openssl https 证书
####################
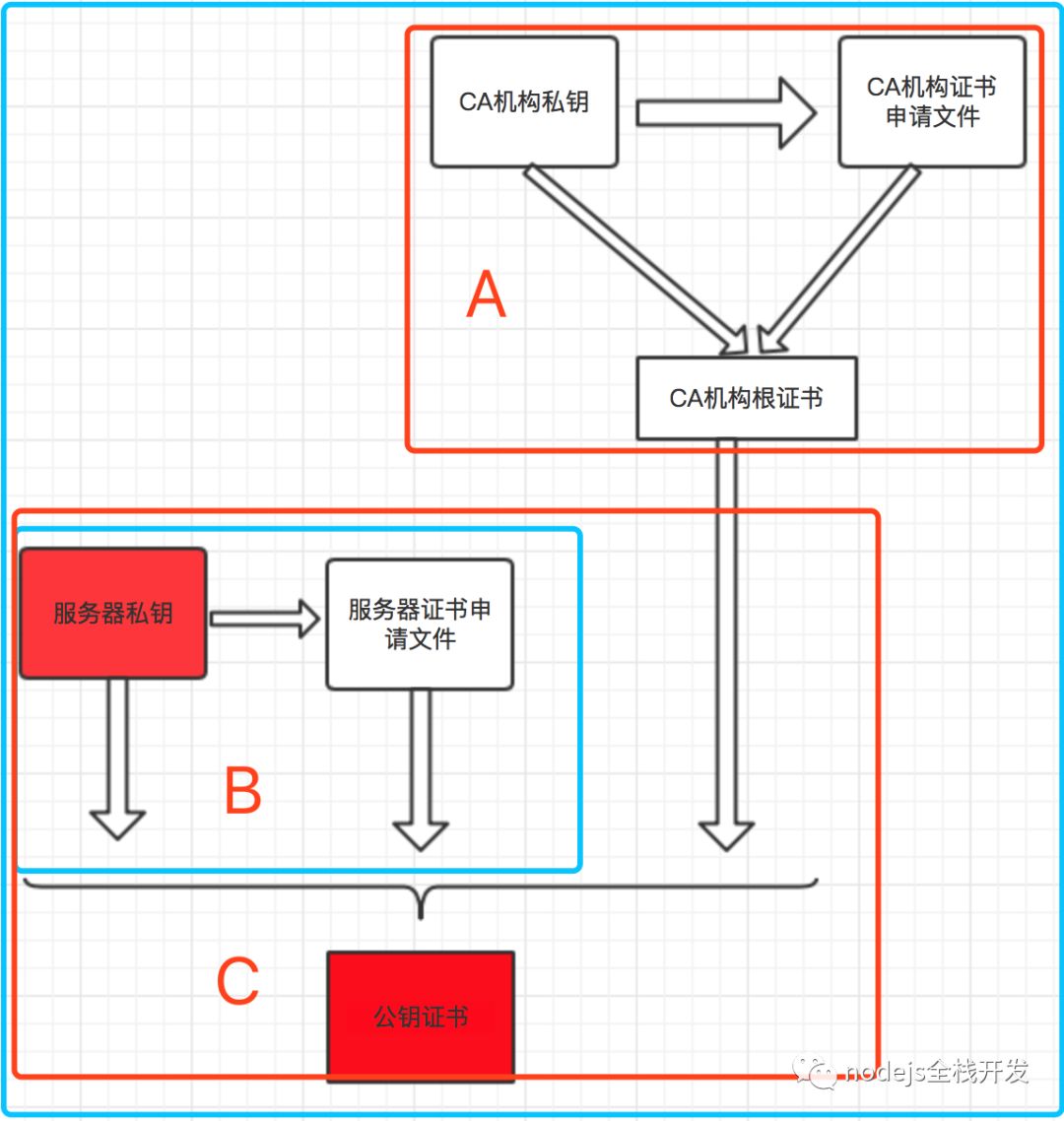
# 一、生成CA机构的私钥,命令和生成服务器私钥一样,只不过这是CA的私钥 >> ca.key openssl genrsa -out ca.key 4096 # 二、生成CA机构自己的证书申请文件 >> ca.crt openssl req -new -sha512 -subj "/C=CN/ST=hubei/L=wuhan/O=igoodful/OU=igoodful/CN=registry.igoodful.com/emailAddress=igoodful@qq.com" -key ca.key -out ca.csr # 三、生成自签名证书,CA机构用自己的私钥和证书申请文件生成自己签名的证书,俗称自签名证书,这里可以理解为根证书 # -nodes 表示私钥不加密,若不带参数将提示输入密码; # x509的含义: 指定格式 # -in的含义: 指定请求文件 # -signkey的含义: 自签名 openssl x509 -req -sha512 -days 3650 -extensions v3_ca -signkey ca.key -in ca.csr -out ca.crt ------------------------------------------------------------------------------------------------------- # 一、生成服务器私钥。nginx中要求的server.key openssl genrsa -out server.key 4096 # 二、请求证书。根据服务器私钥文件生成证书请求文件,这个文件中会包含申请人的一些信息,注意: 这一步也会输入参数,要和上一次输入的保持一致 openssl req -new -sha512 -subj "/C=CN/ST=hubei/L=wuhan/O=igoodful/OU=igoodful/CN=registry.igoodful.com/emailAddress=igoodful@qq.com" -key server.key -out server.csr # 三、使用CA证书签署服务器证书。根据CA机构的自签名证书ca.crt或者叫根证书生、CA机构的私钥ca.key、服务器的证书申请文件server.csr生成服务端证书 # 请求证书,nginx中要求的server.crt # 证数各参数含义如下 # C 国家 Country Name # ST----省份 State or Province Name # L----城市 Locality Name # O----公司 Organization Name # OU----部门 Organizational Unit Name # CN----产品名 Common Name # emailAddress----邮箱 Email Address openssl x509 -req -sha512 -days 3650 -extensions v3_req -CAserial ca.srl -CAcreateserial -CA ca.crt -CAkey ca.key -in server.csr -out server.crt --------------------------------------------------------------------------------------- # 生成客户端证书 # 一、生成客户端私钥 openssl genrsa -out client.key 4096 # 二、申请证书,注意:这一步也会输入参数,要和前两次输入的保持一致 openssl req -new -sha512 -subj "/C=CN/ST=hubei/L=wuhan/O=igoodful/OU=igoodful/CN=registry.igoodful.com/emailAddress=igoodful@qq.com" -key client.key -out client.csr # 三、使用CA证书签署客户端证书 openssl x509 -req -sha512 -days 3650 -CAcreateserial -in client.csr -CA ca.crt -CAkey ca.key -out client.cer -extensions v3_req
------------------------------------------------------------------------ # ca证书 openssl req -newkey rsa:2048 -nodes -keyout ca.key -out ca.csr -subj "/C=CN/ST=hubei/L=wuhan/O=igoodful/OU=igoodful/CN=registry.igoodful.com/emailAddress=igoodful@qq.com" # openssl x509 -req -days 3650 -in ca.csr -signkey ca.key -out ca.crt --------------------------------------------------------------------------------- # 服务端 openssl genrsa -out server.key 2048 # 注意: 