获取句柄的类型以及对应的ID序号
遍历所有进程下的所有句柄,以及对应句柄类型.
一丶简介
在有的时候.我们会需要对应句柄名字.以及句柄类型的名称. 以及它所对应的的ID. 因为每个系统不一样.所以每次都是不一样的. 有的时候我们就需要借助Pchunter等类似的 Ark工具查看句柄名字. 以及对应的类型.
二丶原理讲解
想要获取 指定进程下的所有句柄,以及句柄名字. 句柄类型.我们只需要几步即可.
1.使用未导出API ZwQuerySystemInformation 获取系统所有进程信息.
2.根据PID打开进程句柄.(可以跳过自己)
3.挂起进程(目的进程)
4.使用未导出函数 ZwQueryInfromationProcess获取目的进程句柄的总个数
5.使用句柄拷贝函数 将目的进程中的所有句柄拷贝到本进程中来.
6.使用未导出函数 NtQueryObject 的2号功能.获取句柄信息. (包括句柄名,句柄的序号);
原理其实不难.就是调用API的事情.这里记录一下.
三丶实战
1.获取导出函数以及变量赋值.
导出函数声明为函数指针
ZwSystemInformation
typedef NTSTATUS(WINAPI * PfnZwQuerySystemInformation)(
IN ULONG SysInfoClass,
IN OUT PVOID SystemInfroMation,
IN ULONG SystemInforMationLength,
OUT PULONG RetLen);
NtQueryObject
typedef enum _OBJECT_INFORMATION_CLASS {
ObjectBasicInformation = 0, //如果为1表示获取名字信息
ObjectTypeInformation = 2 //表示获取类型信息
} OBJECT_INFORMATION_CLASS;
//单独对象获取打开句柄的信息
typedef NTSTATUS(WINAPI * PfnZwQueryObject)(
_In_opt_ HANDLE Handle, //句柄
_In_ OBJECT_INFORMATION_CLASS ObjectInformationClass, //要获取的类型信息
PVOID ObjectInformation, //缓冲区 用户模式下使用 NtQueryObject
_In_ ULONG ObjectInformationLength, _Out_opt_ //缓冲区大小
PULONG ReturnLength);
根据类型,Buffer信息为以下结构
类型为2:
typedef struct _PUBLIC_OBJECT_TYPE_INFORMATION {
UNICODE_STRING TypeName;
ULONG TotalNumberOfHandles;
ULONG TotalNumberOfObjects;
WCHAR Unused1[8];
ULONG HighWaterNumberOfHandles;
ULONG HighWaterNumberOfObjects;
WCHAR Unused2[8];
ACCESS_MASK InvalidAttributes;
GENERIC_MAPPING GenericMapping;
ACCESS_MASK ValidAttributes;
BOOLEAN SecurityRequired;
BOOLEAN MaintainHandleCount;
USHORT MaintainTypeList;
POOL_TYPE PoolType;
ULONG DefaultPagedPoolCharge;
ULONG DefaultNonPagedPoolCharge;
BYTE Unknown2[16];
} PUBLIC_OBJECT_TYPE_INFORMATION, *PPUBLIC_OBJECT_TYPE_INFORMATION;
类型为0:
typedef struct _PUBLIC_OBJECT_BASIC_INFORMATION {
ULONG Attributes;
ACCESS_MASK GrantedAccess;
ULONG HandleCount;
ULONG PointerCount;
ULONG Reserved[10];
} PUBLIC_OBJECT_BASIC_INFORMATION, *PPUBLIC_OBJECT_BASIC_INFORMATION;
关于类型为2,主要注意这个结构体.这里面的成员 MaintainTypeList记录的就是句柄对应的需要. TypeName记录的就是句柄类型名称
ZwQueryInformationProcess
typedef NTSTATUS (WINAPI* PfnZwQueryInformationProcess)(
_In_ HANDLE ProcessHandle,
_In_ PROCESSINFOCLASS ProcessInformationClass, //根据类型信息获取不同的信息
_Out_ PVOID ProcessInformation,
_In_ ULONG ProcessInformationLength,
_Out_opt_ PULONG ReturnLength
);
获取未导出函数
PfnZwQueryInformationProcess ZwQueryInformationProcess = reinterpret_cast<PfnZwQueryInformationProcess>(g_PsOpt.MmGetAddress(TEXT("ntdll.dll"), "ZwQueryInformationProcess"));
//根据进程句柄获取名字信息.
