TCP/IP
- telnet:检查端口是否打开。
- telnet的一个最大作用就是检查一个端口是否处于打开,使用的命令是 telnet[domainname or ip] [port],这条命令能告诉我们到远端 server 指定端口的网连接是否可达。
- netstat:用于显示各种网络相关信息。
- -a(all):显示所有选项,默认不显示LISTEN相关;
- -t (tcp)仅显示tcp相关选项;
- -u(udp)仅显示udp相关选项;
- -n 拒绝显示别名,能显示数字的全部转化成数字-仅列出有在 Listen (监听)的服务状态;
- -p显示建立相关链接的程序名;
- -r显示路由信息,路由表;
- -e 显示扩展信息,例如uid等;
- -s按各个协议进行统计;
- -c 每隔一个固定时间,执行该netstat命令
-
netstat -a :显示所有 netstat -at:显示与tcp协议相关的 netstat -au:udp相关 netstat -l:显示正在监听的 netstat -lt:显示正在监听的tcp协议相关的 netstat -lu:显示正在监听的udp协议相关的
- tcpdump:tcpdump 则是一个命令行的网络流量分析工具,功能非常强大,一般我们用来抓TCP的包。
- tcpdump -i any:监听任意网卡
-
# tcpdump -help tcpdump version 4.9.2 libpcap version 1.5.3 OpenSSL 1.0.2k-fips 26 Jan 2017 Usage: tcpdump [-aAbdDefhHIJKlLnNOpqStuUvxX#] [ -B size ] [ -c count ] [ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ] [ -i interface ] [ -j tstamptype ] [ -M secret ] [ --number ] [ -Q|-P in|out|inout ] [ -r file ] [ -s snaplen ] [ --time-stamp-precision precision ] [ --immediate-mode ] [ -T type ] [ --version ] [ -V file ] [ -w file ] [ -W filecount ] [ -y datalinktype ] [ -z postrotate-command ] [ -Z user ] [ expression ] - tcpdump -i any host ip
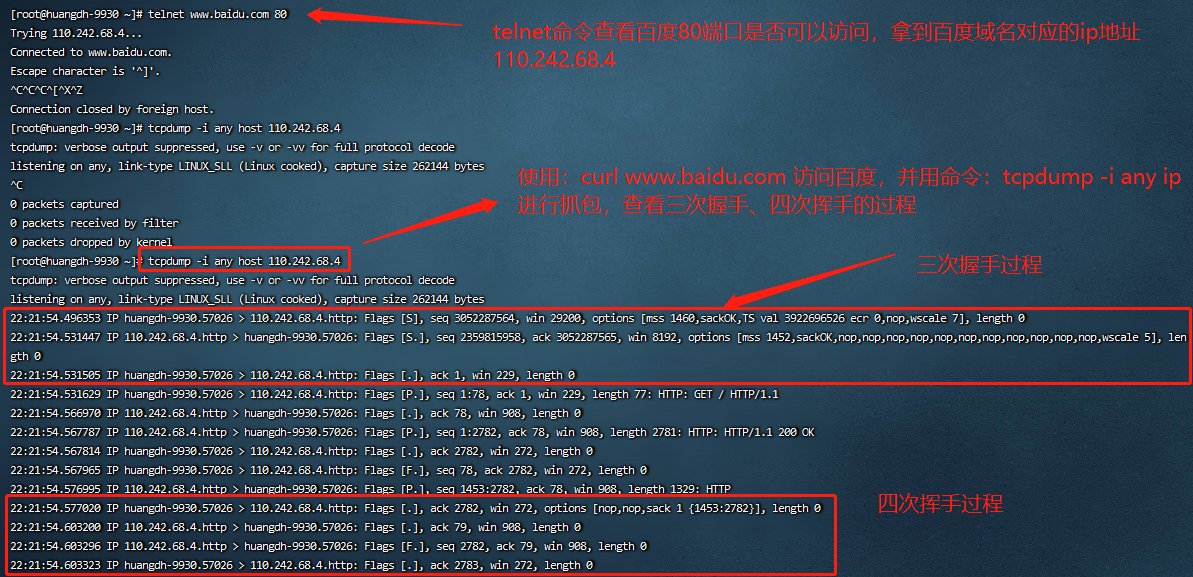
监听本地80端口:
[root@huangdh-9930 ~]# tcpdump -nn -i eth0 port 80
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
12:03:15.556864 IP 172.28.208.175.53044 > 100.100.30.25.80: Flags [P.], seq 2246809072:2246810914, ack 1100304209, win 1432, length 1842: HTTP
12:03:15.584514 IP 100.100.30.25.80 > 172.28.208.175.53044: Flags [.], ack 1842, win 2843, length 0
12:03:17.341897 IP 172.28.208.175.43738 > 110.242.68.4.80: Flags [S], seq 1119341673, win 29200, options [mss 1460,sackOK,TS val 4058379371 ecr 0,nop,wscale 7], length 0
12:03:17.377351 IP 110.242.68.4.80 > 172.28.208.175.43738: Flags [S.], seq 3935201237, ack 1119341674, win 8192, options [mss 1452,sackOK,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,nop,wscale 5], length 0
12:03:17.377389 IP 172.28.208.175.43738 > 110.242.68.4.80: Flags [.], ack 1, win 229, length 0
12:03:17.377520 IP 172.28.208.175.43738 > 110.242.68.4.80: Flags [P.], seq 1:78, ack 1, win 229, length 77: HTTP: GET / HTTP/1.1
12:03:17.413141 IP 110.242.68.4.80 > 172.28.208.175.43738: Flags [.], ack 78, win 908, length 0
12:03:17.414143 IP 110.242.68.4.80 > 172.28.208.175.43738: Flags [P.], seq 1:2782, ack 78, win 908, length 2781: HTTP: HTTP/1.1 200 OK
12:03:17.414158 IP 172.28.208.175.43738 > 110.242.68.4.80: Flags [.], ack 2782, win 272, length 0
12:03:17.414281 IP 172.28.208.175.43738 > 110.242.68.4.80: Flags [F.], seq 78, ack 2782, win 272, length 0
12:03:17.423564 IP 110.242.68.4.80 > 172.28.208.175.43738: Flags [P.], seq 1453:2782, ack 78, win 908, length 1329: HTTP
12:03:17.423586 IP 172.28.208.175.43738 > 110.242.68.4.80: Flags [.], ack 2782, win 272, options [nop,nop,sack 1 {1453:2782}], length 0
12:03:17.449763 IP 110.242.68.4.80 > 172.28.208.175.43738: Flags [.], ack 79, win 908, length 0
12:03:17.449797 IP 110.242.68.4.80 > 172.28.208.175.43738: Flags [F.], seq 2782, ack 79, win 908, length 0
12:03:17.449816 IP 172.28.208.175.43738 > 110.242.68.4.80: Flags [.], ack 2783, win 272, length 0
12:03:17.770320 IP 172.28.208.175.53044 > 100.100.30.25.80: Flags [P.], seq 1842:3568, ack 1, win 1432, length 1726: HTTP
12:03:17.797997 IP 100.100.30.25.80 > 172.28.208.175.53044: Flags [.], ack 3568, win 2843, length 0客户端工具:wireshark

