Lab 1-1
LABS
The purpose of the labs is to give you an opportunity to practice the skills taught in the chapter. In order to simulate realistic malware analysis you will be given little or no information about the program you are analyzing. Like all of the labs throughout this book, the basic static analysis lab files have been given generic names to simulate unknown malware, which typically use meaningless or misleading names.
Each of the labs consists of a malicious file, a few questions, short answers to the questions, and a detailed analysis of the malware. The solutions to the labs are included in Appendix C.
The labs include two sections of answers. The first section consists of short answers, which should be used if you did the lab yourself and just want to check your work. The second section includes detailed explanations for you to follow along with our solution and learn how we found the answers to the questions posed in each lab.
Lab 1-1
This lab uses the files Lab01-01.exe and Lab01-01.dll. Use the tools and techniques described in the chapter to gain information about the files and answer the questions below.
Questions and Short Answers
-
Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
A: These files were written specifically for this book, so as of this writing, you should not find a signature for them on VirusTotal.com. Of course, if these files become part of the antivirus signatures as a result of the publication of this book, the results will be different.
-
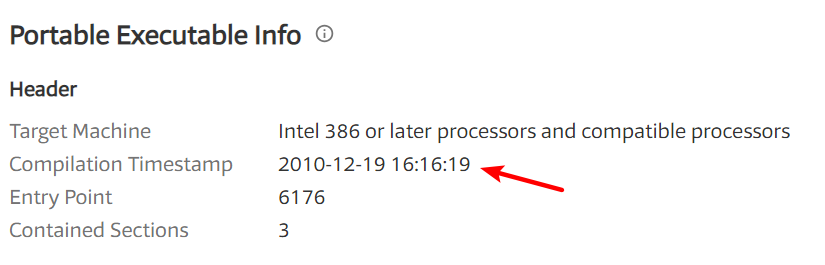
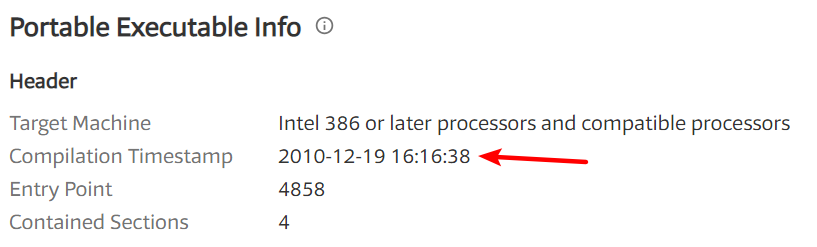
When were these files compiled?
A: Both files were compiled on December 19, 2010, within 1 minute of each other.
-
在 VT(http://www.VirusTotal.com/)中查看的结果如下:
Lab01-01.exe:
Lab01-01.dll:
-
使用 PEview 软件查看如下:
Lab01-01.exe:
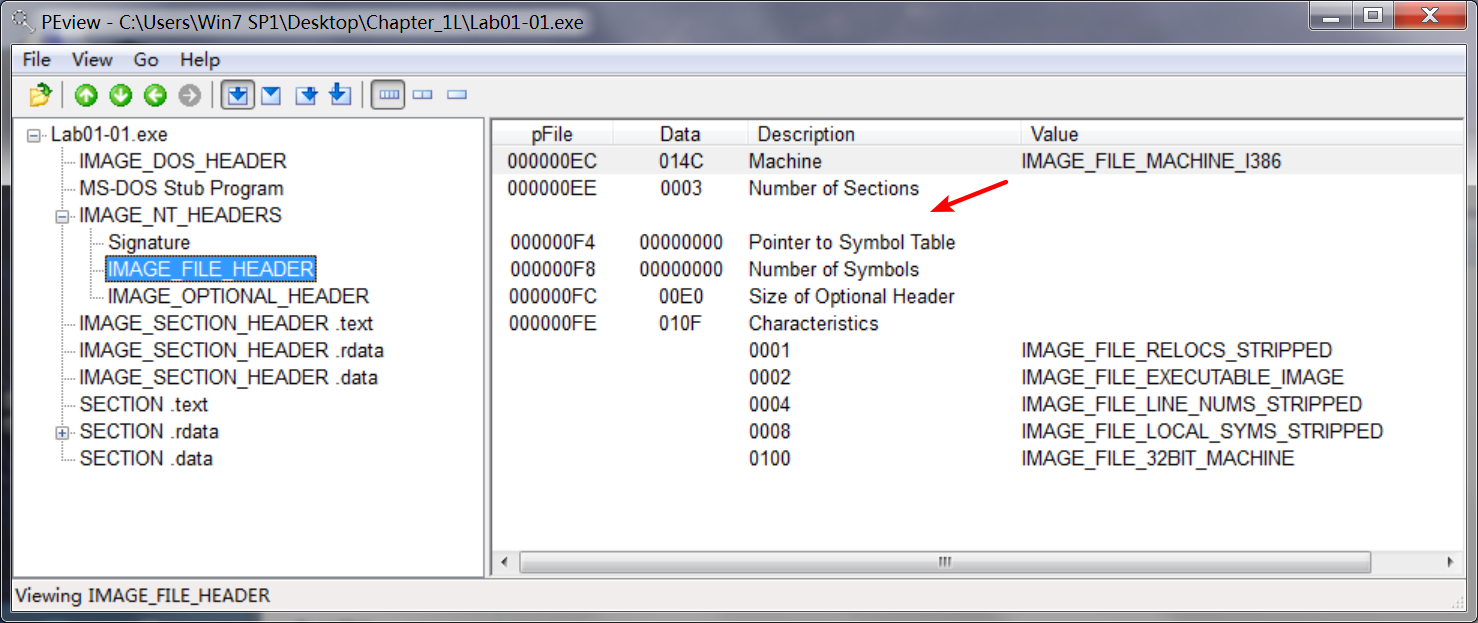
本该在箭头处显示,却为空。
Lab01-01.dll:
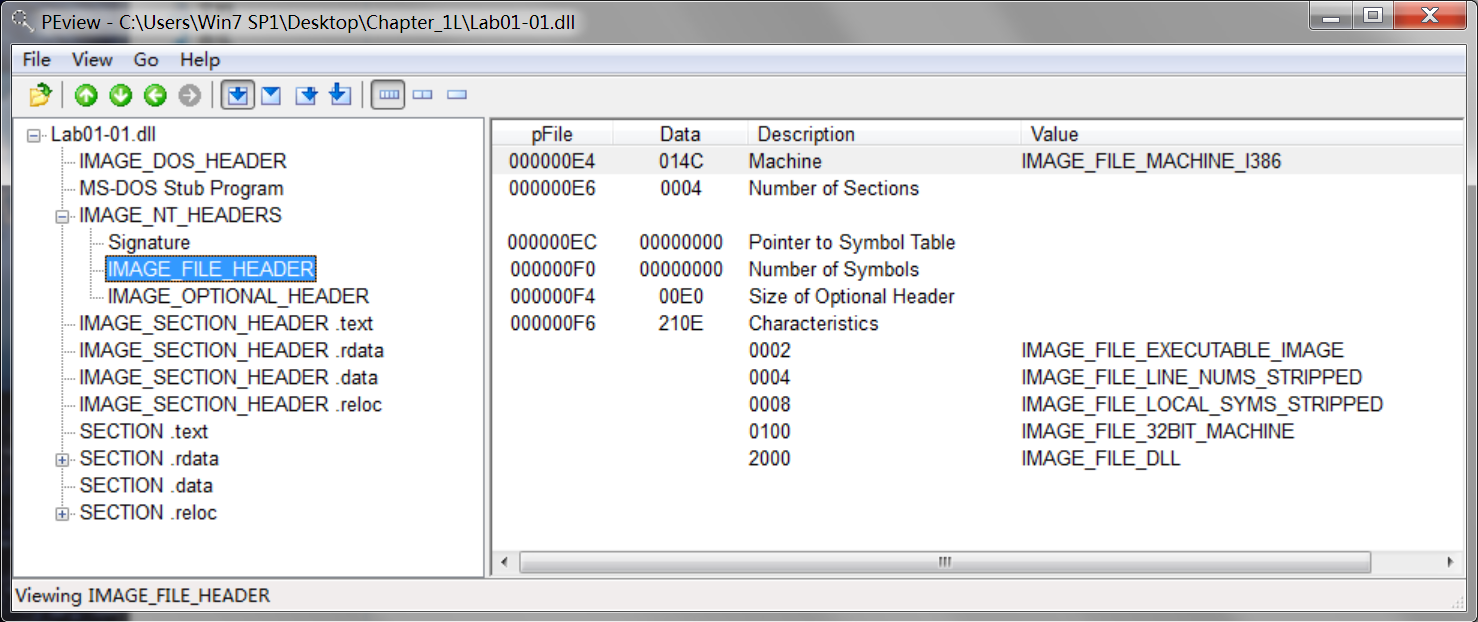
-
-
Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
A: There are no indications that either file is packed or obfuscated.