PfnZwQueryObject g_NtQueryObject = reinterpret_cast<PfnZwQueryObject>(g_PsOpt.MmGetAddress(TEXT("ntdll.dll"), "NtQueryObject"));
PfnZwQuerySystemInformation ZwQuerySystemInformation = reinterpret_cast<PfnZwQuerySystemInformation>(g_PsOpt.MmGetAddress(TEXT("ntdll.dll"),"ZwQuerySystemInformation"));
//根据句柄获取文件名路径.
PfnNtQueryInformationFile ZwQueryInformationFile = reinterpret_cast<PfnNtQueryInformationFile>(g_PsOpt.MmGetAddress(TEXT("ntdll.dll"), "ZwQueryInformationFile"));
其中我是封装了一个类,类里面的提供了个方法叫做MmGetAddress.其实就是对loadlibrary + GetProAddress的封装. 因为导出函数都是在Ntdll中.
2.编程实战
根据上方所定义则可以进行遍历操作了.但是要说的一点就是.上方你看做伪代码即可. 因为成员需要用到的结构很多. 网上一搜一大堆. 我这里会把这些结构放到最下面. 现在只需要知道会用到即可.
伪核心代码:
hProcess = PsOpt.PsGetProcess(dwPid); // 根据PROCESS 读取.
PsOpt.PsSusPendProcess(dwPid);//挂起
ZwQueryInformationProcess(hProcess, ProcessHandleCount, &handlecount, sizeof(handlecount), NULL); //hc == 句柄个数
HANDLE hTarHandle;
for (DWORD64 i = 0; i < 400000; i+=4)
{
if (1 == DuplicateHandle(hProcess, (HANDLE)i, GetCurrentProcess(), &hTarHandle, 0, 0, DUPLICATE_SAME_ACCESS))
{
//使用NtQueryObject遍历这个句柄信息
ULONG uRetLength = 0;
char * Buffer = new char[0x100]();
OBJECT_INFORMATION_CLASS ob = ObjectTypeInformation;
g_NtQueryObject(hTarHandle, ob, Buffer, 0x100, &uRetLength);
PPUBLIC_OBJECT_TYPE_INFORMATION pBuffer = reinterpret_cast<PPUBLIC_OBJECT_TYPE_INFORMATION>(Buffer); //查询类型信息
printf("句柄名字为: %ws \t 句柄类型为: %d \t \r\n", pBuffer->TypeName.Buffer, pBuffer->MaintainTypeList);
}
代码讲解
1.根据PID获取hProcess(自己封装的)
2.根据PID挂起这个进程
3.ZwQueryInfromationProcess 传入类型为ProcessHandleCount (20) 遍历这个进程的所有句柄个数.其中传入的HandleCount就是句柄个数.
关于ProcessHandleCount是ZwQueryInformationProcess用的结构.会放到下面.
4.因为知道句柄个数.但是不知道哪个句柄有效.所有直接遍历.通过DupLicateHandle进行拷贝.拷贝成功的就是有效句柄.
5.拷贝成功的句柄使用NtQueryObject进行遍历.使用第二号功能.传出的结构是上方定义的 PUBLIC_OBJECT_TYPE_INFORMATION 然后转化依稀.
6.输出结构的句柄号.以及句柄名称.
ps: 因为是控制台可能有些没显示或者覆盖了.大概看看对不对即可.
pchunter查看.
