made MER obsolete but the location in "%COMMON FILES%\Microsoft Shared\DW" persisted. Since Vista, the Windows Error Reporting (WER) API has enabled developers to customize the error-handling interface. "Dwwin.exe" can still be found in "C:\Windows\System32" on Win8 described as "Windows Error Reporting." Rather than uninstalling, registry key settings can disable Windows error handling software.
DWWin stands for Dr Watson Client for Windows
The .exe extension on a filename indicates an executable file. Executable files may, in some cases, harm your computer. Therefore, please read below to decide for yourself whether the dwwin.exe on your computer is a Trojan that you should remove, or whether it is a file belonging to the Windows operating system or to a trusted application.
Dwwin.exe file information
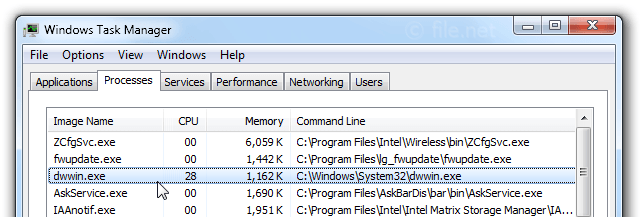 Dwwin.exe process in Windows Task Manager
Dwwin.exe process in Windows Task Manager
The process known as Windows Error Reporting or Microsoft Application Error Reporting or Watson Client belongs to software Microsoft Windows Operating System or Microsoft Application Error Reporting by Microsoft (www.microsoft.com).
Description: The original dwwin.exe from Microsoft is an important part of Windows, but often causes problems. Dwwin.exe is located in the C:\Windows\System32 folder. Known file sizes on Windows 10/11/7 are 180,224 bytes (56% of all occurrences), 136,704 bytes, 176,128 bytes or 130,048 bytes. ![]()
The file is a Microsoft signed file. The program has no visible window. Dwwin.exe is able to monitor applications and manipulate other programs. Therefore the technical security rating is 7% dangerous; however you should also read the user reviews.
Windows 2000
1、drwtsn32.log
drwtsn32.exe(Dr. Watson)是一个Windows系统内置的程序错误调试器。默认状态下,出现程序错误时,Dr. Watson 将自动启动。
Dr.Watson是Win 2000的一个崩溃分析工具,它会在应用程序崩溃的时候自动弹出,并且在默认情况下,它会将与出错有关的内存存为DUMP文件以供程序员分析。
崩溃的瞬间,会有一个对话框弹出,告知应用程序出错将被关闭。这时,一般伴随有巨型的读盘现象,要过很久程序才能关闭。这是因为Dr.Watson在做内存DUMP。
不过,可以通过设置DEP数据保护,避免弹出错误报告窗口。
drwtsn32.log占用大量磁盘空间,它的位置位于:
- C:\Documents and Settings\Default User\Local Settings\Application Data\Microsoft\Dr Watson\
Windows 10
Creating Dr. Watson Crash Dumps
Last update: 18-02-2020
How to create Dr. Watson crash dumps
Introduction
If an application crashes in Windows 2000, Windows XP or Windows Server 2003 not the whole system, then you may need to create Dr. Watson log.
(!) If an application crashes in Windows Vista of later, create a dump with ProcDump, see Creating Process Dumps with ProcDump
Full dumps are of considerable size (up to 800 MB), so you may be asked to use Acronis FTP Server. Please see Uploading Files to Acronis FTP Server.
(!) If Dr. Watson does not generate the dumps, use the ProcDump tool to generate a user dump of a process that shuts down with an exception or that stops responding (hangs). See Creating Process Dumps with ProcDump.
Solution
Creating Dr. Watson log and crash dump file on Windows 2000/2003/XP
- Press the Start button, choose Run, type drwtsn32 and hit Enter;
- In the dialog that appears check the Log File Path and Crash Dump paths;
- Set the Crash Dump Type to Full;
- Make sure the Dump Symbol Table option is checked, then click the OK button;
- Reproduce the issue;
- drwtsn32.log and user.dmp files will be created in the directories specified in Log File Path and Crash Dump.
Which is usually:\Documents and Settings\All Users\Application Data\Microsoft\Dr Watson
More information
(!) If the operating system becomes unresponsive, you can force system crash from the keyboard. See Microsoft Knowledge Base Article 244139.
If an application crashes in Windows Vista of later, create a dump with Procdump, see Creating Process Dumps with ProcDump
Tags:
软件测试之Dr.Watson篇
前一阵出差进行程序的联调,因为公司资源有限,所以并没有给我配备笔记本。当经理和组长逐bug进行调试时,我却只能来到客户的工控机旁进行软件的测试。正所谓生命不
息,bug不止,随着我一步步的操作,bug们也一次又一次开始向我示威。
我这人向来是不喜欢测试工作的,除了对我自己写的模块进行必要的单元测试外,其它测试我只是草草进行。这次他们既然让我来测试,我只好按步就班地进行。
bug一个又一个的出现,让我不胜其烦:这些明明很简单就能测出来的bug,怎么他们都没有发现呢?难道他们比我还更不屑于测试?
然而抱怨是于事无补的,既然黑夜给了我黑色的眼睛,我不妨就用它们来寻找bug.
当测到第N个bug时,我想:与其找到bug然后回去让他们调试,还不如我先找到出现bug的原因,这样就不用回去后再让他们验证错误了,直接验证代码就可以了.
可是,如何在没有调试器和代码的情况下找到出现bug的原因呢?嘿嘿,本文要讲的就是这个......
Dr.Watson是系统自带的一个程序错误调试工具。Dr.Watson其实就是柯南道尔那部著名世界的侦探小说《福尔摩斯》里面的那个医生“华生”,Microsoft的开发人员使用这个
名字来命名自己的调试工具,恐怕是想自己的工具能像“华生”一样有口皆碑,然而事实却是:很少有人关注它,甚至有人把他当做庸医。好了,闲话少谈,下面开始进入topic:
注:下面的内容全部来自Microsoft的帮助文档,他们比我写的好多了.
