DMVPN的实验模拟与分析
此篇博客正在介绍的是下图中的DMVPN:
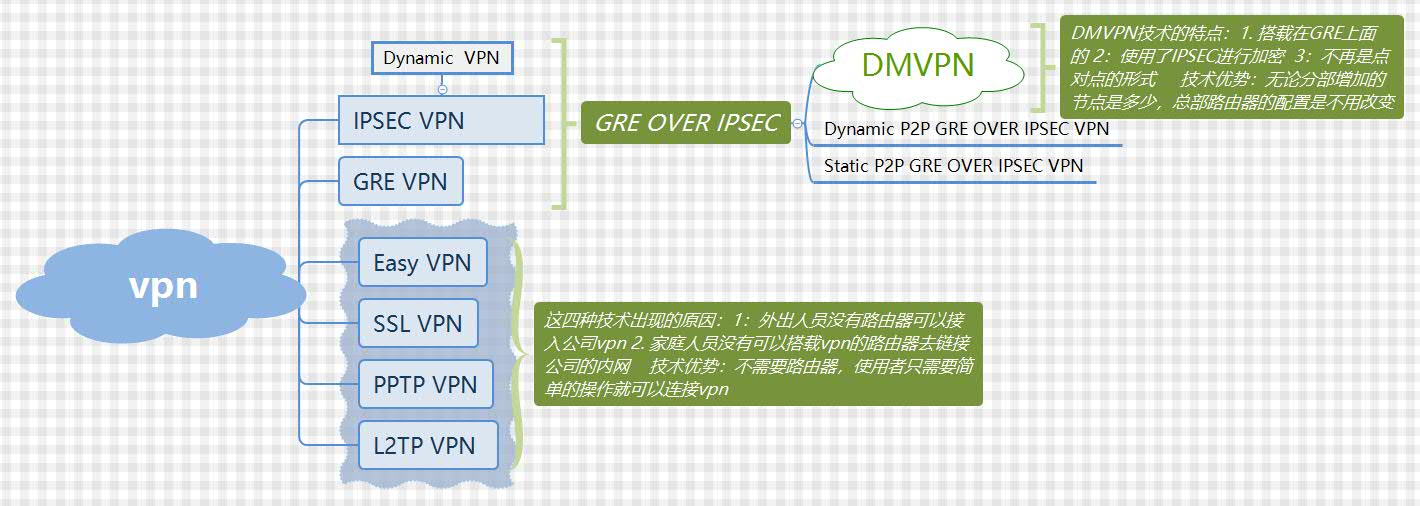
为什么会出现DMVPN这个技术呢?
在这篇博客中https://www.cnblogs.com/huwentao/p/9355240.html介绍过Dynamic P2P GRE OVER VPN的技术,DMVPN的出现就是为了解决Dynamic P2P GRE OVER VPN技术的缺陷的。对于一个公司而言,总部的VPN路由器是相当重要的,因此一旦总部的路由器配置完成之后,无论公司是如何发展的,我们都要尽量的避免总部路由器的变更,但是Dynamic P2P GRE OVER VPN技术却有以下缺陷,如下图中的配置,在我们设置隧道目的地址的时候,需要在分部路由器上面设置一个环回接口,这也就代表着当分部路由器增加一台,我们就要再设置一个GRE tunnel去匹配。因此DMVPN出现了。接下来看一下DMVPN是怎么配置的吧。

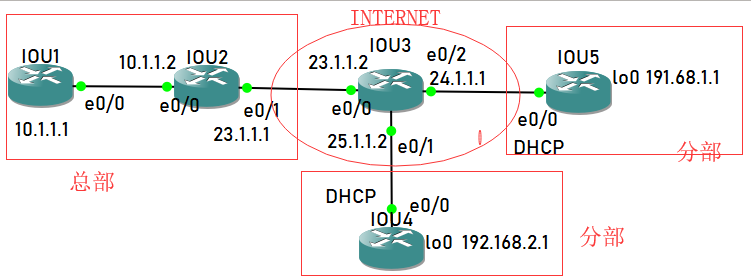
拓扑结构图如下:
拓扑图描述:用IOU3模拟公网INTERNET,并且作为一台DHCP服务器给IOU5和IOU4分配动态的地址,现在要实现的是通过DMVPN技术实现总部和分部的路由交换和互通。总部的路由器一般被成为hub端,分部的被称为spoke端。
步骤一:基础网络配置:
IOU1的配置:
IOU1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. IOU1(config-if)#ip add 10.1.1.1 255.255.255.0 配置地址 IOU1(config-if)#no shutdown IOU1(config)#ip route 0.0.0.0 0.0.0.0 10.1.1.2 设置默认路由指向10.1.1.2接口
IOU2的配置:
IOU2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. IOU2(config)#inter e0/0 IOU2(config-if)#ip add 10.1.1.2 255.255.255.0 IOU2(config-if)#no shutdown IOU2(config-if)#inter e0/1 IOU2(config-if)#ip add 23.1.1.1 255.255.255.0 IOU2(config-if)#no shutdown IOU2(config)#ip route 0.0.0.0 0.0.0.0 23.1.1.2
IOU3的配置:
IOU3#configure terminal Enter configuration commands, one per line. End with CNTL/Z. IOU3(config)#inter e0/1 IOU3(config-if)#ip add 25.1.1.2 255.255.255.0 IOU3(config-if)#no shutdown IOU3(config-if)#inter e0/2 IOU3(config-if)#ip add 24.1.1.1 255.255.255.0 IOU3(config-if)#no shutdown IOU3(config-if)#inter e0/0 IOU3(config-if)#ip add 23.1.1.2 255.255.255.0 IOU3(config-if)#no shutdown IOU3(config-if)#exit IOU3(config)#ip dhcp pool 24DHCP 设置动态的地址池,名字为24DHCP IOU3(dhcp-config)#network 24.1.1.0 255.255.255.0 地址池的地址范围 IOU3(dhcp-config)#default-router 24.1.1.1 设置分发地址的默认网关地址 IOU3(dhcp-config)#exit IOU3(config)#ip dhcp pool 25DHCP IOU3(dhcp-config)#network 25.1.1.0 255.255.255.0 IOU3(dhcp-config)#default-router 25.1.1.2 IOU3(dhcp-config)#exit IOU3(config)#ip dhcp excluded-address 24.1.1.1 除去默认网关的地址,其余地址可以分配 IOU3(config)#ip dhcp excluded-address 25.1.1.2
IOU4的配置:
IOU4#configure terminal Enter configuration commands, one per line. End with CNTL/Z. IOU4(config-if)#ip address dhcp 设置接口地址通过dhcp服务器获取 IOU4(config-if)#no shutdown IOU4(config-if)# *Jul 24 00:55:56.952: %DHCP-6-ADDRESS_ASSIGN: Interface Ethernet0/0 assigned DHCP address 25.1.1.3, mask 255.255.255.0, hostname IOU4 IOU4(config-if)#inte lo0 IOU4(config-if)#ip add 192.168.2.1 255.255.255.0 IOU4(config-if)#no shutdown
IOU5的配置:
IOU5#configure terminal Enter configuration commands, one per line. End with CNTL/Z. IOU5(config-if)#inter e0/0 IOU5(config-if)#ip address dhcp IOU5(config-if)#no shutdown *Jul 24 00:58:56.869: %DHCP-6-ADDRESS_ASSIGN: Interface Ethernet0/0 assigned DHCP address 24.1.1.3, mask 255.255.255.0, hostname IOU5 IOU5(config-if)#inter lo0 IOU5(config-if)#ip add 192.168.1.1 255.255.255.0 IOU5(config-if)#no shutdown IOU5(config-if)#exit
测试网络:
IOU2 ping 24.1.1.3 和 ping 25.1.1.3 是可以ping通的,但是ping 192.168.1.1 和ping 192.168.2.1 是不通的

1 IOU2#ping 24.1.1.3 2 Type escape sequence to abort. 3 Sending 5, 100-byte ICMP Echos to 24.1.1.3, timeout is 2 seconds: 4 !!!!! 5 Success rate is 100 percent (5/5), round-trip min/avg/max = 4/6/8 ms 6 IOU2#ping 25.1.1.3 7 Type escape sequence to abort. 8 Sending 5, 100-byte ICMP Echos to 25.1.1.3, timeout is 2 seconds: 9 !!!!! 10 Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/6 ms 11 IOU2#ping 192.168.1.1 12 Type escape sequence to abort. 13 Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: 14 UUUUU 15 Success rate is 0 percent (0/5) 16 IOU2#ping 192.168.2.1 17 Type escape sequence to abort. 18 Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds: 19 UUUUU 20 Success rate is 0 percent (0/5) 21 IOU2#
步骤二:IPSEC配置
对于IOU2, IOU4, IOU5而言,它的IIPSEC的配置都是一样的。
IOU2的配置:
IOU2#configure terminal Enter configuration commands, one per line. End with CNTL/Z. IOU2(config)#crypto isakmp policy 10 配置ike策略 IOU2(config-isakmp)#encryption 3des 加密算法 IOU2(config-isakmp)#group 1 密钥交换算法 IOU2(config-isakmp)#hAsh md5 hash算法 IOU2(config-isakmp)#authentication pre-share 设置认证方法为预共享密钥 IOU2(config-isakmp)#exit IOU2(config)#crypto isakmp key 0 huwentao address 0.0.0.0 设置密钥,因为是动态的,所以address地址为 0.0.0.0 IOU2(config)#crypto ipsec transform-set IPSEC esp-3des esp-md5-hmac IOU2(cfg-crypto-trans)#exit IOU2(config)#crypto ipsec profile IPSEC_PROFILE 设置ipsec profile对隧道进行加密 IOU2(ipsec-profile)#set transform-set IPSEC IOU2(ipsec-profile)#EXIT
IOU4的配置(和IOU2配置是一样的):
IOU2(config)#crypto isakmp policy 10 IOU2(config-isakmp)#encryption 3des IOU2(config-isakmp)#group 1 IOU2(config-isakmp)#hAsh md5 IOU2(config-isakmp)#authentication pre-share IOU2(config-isakmp)#exit IOU2(config)#crypto isakmp key 0 huwentao address 0.0.0.0 IOU2(config)#crypto ipsec transform-set IPSEC esp-3des esp-md5-hmac IOU2(cfg-crypto-trans)#exit IOU2(config)#crypto ipsec profile IPSEC_PROFILE IOU2(ipsec-profile)#set transform-set IPSEC IOU2(ipsec-profile)#EXIT
IOU5的配置(和IOU2的配置是一样的):
