1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
|
{
"AWSTemplateFormatVersion": "2010-09-09",
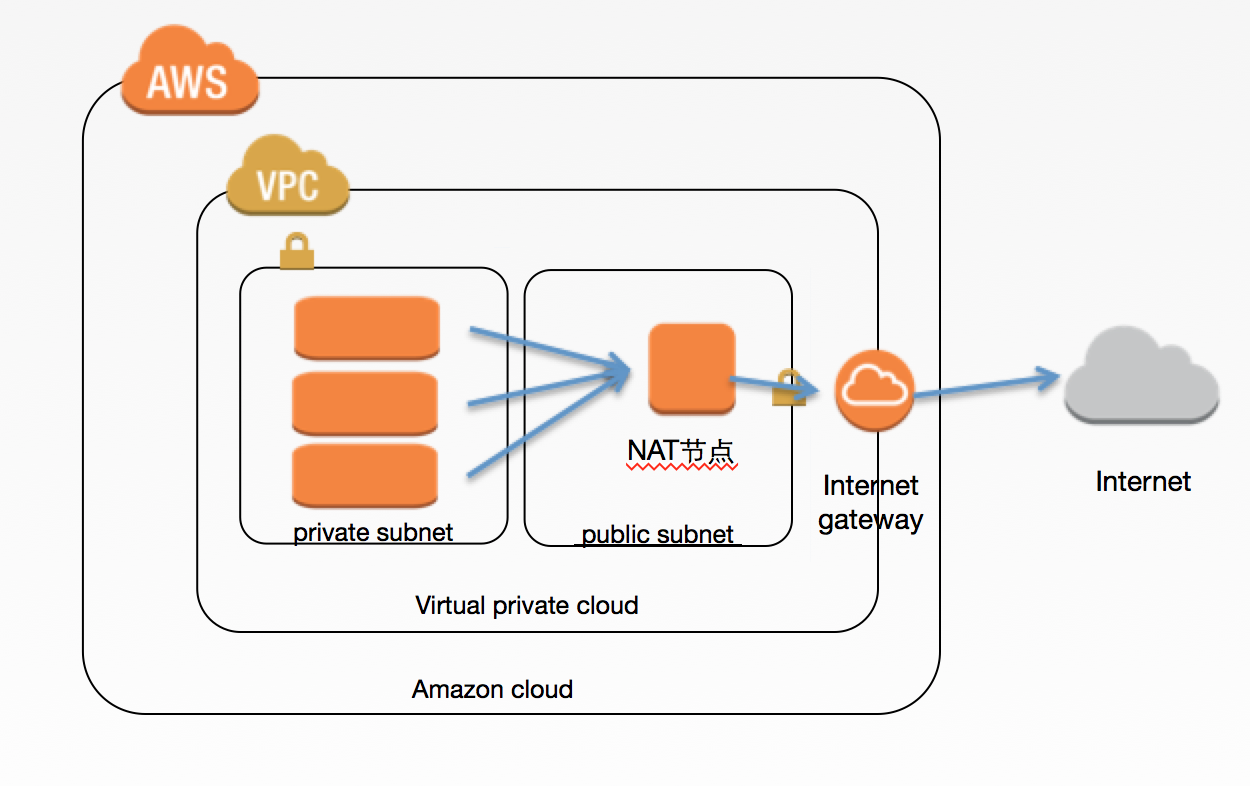
"Description": "Setup a vpc, which contains two subnets and one NAT machine",
"Parameters": {
"KeyName": {
"Description": "Name of and existing EC2 KeyPair to enable SSH access to the instance",
"Type": "String"
},
"VpcCidr": {
"Description": "CIDR address for the VPC to be created.",
"Type": "String",
"Default": "10.2.0.0/16"
},
"AnyCidr": {
"Description": "CIDR address for Any Where.",
"Type": "String",
"Default": "0.0.0.0/0"
},
"AvailabilityZone1": {
"Description": "First AZ.",
"Type": "String",
"Default": "cn-north-1a"
},
"PublicSubnetCidr": {
"Description": "Address range for a public subnet to be created in AZ1.",
"Type": "String",
"Default": "10.2.1.0/24"
},
"PrivateSubnetCidr": {
"Description": "Address range for private subnet.",
"Type": "String",
"Default": "10.2.2.0/24"
},
"NATInstanceType": {
"Description": "Instance type for NAT",
"Type": "String",
"Default": "t1.micro"
}
},
"Mappings": {
"AWSNATAMI": {
"cn-north-1": {
"AMI": "ami-eab220d3"
}
}
},
"Resources": {
"VPC": {
"Type": "AWS::EC2::VPC",
"Properties": {
"CidrBlock": {
"Ref": "VpcCidr"
},
"Tags": [
{
"Key": "Name",
"Value": "VPC"
}
]
}
},
"InternetGateWay": {
"Type": "AWS::EC2::InternetGateway",
"Properties": {
"Tags": [
{
"Key": "Name",
"Value": "INTERNET_GATEWAY"
}
]
}
},
"GatewayToInternet": {
"Type": "AWS::EC2::VPCGatewayAttachment",
"Properties": {
"InternetGatewayId": {
"Ref": "InternetGateWay"
},
"VpcId": {
"Ref": "VPC"
}
}
},
"PublicSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": {
"Ref": "PublicSubnetCidr"
},
"AvailabilityZone": {
"Ref": "AvailabilityZone1"
},
"Tags": [
{
"Key": "Name",
"Value": "PUBLIC_SUBNET"
}
],
"VpcId": {
"Ref": "VPC"
}
}
},
"PrivateSubnet": {
"Type": "AWS::EC2::Subnet",
"Properties": {
"CidrBlock": {
"Ref": "PrivateSubnetCidr"
},
"AvailabilityZone": {
"Ref": "AvailabilityZone1"
},
"Tags": [
{
"Key": "Name",
"Value": "PRIVATE_SUBNET"
}
],
"VpcId": {
"Ref": "VPC"
}
}
},
"DefaultSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Default Instance SecurityGroup",
"SecurityGroupIngress": [
{
"IpProtocol": "-1",
"CidrIp": {
"Ref": "VpcCidr"
}
}
],
"Tags": [
{
"Key": "Name",
"Value": "DEFAULT_SECURITY_GROUP"
}
],
"VpcId": {
"Ref": "VPC"
}
}
},
"PublicRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPC"
},
"Tags": [
{
"Key": "Name",