Dr.Watson 概述
Dr.Watson for Windows 是一个程序错误调试程序。
Dr.Watson 记录的信息是技术支持小组诊断运行 Windows 的计算机的程序错误所需的信息。只要检测到错误,就会创建一个文本文件 (Drwtsn32.log),并可按支持人员常用的方式传递给支持人员。也可以选择创建故障转储文件,它是程序员可以加载到调试程序中的二进制文件。
如果出现程序错误,Dr.Watson 将自动启动。要启动 Dr.Watson,请单击“开始”,单击“运行”,然后键入 drwtsn32。要从命令提示启动 Dr.Watson,请转到根目录,然后键入 drwtsn32。
安装 Dr.Watson
安装 Windows 时,会将 Dr.Watson (Drwtsn32.exe) 安装到系统文件夹中。首次运行 Dr.Watson 时(即出现程序错误时或用户亲自启动 Dr.Watson 时),会设置默认选项。
当 Windows 中出现程序错误时,系统将搜索错误处理程序。程序错误处理程序处理程序运行过程中出现的错误。如果系统找不到程序错误处理程序,系统将验证是否该程序当前没有被调试,并认为错误没有被处理。如果系统找不到程序错误处理程序,系统将验证是否该程序当前没有被调试,并认为错误没有被处理。然后系统通过在“注册表编辑器”中查找程序错误调试程序来处理尚未处理的错误。
系统在“注册表编辑器”的注册表项 //HKEY_LOCAL_MACHINE/Software/Microsoft/Windows NT/CurrentVersion/AeDebug 下查找名为 Debugger 和 Auto 的项。Debugger 项的值指定了调试程序将要用来分析程序错误的命令。如果找到了调试程序项的值,系统将查看 Auto 项的值是设置为 0 还是 1。
- 如果 Auto 项的值设置为 0,系统将产生一个消息框,通知您发生了程序错误。如果“调试程序”项的值指定了有效调试程序所使用的命令,消息框将显示两个按钮:“确定”和“取消”。如果单击“确定”,程序将终止。如果单击“取消”,系统将启动指定的调试程序。如果“调试程序”项的值为空,消息框将只显示“确定”,并且不启动任何调试程序。
- 如果 Auto 项的值设置为 1,并且调试程序项的值指定了有效调试程序所使用的命令,系统将自动启动该调试程序,并且不会产生消息框。
当在系统上安装 Windows 时,默认情况下 Auto 项的值设置为 1,并且调试程序项的值指定了启动 Dr.Watson 的命令。这意味着当出现程序错误时,Dr.Watson for Windows 将自动诊断错误,并记录相应的诊断信息。
如果您使用的默认调试程序不是 Dr.Watson,而又要换用 Dr.Watson,请在命令提示符后键入命令 drwtsn32 -i 来启动 Dr.Watson。键入 -i 可对注册表进行必要的更改。
如果安装了适当的符号并设置了符号搜索路径,Dr.Watson 可以生成更精确的调试信息。为此,首先需要从 Windows CD-ROM 中将符号复制到计算机的新建文件夹中。然后将需要创建新的系统环境变量。首先,请转到计算机上的 Systemroot 文件夹,建立一个名为“Symbols”的新文件夹。接下来,转到光盘上的 /Support/Debug/i386,将符号复制到已创建的“Symbols”文件夹下。复制符号后,请创建一个新的系统环境变量。创建新的系统环境变量时,为变量名称键“ %systemroot% /Symbol”。请务必在添加的服务包中包括变量。例如:_NT_SYMBOL_PATH= %systemroot% /symbol; %systemroot% /hotfixes; %systemroot% /symbolsNt4Sp3。
使用 Dr.Watson
Dr. Watson 检测有关系统和程序失败的信息并将这些信息记录在一个日志文件中。在程序出错事件中,Dr. Watson 自动启动。
注意
- 要打开 Dr. Watson,请单击“开始”,然后单击“运行”。在“打开”框中,键入 drwtsn32。
- Dr. Watson 不能阻止错误的发生,但记录在日志文件中的信息可帮助技术支持人员诊断问题。
- 有关使用 Dr. Watson 的信息,请单击“Dr. Watson”中的“帮助”。
使用 Dr.Watson 日志文件
在发生程序错误时,Dr.Watson 会生成一个日志文件(Drwtsn32.log)。日志文件总是以下列行打头:
发生应用程序意外错误:
日志文件的下一部分总是包含程序错误信息。列出的错误号对应于系统产生的错误。
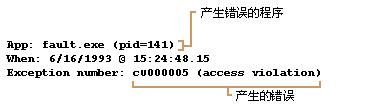
日志文件的再下一部分包含关于用户和发生程序错误的计算机的系统信息。
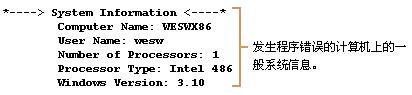
日志文件的再下一部分包含当程序错误发生时在系统上运行的任务的列表。

日志文件的再下一部分包含程序加载的模块的列表。
日志文件的再下一部分包含所列出的线程 ID 的状态转储。状态转储由寄存器转储、当前程序计数器周围代码的分解、堆栈向后跟踪和原始堆栈转储组成。状态转储的第一部分列出了线程 ID。
线程 Id 0xbf 的状态转储
状态转储的下一部分包含寄存器转储。

状态转储的再下一部分包含指令分解。

状态转储的再下一部分包含堆栈向后跟踪。
状态转储的最后一部分包含原始堆栈转储。
在状态转储之后,日志文件的最后一部分包含符号表。
实战:结合Dr.Watson系统日志和Vc6来定位多线程环境下程序异常退出的错误
转自于:http://blog.csdn.net/coding_hello/article/details/2994158
当开发的软件发布以后,在客户那运行时可能会因为各种原因导致程序退出。这种情况很尴尬,很明显我们无法在客户机器上装个Visual Studio调试,所以必须有机制来收集出错的信息。软件本身的运行日志能提供部分信息,但是可能还不够。Windows系统为此提供了解决方案:Dr.Watson工具。Dr.Watson也算是一个小巧的调试器,32位的版本名字是drwtsn32.exe。可用于当系统中有进程发生异常崩溃时采集信息。下面结合一个例子看一下其用法。
先把测试代码贴一下:
- /********************************************************************/
- /* 程序:lesson_2, 结合Dr.Watson与工程map文件定位错误 */
- /* 功能:多线程环境中利用除0错误使程序产生异常,被Dr.Watson捕获之 */
- /* 作者:coding (http://blog.csdn.net/coding_hello) */
- /* 日期:2008-09-29 */
- /********************************************************************/
- #include <stdio.h>
- #include <process.h>
- #include <windows.h>
- const int cnThreadnum = 4;
- UINT WINAPI Worker(LPVOID lpParam)
- {
- srand((DWORD)lpParam);
- DWORD dwTid = GetCurrentThreadId();
- int k=100;
- while(k--)
- {
- printf("tid[%u] tmp = %d/n", dwTid, RAND_MAX/(rand()%cnThreadnum));
- Sleep(10);
- }
- return 0;
- }
- int main(int argc, char* argv[])
- {
- HANDLE hThd[cnThreadnum] = {0};
- for(DWORD i=0; i<cnThreadnum; i++)
- {
- hThd[i] = (HANDLE)_beginthreadex(NULL, 0, Worker, (LPVOID)i, 0, NULL);
- }
- printf("Wait.../n");
- WaitForMultipleObjects(cnThreadnum, hThd, TRUE, INFINITE);
- for(int k=0; k<cnThreadnum; k++)
- {
- CloseHandle(hThd[k]);
- }
- printf("Finish!/n");
- system("pause");
- return 0;
- }
程序已开始就启动了4个线程,然后主线程等待所有的线程结束。线程函数中可能会因为RAND_MAX/(rand()%10)导致出现除0的错误。这里注意,编译的时候选择Link页,把"Generate mapfile"前面勾上。一般来说我就这样用了。但是还可以让map信息更详细一些,在最下面的"Project Options"的最后面手工敲入:"/mapinfo:lines",注意,跟前面内容要用空格隔开。然后再编译。
因为是要演示Dr.Waston,所以我们在命令行先用drwtsn32 -i的命令注册Dr.Watson为默认调试器(下次启动VC6的时候,在菜单option-->debug里面确认just-in-time debugging选中,就会把VC6恢复为默认调试器的)。注册完以后,我们看看注册表是否满足需要了。