IOU2(config)#crypto isakmp policy 10 IOU2(config-isakmp)#encryption 3des IOU2(config-isakmp)#group 1 IOU2(config-isakmp)#hAsh md5 IOU2(config-isakmp)#authentication pre-share IOU2(config-isakmp)#exit IOU2(config)#crypto isakmp key 0 huwentao address 0.0.0.0 IOU2(config)#crypto ipsec transform-set IPSEC esp-3des esp-md5-hmac IOU2(cfg-crypto-trans)#exit IOU2(config)#crypto ipsec profile IPSEC_PROFILE IOU2(ipsec-profile)#set transform-set IPSEC IOU2(ipsec-profile)#EXIT
步骤三:GRE隧道配置
隧道的设置一定要注意的是几个地址的配置
IOU2的配置(隧道地址为1.1.1.1):
IOU2(config)#inter tunnel 1 *Jul 24 02:08:30.478: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel1, changed IOU2(config-if)#ip address 1.1.1.1 255.255.255.0 设置隧道地址为1.1.1.1 IOU2(config-if)#tunnel source e0/1 设置隧道源地址为它的出接口e0/1,因为是MGRE,所以是不用设置隧道的目的地址的 IOU2(config-if)#tunnel mode gre multipoint 设置隧道的模式为MGRE IOU2(config-if)#tunnel protection ipsec profile IPSEC_PROFILE 在隧道上应用IPSEC profile对隧道进行加密 IOU2(config-if)# *Jul 24 02:10:39.273: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON IOU2(config-if)#bandwidth 1000 设置接口的带宽,从而影响路由协议的距离的计算(不更改其实也是可以的),所有节点都要一致 IOU2(config-if)#ip mtu 1400 更改mtu的值为1400,如果不更改,下一跳路由器会对数据包进行分片和重新封装,所有节点都要一致 IOU2(config-if)#ip nhrp authentication huwentao 设置nhrp的认证密码,所有节点的密码都要一致 IOU2(config-if)#ip nhrp network-id 1 设置nhrp的网络id,相当于启用了nhrp,所有节点要一致 IOU2(config-if)#ip nhrp map multicast dynamic 自动的将spoke的地址值加入到hub中 IOU2(config-if)#no ip split-horizon eigrp 1 关掉水平分割,使得两个分部的路由可以交换
IOU4的配置:
IOU4(config)#inter tunnel 1 IOU4(config-if)#ip ad *Jul 24 02:28:25.190: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel1, changed state to down IOU4(config-if)#ip add 1.1.1.4 255.255.255.0 IOU4(config-if)#tunnel source e0/0 IOU4(config-if)#tunnel mode gre multipoint IOU4(config-if)#tunnel protection ipsec profile IPSEC_PROFILE IOU4(config-if)#no ip split-horizon eigrp 1 IOU4(config-if)#bandwidth 1000 IOU4(config-if)#ip mtu 1400 IOU4(config-if)#ip nhrp authentication huwentao IOU4(config-if)#ip nhrp map 1.1.1.1 23.1.1.1 设置hub端的隧道地址和源地址的映射,1.1.1.1是IOU2的隧道地址,23.1.1.1为IOU2的出接口的地址 IOU4(config-if)#ip nhrp map multicast 23.1.1.1 开启组播功能,以及动态路由协议的功能,hub端的地址为23.1.1.1 IOU4(config-if)#ip nhrp network-id 1
IOU4(config-if)#ip nhrp nhs 1.1.1.1 这个地址一定注意,是hub端的隧道地址,也就是IOU2的隧道地址(我在这个地方掉进过一次,排查了好长时间才发现原来是这个地方配置错了)
IOU5的配置(和IOU4的配置是一样的,只是隧道的地址改一下就可以了):