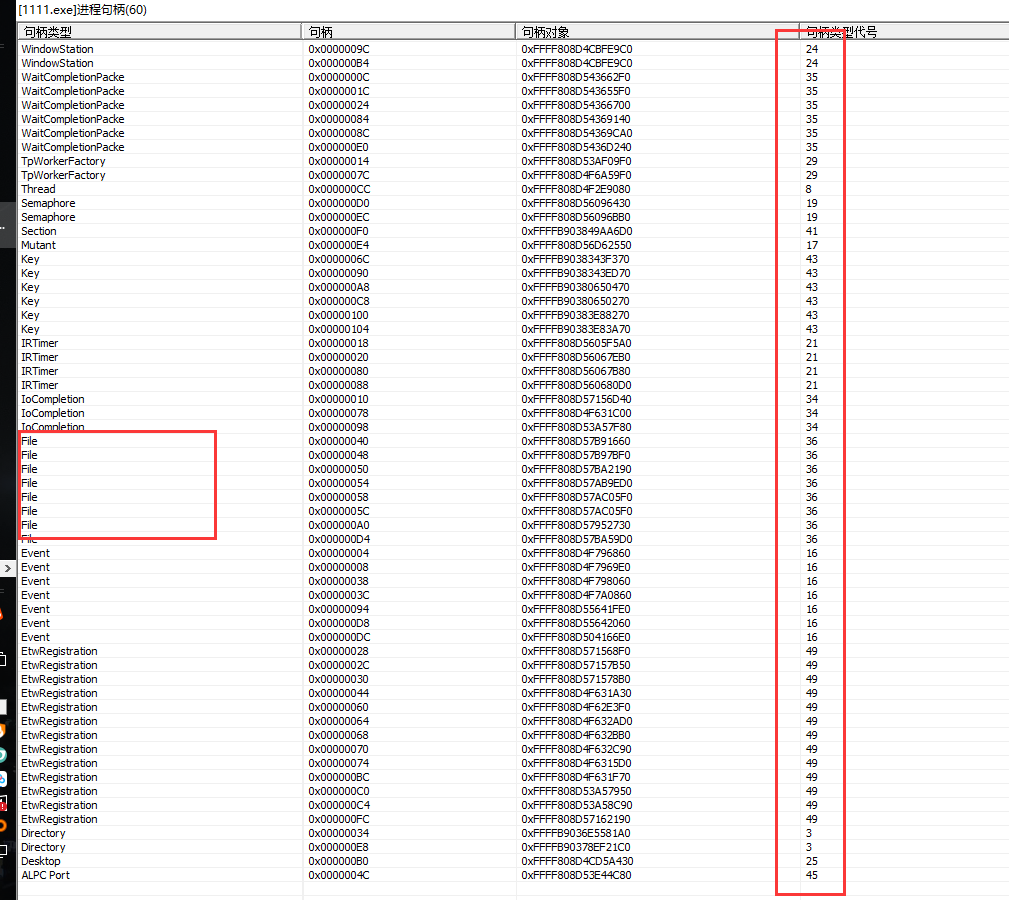
可以看到.File类型的类型确实也是 36. 因为每个系统不一样.所以我们有时候特别需要这个序号.
而使用ZwQuerySystemInformation的时候是可以遍历全局句柄表的.并且得出它的EPROCESS以及 句柄类型. 那个没有写.自己调试看过.现在把这个记录一下.
3.用到的结构
用到的结构如下:
为了方便拷贝.不放.h文件了.直接将里面结构拷贝出来.改改即可.
这是用到所以临时写的.所以拷贝出来的结构很多用不到.可以删除.懒得删了.