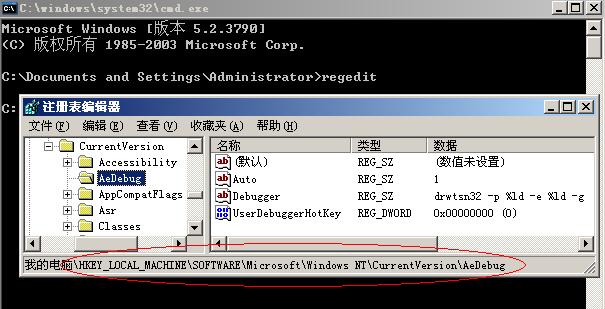
看看注册表中HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Windows NT/CurrentVersion/AeDebug,其中的Auto键的值如果是0的话,程序出错后还会弹出错误提示。我们需要的是出错后安静的处理掉,客户知道了多不好~所以,改成1。下面的Debugger已经是drwtsn32了,很好。最后的UserDebuggerHotKey是调试器的热键,我们不需要。接下来,还是在命令行敲Drwtsn32,回车,终于看到Drwtsn32的庐山真面目了:
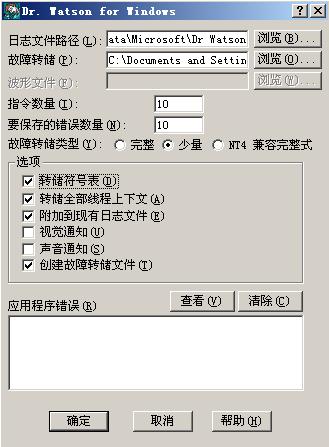
上面是日志文件和dump文件的保存路径。这次我们要看的是日志,dump文件下次再说。符号表我一般都勾上了,有的话就更好不是~ 重点是下面的应用程序错误(&R)这里,如果日志中有信息,就会在下面一条一条以纪录的形式显示出来。如果你的Drwatson中确实有日志的话,可以点清除把以前的都删掉。既然已经见过面了,那就把它关掉吧,需要时再打开,反正它自己也不会实施刷新。
好,现在一切就绪了!运行一下程序~ 只见嗖的一下,程序就停了。赶紧再把Dr.Watson请出来看看~
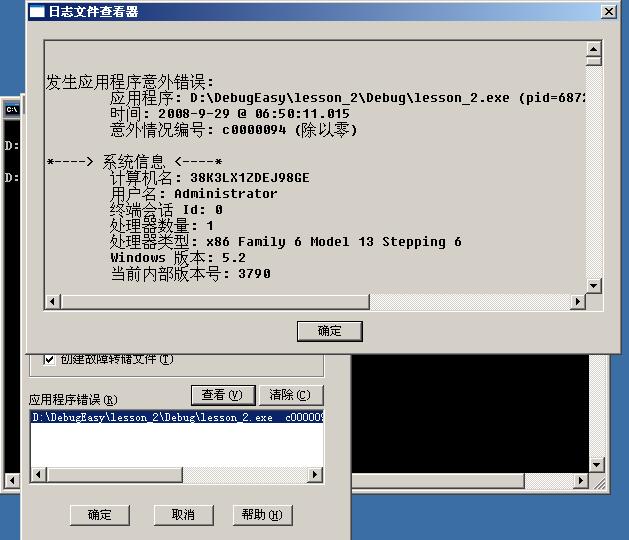
这次我们看到应用程序错误那里有了一条记录,把它选中变蓝后点上面的查看按钮。于是又出来一个对话框,显示“发生应用程序意外错误:”云云,内容很长,信息相当多。嗯,很好,很强大,这就是我们要的。考虑到这个框小了点,可以Ctrl+Shift+END全选后copy出来,用记事本看哈。在记事本中查找"错误 ->",然后就会看到个这:
错误 ->00401087 f7f9 idiv eax,ecx
没错,这就是错误的位置。仔细看看上下文,分析分析。由于是一个多线程的程序,所以这里把出错的线程单独剥离出来。如下所示,每个线程的信息分为几个部分:一开始是错误发生时寄存器的信息;然后是当前发生错误的指令的前后各10条指令(什么是10条,不是20条或者2条?因为Dr.Watson里面默认设置的就是10条呀~,你刚才又没改);接下来是堆栈反向跟踪信息,也就是函数的逆向调用序列;最后是原始堆栈信息,可以获得参数,返回地址,局部变量之类的信息。
- *----> 线程 ID 0x2714 的状态转储 <----*
- eax=00007fff ebx=003724b8 ecx=00000000 edx=00000000 esi=0063ff2c edi=0063ff80
- eip=00401087 esp=0063ff2c ebp=0063ff80 iopl=0 nv up ei pl zr na pe nc
- cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246
- 函数: lesson_2!Worker
- 0040106b 7441 je lesson_2!Worker+0x8e (004010ae)
- 0040106d e86e020000 call lesson_2!rand (004012e0)
- 00401072 8bc8 mov ecx,eax
- 00401074 81e103000080 and ecx,80000003h
- 0040107a 7905 jns lesson_2!Worker+0x61 (00401081)
- 0040107c 49 dec ecx
- 0040107d 83c9fc or ecx,0FFFFFFFCh
- 00401080 41 inc ecx
- 00401081 b8ff7f0000 mov eax,7FFFh
- 00401086 99 cdq
- 错误 ->00401087 f7f9 idiv eax,ecx
- 00401089 50 push eax
- 0040108a 8b55fc mov edx,dword ptr [ebp-4]
- 0040108d 52 push edx
- 0040108e 681cd04200 push offset lesson_2!`string' (0042d01c)
- 00401093 e898010000 call lesson_2!printf (00401230)
- 00401098 83c40c add esp,0Ch
- 0040109b 8bf4 mov esi,esp
- 0040109d 6a0a push 0Ah
- 0040109f ff15d8714300 call dword ptr [lesson_2!_imp__Sleep (004371d8)]
- 004010a5 3bf4 cmp esi,esp
- *----> 堆栈反向跟踪 <---*
- ChildEBP RetAddr Args to Child
- 0063ff80 004015e2 00000001 00000000 00000000 lesson_2!Worker+0x67
- 0063ffb8 7c824829 003724b8 00000000 00000000 lesson_2!_threadstartex+0xb2
- WARNING: Stack unwind information not available. Following frames may be wrong.
- 0063ffec 00000000 00401530 003724b8 00000000 kernel32!GetModuleHandleA+0xdf
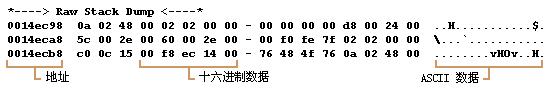
- *----> 原始堆栈转储 <----*
- 000000000063ff2c 00 00 00 00 00 00 00 00 - b8 24 37 00 cc cc cc cc .........$7.....
- 000000000063ff3c cc cc cc cc cc cc cc cc - cc cc cc cc cc cc cc cc ................
- 000000000063ff4c cc cc cc cc cc cc cc cc - cc cc cc cc cc cc cc cc ................
- 000000000063ff5c cc cc cc cc cc cc cc cc - cc cc cc cc cc cc cc cc ................
- 000000000063ff6c cc cc cc cc cc cc cc cc - cc cc cc cc 06 00 00 00 ................
- 000000000063ff7c 14 27 00 00 b8 ff 63 00 - e2 15 40 00 01 00 00 00 .'....c...@.....
- 000000000063ff8c 00 00 00 00 00 00 00 00 - b8 24 37 00 94 00 00 c0 .........$7.....
- 000000000063ff9c 00 00 00 00 8c ff 63 00 - 60 fb 63 00 dc ff 63 00 ......c.`.c...c.
- 000000000063ffac b4 65 40 00 b0 d1 42 00 - 00 00 00 00 ec ff 63 00 .e@...B.......c.
- 000000000063ffbc 29 48 82 7c b8 24 37 00 - 00 00 00 00 00 00 00 00 )H.|.$7.........
- 000000000063ffcc b8 24 37 00 94 00 00 c0 - c4 ff 63 00 60 fb 63 00 .$7.......c.`.c.
- 000000000063ffdc ff ff ff ff 60 1a 82 7c - 30 48 82 7c 00 00 00 00 ....`..|0H.|....
- 000000000063ffec 00 00 00 00 00 00 00 00 - 30 15 40 00 b8 24 37 00 ........0.@..$7.
- 000000000063fffc 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
- 000000000064000c 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
- 000000000064001c 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
- 000000000064002c 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
- 000000000064003c 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
- 000000000064004c 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
- 000000000064005c 00 00 00 00 00 00 00 00 - 00 00 00 00 00 00 00 00 ................