IOU4(config)#inter tunnel 1 IOU4(config-if)#ip ad *Jul 24 02:28:25.190: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel1, changed state to down IOU4(config-if)#ip add 1.1.1.5 255.255.255.0 配置隧道的地址 IOU4(config-if)#tunnel source e0/0 IOU4(config-if)#tunnel mode gre multipoint IOU4(config-if)#tunnel protection ipsec profile IPSEC_PROFILE IOU4(config-if)#no ip split-horizon eigrp 1 IOU4(config-if)#bandwidth 1000 IOU4(config-if)#ip mtu 1400 IOU4(config-if)#ip nhrp authentication huwentao IOU4(config-if)#ip nhrp map 1.1.1.1 23.1.1.1 IOU4(config-if)#ip nhrp map multicast 23.1.1.1 IOU4(config-if)#ip nhrp network-id 1
IOU4(config-if)#ip nhrp nhs 1.1.1.1
查看IOU2 ping 1.1.1.4 和ping 1.1.1.5都是可以ping通的,说明MGRE隧道已经建立成功:

1 IOU2#ping 1.1.1.4 2 Type escape sequence to abort. 3 Sending 5, 100-byte ICMP Echos to 1.1.1.4, timeout is 2 seconds: 4 !!!!! 5 Success rate is 100 percent (5/5), round-trip min/avg/max = 5/5/6 ms 6 IOU2#ping 1.1.1.5 7 Type escape sequence to abort. 8 Sending 5, 100-byte ICMP Echos to 1.1.1.5, timeout is 2 seconds: 9 !!!!! 10 Success rate is 100 percent (5/5), round-trip min/avg/max = 6/13/16 ms 11 IOU2#
查看IOU2 show ip nhrp发现有1.1.1.4和1.1.1.5对应的接口地址信息

1 IOU2#show ip nhrp 2 1.1.1.4/32 via 1.1.1.4 3 Tunnel1 created 00:06:01, expire 01:54:00 4 Type: dynamic, Flags: unique registered 5 NBMA address: 25.1.1.4 6 1.1.1.5/32 via 1.1.1.5 7 Tunnel1 created 00:05:54, expire 01:54:06 8 Type: dynamic, Flags: unique registered 9 NBMA address: 24.1.1.2
查看IOU2 show crypto isakmp peers 发现有两个对等体已经建立成功,已经sa也已经建立成功。

1 IOU2#show crypto isakmp peers 2 Peer: 24.1.1.2 Port: 500 Local: 23.1.1.1 3 Phase1 id: 24.1.1.2 4 Peer: 25.1.1.4 Port: 500 Local: 23.1.1.1 5 Phase1 id: 25.1.1.4 6 IOU2#show crypto isakmp sa 7 IPv4 Crypto ISAKMP SA 8 dst src state conn-id status 9 23.1.1.1 24.1.1.2 QM_IDLE 1006 ACTIVE 10 23.1.1.1 25.1.1.4 QM_IDLE 1005 ACTIVE 11 12 IPv6 Crypto ISAKMP SA 13 14 IOU2#
查看IOU2 show crypto ipsec sa 发现有两个sa分别是和IOU4和IOU5建立的。

1 IOU2#SHOW crypto ipsec sa 2 3 interface: Tunnel1 4 Crypto map tag: Tunnel1-head-0, local addr 23.1.1.1 5 6 protected vrf: (none) 7 local ident (addr/mask/prot/port): (23.1.1.1/255.255.255.255/47/0) 8 remote ident (addr/mask/prot/port): (24.1.1.2/255.255.255.255/47/0) 代表的是和24.1.1.2建立了ipsec sa用来加密数据。 9 current_peer 24.1.1.2 port 500 10 PERMIT, flags={origin_is_acl,} 11 #pkts encaps: 8, #pkts encrypt: 8, #pkts digest: 8 12 #pkts decaps: 8, #pkts decrypt: 8, #pkts verify: 8 13 #pkts compressed: 0, #pkts decompressed: 0 14 #pkts not compressed: 0, #pkts compr. failed: 0 15 #pkts not decompressed: 0, #pkts decompress failed: 0 16 #send errors 0, #recv errors 0 17 18 local crypto endpt.: 23.1.1.1, remote crypto endpt.: 24.1.1.2 19 plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb (none) 20 current outbound spi: 0xFC42BCA6(4232232102) 