这一步也会输入参数,要和上一次输入的保持一致 openssl req -new -key server.key -out server.csr -subj "/C=CN/ST=hubei/L=wuhan/O=igoodful/OU=igoodful/CN=registry.igoodful.com/emailAddress=igoodful@qq.com" # openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out server.crt -days 3650 ------------------------------------------------------------------------- # 客户端 openssl genrsa -out client.key 2048 # 注意:这一步也会输入参数,要和前两次输入的保持一致 openssl req -new -subj "/C=CN/ST=hubei/L=wuhan/O=igoodful/OU=igoodful/CN=registry.igoodful.com/emailAddress=igoodful@qq.com" -key client.key -out client.csr # openssl x509 -req -days 3650 -CAcreateserial -in client.csr -CA ca.crt -CAkey ca.key -out client.crt # 配置示例(Nginx): server { listen 80; listen 443 ssl; server_name 172.21.10.101; ssl_certificate /opt/server.crt; ssl_certificate_key /opt/server.key; if ($scheme = http) { return 301 https://$host$uri?$args; } #charset koi8-r; #access_log logs/host.access.log main; location / { #root html; #index index.html index.htm; proxy_pass http://172.xx.xx.xx:9000/xxx/xxx/; } error_page 500 502 503 504 /50x.html; location = /50x.html { root html; } } # 配置示例(Apache): <VirtualHost *:443> ServerName example.com SSLEngine on SSLCertificateFile /path/to/server.crt SSLCertificateKeyFile /path/to/server.key SSLCACertificateFile /path/to/ca.crt ... </VirtualHost> # 配置示例(Tomcat): <Connector port="8443" protocol="HTTP/1.1" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" keystoreFile="/path/to/server.keystore" keystorePass="password" truststoreFile="/path/to/ca.crt" truststorePass="password" clientAuth="true" sslProtocol="TLS"/>
1. 登录阿里云Docker Registry
$ docker login --username=igoodful registry.cn-hangzhou.aliyuncs.com用于登录的用户名为阿里云账号全名,密码为开通服务时设置的密码。
您可以在访问凭证页面修改凭证密码。
2. 从Registry中拉取镜像
$ docker pull registry.cn-hangzhou.aliyuncs.com/igoodful/igoodful:[镜像版本号]3. 将镜像推送到Registry
$ docker login --username=igoodful registry.cn-hangzhou.aliyuncs.com$ docker tag [ImageId] registry.cn-hangzhou.aliyuncs.com/igoodful/igoodful:[镜像版本号]$ docker push registry.cn-hangzhou.aliyuncs.com/igoodful/igoodful:[镜像版本号]
请根据实际镜像信息替换示例中的[ImageId]和[镜像版本号]参数。
4. 选择合适的镜像仓库地址
从ECS推送镜像时,可以选择使用镜像仓库内网地址。推送速度将得到提升并且将不会损耗您的公网流量。
如果您使用的机器位于VPC网络,请使用 registry-vpc.cn-hangzhou.aliyuncs.com 作为Registry的域名登录。
5. 示例
使用"docker tag"命令重命名镜像,并将它通过专有网络地址推送至Registry。