尽管这里可以简单的利用错误处指出的地址0x401087直接定位,那是因为这是很简单的情况。所以我决定还是简单讲一下在实际的复杂得多的环境中如何分析这些数据。
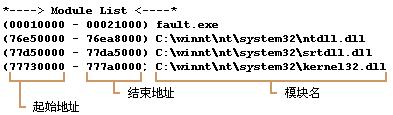
1.定位出错的模块。
我们看到错误的地址是0x401087,应该先确认这个地址是在哪个模块中。在错误日志中查找“模块清单”,能找到以下内容:
- *----> 模块清单 <----*
- 0000000000400000 - 000000000043a000: D:/DebugEasy/lesson_2/Debug/lesson_2.exe
- 0000000074ae0000 - 0000000074b45000: C:/windows/system32/USP10.dll
- 0000000076180000 - 000000007619d000: C:/windows/system32/IMM32.DLL
- 0000000076eb0000 - 0000000076ec3000: C:/windows/system32/Secur32.dll
- 0000000077bd0000 - 0000000077c18000: C:/windows/system32/GDI32.dll
- 0000000077c20000 - 0000000077cbf000: C:/windows/system32/RPCRT4.dll
- 0000000077e10000 - 0000000077ea0000: C:/windows/system32/USER32.dll
- 0000000077f30000 - 0000000077fdb000: C:/windows/system32/ADVAPI32.dll
- 000000007c800000 - 000000007c92b000: C:/windows/system32/kernel32.dll
- 000000007c930000 - 000000007ca00000: C:/windows/system32/ntdll.dll
- 000000007f000000 - 000000007f009000: C:/windows/system32/LPK.DLL
这里清楚的指出0000000000400000 - 0000000000439000这个范围的地址是系统分配给lesson_2.exe的。我们得到的错误地址是0x401087,所以可以确定错误就是发生的lesson_2.exe模块。实际上很多应用都还有些自己的动态库之类的,定位到具体的模块后才能更具体的结合代码分析。有时候出错的地址是属于kernel32,ntdll.dll之类的系统函数,这种情况下需要分析堆栈信息来确定错误模块。
2.分析当前发生错误的直接原因
我们看到错误的指令是:idiv eax,ecx。基本上访问eax和ecx都不会有问题,不然就是cpu有问题了。所以应该是除法指令出错。看看前面的寄存器的信息,eax=00007fff,也就是RAND_MAX,ecx=00000000,除0错误。对于我们这个例子,有了这个信息就足够定位到问题了。不过还是看看我们还能收集到些什么信息,毕竟实际环境可不会这么简单。
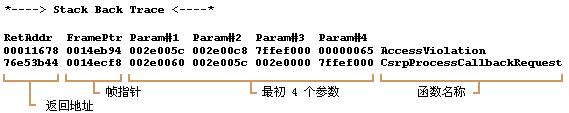
3.分析当前线程的调用堆栈。
ChildEBP RetAddr Args to Child
0063ff80 004015e2 00000001 00000000 00000000 lesson_2!Worker+0x67
0063ffb8 7c824829 003724b8 00000000 00000000 lesson_2!_threadstartex+0xb2
在堆栈反向跟踪部分,这个信息很清晰。_threadstartex系统函数调用了我们的线程函数Worker。当前函数的返回地址是0x4015e2,接着是3个参数(注意:不一定都有效,显然不是所有的函数都有3个参数。实际上通过分析其dump文件能看到我们的例子中只有第一个参数有效,即1,是作为线程参数传入的lpParam)。这里我们结合map文件看看是不是跟这里记录的一样。在工程的debug目录里,有个扩展名为map的文件,用一般的文本编辑器就能打开。这文件太长了,节选一部分看看:
- lesson_2
- Timestamp is 48e0197a (Mon Sep 29 06:50:11 2008)
- Preferred load address is 00400000
- Start Length Name Class
- 0001:00000000 0001bae7H .text CODE
- 0001:0001bae7 00010009H .textbss CODE
- 0002:00000000 00002207H .rdata DATA
- 0002:00002207 00000000H .edata DATA
- 0003:00000000 00000104H .CRT$XCA DATA
- 0003:00000104 00000104H .CRT$XCZ DATA
- 0003:00000208 00000104H .CRT$XIA DATA
- 0003:0000030c 00000109H .CRT$XIC DATA
- 0003:00000418 00000104H .CRT$XIZ DATA
- 0003:0000051c 00000104H .CRT$XPA DATA
- 0003:00000620 00000104H .CRT$XPX DATA
- 0003:00000724 00000104H .CRT$XPZ DATA
- 0003:00000828 00000104H .CRT$XTA DATA
- 0003:0000092c 00000104H .CRT$XTZ DATA
- 0003:00000a30 0000407cH .data DATA
- 0003:00004ab0 00001b94H .bss DATA
- 0004:00000000 00000014H .idata$2 DATA
- 0004:00000014 00000014H .idata$3 DATA
- 0004:00000028 000001b0H .idata$4 DATA
- 0004:000001d8 000001b0H .idata$5 DATA
- 0004:00000388 0000076bH .idata$6 DATA
- Address Publics by Value Rva+Base Lib:Object
- 0001:00000020 ?Worker@@YGIPAX@Z 00401020 f lesson_2.obj
- 0001:000000f0 _main 004010f0 f lesson_2.obj
- 0001:00000212 _Sleep@4 00401212 f kernel32:KERNEL32.dll
- 0001:00000218 _GetCurrentThreadId@0 00401218 f kernel32:KERNEL32.dll
- 0001:0000021e _CloseHandle@4 0040121e f kernel32:KERNEL32.dll
- 0001:00000224 _WaitForMultipleObjects@16 00401224 f kernel32:KERNEL32.dll
- 0001:00000230 _printf 00401230 f LIBCMTD:printf.obj
- 0001:000002d0 _srand 004012d0 f LIBCMTD:rand.obj
- 0001:000002e0 _rand 004012e0 f LIBCMTD:rand.obj
- 0001:00000320 __chkesp 00401320 f LIBCMTD:chkesp.obj
- 0001:00000360 _system 00401360 f LIBCMTD:system.obj
- 0001:00000470 __beginthreadex 00401470 f LIBCMTD:threadex.obj
- 0001:00000630 __endthreadex 00401630 f LIBCMTD:threadex.obj
- 0001:00000680 _mainCRTStartup 00401680 f LIBCMTD:crt0.obj
- 0001:000007d0 __amsg_exit 004017d0 f LIBCMTD:crt0.obj
- 。。。。。。省略若干。。。。。
- Line numbers for ./Debug/lesson_2.obj(d:/debugeasy/lesson_2/lesson_2.cpp) segment .text
- 18 0001:00000020 19 0001:00000038 21 0001:00000044 22 0001:00000056
- 23 0001:0000005d 25 0001:0000006d 26 0001:0000009b 27 0001:000000ac
- 28 0001:000000ae 29 0001:000000b0 32 0001:000000f0 33 0001:00000108
- 34 0001:0000011a 36 0001:00000132 37 0001:00000152 39 0001:00000154
- 40 0001:00000161 42 0001:0000017a 44 0001:00000192 45 0001:000001a9
- 47 0001:000001ab 48 0001:000001b8 49 0001:000001c5 50 0001:000001c7
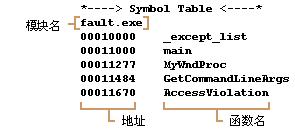
其中显示了程序名,程序的时间戳,程序中的代码分布,预定的加载地址,各个函数的起始地址,包括相对虚拟地址(RVA)以及文件行与RVA的对应关系等信息。我们看到预定的加载地址和我们在模块清单中看到的加载地址相同。很好,省得计算相对位置。一般来说Exe总是加载到0x400000,并且总是能得到这个位置的。而动态库的话,墨认是0x10000000,显然如果有2个动态库就没法都加载到同一个地址,需要计算RVA。
刚才从堆栈反向跟踪信息中我们看到当前Worker函数的返回地址为0x401e52,在map文件中找找。很快就能看到__beginthreadex函数是从0x401470开始,到0x401630结束。那就说明地址0x401e52就在__beginthreadex函数中。这就对了,因为我们就是用__beginthreadex函数启动的线程函数Worker,是吧~。顺手看一下刚才出错的地址0x401087,看看是在哪。再看看map文件,第一个函数就是?Worker@@YGIPAX@Z,地址是0x00401020至0x4010f0(main函数),所以0x401087就是在执行Worker函数中的指令。那么具体在哪一行呢?因为出错的函数Worker在文件lesson_2.cpp中,所以我们查找lesson_2.cpp,就找到了下面的信息:
- Line numbers for ./Debug/lesson_2.obj(d:/debugeasy/lesson_2/lesson_2.cpp) segment .text
- 15 0001:00000020 16 0001:00000038 18 0001:00000044 19 0001:00000056
- 20 0001:0000005d 22 0001:0000006d 23 0001:0000009b 24 0001:000000ac
- 25 0001:000000ae 26 0001:000000b0 29 0001:000000f0 30 0001:00000108
- 31 0001:0000011a 33 0001:00000132 34 0001:00000152 46 0001:00000154
- 37 0001:00000161 39 0001:0000017a 41 0001:00000192 42 0001:000001a9
- 44 0001:000001ab 45 0001:000001b8 46 0001:000001c5 47 0001:000001c7
我们看到前面是个数字,18、19、21啥的,后面是0001:00000020之类。前面的就是cpp文件中的行号,后面是相对虚拟地址,我们的0x401087在哪呢?又回到刚才说的默认加载地址了。map中看到默认加载地址是0x400000,而我们的exe在内存中也是加载到0x400000,所以相对位置就是RVA = 0x401087(错误地址) - 0x400000(模块在内存中实际加载的地址) = 0x1067。不对啊,这里最大才到0x1c7,这是怎~么个情况?因为每个PE模块之前都有0x1000字节的dos stub和PE格式信息。所以0x1087还要减掉0x1000,就剩下0x87了。再看看,大于0x5d,小于0x6d,所以就是第22行。看看代码中的22行,printf("tid[%u] tmp = %d/n", dwTid, RAND_MAX/(rand()%cnThreadnum));没错,就是在这里RAND_MAX/0了~。说明前面根据Dr.Watson的日志分析的结果都是正确的,没骗你噢~
有时候堆栈反向跟踪的信息并不准确,多半是因为函数中的局部变量在memcpy,strcpy之类的函数复制的数据过长,导致堆栈访问越界。这种情况下,要仔细分析原始堆栈转储,以后再说。
在实际工作中,利用Dr.Watson辅助生成错误日志,对于开发人员确实是很有帮助的。有需要的朋友,可以考虑这么试试。
那今天就写到这吧~ 天亮啦,饭去~
Report.wer