21 PFS (Y/N): N, DH group: none 22 23 inbound esp sas: 24 spi: 0x55EA3DDB(1441414619) 25 transform: esp-3des esp-md5-hmac , 26 in use settings ={Tunnel, } 27 conn id: 15, flow_id: SW:15, sibling_flags 80000040, crypto map: Tunnel1-head-0 28 sa timing: remaining key lifetime (k/sec): (4284915/2516) 29 IV size: 8 bytes 30 replay detection support: Y 31 Status: ACTIVE(ACTIVE) 32 33 inbound ah sas: 34 35 inbound pcp sas: 36 37 outbound esp sas: 38 spi: 0xFC42BCA6(4232232102) 39 transform: esp-3des esp-md5-hmac , 定义的ipsec的交换集 40 in use settings ={Tunnel, } 定义的ipsec的加密模式 41 conn id: 16, flow_id: SW:16, sibling_flags 80000040, crypto map: Tunnel1-head-0 42 sa timing: remaining key lifetime (k/sec): (4284915/2516) 43 IV size: 8 bytes 44 replay detection support: Y 45 Status: ACTIVE(ACTIVE) 46 47 outbound ah sas: 48 49 outbound pcp sas: 50 51 protected vrf: (none) 52 local ident (addr/mask/prot/port): (23.1.1.1/255.255.255.255/47/0) 53 remote ident (addr/mask/prot/port): (25.1.1.4/255.255.255.255/47/0)代表的是和25.1.1.4建立的ipsec sa,用来加密数据的额 54 current_peer 25.1.1.4 port 500 55 PERMIT, flags={origin_is_acl,} 56 #pkts encaps: 8, #pkts encrypt: 8, #pkts digest: 8 57 #pkts decaps: 8, #pkts decrypt: 8, #pkts verify: 8 58 #pkts compressed: 0, #pkts decompressed: 0 59 #pkts not compressed: 0, #pkts compr. failed: 0 60 #pkts not decompressed: 0, #pkts decompress failed: 0 61 #send errors 0, #recv errors 0 62 63 local crypto endpt.: 23.1.1.1, remote crypto endpt.: 25.1.1.4 64 plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb (none) 65 current outbound spi: 0x3D0D283B(1024272443) 66 PFS (Y/N): N, DH group: none 67 68 inbound esp sas: 69 spi: 0xAFF87D4(184518612) 70 transform: esp-3des esp-md5-hmac , 定义的ipsec交换集 71 in use settings ={Tunnel, } 72 conn id: 13, flow_id: SW:13, sibling_flags 80000040, crypto map: Tunnel1-head-0 73 sa timing: remaining key lifetime (k/sec): (4265113/2510) 74 IV size: 8 bytes 75 replay detection support: Y 76 Status: ACTIVE(ACTIVE) 77 78 inbound ah sas: 79 80 inbound pcp sas: 81 82 outbound esp sas: 83 spi: 0x3D0D283B(1024272443) 84 transform: esp-3des esp-md5-hmac , 85 in use settings ={Tunnel, } 86 conn id: 14, flow_id: SW:14, sibling_flags 80000040, crypto map: Tunnel1-head-0 87 sa timing: remaining key lifetime (k/sec): (4265113/2510) 88 IV size: 8 bytes 89 replay detection support: Y 90 Status: ACTIVE(ACTIVE) 91 92 outbound ah sas: 93 94 outbound pcp sas:
步骤四:路由交换配置
IOU2的配置:
IOU2(config)#router eigrp 1 IOU2(config-router)#no au IOU2(config-router)#no auto-summary IOU2(config-router)#networ IOU2(config-router)#network 1.1.1.1 255.255.255.0 IOU2(config-router)#network IOU2(config-router)#network 10.1.1.0 255.255.255.0 IOU2(config-router)#exit
IOU4的配置:
IOU4(config)#router eigrp 1 IOU4(config-router)#no auto-summary IOU4(config-router)#network 1.1.1.0 255.255.255.0 *Jul 24 13:40:34.320: %DUAL-5-NBRCHANGE: EIGRP-IPv4 1: Neighbor 1.1.1.1 (Tunnel1) is up: new adjacency IOU4(config-router)#network 192.168.2.0 255.255.255.0 IOU4(config-router)#exit
IOU5的配置:
IOU5(config)#router eigrp 1 IOU5(config-router)#no auto-summary IOU5(config-router)#network 1.1.1.0 255.255.255.0 *Jul 24 13:41:26.047: %DUAL-5-NBRCHANGE: EIGRP-IPv4 1: Neighbor 1.1.1.1 (Tunnel1) is up: new adjacency IOU5(config-router)#network 192.168.1.0 255.255.255.0 IOU5(config-router)#
查看IOU2的eigrp邻居信息和路由表,发现已经能够学习到路由了:

1 IOU2#show ip eigrp neighbors 2 EIGRP-IPv4 Neighbors for AS(1) 3 H Address Interface Hold Uptime SRTT RTO Q Seq 4 (sec) (ms) Cnt Num 5 1 1.1.1.5 Tu1 13 00:02:19 10 132 0 4 6 0 1.1.1.4 Tu1 13 00:03:10 1 132 0 5 7 IOU2#show ip ro 8 IOU2#show ip route 9 Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP 10 D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area 11 N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 12 E1 - OSPF external type 1, E2 - OSPF external type 2 13 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 14 ia - IS-IS inter area, * - candidate default, U - per-user static route 15 o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP 16 a - application route 17 + - replicated route, % - next hop override 18 19 Gateway of last resort is 23.1.1.2 to network 0.0.0.0 20 21 S* 0.0.0.0/0 [1/0] via 23.1.1.2 22 1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks 23 C 1.1.1.0/24 is directly connected, Tunnel1 24 L 1.1.1.1/32 is directly connected, Tunnel1 25 10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks 26 C 10.1.1.0/24 is directly connected, Ethernet0/0 27 L 10.1.1.2/32 is directly connected, Ethernet0/0 28 23.0.0.0/8 is variably subnetted, 2 subnets, 2 masks 29 C 23.1.1.0/24 is directly connected, Ethernet0/1 30 L 23.1.1.1/32 is directly connected, Ethernet0/1 31 192.168.1.0/32 is subnetted, 1 subnets 32 D 192.168.1.1 [90/3968000] via 1.1.1.5, 00:02:30, Tunnel1 33 192.168.2.0/32 is subnetted, 1 subnets 34 D 192.168.2.1 [90/3968000] via 1.1.1.4, 00:03:24, Tunnel1 35 IOU2#
但是对于IOU4和IOU5只和IOU2建立邻居,因为IOU4和IOU5之间是没有模拟隧道的,所以建立不了eigrp邻居