#pragma once
#include <windows.h>
#include <string>
using namespace std;
#ifdef UNICODE
#define CBinString wstring
#else
#define CBinString string
#endif
#ifdef _WIN64
#define UBinSize DWORD64
#else
#define UBinSize DWORD
#endif
typedef LONG NTSTATUS;
#define STATUS_SUCCESS ((NTSTATUS)0x00000000L)
#define STATUS_UNSUCCESSFUL ((NTSTATUS)0xC0000001L)
#define STATUS_NOT_IMPLEMENTED ((NTSTATUS)0xC0000002L)
#define STATUS_INVALID_INFO_CLASS ((NTSTATUS)0xC0000003L)
#define STATUS_INFO_LENGTH_MISMATCH ((NTSTATUS)0xC0000004L)
typedef enum _SYSTEM_INFORMATION_CLASS
{
SystemBasicInformation, // 0 Y N
SystemProcessorInformation, // 1 Y N
SystemPerformanceInformation, // 2 Y N
SystemTimeOfDayInformation, // 3 Y N
SystemNotImplemented1, // 4 Y N
SystemProcessesAndThreadsInformation, // 5 Y N
SystemCallCounts, // 6 Y N
SystemConfigurationInformation, // 7 Y N
SystemProcessorTimes, // 8 Y N
SystemGlobalFlag, // 9 Y Y
SystemNotImplemented2, // 10 Y N
SystemModuleInformation, // 11 Y N
SystemLockInformation, // 12 Y N
SystemNotImplemented3, // 13 Y N
SystemNotImplemented4, // 14 Y N
SystemNotImplemented5, // 15 Y N
SystemHandleInformation, // 16 Y N
SystemObjectInformation, // 17 Y N
SystemPagefileInformation, // 18 Y N
SystemInstructionEmulationCounts, // 19 Y N
SystemInvalidInfoClass1, // 20
SystemCacheInformation, // 21 Y Y
SystemPoolTagInformation, // 22 Y N
SystemProcessorStatistics, // 23 Y N
SystemDpcInformation, // 24 Y Y
SystemNotImplemented6, // 25 Y N
SystemLoadImage, // 26 N Y
SystemUnloadImage, // 27 N Y
SystemTimeAdjustment, // 28 Y Y
SystemNotImplemented7, // 29 Y N
SystemNotImplemented8, // 30 Y N
SystemNotImplemented9, // 31 Y N
SystemCrashDumpInformation, // 32 Y N
SystemExceptionInformation, // 33 Y N
SystemCrashDumpStateInformation, // 34 Y Y/N
SystemKernelDebuggerInformation, // 35 Y N
SystemContextSwitchInformation, // 36 Y N
SystemRegistryQuotaInformation, // 37 Y Y
SystemLoadAndCallImage, // 38 N Y
SystemPrioritySeparation, // 39 N Y
SystemNotImplemented10, // 40 Y N
SystemNotImplemented11, // 41 Y N
SystemInvalidInfoClass2, // 42
SystemInvalidInfoClass3, // 43
SystemTimeZoneInformation, // 44 Y N
SystemLookasideInformation, // 45 Y N
SystemSetTimeSlipEvent, // 46 N Y
SystemCreateSession, // 47 N Y
SystemDeleteSession, // 48 N Y
SystemInvalidInfoClass4, // 49
SystemRangeStartInformation, // 50 Y N
SystemVerifierInformation, // 51 Y Y
SystemAddVerifier, // 52 N Y
SystemSessionProcessesInformation // 53 Y N
} SYSTEM_INFORMATION_CLASS;
typedef struct _LSA_UNICODE_STRING
{
USHORT Length;
USHORT MaximumLength;
PWSTR Buffer;
} LSA_UNICODE_STRING, *PLSA_UNICODE_STRING, UNICODE_STRING, *PUNICODE_STRING;