Version=1 EventType=AppHangB1 EventTime=133237520087557306 ReportType=3 Consent=1 UploadTime=133237520116844746 ReportStatus=268435456 ReportIdentifier=2ce934a2-3746-4d5a-99a0-217cc24304c9 IntegratorReportIdentifier=cbfda79d-c7da-430a-b924-2f8cb7b7900e Wow64Host=34404 NsAppName=procexp64.exe OriginalFilename=Procexp.exe AppSessionGuid=00005eb0-0002-000b-ac35-9f5ed15ad901 TargetAppId=W:0006269e38b31bd42652bc441797f8f689ae00000904!00001613be64046681cf33dce74c10520d7ae06d3bb6!procexp64.exe TargetAppVer=2022//11//10:19:16:32!25280f!procexp64.exe BootId=4294967295 HeapdumpAttached=1 TargetAsId=420254 IsFatal=1 EtwNonCollectReason=4 Response.BucketId=a7c88c9c881608f27574d82ce616b2c1 Response.BucketTable=5 Response.LegacyBucketId=1546098259445330625 Response.type=4 Sig[0].Name=应用程序名 Sig[0].Value=procexp64.exe Sig[1].Name=应用程序版本 Sig[1].Value=17.0.2.0 Sig[2].Name=应用程序时间戳 Sig[2].Value=636d4e10 Sig[3].Name=挂起签名 Sig[3].Value=b050 Sig[4].Name=挂起类型 Sig[4].Value=134217728 DynamicSig[1].Name=OS 版本 DynamicSig[1].Value=10.0.17763.2.0.0.400.8 DynamicSig[2].Name=区域设置 ID DynamicSig[2].Value=2052 DynamicSig[22].Name=其他挂起签名 1 DynamicSig[22].Value=b050c6868e1c2b69bbe3771cfe2d9a71 DynamicSig[23].Name=其他挂起签名 2 DynamicSig[23].Value=0f91 DynamicSig[24].Name=其他挂起签名 3 DynamicSig[24].Value=0f91db3f55c847175ee79f7163125be6 DynamicSig[25].Name=其他挂起签名 4 DynamicSig[25].Value=b050 DynamicSig[26].Name=其他挂起签名 5 DynamicSig[26].Value=b050c6868e1c2b69bbe3771cfe2d9a71 DynamicSig[27].Name=其他挂起签名 6 DynamicSig[27].Value=0f91 DynamicSig[28].Name=其他挂起签名 7 DynamicSig[28].Value=0f91db3f55c847175ee79f7163125be6 UI[3]=Sysinternals Process Explorer 未响应 UI[4]=如果关闭该程序,你可能丢失信息。 UI[5]=关闭程序 UI[6]=关闭程序 UI[7]=关闭程序 LoadedModule[0]=C:\Users\Administrator\Desktop\Tools\procexp64.exe LoadedModule[1]=C:\Windows\SYSTEM32\ntdll.dll LoadedModule[2]=C:\Windows\System32\KERNEL32.DLL LoadedModule[3]=C:\Windows\System32\KERNELBASE.dll LoadedModule[4]=C:\Windows\System32\SHLWAPI.dll LoadedModule[5]=C:\Windows\System32\msvcrt.dll LoadedModule[6]=C:\Windows\System32\combase.dll LoadedModule[7]=C:\Windows\System32\ucrtbase.dll LoadedModule[8]=C:\Windows\System32\RPCRT4.dll LoadedModule[9]=C:\Windows\System32\bcryptPrimitives.dll LoadedModule[10]=C:\Windows\System32\GDI32.dll LoadedModule[11]=C:\Windows\System32\gdi32full.dll LoadedModule[12]=C:\Windows\System32\msvcp_win.dll LoadedModule[13]=C:\Windows\System32\USER32.dll LoadedModule[14]=C:\Windows\System32\win32u.dll LoadedModule[15]=C:\Windows\System32\WS2_32.dll LoadedModule[16]=C:\Windows\System32\SETUPAPI.dll LoadedModule[17]=C:\Windows\System32\cfgmgr32.dll LoadedModule[18]=C:\Windows\SYSTEM32\IPHLPAPI.DLL LoadedModule[19]=C:\Windows\System32\bcrypt.dll LoadedModule[20]=C:\Windows\SYSTEM32\MPR.dll LoadedModule[21]=C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.17763.1577_none_de7444545348a3d0\COMCTL32.dll LoadedModule[22]=C:\Windows\System32\CRYPT32.dll LoadedModule[23]=C:\Windows\SYSTEM32\VERSION.dll LoadedModule[24]=C:\Windows\System32\MSASN1.dll LoadedModule[25]=C:\Windows\SYSTEM32\credui.dll LoadedModule[26]=C:\Windows\System32\POWRPROF.dll LoadedModule[27]=C:\Windows\System32\COMDLG32.dll LoadedModule[28]=C:\Windows\System32\shcore.dll LoadedModule[29]=C:\Windows\SYSTEM32\WTSAPI32.dll LoadedModule[30]=C:\Windows\SYSTEM32\ACLUI.dll LoadedModule[31]=C:\Windows\SYSTEM32\UxTheme.dll LoadedModule[32]=C:\Windows\System32\SHELL32.dll LoadedModule[33]=C:\Windows\System32\windows.storage.dll LoadedModule[34]=C:\Windows\System32\sechost.dll LoadedModule[35]=C:\Windows\System32\advapi32.dll LoadedModule[36]=C:\Windows\System32\profapi.dll LoadedModule[37]=C:\Windows\System32\kernel.appcore.dll LoadedModule[38]=C:\Windows\System32\cryptsp.dll LoadedModule[39]=C:\Windows\System32\ole32.dll LoadedModule[40]=C:\Windows\System32\OLEAUT32.dll LoadedModule[41]=C:\Windows\SYSTEM32\MSIMG32.dll LoadedModule[42]=C:\Windows\SYSTEM32\dwmapi.dll LoadedModule[43]=C:\Windows\SYSTEM32\WINHTTP.dll LoadedModule[44]=C:\Windows\SYSTEM32\XmlLite.dll LoadedModule[45]=C:\Windows\SYSTEM32\NTDSAPI.dll LoadedModule[46]=C:\Windows\System32\IMM32.DLL LoadedModule[47]=C:\Windows\SYSTEM32\winsta.dll LoadedModule[48]=C:\Program Files (x86)\Windows Kits\10\Debuggers\x64\dbghelp.dll LoadedModule[49]=C:\Windows\SYSTEM32\dbgcore.DLL LoadedModule[50]=C:\Windows\System32\wow64cpu.DLL LoadedModule[51]=C:\Windows\System32\wow64.dll LoadedModule[52]=C:\Windows\System32\wow64win.dll LoadedModule[53]=C:\Windows\system32\mscoree.dll LoadedModule[54]=C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscoreei.dll LoadedModule[55]=C:\Windows\Microsoft.NET\Framework64\v4.0.30319\CorperfmonExt.dll LoadedModule[56]=C:\Windows\SYSTEM32\VCRUNTIME140_CLR0400.dll LoadedModule[57]=C:\Windows\SYSTEM32\ucrtbase_clr0400.dll LoadedModule[58]=C:\Windows\System32\psapi.dll LoadedModule[59]=C:\Windows\system32\netfxperf.dll LoadedModule[60]=C:\Windows\Microsoft.NET\Framework64\v4.0.30319\perfcounter.dll LoadedModule[61]=C:\Windows\SYSTEM32\pdh.dll LoadedModule[62]=C:\Windows\SYSTEM32\atlthunk.dll LoadedModule[63]=C:\Windows\System32\MSCTF.dll LoadedModule[64]=C:\Windows\SYSTEM32\WindowsCodecs.dll LoadedModule[65]=C:\Windows\System32\clbcatq.dll LoadedModule[66]=C:\Windows\System32\thumbcache.dll LoadedModule[67]=C:\Windows\system32\propsys.dll LoadedModule[68]=C:\Windows\System32\Wintrust.dll LoadedModule[69]=C:\Windows\System32\TextInputFramework.dll LoadedModule[70]=C:\Windows\System32\CoreUIComponents.dll LoadedModule[71]=C:\Windows\System32\CoreMessaging.dll LoadedModule[72]=C:\Windows\SYSTEM32\ntmarta.dll LoadedModule[73]=C:\Windows\SYSTEM32\wintypes.dll LoadedModule[74]=C:\Windows\SYSTEM32\DEVOBJ.dll LoadedModule[75]=C:\Windows\System32\taskschd.dll LoadedModule[76]=C:\Windows\System32\SspiCli.dll LoadedModule[77]=C:\Windows\system32\rsaenh.dll LoadedModule[78]=C:\Windows\SYSTEM32\CRYPTBASE.dll LoadedModule[79]=C:\Windows\Microsoft.NET\Framework64\v2.0.50727\mscordbi.dll LoadedModule[80]=C:\Windows\WinSxS\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.9554_none_88e038cb2fae7c50\MSVCR80.dll LoadedModule[81]=C:\Windows\System32\imagehlp.dll LoadedModule[82]=C:\Windows\SYSTEM32\gpapi.dll LoadedModule[83]=C:\Windows\SYSTEM32\MrmCoreR.dll LoadedModule[84]=C:\Windows\SYSTEM32\iertutil.dll