1 IOU4#show ip eigrp neighbors 2 EIGRP-IPv4 Neighbors for AS(1) 3 H Address Interface Hold Uptime SRTT RTO Q Seq 4 (sec) (ms) Cnt Num 5 0 1.1.1.1 Tu1 12 00:05:58 13 138 0 6 6 IOU4# 7 IOU5#show ip eigrp neighbors 8 EIGRP-IPv4 Neighbors for AS(1) 9 H Address Interface Hold Uptime SRTT RTO Q Seq 10 (sec) (ms) Cnt Num 11 0 1.1.1.1 Tu1 14 00:05:32 17 138 0 6
由于我们关闭了EIGRP的水平分割,因此IOU4和IOU5都有对方的路由:

1 IOU5#show ip route 2 Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP 3 D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area 4 N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 5 E1 - OSPF external type 1, E2 - OSPF external type 2 6 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 7 ia - IS-IS inter area, * - candidate default, U - per-user static route 8 o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP 9 a - application route 10 + - replicated route, % - next hop override 11 12 Gateway of last resort is 24.1.1.1 to network 0.0.0.0 13 14 S* 0.0.0.0/0 [254/0] via 24.1.1.1 15 1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks 16 C 1.1.1.0/24 is directly connected, Tunnel1 17 L 1.1.1.5/32 is directly connected, Tunnel1 18 10.0.0.0/24 is subnetted, 1 subnets 19 D 10.1.1.0 [90/3865600] via 1.1.1.1, 00:05:39, Tunnel1 20 24.0.0.0/8 is variably subnetted, 2 subnets, 2 masks 21 C 24.1.1.0/24 is directly connected, Ethernet0/0 22 L 24.1.1.2/32 is directly connected, Ethernet0/0 23 192.168.1.0/32 is subnetted, 1 subnets 24 C 192.168.1.1 is directly connected, Loopback0 25 192.168.2.0/32 is subnetted, 1 subnets 26 D 192.168.2.1 [90/5248000] via 1.1.1.1, 00:05:39, Tunnel1 27 IOU5# 28 29 30 31 32 IOU4#show ip eigrp neighbors 33 EIGRP-IPv4 Neighbors for AS(1) 34 H Address Interface Hold Uptime SRTT RTO Q Seq 35 (sec) (ms) Cnt Num 36 0 1.1.1.1 Tu1 12 00:05:58 13 138 0 6 37 IOU4#show ip rout 38 Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP 39 D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area 40 N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 41 E1 - OSPF external type 1, E2 - OSPF external type 2 42 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 43 ia - IS-IS inter area, * - candidate default, U - per-user static route 44 o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP 45 a - application route 46 + - replicated route, % - next hop override 47 48 Gateway of last resort is 25.1.1.2 to network 0.0.0.0 49 50 S* 0.0.0.0/0 [254/0] via 25.1.1.2 51 1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks 52 C 1.1.1.0/24 is directly connected, Tunnel1 53 L 1.1.1.4/32 is directly connected, Tunnel1 