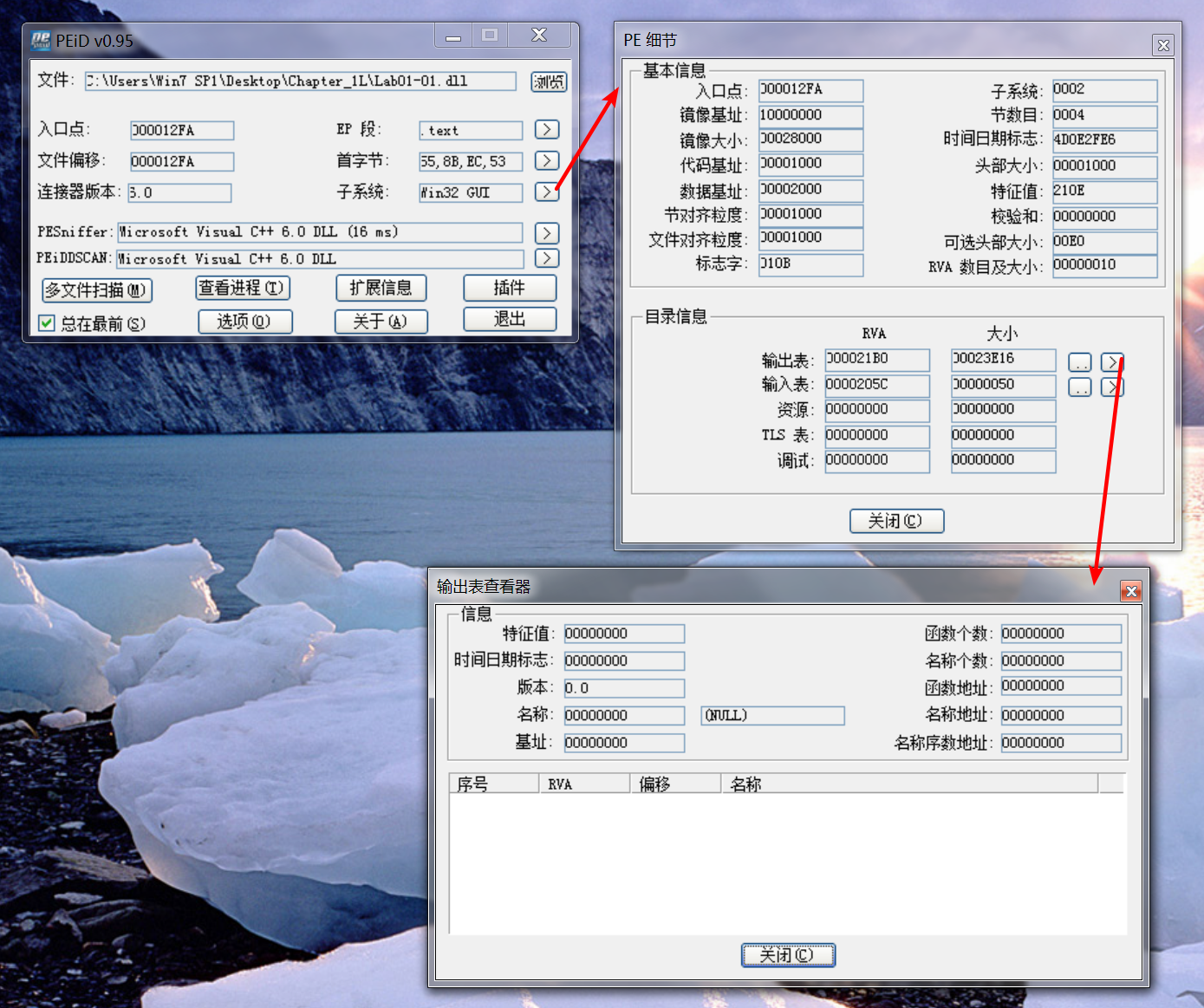
查看是否加壳可以用PEiD软件:
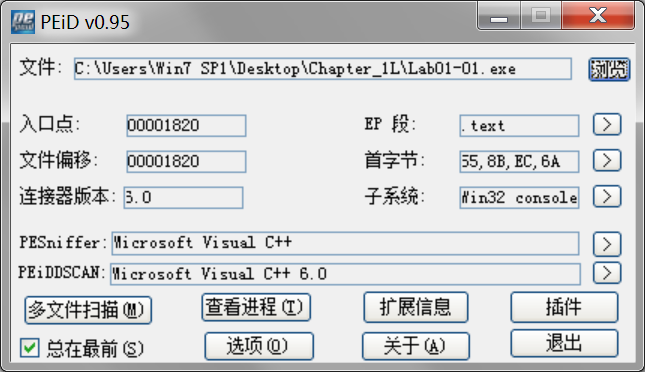
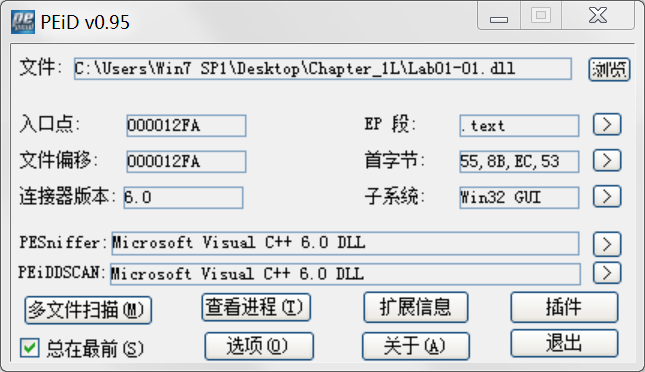
-
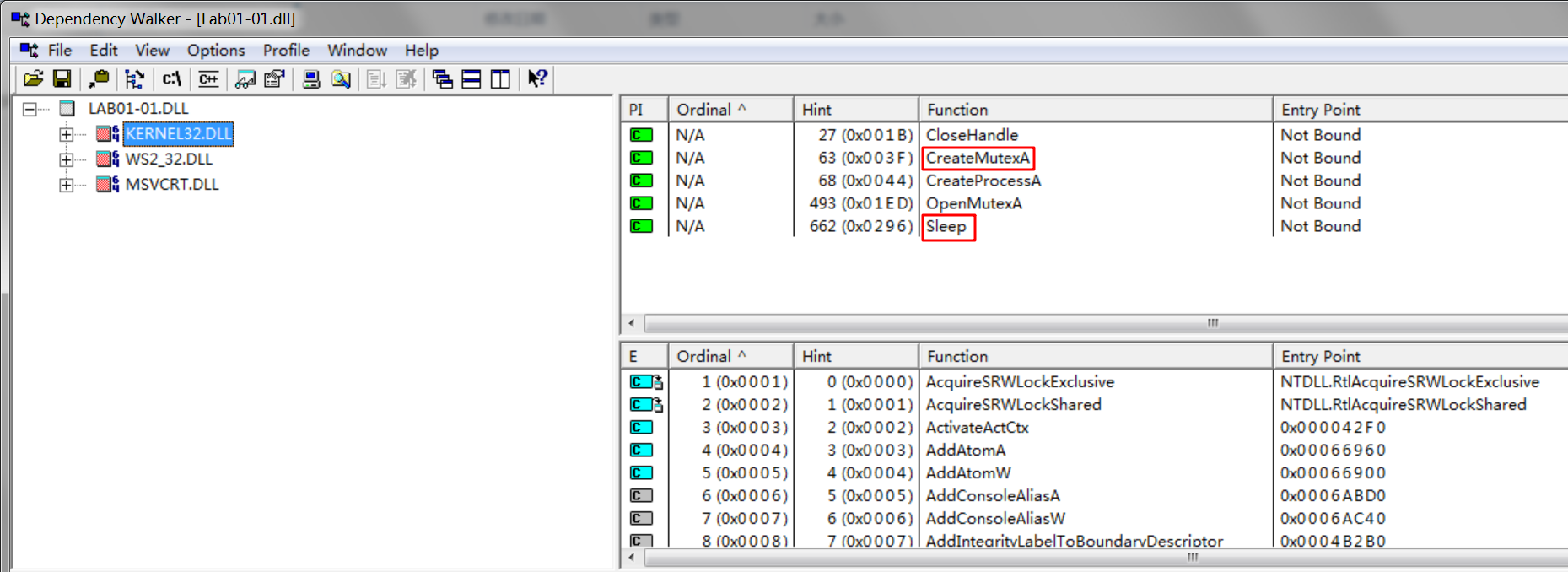
Do any imports hint at what this malware does? If so, which imports are they?
A: The interesting imports from Lab01-01.exe are