LoadedModule[85]=C:\Windows\SYSTEM32\cryptnet.dll LoadedModule[86]=C:\Windows\SYSTEM32\WINNSI.DLL LoadedModule[87]=C:\Windows\System32\NSI.dll LoadedModule[88]=C:\Windows\system32\wbem\wbemprox.dll LoadedModule[89]=C:\Windows\SYSTEM32\wbemcomn.dll LoadedModule[90]=C:\Windows\system32\wbem\wbemsvc.dll LoadedModule[91]=C:\Windows\system32\wbem\fastprox.dll LoadedModule[92]=C:\Windows\system32\mswsock.dll LoadedModule[93]=C:\Windows\SYSTEM32\dhcpcsvc6.DLL LoadedModule[94]=C:\Windows\SYSTEM32\dhcpcsvc.DLL LoadedModule[95]=C:\Windows\SYSTEM32\webio.dll LoadedModule[96]=C:\Windows\SYSTEM32\DNSAPI.dll LoadedModule[97]=C:\Windows\System32\rasadhlp.dll LoadedModule[98]=C:\Windows\System32\fwpuclnt.dll LoadedModule[99]=C:\Program Files (x86)\Windows Kits\10\Debuggers\x64\symsrv.dll LoadedModule[100]=C:\Windows\SYSTEM32\wininet.dll LoadedModule[101]=C:\Windows\SYSTEM32\ondemandconnroutehelper.dll LoadedModule[102]=C:\Windows\SYSTEM32\urlmon.dll LoadedModule[103]=C:\Windows\system32\schannel.DLL LoadedModule[104]=C:\Windows\SYSTEM32\mskeyprotect.dll LoadedModule[105]=C:\Windows\SYSTEM32\ncrypt.dll LoadedModule[106]=C:\Windows\SYSTEM32\NTASN1.dll LoadedModule[107]=C:\Windows\SYSTEM32\DPAPI.DLL LoadedModule[108]=C:\Windows\system32\ncryptsslp.dll LoadedModule[109]=C:\Windows\System32\coml2.dll State[0].Key=Transport.DoneStage1 State[0].Value=1 OsInfo[0].Key=vermaj OsInfo[0].Value=10 OsInfo[1].Key=vermin OsInfo[1].Value=0 OsInfo[2].Key=verbld OsInfo[2].Value=17763 OsInfo[3].Key=ubr OsInfo[3].Value=1577 OsInfo[4].Key=versp OsInfo[4].Value=0 OsInfo[5].Key=arch OsInfo[5].Value=9 OsInfo[6].Key=lcid OsInfo[6].Value=2052 OsInfo[7].Key=geoid OsInfo[7].Value=45 OsInfo[8].Key=sku OsInfo[8].Value=8 OsInfo[9].Key=domain OsInfo[9].Value=0 OsInfo[10].Key=prodsuite OsInfo[10].Value=400 OsInfo[11].Key=ntprodtype OsInfo[11].Value=3 OsInfo[12].Key=platid OsInfo[12].Value=10 OsInfo[13].Key=sr OsInfo[13].Value=0 OsInfo[14].Key=tmsi OsInfo[14].Value=1208976 OsInfo[15].Key=osinsty OsInfo[15].Value=2 OsInfo[16].Key=iever OsInfo[16].Value=11.1577.17763.0-11.0.220 OsInfo[17].Key=portos OsInfo[17].Value=0 OsInfo[18].Key=ram OsInfo[18].Value=16384 OsInfo[19].Key=svolsz OsInfo[19].Value=39 OsInfo[20].Key=wimbt OsInfo[20].Value=0 OsInfo[21].Key=blddt OsInfo[21].Value=180914 OsInfo[22].Key=bldtm OsInfo[22].Value=1434 OsInfo[23].Key=bldbrch OsInfo[23].Value=rs5_release OsInfo[24].Key=bldchk OsInfo[24].Value=0 OsInfo[25].Key=wpvermaj OsInfo[25].Value=0 OsInfo[26].Key=wpvermin OsInfo[26].Value=0 OsInfo[27].Key=wpbuildmaj OsInfo[27].Value=0 OsInfo[28].Key=wpbuildmin OsInfo[28].Value=0 OsInfo[29].Key=osver OsInfo[29].Value=10.0.17763.1577.amd64fre.rs5_release.180914-1434 OsInfo[30].Key=buildflightid OsInfo[31].Key=edition OsInfo[31].Value=ServerDatacenter OsInfo[32].Key=ring OsInfo[32].Value=Retail OsInfo[33].Key=expid OsInfo[34].Key=containerid OsInfo[35].Key=containertype OsInfo[36].Key=edu OsInfo[36].Value=0 FriendlyEventName=已停止响应并且被关闭 ConsentKey=AppHangXProcB1 AppName=Sysinternals Process Explorer AppPath=C:\Users\Administrator\Desktop\Tools\procexp64.exe ReportDescription=出现了一个问题,该问题导致了此程序停止与 Windows 进行交互。 NsPartner=windows NsGroup=windows8 ApplicationIdentity=2272DFD0F3138AA55BBA82FB738F8E3D MetadataHash=-1743588442
Loading control script C:\Program Files\DebugDiag\scripts\CrashRule_Process_JXC_MED.exe.vbs DumpPath set to D:\dump [2023/4/13 15:17:53] Process created. BaseModule - D:\Program Files (x86)\ C:\Windows\SYSTEM32\ntdll.dll loaded at 0x77650000 Thread created. New thread - System ID: 3444 Thread created. New thread - System ID: 5816 Thread created. New thread - System ID: 7888 Thread created. New thread - System ID: 4740 Thread created. New thread - System ID: 476 Thread created. New thread - System ID: 10096 Thread created. New thread - System ID: 1548 Thread created. New thread - System ID: 8276 Thread created. New thread - System ID: 5308 Thread created. New thread - System ID: 7268 Thread created. New thread - System ID: 5400 Thread created. New thread - System ID: 1328 Thread created. New thread - System ID: 7672 Thread created. New thread - System ID: 2008 Thread created. New thread - System ID: 3400 Thread created. New thread - System ID: 2324 Thread created. New thread - System ID: 9132 C:\Windows\System32\KERNEL32.DLL loaded at 0x75940000 C:\Windows\System32\KERNELBASE.dll loaded at 0x77250000 C:\Windows\SYSTEM32\apphelp.dll loaded at 0x72740000 C:\Windows\SYSTEM32\AcLayers.DLL loaded at 0x6b230000 C:\Windows\System32\msvcrt.dll loaded at 0x76f30000 C:\Windows\System32\USER32.dll loaded at 0x76d80000 C:\Windows\System32\win32u.dll loaded at 0x77620000 C:\Windows\System32\GDI32.dll loaded at 0x77220000 C:\Windows\System32\gdi32full.dll loaded at 0x77080000 C:\Windows\System32\msvcp_win.dll loaded at 0x774f0000 C:\Windows\System32\ucrtbase.dll loaded at 0x76ad0000 C:\Windows\System32\SHELL32.dll loaded at 0x75c40000 C:\Windows\System32\SHLWAPI.dll loaded at 0x764b0000 C:\Windows\System32\OLEAUT32.dll loaded at 0x77180000 C:\Windows\System32\combase.dll loaded at 0x76680000 C:\Windows\System32\RPCRT4.dll loaded at 0x75a30000 C:\Windows\System32\SETUPAPI.dll loaded at 0x75500000 C:\Windows\System32\cfgmgr32.dll loaded at 0x77480000 C:\Windows\System32\bcrypt.dll loaded at 0x76660000 C:\Windows\SYSTEM32\MPR.dll loaded at 0x71100000 C:\Windows\SYSTEM32\sfc.dll loaded at 0x66680000 C:\Windows\SYSTEM32\WINSPOOL.DRV loaded at 0x71c50000 C:\Windows\SYSTEM32\sfc_os.DLL loaded at 0x6b220000 C:\Windows\SYSTEM32\SortServer2003Compat.dll loaded at 0x73dd0000 C:\Windows\System32\IMM32.DLL loaded at 0x774c0000 C:\Windows\System32\ADVAPI32.dll loaded at 0x769d0000 C:\Windows\System32\sechost.dll loaded at 0x76a50000 C:\Windows\System32\ole32.dll loaded at 0x75b50000 D:\Program Files (x86)\ C:\Windows\WinSxS\x86_microsoft.windows.common-controls_6595b64144ccf1df_5.82.19041.1110_none_c0da534e38c01f4d\COMCTL32.dll loaded at 0x72ef0000 C:\Windows\SYSTEM32\MSVCP60.dll loaded at 0x73cf0000 C:\Windows\SYSTEM32\WSOCK32.dll loaded at 0x74da0000 C:\Windows\System32\WS2_32.dll loaded at 0x76900000 D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ C:\Windows\SYSTEM32\NETAPI32.dll