$ docker imagesREPOSITORY TAG IMAGE ID CREATED VIRTUAL SIZEregistry.aliyuncs.com/acs/agent 0.7-dfb6816 37bb9c63c8b2 7 days ago 37.89 MB$ docker tag 37bb9c63c8b2 registry-vpc.cn-hangzhou.aliyuncs.com/acs/agent:0.7-dfb6816
使用 "docker push" 命令将该镜像推送至远程。
$ docker push registry-vpc.cn-hangzhou.aliyuncs.com/acs/agent:0.7-dfb6816
Quick setup — if you’ve done this kind of thing before
Get started by creating a new file or uploading an existing file. We recommend every repository include a README, LICENSE, and .gitignore.
…or create a new repository on the command line
echo "# aliyun" >> README.md
git init
git add README.md
git commit -m "first commit"
git branch -M main
git remote add origin https://github.com/igoodful/aliyun.git
git push -u origin main
…or push an existing repository from the command line
git remote add origin https://github.com/igoodful/aliyun.git
git branch -M main
git push -u origin main
…or import code from another repository
You can initialize this repository with code from a Subversion, Mercurial, or TFS project.
ca和服务器证书生成脚本
#!/bin/bash # 如果使用FQDN连接Harbor主机,则必须将其指定为通用名称(CN)属性,因此该名称就写为CN C='CN' # ST表示省份,这里写为湖北 ST='hubei' # L表示城市,这里写为武汉 L='wuhan' # O表示公司名称 O='apple' # OU表示部门 OU='igoodful' # emailAddress表示你的邮箱 emailAddress='igoodful@qq.com' # CN表示你的域名,就是我们的核心目标,比如你的网站是https://www.google.com,那么这里的CN就是www.google.com ,这里不要乱填写,这也是最重要的配置 CN='registry.igoodful.com' # 域名去掉后缀剩下的部分 CN_PREFX='registry.igoodful' # 配置主机名称, HOSTNAME='' if [ "$HOSTNAME" = "" ]; then HOSTNAME=$(hostname) fi # 生成CA私钥和CA证书 function create_ca() { openssl genrsa -out ca.key 4096 openssl req -x509 -new -nodes -sha512 -days 3650 -subj "/C=${C}/ST=${ST}/L=${L}/O=${O}/OU=${OU}/CN=${CN}/emailAddress=${emailAddress}" -key ca.key -out ca.crt } # 根据CA证书生成服务器私钥、生成服务器证书签名请求、生成一个x509的v3扩展文件,服务器证书 function create_server_ca() { # openssl genrsa -out ${CN}.key 4096 # openssl req -sha512 -new -subj "/C=${C}/ST=${ST}/L=${L}/O=${O}/OU=${OU}/CN=${CN}/emailAddress=${emailAddress}" -key ${CN}.key -out ${CN}.csr # cat >v3.ext <<-EOF authorityKeyIdentifier=keyid,issuer basicConstraints=CA:FALSE keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth subjectAltName = @alt_names [alt_names] DNS.1=${CN} DNS.2=${CN_PREFX} DNS.3=${HOSTNAME} EOF # openssl x509 -req -sha512 -days 3650 -extfile v3.ext -CA ca.crt -CAkey ca.key -CAcreateserial -in ${CN}.csr -out ${CN}.crt # openssl x509 -inform PEM -in ${CN}.crt -out ${CN}.cert } function main() { create_ca create_server_ca } main
#######################
igoodful@qq.com