FindFirstFile, FindNextFile, and CopyFile. These imports tell us that the program searches the file-system and copies files.
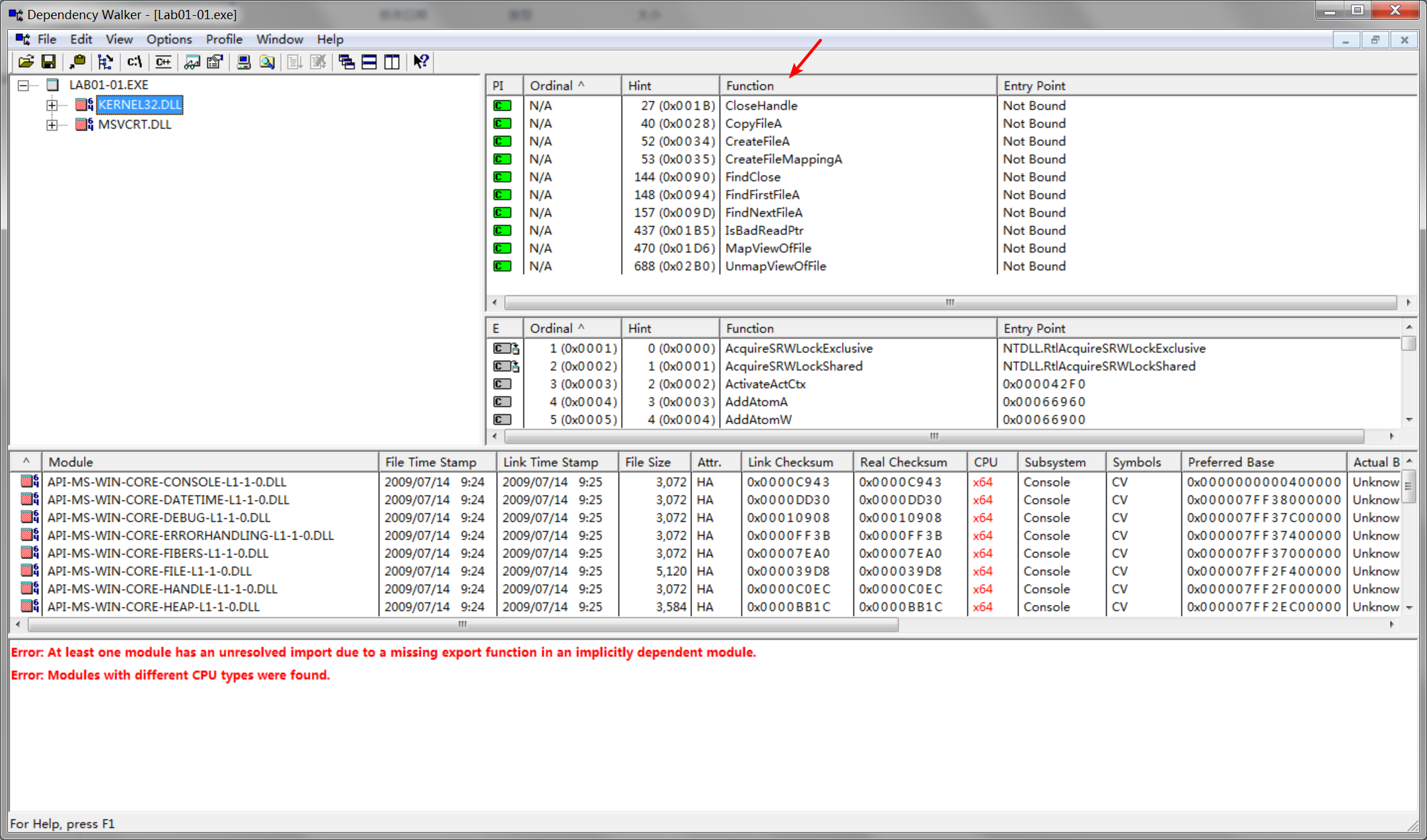
kernel32.dll是Windows 9x/Me中非常重要的32位动态链接库文件,属于内核级文件。它控制着系统的内存管理、数据的输入输出操作和中断处理,当Windows启动时,kernel32.dll就驻留在内存中特定的写保护区域,使别的程序无法占用这个内存区域。