typedef struct _CLIENT_ID
{
HANDLE UniqueProcess;
HANDLE UniqueThread;
} CLIENT_ID;
typedef enum _THREAD_STATE
{
StateInitialized,
StateReady,
StateRunning,
StateStandby,
StateTerminated,
StateWait,
StateTransition,
StateUnknown
} THREAD_STATE;
typedef enum _KWAIT_REASON
{
Executive,
FreePage,
PageIn,
PoolAllocation,
DelayExecution,
Suspended,
UserRequest,
WrExecutive,
WrFreePage,
WrPageIn,
WrPoolAllocation,
WrDelayExecution,
WrSuspended,
WrUserRequest,
WrEventPair,
WrQueue,
WrLpcReceive,
WrLpcReply,
WrVirtualMemory,
WrPageOut,
WrRendezvous,
Spare2,
Spare3,
Spare4,
Spare5,
Spare6,
WrKernel
} KWAIT_REASON;
/*typedef struct _IO_COUNTERS
{
LARGE_INTEGER ReadOperationCount; //I/O读操作数目
LARGE_INTEGER WriteOperationCount; //I/O写操作数目
LARGE_INTEGER OtherOperationCount; //I/O其他操作数目
LARGE_INTEGER ReadTransferCount; //I/O读数据数目
LARGE_INTEGER WriteTransferCount; //I/O写数据数目
LARGE_INTEGER OtherTransferCount; //I/O其他操作数据数目
} IO_COUNTERS, *PIO_COUNTERS;
*/
typedef struct _VM_COUNTERS
{
ULONG PeakVirtualSize; //虚拟存储峰值大小
ULONG VirtualSize; //虚拟存储大小
ULONG PageFaultCount; //页故障数目
ULONG PeakWorkingSetSize; //工作集峰值大小
ULONG WorkingSetSize; //工作集大小
ULONG QuotaPeakPagedPoolUsage; //分页池使用配额峰值
ULONG QuotaPagedPoolUsage; //分页池使用配额
ULONG QuotaPeakNonPagedPoolUsage; //非分页池使用配额峰值
ULONG QuotaNonPagedPoolUsage; //非分页池使用配额
ULONG PagefileUsage; //页文件使用情况
ULONG PeakPagefileUsage; //页文件使用峰值
} VM_COUNTERS, *PVM_COUNTERS;
typedef LONG KPRIORITY;
typedef struct _SYSTEM_THREADS
{
LARGE_INTEGER KernelTime;
LARGE_INTEGER UserTime;
LARGE_INTEGER CreateTime;
ULONG WaitTime;
PVOID StartAddress;
CLIENT_ID ClientId;
KPRIORITY Priority;
KPRIORITY BasePriority;
ULONG ContextSwitchCount;
THREAD_STATE State;
KWAIT_REASON WaitReason;
} SYSTEM_THREADS, *PSYSTEM_THREADS;
typedef struct _SYSTEM_PROCESSES
{
ULONG NextEntryDelta;
ULONG ThreadCount;
ULONG Reserved1[6];
LARGE_INTEGER CreateTime;
LARGE_INTEGER UserTime;
LARGE_INTEGER KernelTime;
UNICODE_STRING ProcessName;
KPRIORITY BasePriority;
ULONG ProcessId;
ULONG InheritedFromProcessId;
ULONG HandleCount;
ULONG Reserved2[2];
VM_COUNTERS VmCounters;
IO_COUNTERS IoCounters;
SYSTEM_THREADS Threads[1];
} SYSTEM_PROCESSES, *PSYSTEM_PROCESSES;
typedef struct _SYSTEM_BASIC_INFORMATION
{
BYTE Reserved1[24];
PVOID Reserved2[4];
CCHAR NumberOfProcessors;
} SYSTEM_BASIC_INFORMATION;
typedef struct tagSYSTEM_MODULE_INFORMATION {
ULONG Reserved[2];
PVOID Base;
ULONG Size;
ULONG Flags;
USHORT Index;
USHORT Unknown;
USHORT LoadCount;
USHORT ModuleNameOffset;
CHAR ImageName[256];
} SYSTEM_MODULE_INFORMATION, *PSYSTEM_MODULE_INFORMATION;
//ZwQueryInformationProcess 遍历进程信息.