"Value": "PUBLIC_ROUTE_TABLE"
}
]
}
},
"PublicRoute": {
"Type": "AWS::EC2::Route",
"Properties": {
"DestinationCidrBlock": {
"Ref": "AnyCidr"
},
"GatewayId": {
"Ref": "InternetGateWay"
},
"RouteTableId": {
"Ref": "PublicRouteTable"
}
}
},
"PublicSubnetRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"RouteTableId": {
"Ref": "PublicRouteTable"
},
"SubnetId": {
"Ref": "PublicSubnet"
}
}
},
"NATEIP": {
"Type": "AWS::EC2::EIP",
"Properties": {
"InstanceId": {
"Ref": "NATInstance"
}
}
},
"NATInstance": {
"Type": "AWS::EC2::Instance",
"Properties": {
"InstanceType": {
"Ref": "NATInstanceType"
},
"KeyName": {
"Ref": "KeyName"
},
"SubnetId": {
"Ref": "PublicSubnet"
},
"SourceDestCheck": false,
"ImageId": {
"Fn::FindInMap": [
"AWSNATAMI",
{
"Ref": "AWS::Region"
},
"AMI"
]
},
"Tags": [
{
"Key": "Name",
"Value": "NAT"
}
],
"SecurityGroupIds": [
{
"Ref": "NATSecurityGroup"
}
]
}
},
"PrivateSubnetRouteTable": {
"Type": "AWS::EC2::RouteTable",
"Properties": {
"VpcId": {
"Ref": "VPC"
},
"Tags": [
{
"Key": "Name",
"Value": "PRIVATE_SUBNET_ROUTE_TABLE"
}
]
}
},
"PrivateSubnetRoute": {
"Type": "AWS::EC2::Route",
"Properties": {
"DestinationCidrBlock": {
"Ref": "AnyCidr"
},
"InstanceId": {
"Ref": "NATInstance"
},
"RouteTableId": {
"Ref": "PrivateSubnetRouteTable"
}
}
},
"PrivateSubnetRouteTableAssociation": {
"Type": "AWS::EC2::SubnetRouteTableAssociation",
"Properties": {
"RouteTableId": {
"Ref": "PrivateSubnetRouteTable"
},
"SubnetId": {
"Ref": "PrivateSubnet"
}
}
},
"NATSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "NAT Instance SecurityGroup",
"SecurityGroupIngress": [
{
"IpProtocol": "-1",
"CidrIp": {
"Ref": "VpcCidr"
}
}
],
"Tags": [
{
"Key": "Name",
"Value": "NAT_SECURITY_GROUP"
}
],
"VpcId": {
"Ref": "VPC"
}
}
}
},
"Outputs": {
"VPCId": {
"Description": "VPC id",
"Value": {
"Ref": "VPC"
}
},
"PublicSubnetId": {
"Description": "public subnet id",
"Value": {
"Ref": "PublicSubnet"
}
},
"PrivateSubnetId": {
"Description": "private subnet id",
"Value": {
"Ref": "PrivateSubnet"
}
},
"NATSecurityGroupId": {
"Description": "NAT SG id",
"Value": {
"Ref": "NATSecurityGroup"
}
},
"NATEIP": {
"Description": "NAT Server EIP.",
"Value": {
"Ref": "NATEIP"
}
}
}
}
|




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 如何编写易于单元测试的代码
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· .NET周刊【3月第1期 2025-03-02】
· 分享 3 个 .NET 开源的文件压缩处理库,助力快速实现文件压缩解压功能!
· [AI/GPT/综述] AI Agent的设计模式综述