msvcrt.dll是微软在windows操作系统中提供的C语言运行库执行文件(MicrosoftCRuntimeLibrary),其中提供了printf、malloc、strcpy等C语言库函数的具体运行实现,并且为使用C/C++(Vc)编绎的程序提供了初始化(如获取命令行参数)以及退出等功能。
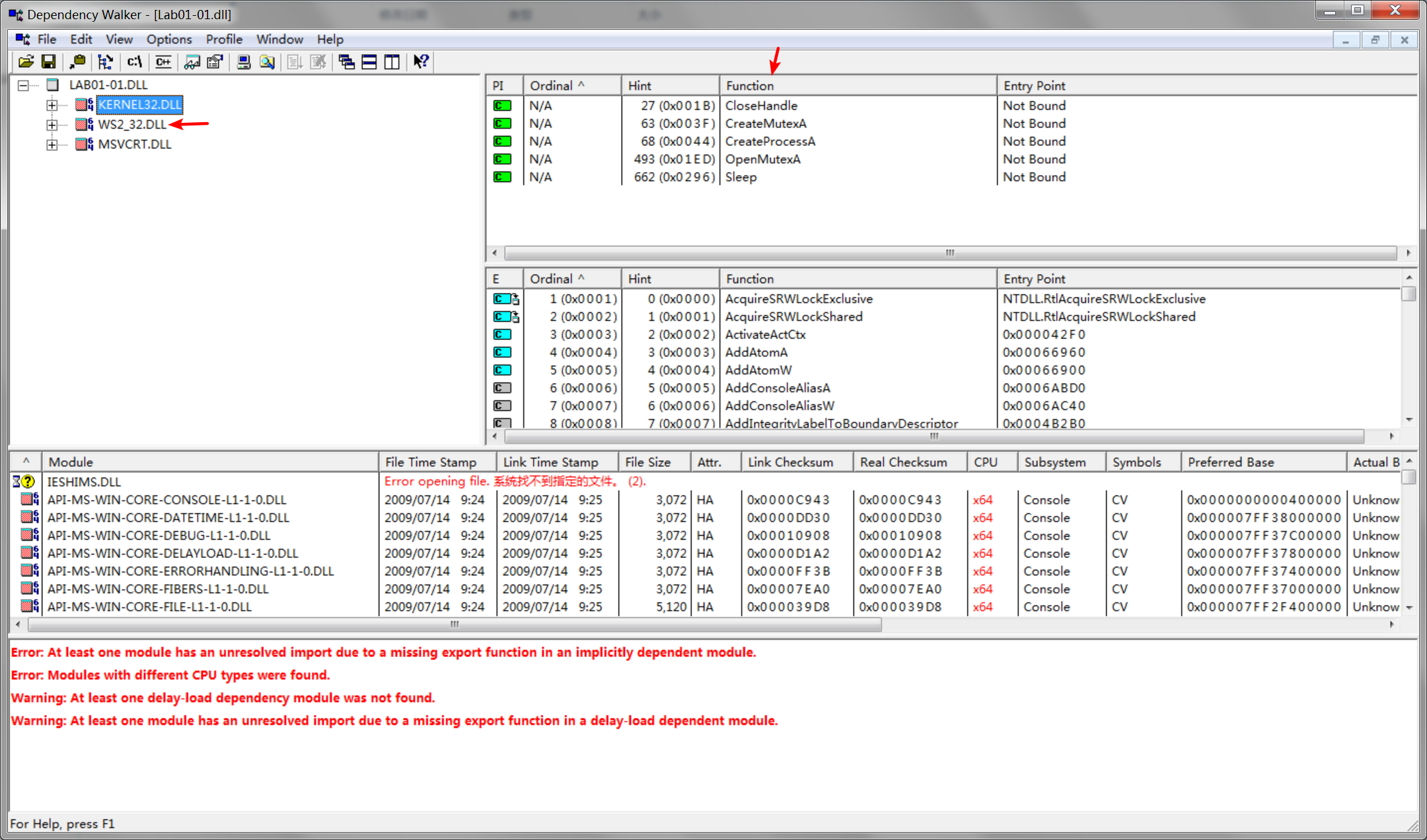
The most interesting imports from Lab01-01.dll are CreateProcess and Sleep. We also see that this file imports functions from WS2_32.dll, which provides network functionality.