typedef enum _PROCESSINFOCLASS {
ProcessBasicInformation = 0,
ProcessQuotaLimits = 1,
ProcessIoCounters = 2,
ProcessVmCounters = 3,
ProcessTimes = 4,
ProcessBasePriority = 5,
ProcessRaisePriority = 6,
ProcessDebugPort = 7,
ProcessExceptionPort = 8,
ProcessAccessToken = 9,
ProcessLdtInformation = 10,
ProcessLdtSize = 11,
ProcessDefaultHardErrorMode = 12,
ProcessIoPortHandlers = 13, // Note: this is kernel mode only
ProcessPooledUsageAndLimits = 14,
ProcessWorkingSetWatch = 15,
ProcessUserModeIOPL = 16,
ProcessEnableAlignmentFaultFixup = 17,
ProcessPriorityClass = 18,
ProcessWx86Information = 19,
ProcessHandleCount = 20,
ProcessAffinityMask = 21,
ProcessPriorityBoost = 22,
ProcessDeviceMap = 23,
ProcessSessionInformation = 24,
ProcessForegroundInformation = 25,
ProcessWow64Information = 26,
ProcessImageFileName = 27,
ProcessLUIDDeviceMapsEnabled = 28,
ProcessBreakOnTermination = 29,
ProcessDebugObjectHandle = 30,
ProcessDebugFlags = 31,
ProcessHandleTracing = 32,
ProcessIoPriority = 33,
ProcessExecuteFlags = 34,
ProcessTlsInformation = 35,
ProcessCookie = 36,
ProcessImageInformation = 37,
ProcessCycleTime = 38,
ProcessPagePriority = 39,
ProcessInstrumentationCallback = 40,
ProcessThreadStackAllocation = 41,
ProcessWorkingSetWatchEx = 42,
ProcessImageFileNameWin32 = 43,
ProcessImageFileMapping = 44,
ProcessAffinityUpdateMode = 45,
ProcessMemoryAllocationMode = 46,
ProcessGroupInformation = 47,
ProcessTokenVirtualizationEnabled = 48,
ProcessOwnerInformation = 49,
ProcessWindowInformation = 50,
ProcessHandleInformation = 51,
ProcessMitigationPolicy = 52,
ProcessDynamicFunctionTableInformation = 53,
ProcessHandleCheckingMode = 54,
ProcessKeepAliveCount = 55,
ProcessRevokeFileHandles = 56,
ProcessWorkingSetControl = 57,
ProcessHandleTable = 58,
ProcessCheckStackExtentsMode = 59,
ProcessCommandLineInformation = 60,
ProcessProtectionInformation = 61,
ProcessMemoryExhaustion = 62,
ProcessFaultInformation = 63,
ProcessTelemetryIdInformation = 64,
ProcessCommitReleaseInformation = 65,
ProcessReserved1Information = 66,
ProcessReserved2Information = 67,
ProcessSubsystemProcess = 68,
ProcessInPrivate = 70,
ProcessRaiseUMExceptionOnInvalidHandleClose = 71,
ProcessSubsystemInformation = 75,
ProcessWin32kSyscallFilterInformation = 79,
ProcessEnergyTrackingState = 82,
MaxProcessInfoClass // MaxProcessInfoClass should always be the last enum
} PROCESSINFOCLASS;
//句柄相关信息获取
typedef struct _SYSTEM_HANDLE_TABLE_ENTRY_INFO
{
USHORT UniqueProcessId;
USHORT CreatorBackTraceIndex;
UCHAR ObjectTypeIndex;
UCHAR HandleAttributes;
USHORT HandleValue;
PVOID Object;
ULONG GrantedAccess;
} SYSTEM_HANDLE_TABLE_ENTRY_INFO, *PSYSTEM_HANDLE_TABLE_ENTRY_INFO;
typedef struct _SYSTEM_HANDLE_INFORMATION
{
ULONG NumberOfHandles;
SYSTEM_HANDLE_TABLE_ENTRY_INFO Handles[1];
} SYSTEM_HANDLE_INFORMATION, *PSYSTEM_HANDLE_INFORMATION;
//ZwQueryinfromation信息
typedef enum _RFILE_INFORMATION_CLASS {
FileDirectoryInformation1 = 1,
FileFullDirectoryInformation,
FileBothDirectoryInformation,