54 10.0.0.0/24 is subnetted, 1 subnets 55 D 10.1.1.0 [90/3865600] via 1.1.1.1, 00:10:02, Tunnel1 56 25.0.0.0/8 is variably subnetted, 2 subnets, 2 masks 57 C 25.1.1.0/24 is directly connected, Ethernet0/0 58 L 25.1.1.4/32 is directly connected, Ethernet0/0 59 192.168.1.0/32 is subnetted, 1 subnets 60 D 192.168.1.1 [90/5248000] via 1.1.1.1, 00:08:54, Tunnel1 61 192.168.2.0/32 is subnetted, 1 subnets 62 C 192.168.2.1 is directly connected, Loopback0 63 IOU4#
测试结果:
IOU2去ping IOU4和IOU5,可以ping 通,中间的被隧道所隐藏:
IOU2#traceroute 192.168.1.1 Type escape sequence to abort. Tracing the route to 192.168.1.1 VRF info: (vrf in name/id, vrf out name/id) 1 1.1.1.5 5 msec 5 msec 5 msec IOU2#traceroute 192.168.2.1 Type escape sequence to abort. Tracing the route to 192.168.2.1 VRF info: (vrf in name/id, vrf out name/id) 1 1.1.1.4 5 msec 5 msec 5 msec IOU2#
IOU4去ping IOU2和IOU5:
IOU4#traceroute 10.1.1.1 Type escape sequence to abort. Tracing the route to 10.1.1.1 VRF info: (vrf in name/id, vrf out name/id) 1 1.1.1.1 6 msec 5 msec 2 msec 2 10.1.1.1 5 msec 6 msec 5 msec IOU4#traceroute 192.168.1.1 Type escape sequence to abort. Tracing the route to 192.168.1.1 VRF info: (vrf in name/id, vrf out name/id) 1 1.1.1.1 5 msec 6 msec 4 msec 2 1.1.1.1 4 msec 5 msec 5 msec 3 1.1.1.5 5 msec 5 msec 7 msec IOU4#
为了不让IOU2进行中转,因此在IOU2上面配置:
IOU2(config)#interface tunnel 1 IOU2(config-if)#no ip next-hop-self eigrp 1 IOU2(config-if)#
重新ping 192.168.1.1就会发现,不在向IOU2进行询问,直接从1.1.1.5发出去了:
Type escape sequence to abort. Tracing the route to 192.168.1.1 VRF info: (vrf in name/id, vrf out name/id) 1 1.1.1.5 4 msec 4 msec 5 msec IOU4#
小小技巧:
配置没有问题,但是就是没有办法ping通的时候:从hub端开始,依次在internet tunnel 【number】下shutdown之后,再重新no shutdown一下
例如此配置:
操作一:shutdown

1 先shutdownIOU2 2 IOU2#configure terminal 3 Enter configuration commands, one per line. End with CNTL/Z. 4 IOU2(config)#inter 5 IOU2(config)#interface tu 6 IOU2(config)#interface tunnel 1 7 IOU2(config-if)#shutdown 8 9 10 然后shutdown IOU4和IOU5 11 IOU4(config)#interface tunnel 1 12 IOU4(config-if)#shutdown 13 14 IOU5(config)#interface tunnel 1 15 IOU5(config-if)#shutdown
操作二:no shutdown

1 先no shutdownIOU2 2 IOU2#configure terminal 3 Enter configuration commands, one per line. End with CNTL/Z. 4 IOU2(config)#inter 5 IOU2(config)#interface tu 6 IOU2(config)#interface tunnel 1 7 IOU2(config-if)#no shutdown 8 9 10 然后shutdown IOU4和IOU5 11 IOU4(config)#interface tunnel 1 12 IOU4(config-if)#no shutdown 13 14 IOU5(config)#interface tunnel 1 15 IOU5(config-if)#no shutdown