-
Are there any other files or host-based indicators that you could look for on infected systems?
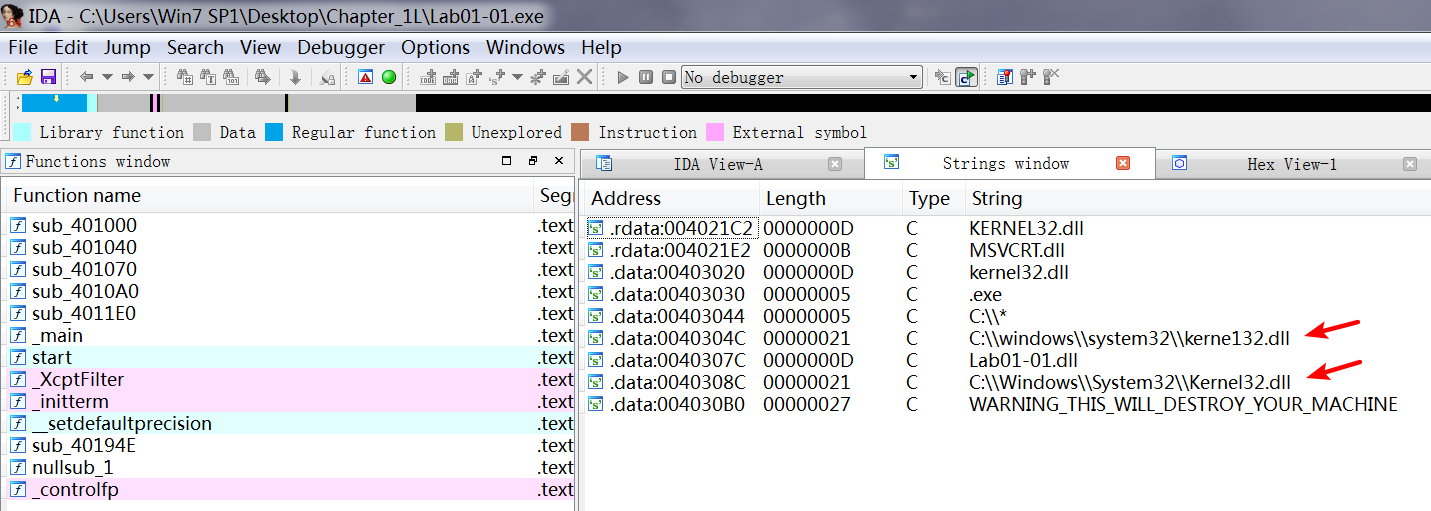
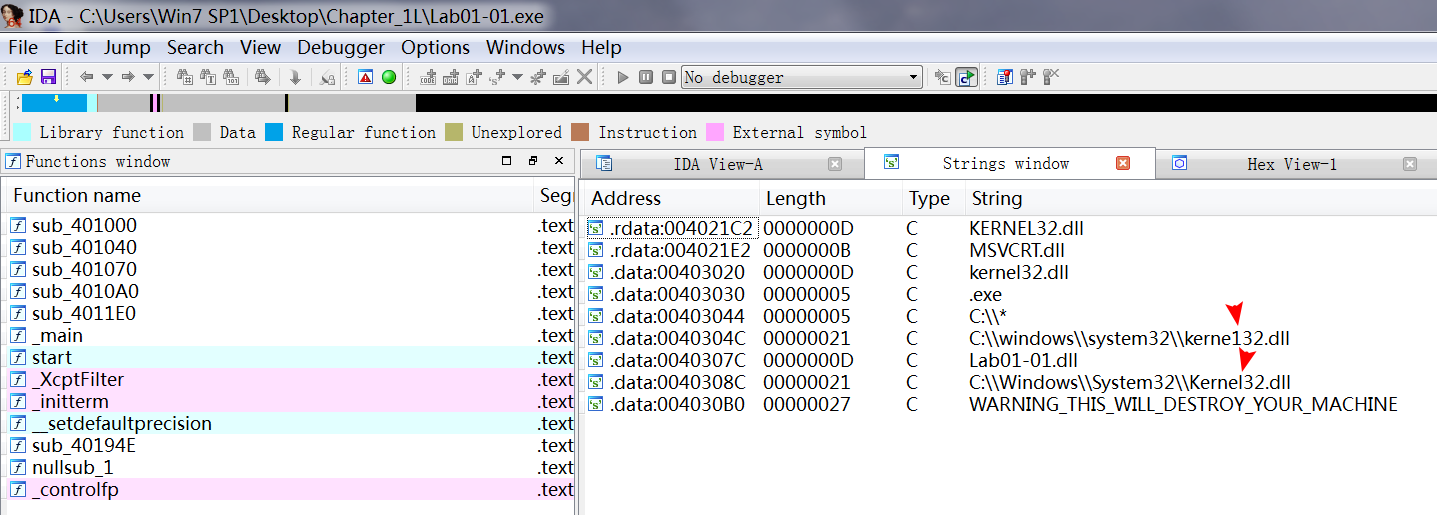
A: Examine C:\Windows\ System32\ kerne132.dll for additional malicious activity. Note that the file kerne132.dll, with the number 1 instead of the letter l, is meant to look like the system file kernel32.dll. This file can be used as a host indicator to search for the malware.
通过 IDA 查看 Lab01-01.exe,View -> Open subviews -> Strings :
-
What network-based indicators could be used to find this malware on infected machines?
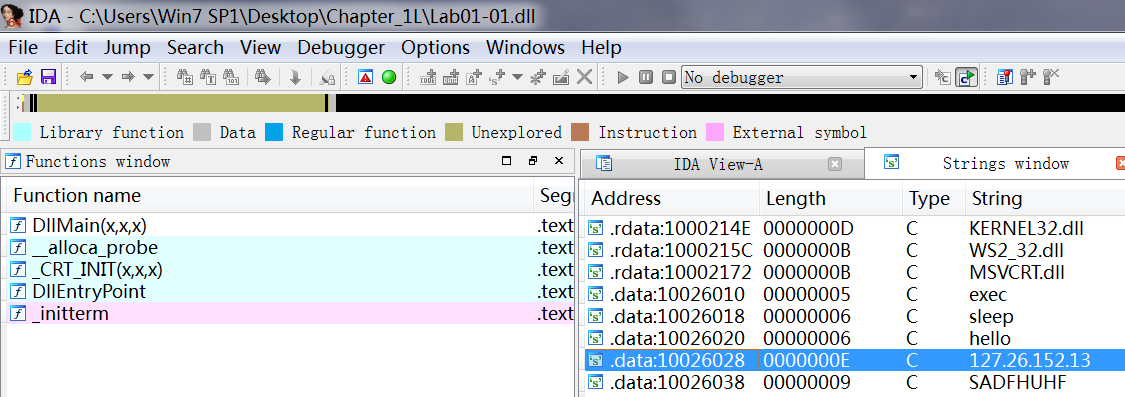
A: The .dll file contains a reference to local IP address 127.26.152.13. This address is an artifact of this program having been created for educational and not malicious purposes. If this was real malware, the IP address should be routable, and it would be a good network-based indicator for use in identifying this malware.
通过 IDA 查看 Lab01-01.dll,View -> Open subviews -> Strings :
-
What would you guess is the purpose of these files?
A: The .dll file is probably a backdoor. The .exe file is used to install or run the DLL.
Detailed Analysis
To answer the first question, we upload the file to VirusTotal.com, which performs a scan against antivirus signatures.
Next, we open the files in PEview. For each file, we navigate to the IMAGE_NT_HEADERSIMAGE_FILE_HEADER -> Time Date Stamp field, which tells us the compile time. Both files were compiled on December 19, 2010, within 1 minute of each other. This confirms our suspicions that these files are part of the same package. In fact, a compile time that close strongly suggests that these files were created at the same time by the same author. We know that the files are related because of the compile times and where they were found. It’s likely that the .exe will use or install the .dll, because DLLs cannot run on their own.
Then we check to see if either file is packed. Both files have small but reasonable numbers of imports and well-formed sections with appropriate sizes. PEiD labels this as unpacked code compiled with Microsoft Visual C++, which tells us that these files are not packed. The fact that the files have few imports tells us that they are likely small programs. Notice that the DLL file has no exports, which is abnormal, but not indicative of the file being packed. (You will learn more about this export section when we return to these files in Lab 7-3.)
Next, we look at the files’ imports and strings beginning with the .exe. All of the imports from msvcrt.dll are functions that are included in nearly every executable as part of the wrapper code added by the compiler.