FileBasicInformation,
FileStandardInformation,
FileInternalInformation,
FileEaInformation,
FileAccessInformation,
FileNameInformation,
FileRenameInformation,
FileLinkInformation,
FileNamesInformation,
FileDispositionInformation,
FilePositionInformation,
FileFullEaInformation,
FileModeInformation,
FileAlignmentInformation,
FileAllInformation,
FileAllocationInformation,
FileEndOfFileInformation,
FileAlternateNameInformation,
FileStreamInformation,
FilePipeInformation,
FilePipeLocalInformation,
FilePipeRemoteInformation,
FileMailslotQueryInformation,
FileMailslotSetInformation,
FileCompressionInformation,
FileObjectIdInformation,
FileCompletionInformation,
FileMoveClusterInformation,
FileQuotaInformation,
FileReparsePointInformation,
FileNetworkOpenInformation,
FileAttributeTagInformation,
FileTrackingInformation,
FileIdBothDirectoryInformation,
FileIdFullDirectoryInformation,
FileValidDataLengthInformation,
FileShortNameInformation,
FileIoCompletionNotificationInformation,
FileIoStatusBlockRangeInformation,
FileIoPriorityHintInformation,
FileSfioReserveInformation,
FileSfioVolumeInformation,
FileHardLinkInformation,
FileProcessIdsUsingFileInformation,
FileNormalizedNameInformation,
FileNetworkPhysicalNameInformation,
FileIdGlobalTxDirectoryInformation,
FileIsRemoteDeviceInformation,
FileUnusedInformation,
FileNumaNodeInformation,
FileStandardLinkInformation,
FileRemoteProtocolInformation,
FileRenameInformationBypassAccessCheck,
FileLinkInformationBypassAccessCheck,
FileVolumeNameInformation,
FileIdInformation,
FileIdExtdDirectoryInformation,
FileReplaceCompletionInformation,
FileHardLinkFullIdInformation,
FileIdExtdBothDirectoryInformation,
FileMaximumInformation
} RFILE_INFORMATION_CLASS, *PRFILE_INFORMATION_CLASS;
typedef _Enum_is_bitflag_ enum _POOL_TYPE {
NonPagedPool,
NonPagedPoolExecute = NonPagedPool,
PagedPool,
NonPagedPoolMustSucceed = NonPagedPool + 2,
DontUseThisType,
NonPagedPoolCacheAligned = NonPagedPool + 4,
PagedPoolCacheAligned,
NonPagedPoolCacheAlignedMustS = NonPagedPool + 6,
MaxPoolType,
//
// Define base types for NonPaged (versus Paged) pool, for use in cracking
// the underlying pool type.
//
NonPagedPoolBase = 0,
NonPagedPoolBaseMustSucceed = NonPagedPoolBase + 2,
NonPagedPoolBaseCacheAligned = NonPagedPoolBase + 4,
NonPagedPoolBaseCacheAlignedMustS = NonPagedPoolBase + 6,
//
// Note these per session types are carefully chosen so that the appropriate
// masking still applies as well as MaxPoolType above.
//
NonPagedPoolSession = 32,
PagedPoolSession = NonPagedPoolSession + 1,
NonPagedPoolMustSucceedSession = PagedPoolSession + 1,
DontUseThisTypeSession = NonPagedPoolMustSucceedSession + 1,
NonPagedPoolCacheAlignedSession = DontUseThisTypeSession + 1,
PagedPoolCacheAlignedSession = NonPagedPoolCacheAlignedSession + 1,
NonPagedPoolCacheAlignedMustSSession = PagedPoolCacheAlignedSession + 1,
NonPagedPoolNx = 512,
NonPagedPoolNxCacheAligned = NonPagedPoolNx + 4,
NonPagedPoolSessionNx = NonPagedPoolNx + 32,
} _Enum_is_bitflag_ POOL_TYPE;