loaded at 0x74de0000 C:\Windows\SYSTEM32\OLEPRO32.DLL loaded at 0x73cd0000 C:\Windows\SYSTEM32\ODBC32.dll loaded at 0x73c30000 C:\Windows\System32\CRYPT32.dll loaded at 0x76c60000 C:\Windows\SYSTEM32\VERSION.dll loaded at 0x754f0000 C:\Windows\SYSTEM32\MSIMG32.dll loaded at 0x74ec0000 C:\Windows\SYSTEM32\DPAPI.DLL loaded at 0x6c840000 C:\Windows\System32\comdlg32.dll loaded at 0x77570000 C:\Windows\System32\shcore.dll loaded at 0x763d0000 C:\Windows\SYSTEM32\WININET.dll loaded at 0x73e10000 D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ D:\Program Files (x86)\ C:\Windows\SYSTEM32\kernel.appcore.dll loaded at 0x74e80000 C:\Windows\System32\bcryptPrimitives.dll loaded at 0x76370000 C:\Windows\system32\uxtheme.dll loaded at 0x70fc0000 C:\Windows\SYSTEM32\dwmapi.dll loaded at 0x707d0000 C:\Windows\System32\MSCTF.dll loaded at 0x76580000 C:\Windows\system32\SQLSRV32.dll loaded at 0x72940000 C:\Windows\SYSTEM32\SspiCli.dll loaded at 0x74f00000 C:\Windows\SYSTEM32\odbccp32.dll loaded at 0x70f50000 C:\Windows\SYSTEM32\CRYPTBASE.dll loaded at 0x72c40000 C:\Windows\System32\msv1_0.DLL loaded at 0x70eb0000 C:\Windows\SYSTEM32\NtlmShared.dll loaded at 0x73dc0000 C:\Windows\SYSTEM32\cryptdll.dll loaded at 0x70e90000 C:\Windows\system32\mswsock.dll loaded at 0x73d60000 C:\Windows\SYSTEM32\DNSAPI.dll loaded at 0x73b90000 C:\Windows\SYSTEM32\IPHLPAPI.DLL loaded at 0x75360000 C:\Windows\System32\NSI.dll loaded at 0x77170000 C:\Windows\System32\rasadhlp.dll loaded at 0x717b0000 C:\Windows\System32\fwpuclnt.dll loaded at 0x716e0000 C:\Windows\System32\schannel.dll loaded at 0x66290000 C:\Windows\SYSTEM32\mskeyprotect.dll loaded at 0x69f20000 C:\Windows\SYSTEM32\NTASN1.dll loaded at 0x68190000 C:\Windows\SYSTEM32\ncrypt.dll loaded at 0x66260000 C:\Windows\system32\ncryptsslp.dll loaded at 0x69f00000 C:\Windows\SYSTEM32\TextShaping.dll loaded at 0x73210000 C:\Windows\SYSTEM32\textinputframework.dll loaded at 0x70d90000 C:\Windows\System32\CoreUIComponents.dll loaded at 0x70b10000 C:\Windows\System32\CoreMessaging.dll loaded at 0x70a70000 C:\Windows\SYSTEM32\wintypes.dll loaded at 0x70990000 C:\Windows\SYSTEM32\ntmarta.dll loaded at 0x71780000 C:\Windows\System32\clbcatq.dll loaded at 0x76500000 C:\Windows\System32\SogouTSF.ime loaded at 0x70800000 C:\Windows\SYSTEM32\windows.storage.dll loaded at 0x732d0000 C:\Windows\SYSTEM32\Wldp.dll loaded at 0x73090000 C:\Windows\system32\SogouPy.ime loaded at 0x088e0000 C:\Windows\SYSTEM32\OLEACC.dll loaded at 0x738e0000 C:\Windows\SYSTEM32\WINHTTP.dll loaded at 0x71b50000 C:\Program Files (x86)\SogouInput\11.8.0.5496\Resource.dll loaded at 0x0a280000 C:\Program Files (x86)\SogouInput\Components\PicFace\1.1.0.1895\PicFace.dll loaded at 0x70610000 C:\Windows\System32\PSAPI.DLL loaded at 0x76f20000 C:\Windows\SYSTEM32\profapi.dll loaded at 0x72280000 C:\Windows\WinSxS\x86_microsoft.windows.common-controls_6595b64144ccf1df_6.0.19041.1110_none_a8625c1886757984\comctl32.DLL loaded at 0x74900000 C:\Windows\SYSTEM32\DBNETLIB.DLL loaded at 0x70f30000 C:\Windows\SYSTEM32\security.dll loaded at 0x46480000 C:\Windows\SYSTEM32\SECUR32.DLL loaded at 0x74f30000 C:\Windows\SYSTEM32\ntdsapi.dll loaded at 0x710e0000 C:\Windows\SYSTEM32\DSPARSE.DLL loaded at 0x722d0000 C:\Windows\SYSTEM32\ODBCCR32.DLL loaded at 0x6c7c0000 C:\Windows\System32\ieframe.dll loaded at 0x66830000 C:\Windows\System32\iertutil.dll loaded at 0x71e30000 C:\Windows\System32\USERENV.dll loaded at 0x754b0000 C:\Windows\System32\NETUTILS.DLL loaded at 0x74dd0000 C:\Windows\System32\WKSCLI.DLL loaded at 0x732b0000 C:\Windows\SYSTEM32\msIso.dll loaded at 0x67050000 C:\Windows\SYSTEM32\urlmon.dll loaded at 0x722e0000 C:\Windows\SYSTEM32\srvcli.dll loaded at 0x721f0000 C:\Windows\SYSTEM32\sxs.dll loaded at 0x6c730000 C:\Windows\SYSTEM32\PROPSYS.dll loaded at 0x71cd0000 C:\Windows\SYSTEM32\virtdisk.dll loaded at 0x651a0000 C:\Windows\SYSTEM32\FLTLIB.DLL loaded at 0x726c0000 C:\Windows\System32\mshtml.dll loaded at 0x62650000 C:\Windows\SYSTEM32\powrprof.dll loaded at 0x712c0000 C:\Windows\SYSTEM32\UMPDC.dll loaded at 0x712b0000 C:\Windows\System32\srpapi.dll loaded at 0x6c7f0000 C:\Windows\system32\mlang.dll loaded at 0x6bd20000 C:\Windows\SYSTEM32\ondemandconnroutehelper.dll loaded at 0x70fa0000 C:\Windows\SYSTEM32\WINNSI.DLL loaded at 0x70f90000 C:\Windows\SYSTEM32\edputil.dll loaded at 0x6bed0000 C:\Windows\System32\Windows.StateRepositoryPS.dll loaded at 0x71310000 C:\Windows\System32\appresolver.dll loaded at 0x6be50000 C:\Windows\System32\Bcp47Langs.dll loaded at 0x6c390000 C:\Windows\System32\SLC.dll loaded at 0x6be30000 C:\Windows\System32\sppc.dll loaded at 0x6be10000 C:\Windows\System32\OneCoreCommonProxyStub.dll loaded at 0x6bdd0000 C:\Windows\System32\OneCoreUAPCommonProxyStub.dll loaded at 0x6b880000 C:\Windows\System32\MSSOAP30.dll loaded at 0x0ec10000 C:\Windows\System32\MSSOAPR3.DLL loaded at 0x0ea80000 C:\Windows\System32\WISC30.dll loaded at 0x0ec80000 C:\Windows\System32\msxml4.dll loaded at 0x69b10000 C:\Windows\system32\napinsp.dll loaded at 0x71760000 C:\Windows\system32\pnrpnsp.dll loaded at 0x71740000 C:\Windows\system32\wshbth.dll loaded at 0x714d0000 C:\Windows\system32\NLAapi.dll loaded at 0x714b0000 C:\Windows\System32\winrnr.dll loaded at 0x714a0000 C:\Windows\system32\msimtf.dll loaded at 0x70f80000 C:\Windows\System32\msls31.dll loaded at 0x6aec0000 C:\Windows\System32\d2d1.dll loaded at 0x10010000 C:\Windows\System32\DWrite.dll loaded at 0x6d0b0000 C:\Windows\System32\dxgi.dll loaded at 0x65f20000 C:\Windows\System32\d3d11.dll loaded at 0x681c0000 C:\Windows\SYSTEM32\d3d10warp.dll loaded at 0x65950000 C:\Windows\system32\windowscodecs.dll loaded at 0x6cab0000 C:\Windows\SYSTEM32\dxcore.dll loaded at 0x69f90000 C:\Windows\System32\jscript9.dll loaded at 0x6bfd0000 C:\Windows\system32\windowscodecsext.dll loaded at 0x6c6f0000 C:\Windows\System32\msxml6.dll loaded at 0x6c510000 C:\Windows\System32\msxml3.dll loaded at 0x6b730000 C:\Windows\SYSTEM32\pcacli.dll loaded at 0x6c4f0000 Thread created. New thread - System ID: 10028 Initializing control script Clearing any existing breakpoints Current Breakpoint List(BL) [2023/4/13 15:17:56] Thread exited. Exiting thread - System ID: 10028. Exit code - 0x00000000 [2023/4/13 15:18:06] Thread created. New thread - System ID: 4968 Thread created. New thread - System ID: 6876 Thread created. New thread - System ID: 9888 [2023/4/13 15:18:12] Thread created. New thread - System ID: 8908 [2023/4/13 15:18:16] Exception 0XE06D7363 on thread 8908. DetailID = 1 [2023/4/13 15:18:17] Exception 0XC0000005 on thread 1548. DetailID = 2 [2023/4/13 15:18:26] Second chance exception - 0XC0000005 caused by thread with System ID: 1548 DetailID = 2 Thread exited. Exiting thread - System ID: 7888. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 6932. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 5816. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 476. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 10096. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 3444. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 4740. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 5308. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 7268. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 5400. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 8276. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 7672. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 3400. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 1328. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 2324. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 4968. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 9132. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 6876. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 2008. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 9888. Exit code - 0xffffffff Thread exited. Exiting thread - System ID: 8908. Exit code - 0xffffffff Process exited. Exit code - 0xffffffff *********************** * EXCEPTION DETAILS * *********************** DetailID = 1 Count: 1 Exception #: 0XE06D7363 Stack: DetailID = 2 Count: 2 Exception #: 0XC0000005 Stack: *********************** * EXCEPTION SUMMARY * *********************** |--------------------| | Count | Exception | |--------------------| | 2 | 0XC0000005 | | 1 | 0XE06D7363 | |--------------------| Debugging Overhead Cost: Total Elapsed Ticks = 32656 (100%) Total Ticks Spent in Debugger Engine = 11500 (35%) Total Ticks Spent in Crash Rule Script = 5437 (17%)
C:\ProgramData\Microsoft\Windows\WER
Collecting User-Mode Dumps
Starting with Windows Server 2008 and Windows Vista with Service Pack 1 (SP1), Windows Error Reporting (WER) can be configured so that full user-mode dumps are collected and stored locally after a user-mode application crashes. Applications that do their own custom crash reporting, including .NET applications, are not supported by this feature.
This feature is not enabled by default. Enabling the feature requires administrator privileges. To enable and configure the feature, use the following registry values under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps key.
| Value | Description | Type | Default value |
|---|---|---|---|
| DumpFolder | The path where the dump files are to be stored. If you do not use the default path, then make sure that the folder contains ACLs that allow the crashing process to write data to the folder. For service crashes, the dump is written to service specific profile folders depending on the service account used. For example, the profile folder for System services is %WINDIR%\System32\Config\SystemProfile. For Network and Local Services, the folder is %WINDIR%\ServiceProfiles. | REG_EXPAND_SZ | %LOCALAPPDATA%\CrashDumps |
| DumpCount | The maximum number of dump files in the folder. When the maximum value is exceeded, the oldest dump file in the folder will be replaced with the new dump file. | REG_DWORD | 10 |
| DumpType | Specify one of the following dump types:
|
REG_DWORD | 1 |
| CustomDumpFlags | The custom dump options to be used. This value is used only when DumpType is set to 0. The options are a bitwise combination of the MINIDUMP_TYPE enumeration values. |
REG_DWORD0x00000121 (MiniDumpWithDataSegs MiniDumpWithUnloadedModules MiniDumpWithProcessThreadData == 0x00000001 0x00000020 0x00000100) |
Note
A crash dump is not collected when you set automatic debugging for application crashes.
These registry values represent the global settings. You can also provide per-application settings that override the global settings. To create a per-application setting, create a new key for your application under HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Windows Error Reporting\LocalDumps (for example, HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Windows Error Reporting\LocalDumps\MyApplication.exe). Add your dump settings under the MyApplication.exe key. If your application crashes, WER will first read the global settings, and then will override any of the settings with your application-specific settings.
After an application crashes and prior to its termination, the system will check the registry settings to determine whether a local dump is to be collected. After the dump collection has completed, the application will be allowed to terminate normally. If the application supports recovery, the local dump is collected before the recovery callback is called.
These dumps are configured and controlled independently of the rest of the WER infrastructure. You can make use of the local dump collection even if WER is disabled or if the user cancels WER reporting. The local dump can be different than the dump sent to Microsoft.
南来地,北往的,上班的,下岗的,走过路过不要错过!
======================个性签名=====================
之前认为Apple 的iOS 设计的要比 Android 稳定,我错了吗?
下载的许多客户端程序/游戏程序,经常会Crash,是程序写的不好(内存泄漏?刚启动也会吗?)还是iOS本身的不稳定!!!
如果在Android手机中可以简单联接到ddms,就可以查看系统log,很容易看到程序为什么出错,在iPhone中如何得知呢?试试Organizer吧,分析一下Device logs,也许有用.


 @ioriwellings
@ioriwellings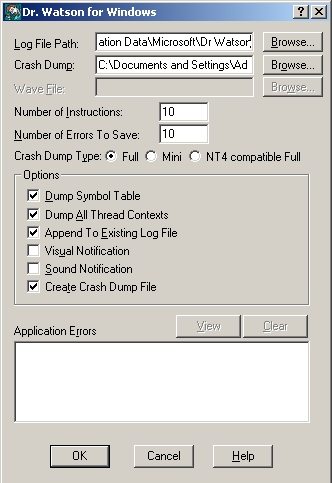








【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· .NET周刊【3月第1期 2025-03-02】
· 分享 3 个 .NET 开源的文件压缩处理库,助力快速实现文件压缩解压功能!
· Ollama——大语言模型本地部署的极速利器
2015-01-27 rand & random & arc4random