When we look at the imports from kernel32.dll, we see functions for opening and manipulating files, as well as the functions FindFirstFile and FindNextFile. These functions tell us that the malware searches through the filesystem, and that it can open and modify files. We can’t be sure what the program is searching for, but the .exe string suggests that it is searching for 1 executables on the victim’s system.
We also see the strings C:\Windows\System32\Kernel32.dll and C:\windows\ system32\kerne132.dll. (Notice the change from the letter l to the number 1
in kernel32.dll.) The file kerne132.dll is clearly meant to disguise itself as the Windows kernel32.dll file. The file kerne132.dll can serve as a host-based indicator to locate infections, and it is one that we should analyze for malicious code.
Next, we look at the imports and strings for Lab01-01.dll, which imports functions from WS2_32.dll. Because these functions are imported by ordinal, we don’t know which functions are being imported.
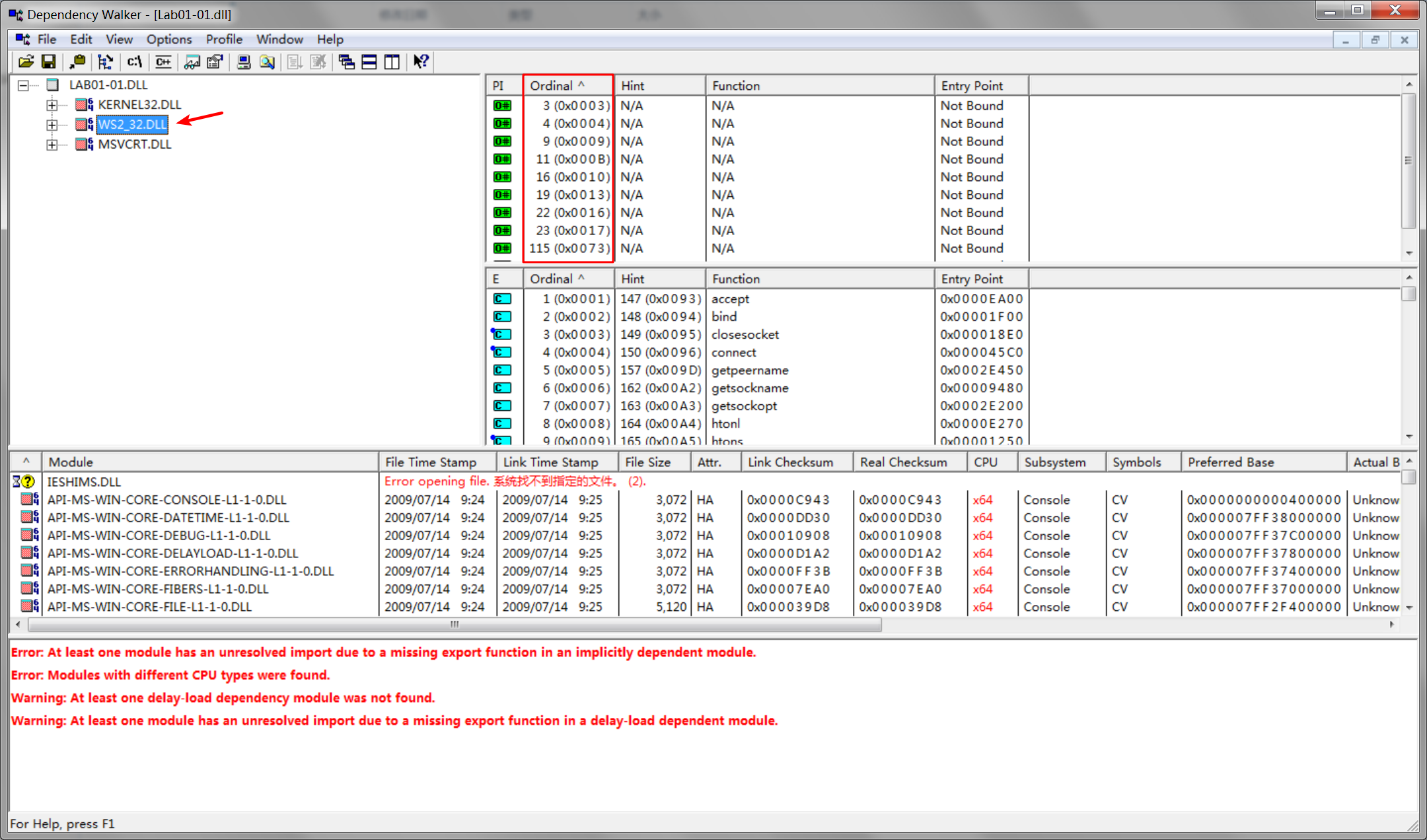
We also see two interesting functions imported from kernel32.dll: CreateProcess and Sleep, which are commonly used as backdoors. These functions are particularly interesting to us in combination with the strings exec and sleep. The exec string is probably sent over the network to command the backdoor to run a program with CreateProcess. The sleep string is probably used to command the backdoor program to sleep. (This malware is complex. We’ll return to it in Lab 7-3, once we have covered the skills to analyze it fully.)