typedef struct _PUBLIC_OBJECT_TYPE_INFORMATION {
UNICODE_STRING TypeName;
ULONG TotalNumberOfHandles;
ULONG TotalNumberOfObjects;
WCHAR Unused1[8];
ULONG HighWaterNumberOfHandles;
ULONG HighWaterNumberOfObjects;
WCHAR Unused2[8];
ACCESS_MASK InvalidAttributes;
GENERIC_MAPPING GenericMapping;
ACCESS_MASK ValidAttributes;
BOOLEAN SecurityRequired;
BOOLEAN MaintainHandleCount;
USHORT MaintainTypeList;
POOL_TYPE PoolType;
ULONG DefaultPagedPoolCharge;
ULONG DefaultNonPagedPoolCharge;
BYTE Unknown2[16];
} PUBLIC_OBJECT_TYPE_INFORMATION, *PPUBLIC_OBJECT_TYPE_INFORMATION;
//遍历系统信息
typedef NTSTATUS(WINAPI * PfnZwQuerySystemInformation)(
IN ULONG SysInfoClass,
IN OUT PVOID SystemInfroMation,
IN ULONG SystemInforMationLength,
OUT PULONG RetLen);
typedef enum _OBJECT_INFORMATION_CLASS {
ObjectBasicInformation = 0, //如果为1表示获取名字信息
ObjectTypeInformation = 2 //表示获取类型信息
} OBJECT_INFORMATION_CLASS;
//单独对象获取打开句柄的信息
typedef NTSTATUS(WINAPI * PfnZwQueryObject)(
_In_opt_ HANDLE Handle, //句柄
_In_ OBJECT_INFORMATION_CLASS ObjectInformationClass, //要获取的类型信息
PVOID ObjectInformation, //缓冲区 用户模式下使用 NtQueryObject
_In_ ULONG ObjectInformationLength, _Out_opt_ //缓冲区大小
PULONG ReturnLength); //返回长度
// NtQueryObject类型为0的信息结构体
typedef struct _PUBLIC_OBJECT_BASIC_INFORMATION {
ULONG Attributes;
ACCESS_MASK GrantedAccess;
ULONG HandleCount;
ULONG PointerCount;
ULONG Reserved[10];
} PUBLIC_OBJECT_BASIC_INFORMATION, *PPUBLIC_OBJECT_BASIC_INFORMATION;
//遍历文件需要的信息
typedef struct _IO_STATUS_BLOCK {
#pragma warning(push)
#pragma warning(disable: 4201) // we'll always use the Microsoft compiler
union {
NTSTATUS Status;
PVOID Pointer;
} DUMMYUNIONNAME;
#pragma warning(pop)
ULONG_PTR Information;
} IO_STATUS_BLOCK, *PIO_STATUS_BLOCK;
typedef struct _FILE_NAME_INFORMATION {
ULONG FileNameLength;
WCHAR FileName[1];
} FILE_NAME_INFORMATION, *PFILE_NAME_INFORMATION;
typedef NTSTATUS(WINAPI * PfnNtQueryInformationFile)(
HANDLE FileHandle,
PIO_STATUS_BLOCK IoStatusBlock,
PVOID FileInformation,
ULONG Length,
RFILE_INFORMATION_CLASS FileInformationClass
);
//NtQueryObject类型为1的信息结构体.
//typedef struct __PUBLIC_OBJECT_TYPE_INFORMATION {
// UNICODE_STRING TypeName;
// ULONG Reserved[22];
//} PUBLIC_OBJECT_TYPE_INFORMATION, *PPUBLIC_OBJECT_TYPE_INFORMATION;
//函数指针赋值.
//遍历某个进程的句柄信息
typedef NTSTATUS(WINAPI* PfnZwQueryInformationProcess)(
_In_ HANDLE ProcessHandle,
_In_ PROCESSINFOCLASS ProcessInformationClass, //根据类型信息获取不同的信息
_Out_ PVOID ProcessInformation,
_In_ ULONG ProcessInformationLength,
_Out_opt_ PULONG ReturnLength
);
坚持两字,简单,轻便,但是真正的执行起来确实需要很长很长时间.当你把坚持两字当做你要走的路,那么你总会成功. 想学习,有问题请加群.群号:725864912(收费)群名称: 逆向学习小分队 群里有大量学习资源. 以及定期直播答疑.有一个良好的学习氛围. 涉及到外挂反外挂病毒 司法取证加解密 驱动过保护 VT 等技术,期待你的进入。
详情请点击链接查看置顶博客 https://www.cnblogs.com/iBinary/p/7572603.html
本文来自博客园,作者:iBinary,未经允许禁止转载 转载前可联系本人.对于爬虫人员来说如果发现保留起诉权力.https://www.cnblogs.com/iBinary/p/11344237.html
欢迎大家关注我的微信公众号.不定期的更新文章.更新技术. 关注公众号后请大家养成 不白嫖的习惯.欢迎大家赞赏. 也希望在看完公众号文章之后 不忘 点击 收藏 转发 以及点击在看功能. QQ群:
QQ群:




 浙公网安备 33010602011771号
浙公网安备 33010602011771号